- Home
- Microsoft 365
- Microsoft 365
- MFA, Can not change from SMS to Authenticator app
MFA, Can not change from SMS to Authenticator app
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 22 2021 08:16 AM
Hello,
I have an issue with MFA within my tenant. We have been using SMS based MFA for some time now. We would like to move to the Microsoft Authenticator App for MFA.
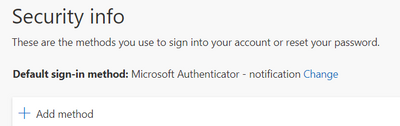
But for some reason, when a user goes in to his / hers "security info" page. They see as the "Default sign-in method:" as "Phone text".
The authenticator app is configured for a user, they can not set is as default.
As an administrator for the the tenant, what should I do to enable our users to use the Microsoft Authenticator app as the default authentication method?
- Labels:
-
Admin
-
Office 365
-
Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 22 2021 11:21 AM - edited Aug 22 2021 11:41 AM
Hello, the easy and quick way is to enable Security defaults Azure Active Directory security defaults | Microsoft Docs (only the Authenticator app) but if you're using a subscription with conditional access for more granular control you should enter the Azure AD MFA settings to verify the authentication methods you provide to your users Configure Azure AD Multi-Factor Authentication - Azure Active Directory | Microsoft Docs
Set up the Microsoft Authenticator app as your verification method - Azure AD | Microsoft Docs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 04:21 AM
@ChristianJBergstromThanks for the reply.
I checked and confirmed that Security defaults is turned on. There is no conditional access set up. All licenses are either Business Basic or Business Standard. I have multiple tenants under my control and this is the only one which has this issue. Like said, users can setup the Microsoft Authenticator app, but can not se it as the default sign-in method.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 04:46 AM - edited Aug 23 2021 05:14 AM
Do you see the Change link here or only "Phone" (instead of below Authenticator).
https://mysignins.microsoft.com/security-info
What makes me wonder is "these free security defaults allow registration and use of Azure AD Multi-Factor Authentication using only the Microsoft Authenticator app using notifications."
Thinking you might hit a bug or something. Perhaps raise a case with Microsoft?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 05:39 AM
SolutionI went and did some more research on the Azure admin center. Found out that in the "Security" section -> "Manage" -> "Authentication Methods" -> Microsoft Authenticator was turned off.
After enabling it, I can now change the default sign-in method.
Thanks for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 05:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 05:56 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 06:59 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 06 2022 08:46 AM
I tried Clerk Chat. They enable a non-voip number on Teams and I get all my MFA codes on that number directly on teams.
It's really handy. :smiling_face_with_smiling_eyes:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 07 2023 05:18 AM
Unless you're using Conditional Access Policies to require MFA to log into Teams as well via Modern Auth client Apps - then you're in a world of hurt as you'll need to Authenticate via MFA in order to log into Teams to get your codes (chicken and egg scenario)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2021 05:39 AM
SolutionI went and did some more research on the Azure admin center. Found out that in the "Security" section -> "Manage" -> "Authentication Methods" -> Microsoft Authenticator was turned off.
After enabling it, I can now change the default sign-in method.
Thanks for your help!