- Home
- Microsoft Teams
- Teams Developer
- Authenticating with an access token Connect-MicrosoftTeams
Authenticating with an access token Connect-MicrosoftTeams
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2021 04:38 PM
New-CsOnlineSession has been dropped and the SfB Connector is end of life in July and Connect-MicrosoftTeams does appear to support token for the telephony functions.
- Labels:
-
Administrator
-
Calling
-
Microsoft Teams
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 21 2022 05:10 AM - edited Sep 21 2022 05:11 AM
Here is the documentation for using app-based auth with 4.7.1.
https://learn.microsoft.com/en-us/microsoftteams/teams-powershell-application-authentication
"For *-Cs cmdlets - no API permissions are needed."
"The application needs to have the appropriate RBAC roles assigned."
The first I've realized that you can assign AAD RBAC roles to an application.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 21 2022 05:55 AM
"Cmdlets Supported
All Non *-Cs cmdlets (for example, Get-Team), Get-CsTenant, Get-CsOnlineUser, Get-CsOnlineVoiceUser & *-CsOnlineSipDomain cmdlets are already supported. Other cmdlets will be gradually rolled out."
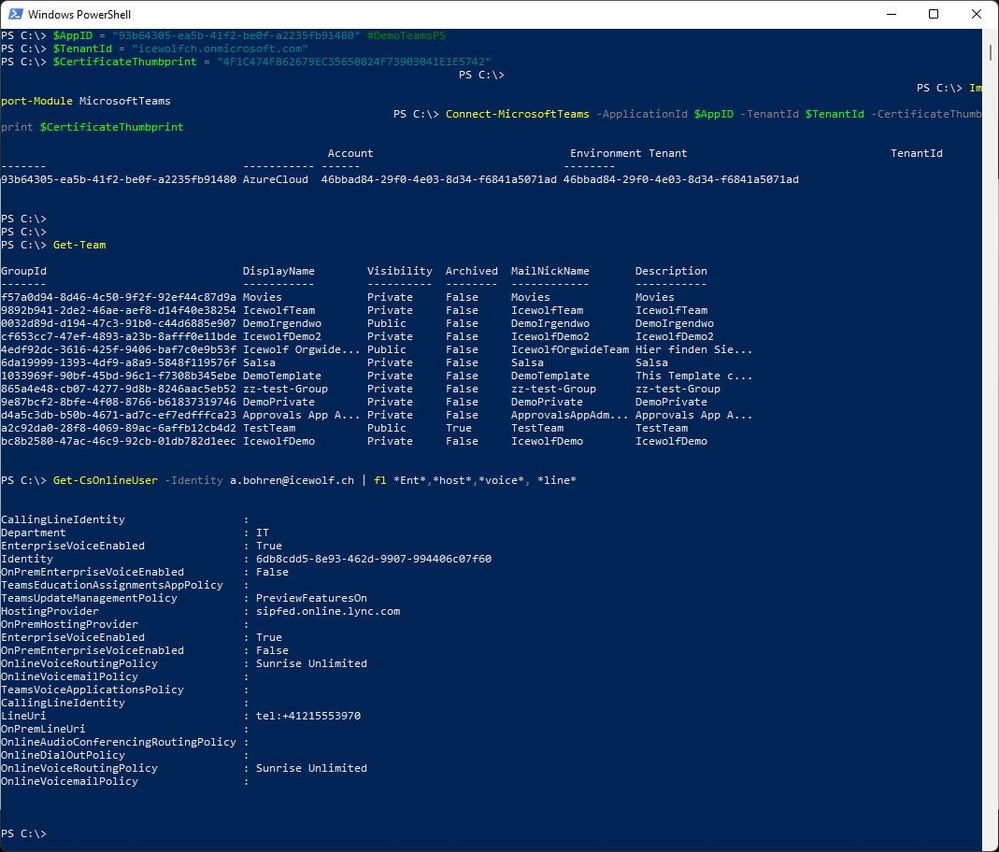
I was able to connect with CertificateThumbprint and run a Get-CsOnlineUser. However, I need several other -Cs cmdlets. I suppose I need some more patience!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 21 2022 09:39 PM
This error is most likely caused by the module trying to find the "UPN" value of the token, which is the user name of the respective account. Since the authorization flow takes place within the context of a user, the token has a UPN, which allows this flow to work. There is no user context or UPN involved with the client credentials, which leads to the credentials not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 22 2022 12:42 PM
i'm getting "access denied" for Get-CsOnlineUser, Get-Team works.
what permissions did you add to your app ?
i'm working with a developer account, do you know if that would be a constraint ?
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 25 2022 04:17 PM
1. "Assign API permissions to the application": Do the listed permissions need to be application permissions with subsequent admin consent granted or delegated permissions?
2. "Assign Azure AD roles to the application": How do you do this? Can anyone provide links to additional documentation?
Like @lazedo, I get "access denied" with Get-CsOnlineUser, and suspect permissions and roles aren't set up properly. I'm using MicrosoftTeams v4.7.1 and authenticating via access tokens. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 26 2022 02:33 AM
GET-TEAM works fine for me. However I get below error for Get-CsOnlineUser. Have given RBAC role to the app. I am using Pwsh on linux.
Get-CsOnlineUser: Connecting to remote server api.interfaces.records.teams.microsoft.com failed with the following error message : MI_RESULT_FAILED For more information, see the about_Remote_Troubleshooting Help topic.
Sep 26 2022 06:36 AM - edited Sep 26 2022 06:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 26 2022 06:36 AM - edited Sep 26 2022 06:37 AM
Answer to question 2: Azure Portal > Azure Active Directory > Roles and Administrators > Search for the Teams Administrator role and select it > Add assignments > Click on the "No member selected" link > Search for your teams management service principle previously set up > Click on its tile > Click Select > Click Next > Select Active > Check Permanently Assigned or set start and end dates as needed > Type in a justification > Click Assign. Azure global administrators will get an email an a minute or two from the Azure Privileged Identity Management service when it's set up. This makes Get-CsOnlineUser work with both token-based and certificate-based authentication as described in the above article. Adding the service principle to the Skype for Business Administrator role does not appear to be necessary, at least for present purposes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 27 2022 06:40 AM
Hi, assigning "Teams Administrator" to service principal (appid) does work.
but this is not going to solve the user experience part.
Tenant A - creates the app and publishes it
Tenant B - grants admin consent on the app
Tenant A - tries to manage teams settings and gets unauthorized
Tenant A - cannot get into Tenant B and add the service principal to Tenant Administrators, Tenant B admin needs to do this
this should be done automatically when Tenant B admin grants admin consent but there's no permission available that Tenant A could provide that would do this.
getting better but still this ux is not what we're seeking for over a year.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 28 2022 12:15 AM - edited Sep 28 2022 12:16 AM
Hi All,
Here is my Blog how to do App Authentication with a Certificate in the Microsoft Teams PowerShell Module in Preview
For now only a few commandlets work.
All Non *-Cs cmdlets (for example, Get-Team), Get-CsTenant, Get-CsOnlineUser, Get-CsOnlineVoiceUser & *-CsOnlineSipDomain cmdlets are already supported. Other cmdlets will be gradually rolled out.
Regards
Andres
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 04 2022 04:14 AM
I am trying to authenticate using tokens. Any idea on what am I missing?
Thank you,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 11 2022 11:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 12 2022 03:13 AM - edited Oct 12 2022 03:23 AM
@lazedo I removed the "Skype and Teams Tenant Admin API" from my app permissions and assigned the AD Role "Skype for Business administrator" to my app. Still the same error.
Does this work on multi-tenant cases? Or this will only work with the tenant that owns the app?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 12 2022 05:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 13 2022 01:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 14 2022 03:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 20 2022 12:16 PM
Currently its only available in none-interactive scripts using Client Secret !!!!
- « Previous
- Next »