Dear Active Directory friends,
This article is about setting up advanced monitoring for an Active Directory infrastructure. In order to then be able to carry out an extended hunt.
In order for information to be examined quickly and efficiently, I believe it is essential to store the information centrally. This is where Security Onion comes in (The tool is free of charge!).
But before information can be examined, advanced logging (in this example, with domain controllers) must be set up. The following article from the Microsoft documentation is a great starting point.
Configure Windows Event collection:
Now it's time to install and configure Security Onion. On the website of Security Onion Solutions there is a really great documentation for installation and configuration. The hardware requirements are addressed and everything needed to get an instance up and running.
Note: Here you can find the information about the installation and configuration:
Use the new Security Onion 2.4
Note: If you are still using the Winlogbeat agent, you should first uninstall it before installing the new agent.
Stop the service - should be removed after uninstall
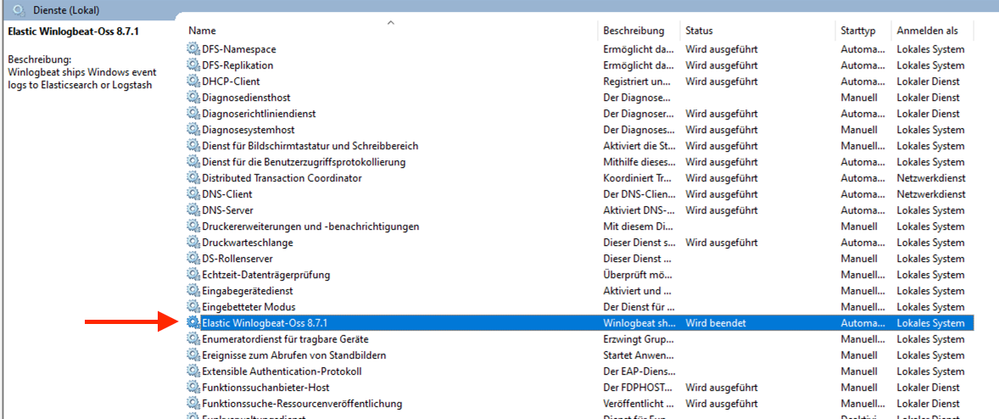
Uninstall old agents if necessary
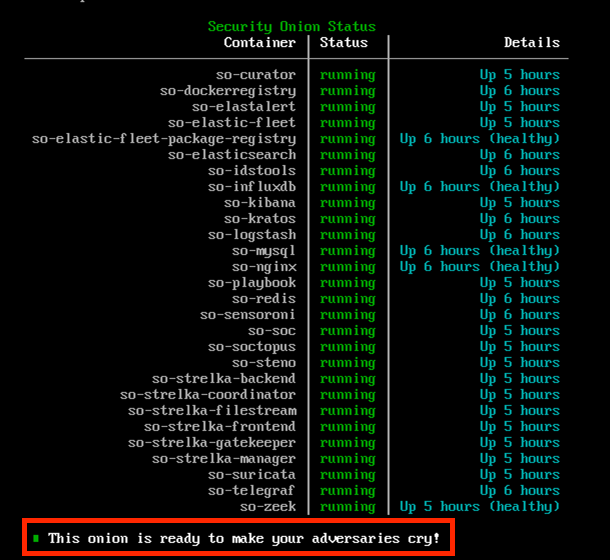
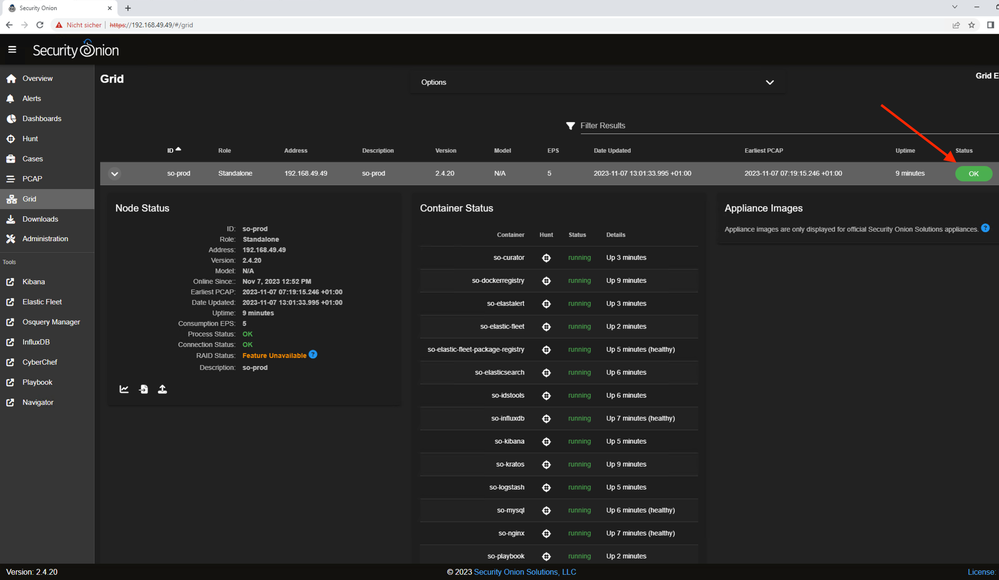
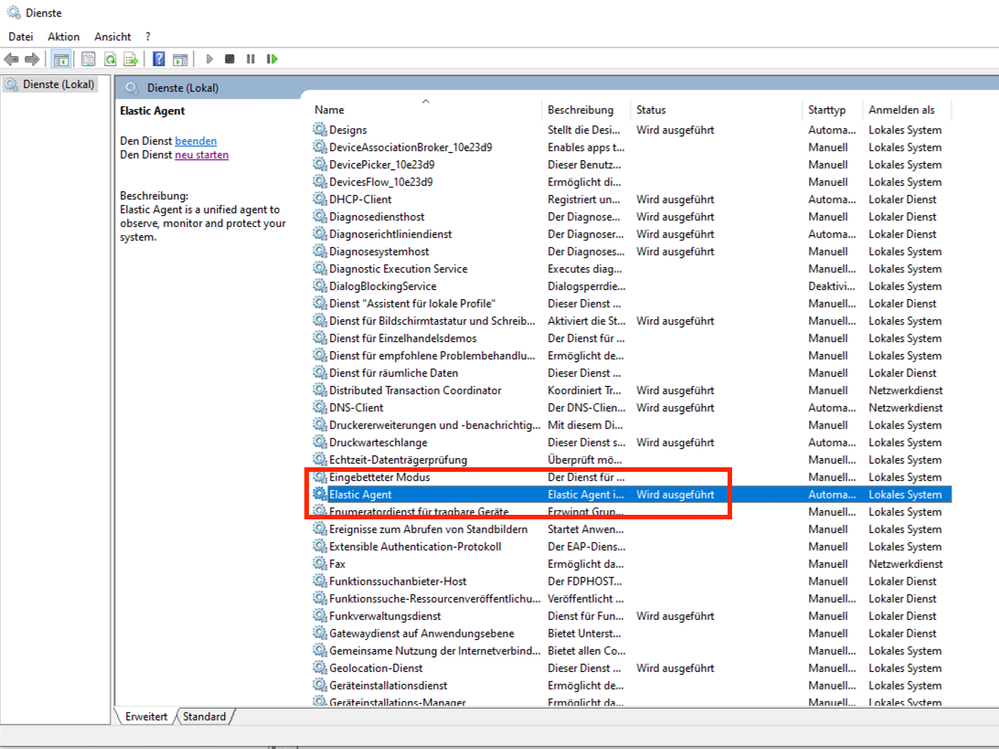
The status of the Security Onion
After the installation of the Security Onion, it is now time to set up the agent (Elastic Agent) on all systems (that are to be monitored). First, check the status of the Security Onion.
At the console: sudo so-status
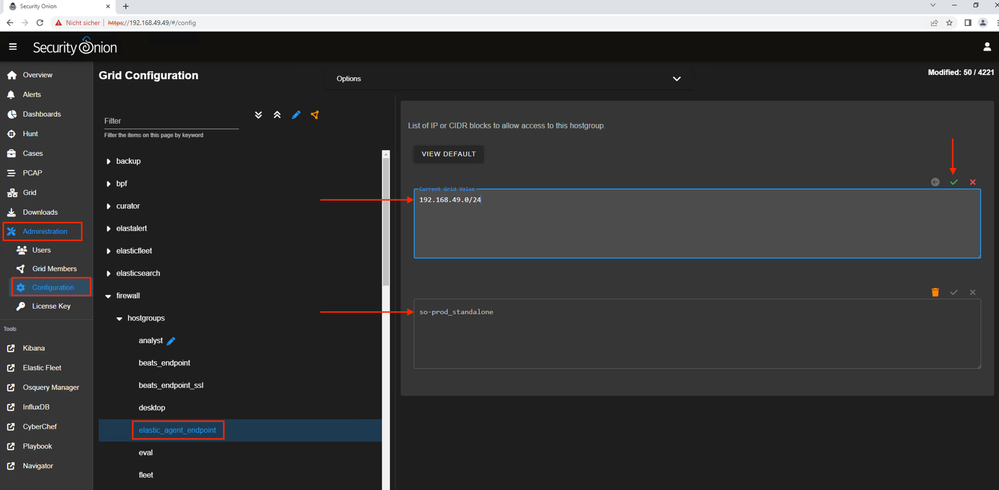
But before we start with the installation of the agent. We first need to adjust the Security Onion firewall settings so that the agent can communicate with the Security Onion.
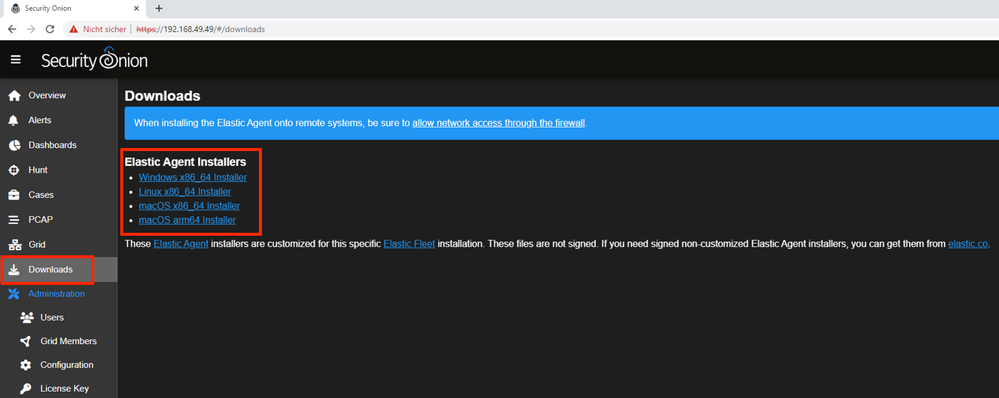
Install the agent (elevated rights)
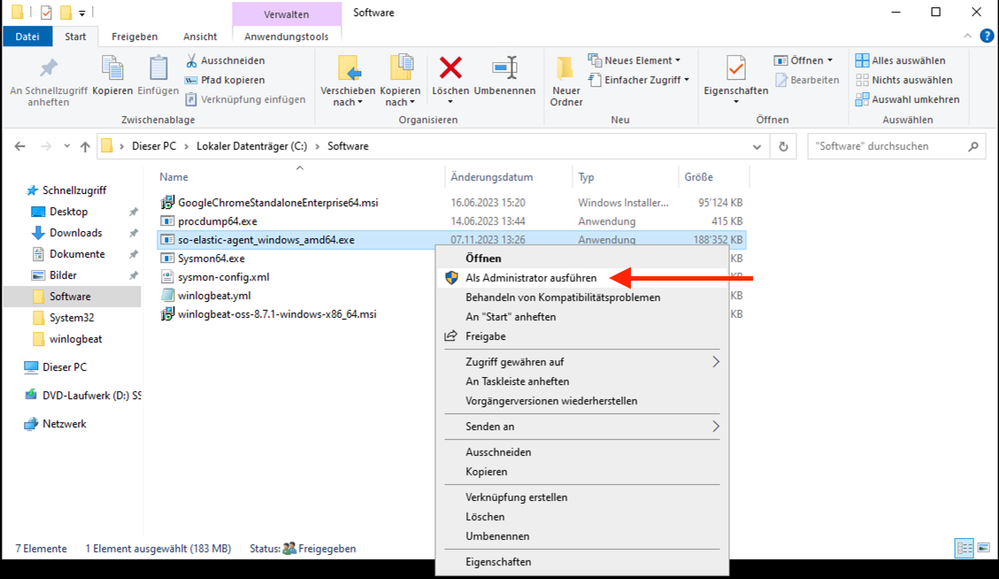
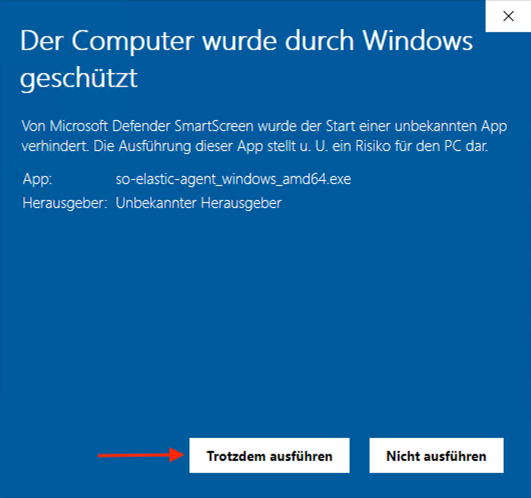
Accept warning and install the agent
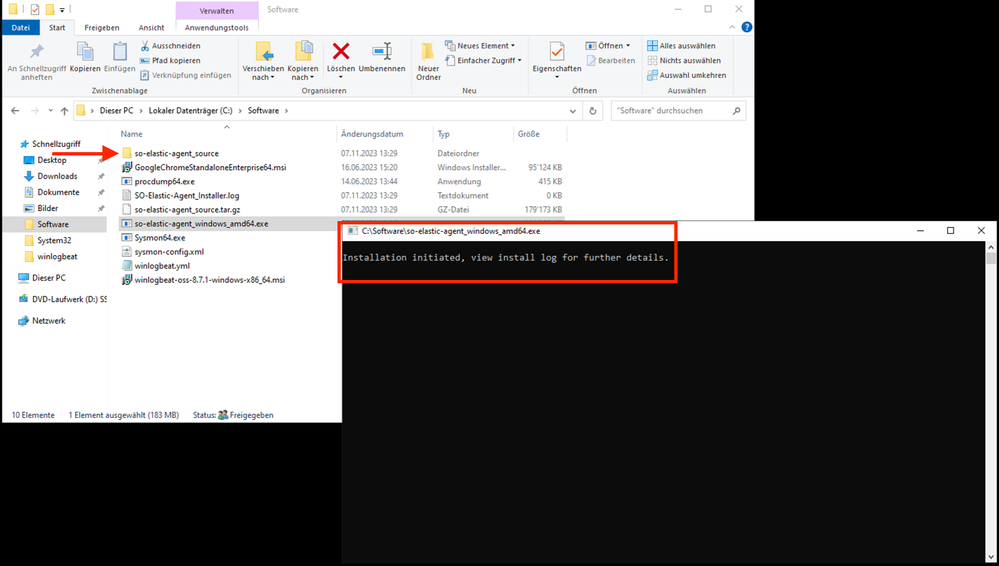
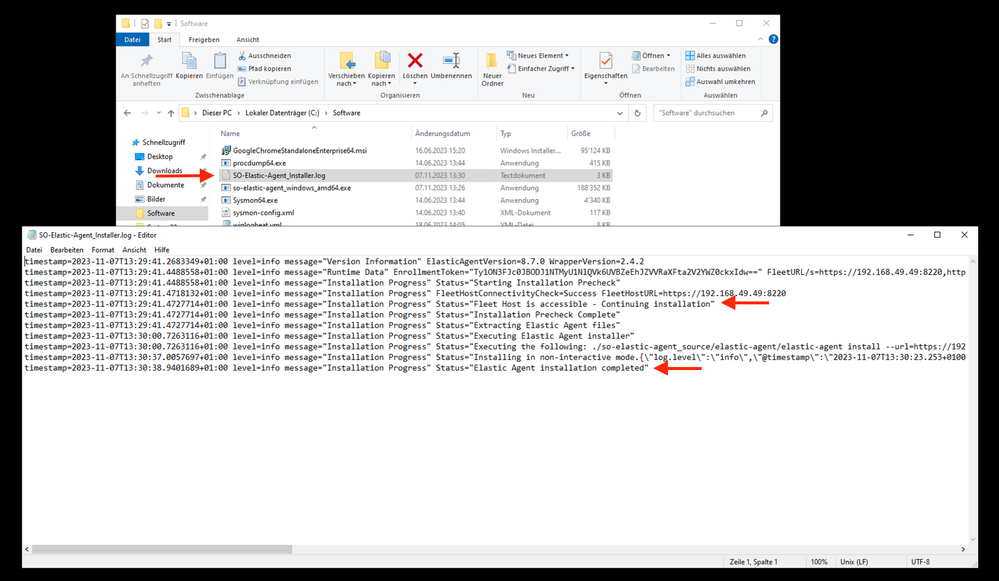
The installation is complete
Now it's time to install Sysmon. You can get the tool directly from the Sysinternals website:
I have downloaded the file Sysmon64.exe. Sysmon is very detailed in its default configuration. But you can define which information is important for you. I have used the following configuration file:
This configuration file is from @SwiftOnSecurity (many thanks here!)
Afterwards the installation is done as follows: sysmon64.exe -i sysmon-config.xml
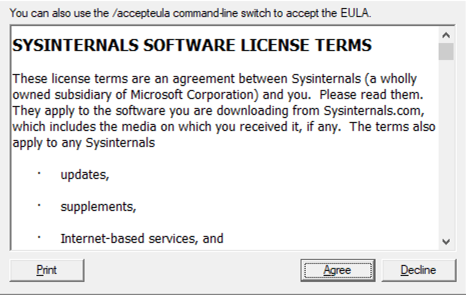
When you access the file for the first time, you still have to accept the license terms.
Install Sysmon on every system where you want to collect additional information. Note: You can automate the installation of the Elastic Agent and Sysmon very well with a group policy object.
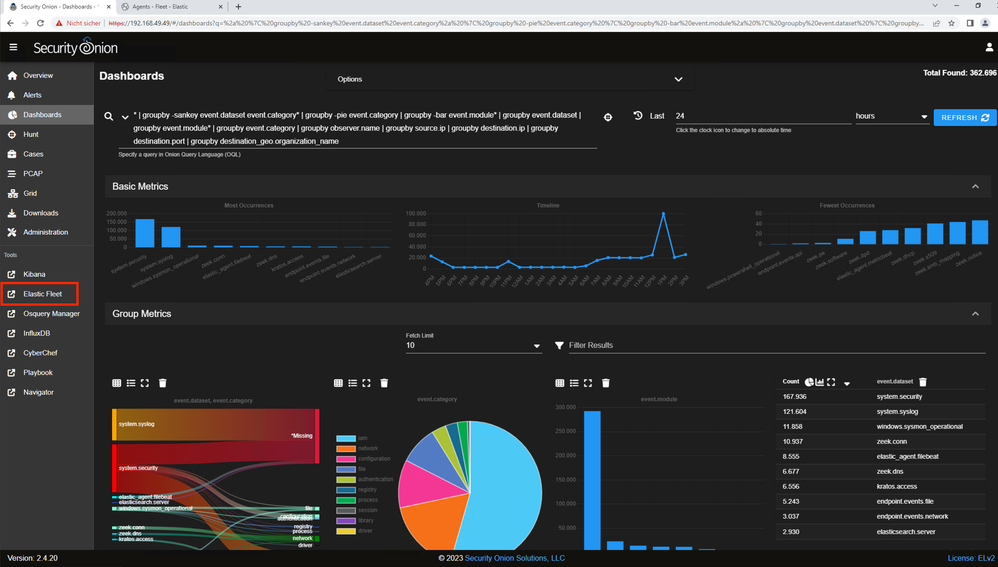
If you have made all preparations you can now call the URL to your Security Onion (as defined by you during the installation) and check if the information has arrived.
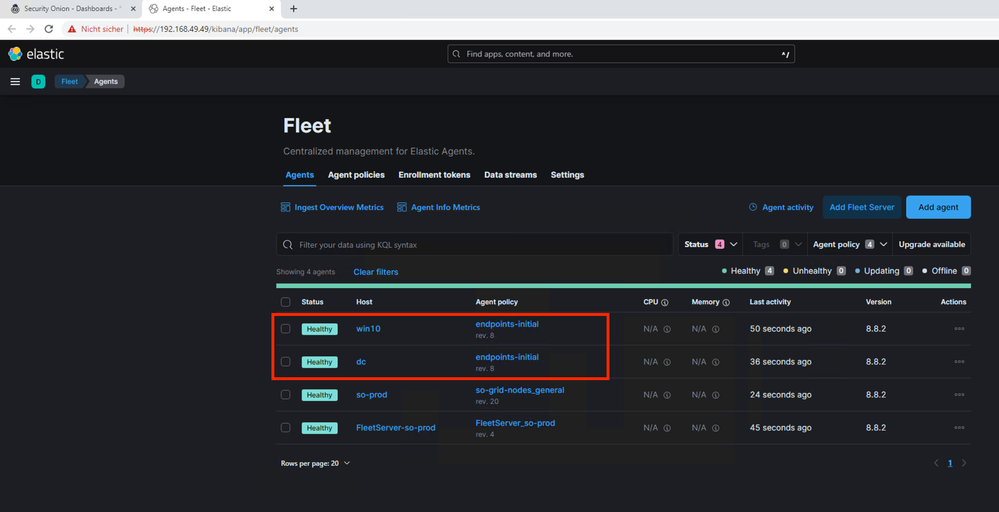
All systems with the Fleet Agents
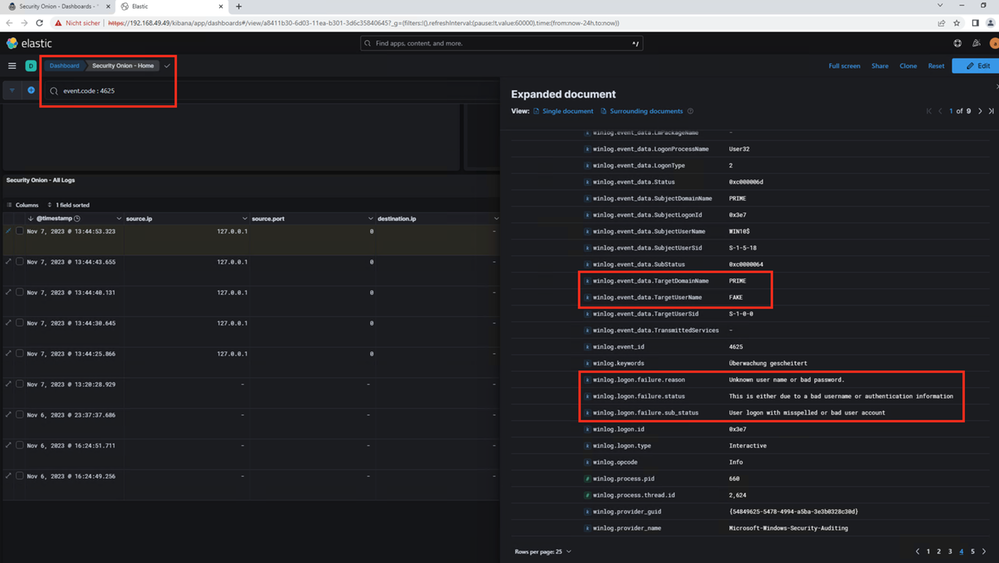
Here is an example of an advanced hunt!
I realize that this was not necessarily spectacular. It was simply important for me to share my experience with you. Nevertheless, I hope that this article was helpful. Thank you for taking the time to read the article.
Best regards, Tom Wechsler
P.S. All scripts (#PowerShell, Azure CLI, #Terraform, #ARM) that I use can be found on GitHub! https://github.com/tomwechsler