- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Re: How to exclude specific machines from Intune compliance policy?
How to exclude specific machines from Intune compliance policy?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 07 2018 07:05 AM - edited Mar 07 2018 07:09 AM
Hi,
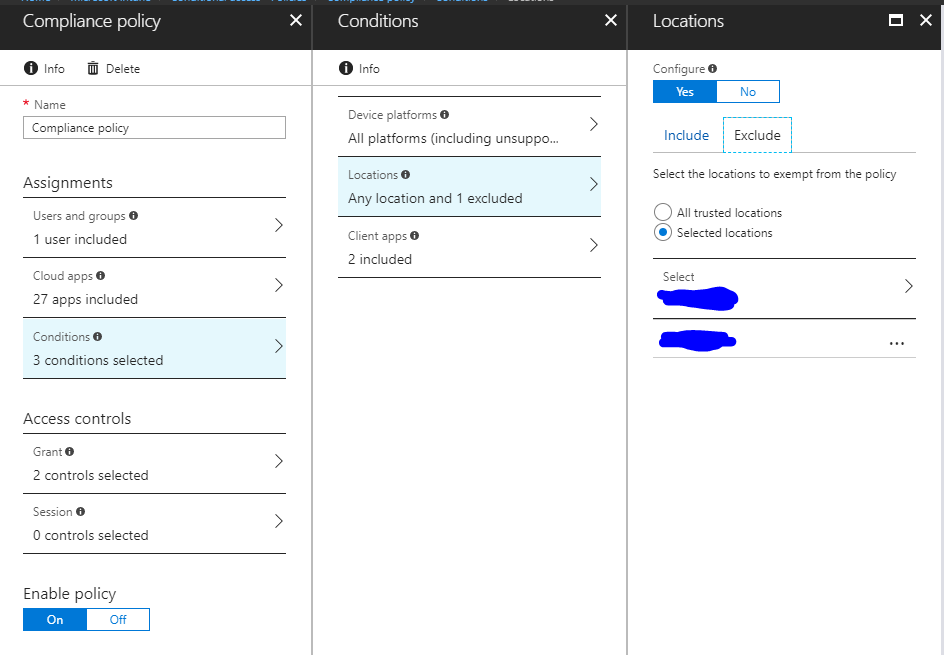
I need a few virtual machines to be excluded from the Intune compliance policy, I thought that the following setup would be sufficient to accomplish this and be able to access corporate data without the need to make these virtual machines compliant (they all have fixed IPs):
Unfortunately this isn't working and I'm wondering how could I exclude this machines from enrolment.
Thank you,
Ion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 03:16 AM
Hello Ion,
Can you create a device group with the virtual machines and exclude the group from the Compliance Policy? See if that works like expected?
Best regards,
Ruud Gijsbers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 03:33 AM
Hi Ion,
it's not really clear for me what you like to achieve from the description. Your screenshot shows the Conditional Access policy and you are talking about Compliance policy. Do you want to exclude devices from CA or from the Compliance policy itself? If you want to exclude from Compliance policy you need to be aware how the Compliance policy is assigned. If the Compliance policy is assigned to users than you can use the exclude feature only with user groups. If assigned to a device group the exclude can only contain device groups. You can't mix user and device groups when using include/exclude, this is the current implementation and by design.
Regarding your CA policy you need to specify IP ranges. To specify a single IP address you need to use 192.168.1.1/32, the /32 at the end is important to specify a single IP address.
Hope this helps.
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 04:09 AM
Hi Oliver,
Sorry if it wasn't very clear, but it is as you describe.
I'm trying to exclude this machines from the compliance policy itself, but this policy applies to user groups. I was aware that the issue was here, but I was hoping there was a way to say "with the exception of these machines regardless of the user", which I think it would be a very useful and sensible option to have.
I want users to be able to access corporate data as long as they are using a device under Intune's umbrella, therefor I'm applying the group policy to the users. This virtual machines are hosts to sessions that some of our users connect to and work from with the use of thin clients.
I understand it won't be possible to achieve this on this scenario?
Thank you,
Ion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 04:20 AM - edited Mar 08 2018 04:21 AM
Hi Ruud,
Thank you for your reply.
It looks like it might not be possible to exclude them (see Oliver's reply above). At the moment the way I'm trying to exclude this machines is by using their public IPs, which I understand should have the same effect (I've use them to exclude them from other policies in the past successfully).
Kind regards,
Ion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 04:24 AM
SolutionHi Ion,
I totally understand and agree that this would be great to have. User assignment and exclusion of devices. This would solve this problem and many more I think. I don't see any other solution than using device groups in total for compliance policy. Gather your devices via a dynamic group and assign the compliance policy. But there is another side effect if you assign users compliance policies and devices compliance policies. When a user is now target of a policy and his device also, the overall status of compliance policy is not calculated as an logical AND it's an logical OR. let me give an example:
user A -> user policy A
user A uses device A and has device policy B
then it might be like this:
user policy A is evaluated as compliant and device policy B is evaluated as non-compliant. Now because of the logical OR the user will get IsCompliant=True
So mixing is not a great idea. At the moment we need to decide to go for user assignments or device assignments imho. this leads to various restrictions.
Best way imho is to exclude them from the Conditional Access policy...
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 05:01 AM
Hi Oliver,
It looks like I'm going to have to re-think how to approach this and adapt our desired outcome to using device groups to apply the policies then.
My thanks for your assistance on this matter.
Kind regards,
Ion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 05:08 AM
Hi Ion,
sure no problem. Another effect to mention when using device assignment is, that it might take long to apply. Imagine the situation. Using Windows 10 and OOBE + AAD join + Intune auto enrollment. Then the device is not instantly available and needs to be registered first by the enrollment process. This needs some time. Then the dynamic group needs some time to pick up the device and then the device must sync to get the new policy to evaluate. So it might be (depending on the scenario) that you face delays which might be a problem. For example when you have a conditional access policy which requires compliant devices, then the device needs some time to get compliant and as long as it is non-compliant it can't access corporate data protected by conditional access.
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 07:28 AM
Hi Oliver,
It just occurred to me; since we have absolutely no connection between our on-premises infrastructure and our Azure and 365 users and devices (thus not using Hybrid Azure AD), I believe this path isn't going to work either.
I can create a group (or groups) and add all of our company own devices there to then force compliance upon it. However, I see no policies within conditional access that will allow me to deny access to company data to any device outside of that hypothetical group.
Regards,
Ion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 07:50 AM - edited Mar 09 2018 01:30 AM
Yes that's right Conditional Access (CA) will allow rules based on User groups only. The identity is what counts. A user needs access to corp data and therefore wants an access token. This will be provided only if you fulfill the CA requirements as set (e.g. require compliant device). So in your case you can only say enforce CA for all users, assign a compliance policy to the device group and then they get access. There will be a change (currently in rollout) in Intune which basically treats all devices without compliance policy as non-compliant. See here: https://blogs.technet.microsoft.com/intunesupport/2018/02/09/updated-upcoming-security-enhancements-...
With this you could build your CA policy to allow only compliant devices, assign the compliance policy to your device group and all others are treated as non-compliant and will not get access to the corp resources.
Do you get the idea?
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 09 2018 01:26 AM
Hello,
That update is spot on, thank you for the information Oliver.
Best regards,
Ion
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 08 2018 04:24 AM
SolutionHi Ion,
I totally understand and agree that this would be great to have. User assignment and exclusion of devices. This would solve this problem and many more I think. I don't see any other solution than using device groups in total for compliance policy. Gather your devices via a dynamic group and assign the compliance policy. But there is another side effect if you assign users compliance policies and devices compliance policies. When a user is now target of a policy and his device also, the overall status of compliance policy is not calculated as an logical AND it's an logical OR. let me give an example:
user A -> user policy A
user A uses device A and has device policy B
then it might be like this:
user policy A is evaluated as compliant and device policy B is evaluated as non-compliant. Now because of the logical OR the user will get IsCompliant=True
So mixing is not a great idea. At the moment we need to decide to go for user assignments or device assignments imho. this leads to various restrictions.
Best way imho is to exclude them from the Conditional Access policy...
best,
Oliver