Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Windows
- Windows Blog Archive
- Sony’s Rootkit: First 4 Internet Responds
Sony’s Rootkit: First 4 Internet Responds
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Jun 26 2019 11:22 PM
5,584
Views
Jun 26 2019
11:22 PM
Jun 26 2019
11:22 PM
First published on TechNet on Nov 06, 2005
First 4 Internet , the company that implements Sony’s Digital Rights Management (DRM) software that includes a rootkit, has responded to my last post, More on Sony: Dangerous Decloaking Patch, EULAs and Phoning Home . They rebut four of the points I raise in the post. Their first statement relates to my assertion that Sony’s player contacts Sony’s web site each time it runs and sends the site an ID associated with the CD the user is playing:
The player has a standard rotating banner that connects the user to additional content (e.g. provides a link to the artist web site). The player simply looks online to see if another banner is available for rotation. The communication is one-way in that a banner is simply retrieved from the server if available. No information is ever fed back or collected about the consumer or their activities.
I speculated that the player sends Sony’s web site a CD identifier as part of a check to see if new song lyrics or artwork was available, which they essentially confirm. Their claim that the communication is “one way” from Sony’s web site is false, however, since Sony can make a record of each time their player is used to play a CD, which CD is played, and what computer is playing the CD. If they’ve configured standard Web server logging then they are doing that. As I stated earlier, I doubt Sony is using this information to track user behavior, but the information allows them to do so. In any case, First 4 Internet cannot claim what Sony is or is not doing with the information since they do not control those servers, and the First 4 Internet response fails to address the fact that the End User License Agreement (EULA) and Sony executives either make no mention of the “phone home” behavior or explicitly deny it .
Another point that I made in the post is that the decloaking patch that Sony has made available weighs in at a relatively large 3.5 MB because it not only removes the rootkit, it also replaces most of the DRM files with updated versions. First 4 Internet responded with this:
In addition to removing the cloaking, Service Pack 2 includes all fixes from the earlier Service Pack 1 update. In order to ensure a secure installation, Service Pack 2 includes the newest version of all DRM components, hence the large file size for the patch. We have updated the language on our web site to be clearer on this point.
It’s not clear to me what they mean by “a secure installation”, but like most of the disclosure in this story, they’ve acknowledged the updating nature of the patch only after someone else has disclosed it first. What’s also lost in their response is that Sony DRM users not following this story as it develops have no way of knowing that there’s a patch available or that they even have software installed that requires a patch.
Further, Sony’s patch is dangerous because the way that it removes the cloak could crash Windows. I discussed the flaw in the patch’s decloaking method in the first post and again in the last one (I also provide a simple way for users to remove the cloak safely), yet First 4 Internet refuses to recognize it. They contest my claim in their comment:
This is pure conjecture. F4I is using standard Windows commands (net stop) to stop their driver. Nothing more.
While the probability of a crash is relatively small, its not “pure conjecture”, but fundamental to multithreaded programming concepts. Anyone that writes Windows device driver code must have a firm grasp of these concepts or they can easily introduce bugs and security holes into Windows. Here’s one of many scenarios that will lead to a crash when the patch decloaks Sony’s rootkit:
As further evidence of this, I’ve performed further testing of the Aries.sys driver using a program I wrote, NTCrash2 , and found that Aries.sys fails to perform basic checks on the data passed to it by applications. NTCrash2 passes randomly-generated invalid data to Windows APIs and on a stock Windows system simply receives error codes from the APIs. However, when NTCrash2 runs on a system that has the Sony rootkit installed Windows crashes. Here’s an example Windows blue screen that identifies Aries.sys as the cause of a crash that occurred while NTCrash2 ran:
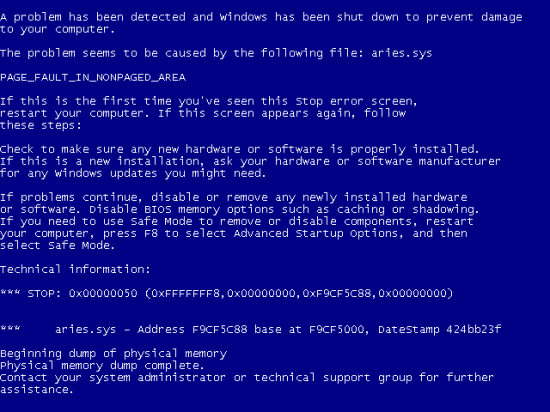
Besides demonstrating the ineptitude of the First 4 Internet programmers, this flaw highlights my message that rootkits create reliability risks in addition to security risks. Because the software package that installed the rootkit is hidden when Windows is running (in this case Sony’s DRM software), and even if exposed not clearly identified, if an application triggers one of Aries.sys’s bugs a user would have no way of associating the driver responsible for the resulting crash with any software package they have installed on their system. The user would therefore be unable to conclusively diagnose the cause of the crash, check to see if they have the most recent version of the driver or of uninstalling the driver.
First 4 Internet and Sony also continue to argue that the rootkit poses no security vulnerability, repeating it in the description of the patch download. Any software that hides files, processes, and registry keys based on a prefix of letters can clearly be used by malicious software.
First 4 Internet’s final rebuttal relates to my complaint that as part of a request to uninstall their DRM software Sony requires you to submit your email address to their marketing lists. First 4 Internet says:
An email address is required in order to send the consumer the uninstall utility. The wording on the web site is the standard Sony BMG corporate privacy policy that is put on all Sony web sites. Sony BMG does nothing with the customer service data (email addresses) other than use them to respond to the consumer.
The Sony privacy policy the comment refers to clearly states that Sony may add a user’s email address to their marketing lists:
Except on sites devoted to particular recording artists, we may share the information we collect from you with our affiliates or send you e-mail promotions and special offers from reputable third parties in whose products and services we think you may have an interest. We may also share your information with reputable third-parties who may contact you directly.
Again, the fact is that most users of Sony’s DRM won’t realize that they even have software that can be uninstalled. Also, the comment does not explain why Sony won’t simply make the uninstaller available as a freely accessible download like they do the patch, nor why users have to submit two requests for the uninstaller and then wait for further instructions to be emailed (I still have not received the uninstaller). The only motivation I can see for this is that Sony hopes you’ll give up somewhere in the process and leave their DRM software on your system. I’ve seen similar strategies used by adware programs that make it difficult, but not impossible, for you to remove them.
Instead of admitting fault for installing a rootkit and installing it without proper disclosure, both Sony and First 4 Internet claim innocence. By not coming clean they are making clear to any potential customers that they are a not only technically incompetent, but also dishonest.
More on the story in Sony: You don't reeeeaaaally want to uninstall, do you?
Originally by Mark Russinovich on 11/6/2005 7:29:00 PM
Migrated from original Sysinternals.com/Blog
# re: Sony’s Rootkit: First 4 Internet Responds
damn, if they knew that their rootkit can crash they could just disable the driver and ask the user to reboot (not nice, but safe)
11/7/2005 6:44:00 AM by Diego Calleja
# re: Sony’s Rootkit: First 4 Internet Responds
The responses of both First 4 and Sony only confirm what many of us have suspected ever since Mark broke the news of this rootkit, that:
a) Sony and First 4 must think that this blog and its readers comprise a negligible portion of the market,
b) that by offering de-cloaking and the above rebuttals they can minimise any potential damage the story will have on those who aren't necessarily versed in the technical theory underlying much of our concerns, and
c) further 'rootkit' anti-piracy countermeasures are obviously something they are determined to push ahead with (as a valid practice), despite our concerns about their abilities to tinker with our systems.
It really does not bode well for the future of consumer computing when supposedly reputable companies are blurring the lines between virus propagation and product license protection. Okay, so the kit doesn't self propagate. I'll bet if it hadn't been for this blog we would be seeing instances of $sys$ prefixed trojans in pretty sharp fashion. And though he doesn't explicitly say in the article, the blue screen of death is synonimous with buffer overruns. So in this instance there may not exactly be an exploitable buffer, but how are we supposed to know whether there will be one in the future if we are in the dark about what processes are being introduced into our machines, at what level of privelege, and competence of design.
Nice hacking Mark. Ironically, this Sony/First4 blog has evidenced some rather Linux-style open source solidarity. Surely you pay the cost of end-user agreements so that your proprietary vendor ensures that this kind of thing shouldn't need to happen at the grass roots level? And further, for such a low level of device driver access (that this rootkit needs to install) you would expect some kind of OS warning or administrative password prompt? What do Microsoft have to say on the issue? They've been terribly quiet!
11/7/2005 7:25:00 AM by ruy_lopez
# re: Sony’s Rootkit: First 4 Internet Responds
I'm just some network admin. Just a couple hundred users, a few servers, nohting special. I've encouraged users to bring CD's in to work if they want to listen to music 'cause I don't really have the bandwidth to support a lot of streaming content. Silly me.
I don't have 1/4 of Russinovich's brains. If I find rootkits and spyware and ADS junk on my network, I go after it with a chainsaw, not a scalpel. It's the best I can do. I wish I had the time and IQ to research everything, set up test beds, etc. I don't. If I see it, I have to assume it's malicious and whack it.
Looks like if I try this with the Sony rootkit I'm pretty likely to wreck the CD drives. Which I'll have to spend half a day trying to fix to keep "Those-Who-Must-Not-Be-Annoyed"
happy.
Sony's uninstall routine ain't gonna work for me. Maybe or maybe not it'll work for an individual, but what am I supposed to do about a network with a bunch of infected (there, I've said it) machines? I need Sony to at least post the uninstaller at a website so I can go from station to station, detect it, and get rid of it at a single pass. I don't even have time for that, but what else am I gonna do?
11/7/2005 7:40:00 AM by jimnoble
# re: Sony’s Rootkit: First 4 Internet Responds
Hi,
I am a belgian lawyer specialised in ICT law and I would like to analyse more in depth this story.
Could you post the Sony's licence which appears when you install the proprietary program of Sony ?
Thanks.
11/7/2005 8:09:00 AM by Hydre
# re: Sony’s Rootkit: First 4 Internet Responds
Hydre - the EULA provided when Mark first installed the DRM "application" is linked to from within the first in this series of articles ( http://www.sysinternals.com/blog/2005/10/sony-rootkits-and-digital-rights.html ).
11/7/2005 8:13:00 AM by Wes
# re: Sony’s Rootkit: First 4 Internet Responds
I have been following this story since it hit betanews a few days ago. I must say first off that Mark you have done a tremendous job disecting this whole issue.
First I have to comment on the whole crash issue brought up by Mark which First4 has refuted. I am not going to sit here and say that I have written or fooled around with drivers before because I havent, however the FIRST rule that I learned in Multithreading in just a single app is that any and all threads that are accessing any piece of data in memory must be informed if said memory changes address. It is basic Multithreading programming. Heck it is basic pointers.
Anyhow, as far as the issue as a whole. I find it very disturbing to see this, and even more disturbing that the big news Corps are not covering this story heavily, since it is a clear case of invasion of privacy by a huge Corporation like Sony. However it doesnt surprise me since most of the news conglomerants are run by these companies.
Has anyone tried contacting Microsoft to see their response to this issue? Microsoft right now is advertising their focus on security for their current and future Operating Systems. It is basically their selling point right now.
The implications of "Legit" bussinesses distributing cloacking software unkowingly to consumers opens up a Pandoras box that could cause some serious trouble. How long before we see a virus or trojan out there that exploits this flaw?
11/7/2005 8:57:00 AM by Jedite
# re: Sony’s Rootkit: First 4 Internet Responds
Mark, again some stellar work. I'm wondering whether either Sony or F4I came back with anything about why they feel they need to "lie" to users by obfuscating the names of their files and software (for instance calling the aries driver "Network control manager" when it has nothing to do with networking)? I'd imagine that so far they have refrained from touching that, but I think long term we want to get them to address that too.
Thanks for all the great work on this.
11/7/2005 9:07:00 AM by Jerry Ham
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Thank you for all the great work on this very real issue. I hate to say it but it begs the questions "What else is out there?".
I recall working for a/the software company that sent out a beta to it's work force for testing. The beta had a giant bug due to a rootkit that reported back to the security department to see if anyone was making illegal copies. And that was from a company the should understand Windows drivers, hehe.
People think of their personal machines as their personal space without realizing how much the EULA's for the multitude of companies you are forced to accept opens your system and your life to their prying eyes.
Thank you again!
11/7/2005 9:17:00 AM by Adam Gates
# re: Sony’s Rootkit: First 4 Internet Responds
One underestimated way of preventing things to get installed on your computer, is to run without admin rights. The problem is that not all programs handle this well.
Does this mean you cannot play CDs with Sony's "rootkit" DRM if you are not an admin?
11/7/2005 9:26:00 AM by Thriol
# re: Sony’s Rootkit: First 4 Internet Responds
This may have already been addressed in the comments to the earlier stories
Am I right in thinking that if Autorun is disabled, this DRM never gets installed? (so long as you don't 'run' the CD)
These disks are intrinsically unprotected, and depend upon the DRM rootkit that infects your computer to protect them. So am I right thinking that non-windows systems are essentially immune?
11/7/2005 9:54:00 AM by Symphonic
# re: Sony’s Rootkit: First 4 Internet Responds
I was directed to a page to fill in my email address. However, the page required IE and you needed to let them install an Active-X control, which I refused after this fiasco. I am still arguing it with their support center.
11/7/2005 10:03:00 AM by Marcus
# re: Sony’s Rootkit: First 4 Internet Responds
I just sent an email to Sony telling them I'm putting on hold buying any Sony hardware or downloading and Sony software.
Can't take these risks until they get their act together.
11/7/2005 10:07:00 AM by worldcitizen
# re: Sony’s Rootkit: First 4 Internet Responds
Excellent work, Mark.
I've been following this discussion from the beginning. As a part of my job, I am sysadmin running less than 50 computers (with Windows XP and some Windows 2000) and several servers (Windows 2003). Although the number of computers is small, I need to spend some time in order to keep them all clean and safe; so I check this websiteas well as others to be as informed as possible (although this is the first time that I write a comment) .
This Sony's Rootkit just makes my work harder. And what's worse, it doesn't make any good to legal users that inadvertently install it. Having this program installed calling home is a security risk that no sysadmin can take, period. No matter how you call it: rootkit, DRM, etc. It opens a door in an already difficult to secure OS.
I am wondering if setting up users with limited accounts will prevent this rootkit from being installed. Not every user could be set this way, because some (poorly written) programs require you to have admin permissions to work; but at least would make the computer less vulnerable.
Thanks.
11/7/2005 10:19:00 AM by igalan
# re: Sony’s Rootkit: First 4 Internet Responds
Sony is just digging themselves a deeper hole by not admitting their guilt.
I'm sure that if asked politely most people would not mind installing some DRM software.
These covert ops however won't lead to anything good. Even being a fairly experienced sys-admin, up to just now, I would have never imagined that an audio CD could lead to blue screens.
11/7/2005 10:23:00 AM by Dmitriy
# re: Sony’s Rootkit: First 4 Internet Responds
"So am I right thinking that non-windows systems are essentially immune?"
# posted by Symphonic : 9:54 AM, November 07, 2005
This is easy to test: just
download a liveCD of knoppix and test your hipotese.
http://www.knopper.net/knoppix-mirrors/
11/7/2005 10:27:00 AM by zeh
# re: Sony’s Rootkit: First 4 Internet Responds
It is amazing that Sony can get away with doing things like this. Let's hope that these blogs and articles embarass them enough to stop this kind of behavior.
Didn't they used to have some nice products? I got burned on my minidisc player -- good idea, good construction, but the thing wasn't much more than a walkman -- by design. They could have done so much more, with just a bit of extra firmware.
11/7/2005 10:30:00 AM by Drew from Zhrodague
# re: Sony’s Rootkit: First 4 Internet Responds
If Sony was smart (insert joke here...) they would contact Dr. Russinovich and hire him to dig them out of this mess.
Personally I would feel MUCH more confident about the solution if I knew that it was written by Mark.
This would also be a nice 'mea culpa' for Sony. A little humility would be welcome in my opinion at this stage of the comedy of errors we've all witnessed.
11/7/2005 10:36:00 AM by ThisAJoke
# re: Sony’s Rootkit: First 4 Internet Responds
Hello, I found while searching on Microsoft.com for "first 4 internet" a link to a story posted at Cnet news :
http://news.com.com/New+CD+copy-lock+technology+nears+market/2100-1027_3-5492395.html
Sony and First 4 internet are both mentioned.
11/7/2005 10:37:00 AM by Bob-NL
# re: Sony’s Rootkit: First 4 Internet Responds
Isn't the CD still standard (redbook) CD Audio? If so, wouldn't you just put in the cd, cancel or block the autoinstall (shift) then just play with Media Player or other cd audio player? Perhaps with the older Media Player (start->run->mplay32->device->CD Audio)?
I don't have any F4I protected CDs to test this out.
11/7/2005 10:45:00 AM by halfdone
# re: Sony’s Rootkit: First 4 Internet Responds
Bob,
It is possible to circumvent most of those poorly written programs with a time and experimentation. Many of these programs 'need' admin access so they can modify data in their program folder and in specific registry keys. You can use detection software, such as regmon / filemon, to see what they access and give users modify permissions to only those things.
The upfront cost in time will save you much after your users are locked down.
11/7/2005 10:48:00 AM by McCitizen
# re: Sony’s Rootkit: First 4 Internet Responds
poor Sony programmers, they never thought a guy like Mark would find out (and disect in this way) about this stuff
now Sony is in deep trouble, messing up with the wrong guy
11/7/2005 10:53:00 AM by BlackTigerX
# re: Sony’s Rootkit: First 4 Internet Responds
Bob,
With a little time you could probably tame the poorly written programs as well. Often these programs 'require' admin rights so they can update specific files or registry keys. If you track what they access, say using regmon and filemon, you can give 'Domain Users' modify rights to the specific resources. Then they can run the programs and you can worry less about viruses and spyware.
11/7/2005 10:54:00 AM by McCitizen
# re: Sony’s Rootkit: First 4 Internet Responds
So it also forces you to install Windows SP2? I don't use that and don't intend to.
11/7/2005 11:07:00 AM by Per
# re: Sony’s Rootkit: First 4 Internet Responds
Thanks for keeping up the pressure, Mark. It strikes me as funny that it's more important to Sony and the rest of the RIAA crowd to stop the potential of piracy than it is to keep everyone who reads this as a customer. Which is going to cost them more in the long run, keeping me from stealing a CD, or guaranteeing that I'll never buy another Sony product?
11/7/2005 11:18:00 AM by Martin McKeay
# re: Sony’s Rootkit: First 4 Internet Responds
Answer to Limited User Account question: The Sony DRM player requires administrative rights to install. Tested on Windows 2000 on virtual machine. A regular limited user could not install the player and the DRM rootkit. The software presented a prompt saying that administrative rights were required. I did not test this as a "power user".
11/7/2005 11:48:00 AM by Hooper3.0
# re: Sony’s Rootkit: First 4 Internet Responds
I've been following this with great interest as my Granddaughter had asked me to look @ a Sony-BMG CD that she'd recently purchased (I got the CD just a day or two before this story broke).
I hadn't had a chance to look @ the CD before the story broke and read Mark's initial analysis closely. This remindes me of a copy protection scheme I discoverd after loading a new game.... The wonderful folk @ Starforce.com use a copy protection scheme that inserts 'daisy-chained' drivers in your IDE channel and the ATAPI code. This caused me no end of problems.... overall a 10% reduction in system operation, stuttering in games OTHER THAN the GTR racing game that installed the scheme, and loss of functionallity of legally purchased cd duplication software (Nero and CloneCD, and yes there ARE legal uses for both!). Starforce DOES supply a removal tool, but the version that I had (current version from the starforce.com site at the time I was looking) didn't remove the files from the "driver cache" so I STILL decided to go thru a complete re-install of the O/S after removing the software... I, at the time, decided to just NOT use the game (probably should have been more agressive, but a $40 game just isn't worth the hassles... I just wrote off the company(s) involved, 10tacle studios and SimBin...)... I've not yet gone over to their house to remove the root-kit, but will be doing so soon...
While I agree, companies have the legal right to protect their Intellectual Property, the metods used by Sony BMG and by 10tacle Studios and SimBin go too far... I'm a CISSP (Certified Information Systems Security Professional) and work with IP issues on a daily basis.. so I do understand the issues involved..
11/7/2005 11:48:00 AM by NtwkGestapo
# re: Sony’s Rootkit: First 4 Internet Responds
For those of you who are Sony stockholders, let them know how you feel about how they are representing your money and write Investor Relations:
http://www.sony.net/SonyInfo/IR/info/contact/index.html
11/7/2005 11:50:00 AM by Jason
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Great job! You have put the spotlight on Sony and their unethical Machiavellian business tactics. I really hope to see them get the book thrown at them. However, I think you are being too nice to them.
In your blog you write:
"I checked the EULA and saw no mention of the fact that I was agreeing to have software put on my system that I couldn't uninstall. Now I was mad."
"When I logged in again I discovered that the CD drive was missing from Explorer. Deleting the drivers had disabled the CD. Now I was really mad."
Ok, so you say you are "really mad".. then you write the following and here is where I think you are being WAY too nice to Sony:
"The media has done a great job of publicizing this story, which has implications that extend beyond DRM to software EULAs and disclosure, and I hope that the awareness they’re creating will result in Congressional action. Both the software industry and consumers need laws that will clearly draw lines around acceptable behaviors."
The problem is the mentality behind their actions. As consumers we want and need such laws as you mention. However, we shouldn't need these laws because businesses shouldn't have the desire to screw over their consumer base. This is just one example of corporate american greed that disgusts me. The problem is that they are by definition, being an american capitalist business, are purely in the "business" of making money... not just making money, but their goal is to make as much money as possible to increase the value of their stocks as highly as possible. This is the recipe for disaster. It's sad that we have to act retroactively on this. The business model allows for this behavior which is obviously unethical from the perspective of the consumer, however to the business they feel they are within their right to protect their income and revenue which they believe is under threat of piracy. Their entire mentality is backwards. The reality is that they are screwing everybody over so that they can make as much money as possible. I don't believe that "congressional action", essentially making new laws to limit what Sony can do, is enough. They will just come up with something else. What needs to happen is that they need to be sued and slammed with a HUGE punitive fine.. when I say huge, the only thing that Sony cares about is money, so with that in mind, they need the equivalent punishment as getting roundhouse kicked in the face repeatedly by Bruce Lee about 20 times, I don't know how many millions of dollars that needs to be, but that is what needs to happen.. the next question is, who gets that money? The sad thing is that attorneys will get 30 to 40% of the money. The money should be given to consumers of Sony products. What can consumers do in the mean time? Boycott Sony's products, this means don't buy Sony Televisions, DVD players, video cameras, digital cameras, etc. There are other brands that are better anyway. I was going to buy a Sony Digital Camera, but now I'm going to buy a Canon instead. I was going to buy a 65" Sony HDTV, but now I'll buy either the Mitsubishi 1080p or Toshiba instead. I have been a huge Sony fan all of my life and have recommended to dozens of people their products.. now I'm disgusted that I have contributed to a company that would resort to this sort of behavior. I think of all of the Sony VAIO laptops I have recommended in the past.. now I will be recommending Toshiba instead.
Also,Mark, could you please write a very simple step by step instruction list for removing this root kit. Or better yet, if you could please write an uninstaller or work with Adaware or Spybot or Microsoft Antispyware so that they can update their software to remove this infection. It would be great if I could have a simple .exe file that I could put in the login script that scans and removes this garbage and outputs a log file to a network drive.. Thanks again!
11/7/2005 11:59:00 AM by miamibeachman
# re: Sony’s Rootkit: First 4 Internet Responds
I hope this is true report: Sony to be sued in Italy:
http://theinquirer.net/?article=27508
11/7/2005 12:01:00 PM by Enough
# re: Sony’s Rootkit: First 4 Internet Responds
"An email address is required in order to send the consumer the uninstall utility."
You clearly already showed that the utility is available online, and does not need to be emailed. :|
11/7/2005 12:36:00 PM by nozzlehead
# re: Sony’s Rootkit: First 4 Internet Responds
I think that the scariest part of this whole fiasco is that now Mr. Russinovich is liable under the DMCA (under the Circumvention provisions - a prohibition on the removal of copyright management information (CMI) [1202(b)]). I would suggest that he consult with his attorneys forthwith before those A-Holes at Sony file charges.
11/7/2005 12:49:00 PM by xgwpc
# re: Sony’s Rootkit: First 4 Internet Responds
The worst and most stupid thing SONY can do is firing charges against Mark, that would bring this whole mess and bad publicity to a whole new level.
SONY should:
1. publish a uninstaller that can complete remove the rootkit;
2. dismiss F4I and then blame them for this;
3. buy this website and hire Mark.
11/7/2005 1:03:00 PM by dan
# re: Sony’s Rootkit: First 4 Internet Responds
This anti-consumer attitude is even more obvious in the upcoming HD-DVD/Blu-Ray war. Both formats allow the content creators to not only disable all copies of a "compromised" disc, but also brick all players that have been compromised as well.
Buy the latest video and lose the ability to play a portion of your movies or turn your top of the line video player into a brick even if you haven't done anything illegal/unethical/wrong.
http://www.dvdsite.org/faq.html#issue2
Even though I was an early adopter of DVD (Pioneer DVL-700 @ $1200 and over 300 movies), there is no way I'm going to give either format a dime until this attitude changes. The thought of having my equipment disabled because the inevitable happened is unacceptable.
Prime Mover for Blu-ray Disc:
Sir Howard Stringer, Chairman & CEO
Sony Corporation of America
550 Madison Avenue
New York, NY 10022
And/Or
Ryoji Chubachi, President & CEO
Sony Electronics, Inc.
16450 West Bernardo Drive
San Diego, CA 92127
- From the dvdsite.org FAQ
11/7/2005 1:37:00 PM by Altair
# re: Sony’s Rootkit: First 4 Internet Responds
Nozzlehead - you said "You clearly already showed that the utility is available online, and does not need to be emailed"
Not true - Sony only makes the DECLOAKING patch available, which Mark pointed out does this in a manner that can lead to a system crash.
The uninstall for their DRM stuff is NOT downloadable - read Mark's previous blog (and he's still waiting for the uninstall - he requested it last week).
11/7/2005 1:48:00 PM by David Solomon
# re: Sony’s Rootkit: First 4 Internet Responds
Also, the comment does not explain why Sony won’t simply make the uninstaller available as a freely accessible download like they do the patch, nor why users have to submit two requests for the uninstaller and then wait for further instructions to be emailed (I still have not received the uninstaller). The only motivation I can see for this is that Sony hopes you’ll give up somewhere in the process and leave their DRM software on your system.
Has anybody received this uninstaller by email as promised ? because otherwise, there is also an alternative explanation: they do not have such utility and they are frantically rushing to develop one. The email thing could be just a lame way to gather some extra time.
11/7/2005 2:00:00 PM by pennino
# re: Sony’s Rootkit: First 4 Internet Responds
I was looking forward to Blu-Ray, even though Sony championed it... After this story broke, I'm not sure I can trust the format.
It seems like a bone-headed thing for Sony to do. At the time when they are trying to make serious money on their new format, they are stabbing consumers in the back?
Sony didn't make money off of BetaMax, they largely failed (in the US) on MiniDisc, nobody I know ever got behind DTS... now this, just before Hollywood finally chooses sides on the movie format of the future.
Consumers can hit Sony where it hurts by voting with their wallets... don't buy thier "enhanced" music discs, and opt for HD-DVD. I sure won't.
11/7/2005 2:05:00 PM by Lee Jones
# re: Sony’s Rootkit: First 4 Internet Responds
I just took my recently purchased Sony DVD±RW back to Fry's. I didn't need it immediately, but figured it was a good enough deal to keep.
As I was filling in the rebate form, I realized I could make a small contribution to the world by not keeping it.
And the rest is now history...
11/7/2005 2:08:00 PM by RichHubbins
# re: Sony’s Rootkit: First 4 Internet Responds
Sony's insistance that you provide them with your email address (and other information, I gather) before they will grant you access to an uninstall tool is completely unacceptable behaviour. They are holding you and your system hostage until you give over personal information (and it makes not difference if they promise you they will never use it for any other purpose--it's still morally wrong).
11/7/2005 2:14:00 PM by Michael J. Walker
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Thank you for your insight, ability and clarity.
I sure hope this gets picked up more by the mainstream press.
11/7/2005 2:49:00 PM by Guy
# re: Sony’s Rootkit: First 4 Internet Responds
Some peon at First4 is actually trying to argue with Mark Russinovich about how to write a device driver and what is the correct behavior for such a drive? That is just hilarious. Do these guys have any idea who Mark is? Maybe I should get some popcorn.
Up next: A barely literate high school drop-out argues with Shakespeare about how to write sonnets.
11/7/2005 3:10:00 PM by Rhomboid
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/7/2005 3:25:00 PM by Ian
# re: Sony’s Rootkit: First 4 Internet Responds
Regarding coverage by major news agencies...
I noticed a lot of folks thinking it odd that the major news corporations aren't giving this issue a lot of air time. Well let's think about this for a moment:
CNN - AOL/Time/Warner
Foxnews - 20th Century Fox
ABC - Disney
NBC - Universal
CBS - oh, wasn't this Columbia? cant' remember
Now lets look at the members of the RIAA/MPAA...
MPAA:
Disney
Sony
MGM Studios Inc.
Paramount
20th Century Fox
Universal
Warner Bros
RIAA: - too many to list.
http://www.riaa.com/about/members/default.asp
Needless to say, all the major news outlets are well represented. Their not going to rat on their bretherin.
11/7/2005 3:29:00 PM by Ian
# re: Sony’s Rootkit: First 4 Internet Responds
Has anybody received this uninstaller by email as promised ? because otherwise, there is also an alternative explanation: they do not have such utility and they are frantically rushing to develop one. The email thing could be just a lame way to gather some extra time.
Or here's another thought... The development and web teams at Sony are rushing to wait for feedback from their lawyers because their masters that be have threatened certian death with the release of such code and they're all in a tivvy to see if their truely breaking any laws (or atleast any that will cause them significant damage). Ah... but that would be more conspiracy mode kicking in wouldn't it....
11/7/2005 3:34:00 PM by Ian
# re: Sony’s Rootkit: First 4 Internet Responds
In an earlier comment in this blog it was suggested that we, the readers, will do nothing about this problem. I already have taken action.
I've checked my own machines for the rootkit.
I've instructed my wife and children to NOT buy any CD that lacks the CompactDisc labeling. I plan on letting Sony and my local music distributors know of my decision.
I will not be purchasing any Sony audio, video, or computer equipment. I find it amazing that Sony sells digital recording devices. It appears they want to have it both ways...
I've written to the Boston Globe to inquire as to why they have not covered the story.
I've written to the technology writer for the Washington Post to them them for their coverage.
I'm looking for other ideas on how to act. Any ideas?
11/7/2005 3:47:00 PM by Dennis Murphy
# re: Sony’s Rootkit: First 4 Internet Responds
Can I suggest that all this anger with Sony is turned into corporate bruising?
Go to www.karmabanque.com and start a boycott, ecourage the hedge-funders in and go from there...
Enjoy
11/7/2005 3:59:00 PM by BlogOT
# re: Sony’s Rootkit: First 4 Internet Responds
Regarding Ian's comment: Fox News ran this story on their website, and was linked from the top of the front page for a while (not as the main headline, but as one of the several just to the right of that).
Another comment. Sony claims that most users are uninterested in whether their CDs install rootkit software to their computers. But the whole point of the rootkit is to foil people who would attempt to disable/bypass the DRM software, meaning it targets technically savvy people who are interested in preventing rootkit infection.
In other words, most of Sony's customers get punished with rootkit infection even though it has no additional effect on their ability to rip the CD beyond what the DRM provides. Considering them to be within the "audience" for the rootkit, and then claiming that their ignorance forms a sort of democratically-decided consent, is ridiculous.
11/7/2005 4:13:00 PM by Dachannien
# re: Sony’s Rootkit: First 4 Internet Responds
@ Ian
If you post "research", get your facts right, you are not credible with your post.
I just checked Foxnews, they had article on November 3rd.
http://www.foxnews.com/story/0,2933,174334,00.html
11/7/2005 4:15:00 PM by Enough
# re: Sony’s Rootkit: First 4 Internet Responds
The Beeb's(BBC) coverage of this very blog.
http://news.bbc.co.uk/2/hi/technology/4413856.stm
11/7/2005 4:15:00 PM by Sharpy
# re: Sony’s Rootkit: First 4 Internet Responds
ABC News has picke this up also
http://abcnews.go.com/Technology/ZDM/story?id=1289711
11/7/2005 4:27:00 PM by goober
# re: Sony’s Rootkit: First 4 Internet Responds
So if I pirate the music I am safe but if I pay for it I am risking my system? Leaves little choice doesn't it sony?
11/7/2005 5:20:00 PM by Shaedo
# re: Sony’s Rootkit: First 4 Internet Responds
A quick question from a non-MS Windows user following this mess: Does this mean that MS Windows based machines with the Sony rootkit installed cannot be cleaned up if they don't have internet access at this time?
11/7/2005 5:25:00 PM by Tomas
# re: Sony’s Rootkit: First 4 Internet Responds
Thank you for continuing to update your blog, Mark.
To quote the good guy:
"There's no way to ensure that you have up-to-date security patches for software you don't know you have and there's no way to remove, update or even identify hidden software that's crashing your computer"
An extract from the BBC's commentry on the bad guys:
"First 4 Internet, which made the copy protection system for Sony BMG, said that it would work with anti-virus companies to ensure that false alarms were not triggered by its software.
Sony says that users have been adequately warned about the copy protection software in the licence agreement and had been told that it used proprietary software to play the CD."
http://news.bbc.co.uk/2/hi/technology/4413856.stm
---
Is everyone waiting for someone else to make the first move in regards to which Antivirus/malware vendor will sig Sony's rootkit?
Mark has already demonstrated that this rootkit is a vulnerability in that it's been proven to be exploitable. There are no shortage of threats on the Internet today plus you could argue that the rootkit itself is a threat.
Mark: If Sony contacted you asking you to update RKR to ignore their "product", how would you respond?
Are you in contact with anyone on the (newly renamed) "Windows Defender" team? Are they considering blocking Sony's rootkit?
I just watched your Microsoft Technet presentation on Malware from a few months back. Great stuff. You're the man.
--
More links:
They're trying to /. this site again:
http://games.slashdot.org/games/05/11/07/1221209.shtml?tid=233&tid=207&tid=10
/. article also provided a Google translated link to the Italian lawsuit
http://translate.google.com/translate?u=http%3A%2F%2Fwww.lastknight.com%2F2005%2F11%2F07%2Fsony-bgm-...
11/7/2005 5:25:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
I don't think those idiots have a cleaning tool developed yet. If they're smart- they'll have Mark scrutinize it before setting off a new wave of BSoDs and disappearing CDROMs.
Or maybe they have they have their dodgy uninstall ready to go (or so they think) but they are waiting on the legal team to finish the soul stealing license agreement to go with it.
11/7/2005 5:33:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
Mark, I do believe you've started a major backlash against DRM.
11/7/2005 5:51:00 PM by anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/7/2005 6:02:00 PM by Spider Rice
# re: Sony’s Rootkit: First 4 Internet Responds
I was looking forward to buying a shinny new PS3 when they get release, but now Sony can go fornicate themselfs with a pole for all i care. They aint getting any more sales out of me!
Only problem being the alturnative is Micro$oft. Looks like the 'Revoltion' and it's wacky looking controler is the go!
11/7/2005 6:07:00 PM by Spider Rice
# re: Sony’s Rootkit: First 4 Internet Responds
I am willing to BET that Sony will never release a FULL un-installer for the PUBLIC here is why.
Sony is using these CD's as a LEGAL DRM Shield test, more below:
Just Wondered if others thought these same thoughts?
I am sure as some have already stated, that this Sony Mess, is not considered a "Big Deal" but are we forgetting the possible Fallout from this?
It could go 2 ways:
No Legal Action Or Change Of Laws Because Of This
1. Others can and will use similar techniques and claim they were protecting their software and not just for Media related software, but for everything!
2. Many folks in these forums, who already are kind enough to volunteer their time to help others will be swamped with very complicated removal instructions.
3. When more than one of these type protection mechanisms is installed on a system, it will be a house of cards to determine, which one to un-install first. There will be NO right way, it will be based on the order the malware was installed, as well as how many of these you are infected with.
4. More systems than ever before will become infected with malware because the mechanism used is now provided by companies providing commercial software which have much more access to the general public and in many different forms than the current malware producers, including hackers.
5. Most people might not even be able to pre-scan the software prior to being installed because it may be compressed or encrypted in such a way that you cannot see what it will look like until fully installed. This would mean you would need to take the chance to install it, and check later.
6. Exploits of holes in these protection methods will allow non-seasoned hackers to take advantage of such said holes with no liability as well. Since in some cases what they did might not have been possible without the commercial companies software.
7. As stated on Mark's Blog, if Sony's software stands as is, as legitimate DRM. Then any company that makes software that fixes the problems caused by this Root Kit exploit could be in violation of DRM laws and face serious consequences. For example, Microsoft could not legally create a patch that prevents this type of behavior as a security update.
If ANY software author creates software which contains media files, they could claim the cloaking portion was to protect their Media files under DRM, which would make it illegal to remove their cloaking as well.
This would include currently known spyware as well. Which for all practical purposes would now restrict automated removal, which is now allowed, simply by using DRM as a shield by including Media files of any type during their installation process.
Legal Action Or Change Of Laws Because Of This
1. Finally, some sanity comes to the rights of ownership of computer systems, and the ability of International Companies to Join the malware industry will be at least hindered, if not stopped.
2. Companies that could supply automated methods attempting to remove this type of software from systems will not need to fear litigation because the creators of the software use DRM as their shield.
Very Dangerous Precedent Exists NOW!
It matters very little if this was oversight, malice or accidental. Equally, it matters just as little that a ActiveX method of removal is offered because it does NOT determine that this method of DRM is wrong.
Therefore it is tying the hands of any entity which would attempt to offer any automated process to remove this or any future derivative of these types of methodologies because it has been used as an excepted method for DRM.
The proof itself that Sony was NOT compelled to remove this method of DRM as a mandate, would itself prove this.
We are setting a very dangerous precedent for other companies, and/or individuals who create software.
This actually could be the most important precedent set since the personal computer was created if we are going to allow ANY entity to continue to do this in the future.
We will have almost removed the purpose of EULA and in fact created the "Act Of Downloading" ANYTHING removes the liability of the creator(s) of the software downloaded itself.
I hope people don't think I am going over-board here, because I think after all is said and done, there are many companies that are waiting in the wings to see how this is resolved, and that this moment based on how it all goes down, could be the turning-point of what rights the computer owner has, once they have accepted ANY download.
There are many more possible BAD things that could come out of this, I just tried to think of some major ones.
Sony, will NEVER release a PUBLIC un-installer that removes ALL of this, without legal action requiring them to do so.
This is a Cheap DRM shield test testing their legal rights, and I would also BET they WILL threaten ANY company that attempts to create an automated method to remove this from systems using DRM as their shield ;-), watch..
They have already INFORMED virus scanning compaines on how to not FLAG this as a false-positive get it?
See where they are going, they will SUE anyone who tries to remove it on a mass scale!
Comments, Please?
11/7/2005 6:40:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
This is only one thing that the Sony Software Developers have rushed to delivery. Before this story broke I had purchased a Sony Network Walkman, an MP3 Player. They shipped a program called Sonic Stage with the unit.
Now I have a massive collection of MP3s that I have legally ripped from CDs I own. (I’ve always had certain apprehensions against buying MP3's online, and not actually owning a product.) The Sonic Stage software was some of the worst software I’ve dealt with, ever. It crashed every time I ever tried to use it and ended up searching the web for a month trying to find a program that would enable me to actually use this $200 dollar piece of equipment I had purchased. I eventually found a program; however that’s not the point. The point is that Sony’s Software division is obviously either lacking the necessary knowledge of how to write programs, or they’re rushed so much so that they cant even finish what they were sent to do.
I personally will never buy another Sony product ever again. I had been a huge fan of Sony, and had been thoroughly looking forward to the PS3. However no longer will I be buying one of these. Sony has seriously screwed up, and no matter what kind of bad publicity they get, they will still continue to screw up.
The only thing we can do is simply stop buying their products and hope they eventually get bought up buy a company that actually has some thoughts in their heads.
11/7/2005 9:40:00 PM by Dave B.
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
I received an email from Sony BMG with a link to uninstall the software. I'm hesitant to publish it here, because it may have a limited number of uses.
If you want to send me an email address, I'll forward it to you. *Mark only please!*
Thanks for all of your work on this.
Tom
user is thwalters
mail server is yahoodotcom
11/7/2005 9:53:00 PM by Tom
# re: Sony’s Rootkit: First 4 Internet Responds
NtwkGestapo mentioned this earlier- Starforce.
Apparently this is not entirely new ground. I'm just starting to look into this but there is copy protection for PC games called Starforce. It's been around for a while now and it loads in 'hidden' device drivers as part of it's protection mechanism.
Here's an extract from an interview last year by Firingsquad :
"FiringSquad: There's an uproar among segments of the game community that StarForce is installed without user approval. Is this a potential legal concern for your company?
Abbie Sommer: There is no legal concern because before a user loads a game, he or she has agreed to accept the conditions of the end-user licensing agreement, typically known as a EULA. These are also known as click and go, or click and accept agreements. When you accept, you are saying I will load this game or application at my own risk, and have read and understood the terms. Or there will be a disclaimer that protects the publisher from damages of any kind due to their products? use. Our product is licensed to our customers, and becomes part of their product, so the user by accepting the terms, is giving approval."
http://www.firingsquad.com/features/starforce_interview/
And a response to it:
http://www.tgdaily.com/2005/10/01/the_war_on_game_pirates/index.html
It does have a freely available removal tool because removing the game does not always remove the Starforce device drivers:
http://www.onlinesecurity-on.com/protect.phtml?c=55
So you buy music/game/whatever - the "product". You install the licenced "product" with your consent by accepting the EULA. Well the copy protection/rootkit/drm/malware is part of the "product" and you agreed to it- so you're screwed right there is the argument the bad guys will take.
11/7/2005 10:00:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
This BSoD issue with redirected code pointers in driver chains is a classic programming problem that goes back before Windows was even written. The earliest example I know of was with MS-DOS (there's that MS again) TSR utilities (Terminate and Stay resident). You could install multiple utilities, each of which put a hook into the keyboard interrupt, so that it could detect its hot-key combination and activate when requested. Anyone remember a little tool called Sidekick from Borland? If you uninstalled your TSRs out of order, your system would lock up because it couldn't read from the keyboard anymore. There are probably older examples out there.
So these clowns committed a programming error that was known and documented over 20 years ago.
11/7/2005 10:07:00 PM by Where_Wolf
# re: Sony’s Rootkit: First 4 Internet Responds
Three Programmers testing their design for their Sony DRM release:
MOE, come here, it's done, it hides our stuff!
Great Larry are you sure it hides just our stuff?
Well Curly says he tried to rename notepad.exe to C:\$sys$notepad.exe and he could see it!
OK, lets tell Sony were ready for the first CD!
Curly "Certainly...yuck...yuck...yuck"
11/7/2005 10:15:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
I have a Sony Ericsson GC79 wireless card installed on my laptop. This card and the associated software is the interface between my laptop and the local wireless communications tower.
Theoretically, the software for the GC79 could intercept certain packets from a known IP address. This software could rummage around my computer for certain personal information and send it back to that IP address. Theoretically, this could be done in a way that is undetectable by my firewall, spyware, and virus software. The traffic could be made undetectable by any monitoring software such as Ethereal.
Now I do not know whether the GC79 software does such things, but I would like to check the GC79 software just to be sure. Has this been done by anyone? And what about the software for the GC75/82/83/85/89?
11/7/2005 11:56:00 PM by Chris Billings
# re: Sony’s Rootkit: First 4 Internet Responds
Hey! I recognized the 'blue screen' in Marks NTCrash2 test.
A couple of weeks ago my daughter tried to play a CD that needed administrator rights. I am not against copy protection, so I installed the software for her. It came with some nice, fancy extra features, so she was happy.
The next day I wanted to make a backup to DVD of my digital photographs with Pinnacle instant CD/DVD and there it was: the blue screen!
After restart, I send Microsoft an error report and got back a message, stating that the problem was known, it had to do with CD copy protection and they directed me to a link on First 4 Internet for an update. After that I was able make a backup of my photographs.
I was glad with the service Microsoft provided and how quick I was up and running again, but I had an awkward feeling about that copy protection mechanism.
I do not use my CD burner that often, but a couple of days ago I had again some problems with my cd burner. The process could not be killed and Windows could not be shut down.
What bothers me, is that I do everything to keep my computer clean and by installing a copy protection mechanism on a legal CD I get this kind of trouble.
Feels like punishment for buying legal CD's.
Today, I got a link from Sony to deinstall the DRM software.
After returning from work (and find out what experience other people had with deinstalling) I will try this out.
11/8/2005 12:25:00 AM by hans
# re: Sony’s Rootkit: First 4 Internet Responds
I hope this is true report: Sony to be sued in Italy:
http://theinquirer.net/?article=27508
Actually Alcei (which is a private italian organization similar to EFF) didn't sue. It delivered what in Italy is called an "esposto" that is, you go to the Police and tell them that you have the notion that a crime is being or has been committed and you explain why. In this case, they used the information provided by F-Secure and a technical analysis made by an italian engineer from the Technical University of Milan.
Now it's up to the italian authorities to decide if the information provided is enough to warrant an inquiry. If a judge agrees that a penal crime has been committed, he/she is obliged to press charges, otherwise you have to start a civil action by yourself.
11/8/2005 2:49:00 AM by pennino
# re: Sony’s Rootkit: First 4 Internet Responds
The problem with legal action against Sony is the EULA. I am guessing that one reason that they picked New York for their choice of law is that they felt that their EULA would more likely be confirmed under that law. Since ProCD (one of the worst decisions I have ever read, by a fairly well respected judge), courts have more than not affirmed shrinkwrap licenses, and the Sony EULA fits right in there.
If you get through the boilerplate, what their EULA says is that you can't sue them for anything they did, if you do, you have to do it in NY, under NY law, and if you win, you are limited to $5.
I think that the EULA can be broken, but if it is, it will have major impacts on EULAs and shrinkwrap licenses across the music AND software industry. So, with the money at stake, expect an expensive, brutal, fight.
Remember, they have the money to fight this and a real economic incentive to do so - they stand to lose a lot of money if their EULA falls. And it does take a lot of money to fight this sort of case.
I see a couple of approaches that might have some success:
1. Small claims court. Informal, and they probably won't fight that hard (they can't) - but the damages are very limited. Pin pricks at best.
2. Class action suits. Would need them persued in more than CA though. A coordinated national effort in a lot of states, and you could probably break the EULA in one, opening up some of the rest of the country. But this takes finding enough attorneys willing to do this on consignment.
3. State Attorney Generals. I have sent a complaint in to the CO AG, and suggest that you do to yours too. Can't hurt, and they are more likely to break a EULA than anyone, except for the Feds. The problem is getting their attention. Need to convince them that this is a big consumer issue.
4. The FTC. A big long shot. But again, maybe a large concerted campaign might get their attention. They have the best chance of breaking the Sony EULA, but I think would be hesitant to do so, given how common they have become in the software industry.
Again, some links to legal issues on my blog:
Sony DRM rootkit code (#19) EULA
Sony DRM rootkit code (#11) Letter to CO AG
Sony DRM rootkit code (#6) Trespass to Chattels
Sony DRM rootkit code (#5) Msc Causes of Action
Sony DRM rootkit code (#4)
Sony DRM rootkit code (#3) Cyberia-l suggestions
Sony DRM rootkit code (#2) Class Action
11/8/2005 3:12:00 AM by Bruce Hayden
# re: Sony’s Rootkit: First 4 Internet Responds
Sorry, in my last post, I meant "contingency fee basis" instead of "consignment". Somewhat different for class action suits.
11/8/2005 3:15:00 AM by Bruce Hayden
# re: Sony’s Rootkit: First 4 Internet Responds
I do find the Italian system interesting here, as compared to our American system. Here, you have to get either the police, a DA, or a state or federal AG interested. But it is invariably discretionary, and almost all will pass on this sort of thing. And without that, you can't proceed criminally.
On the other hand, I would worry in the Continental system if you were to get a judge to say, yes, there is a case, but then the prosecutors wouldn't really get behind the suit. As noted in my previous entries, this is going to be expensive to prosecute.
That said, I do expect that Sony is going to run into more trouble legally in Europe than in the U.S., more from a different business climate than due to different judicial systems.
But if they do, I would expect that they would just not use the DRM code there, and fight the importation of such here - if it did make economic sense to do so, which it probably wouldn't.
11/8/2005 3:26:00 AM by Bruce Hayden
# re: Sony’s Rootkit: First 4 Internet Responds
First a big thanks to Mark for discovering all this.
Computer Associates are now descriping Sonys DRM as spyware and plan to enable detection and removal in their antispyware from November 12.
Source: http://www.pcworld.com/news/article/0,aid,123454,00.asp
Hopefully all the other security companies will do the same.
11/8/2005 3:57:00 AM by Fuzhi
# re: Sony’s Rootkit: First 4 Internet Responds
Hi,
Perhaps when Mark has some "free time" he could document NTCrash2 so we know what to expect amd how we might use this tool.
What results should we see on "working" systems against ones with XCP-Aurora installed?
What other software out there don't pass the tests from NTCrash2 ?
Kind Regards
Simon
11/8/2005 4:41:00 AM by Simon Zerafa
# re: Sony’s Rootkit: First 4 Internet Responds
I can confirm that, with autoplay disabled, the rootkit never installs. I have autoplay disabled on every machine I work with regularly, as a security precaution for just such things as this. I was even quite able to rip the CD to mp3 tracks. RootkitRevealer showed my system to be clean afterwards. I am currently showing all my housemates how to disable autoplay.
11/8/2005 4:56:00 AM by Synkronos
# re: Sony’s Rootkit: First 4 Internet Responds
A CD is a type of FORMAT (Phillips wont allow the CD logo on these sony disks)
So we need a new Acronym for them
M usic D elivery S ystem been used here already so MDS it is.
11/8/2005 6:38:00 AM by Sharpy
# re: Sony’s Rootkit: First 4 Internet Responds
Reading hans' comment above (that he had an aries BSOD, but MS support recognized it as First 4 Internet's problem) it sounded like MS had seen it cause crashes before, so I checked in MS support articles. Sho' nuff: aries.sys crashed Media Centre . Quoting the relevant portion:
Transcript: Windows Media Center Edition, August 18, 2005
...
Andrew_MSFT (Moderator):
Q: i have encountered the "blue screen" and the mini-dump files says the sytem is looking for aries.sys. An exhaustive search on my system and the web has turned up nada. What is aries.sys and where can it be found or how can i shut it off? Thanks
A: Which version of Windows XP Media Center Edition are you running on your PC?
11/8/2005 7:09:00 AM by bazzargh
# re: Sony’s Rootkit: First 4 Internet Responds
Hans,
Just share the uninstall utility!
11/8/2005 7:22:00 AM by Raj
# re: Sony’s Rootkit: First 4 Internet Responds
I have an idea! Instead of wasting your money on another SONY CD, why not waste your money buying shares in the company instead... If enough people did this... well I'm sure you can see where I'm going!
11/8/2005 7:50:00 AM by Chunky
# re: Sony’s Rootkit: First 4 Internet Responds
Look folks, a race condition isn't that big of a deal. They almost never happen! After all, race conditions have been directly linked to only five deaths and a handful of serious injuries (Therac-25).
11/8/2005 9:48:00 AM by Daniel Einspanjer
# re: Sony’s Rootkit: First 4 Internet Responds
I received this blue-screen-o-death in your blog starting on september 23rd, and continuing into the week. http://blogs.technet.com/photos/markrussinovich/images/482355/original.aspx
On the Following Tuesday, Microsoft recognized it and sent me to first4dangerous rootkits for information. They told me I had to go to Sony.
I harrassed Sony until they relented and emailed me a link to go to to get an unistaller. I downloaded it and it appears to have do the job. They DID NOT email it to me.
Here is a series of letters I have written to Sony starting on Sept 23rd, and includes their letters as response.
http://www.mboxcommunity.com/SONY.html
anybody wanting to contact me with my long experience ranging back to mid september and this rootkit can email me at sugar@coldprofessionals.com
11/8/2005 10:44:00 AM by Mark C
# re: Sony’s Rootkit: First 4 Internet Responds
Oh, and the uninstall utility had a time bomb in it that caused it to stop working after download and a period of time passed. I do not believe it can be passed around to all, which means that Sony id determined to leave this on most computers.
11/8/2005 10:48:00 AM by Mark C
# re: Sony’s Rootkit: First 4 Internet Responds
Concerning the fact that big content-companies (movie and music companies) own all or most of the news agencies... That is something has had a number of people concerned over the years, and I think it is time some action was taken about that, too.
Many moons ago, when the motion picture industry was new, the studios owned the theaters. Because of that, it was not possible for independant movie makers, and small studios to get their movies into the theaters. At some point, the government realised this was a Very Bad Thing and banned the ownership by the studios of theater chains. It was declared BY LAW that the studios had to sell off all the theaters that they owned, and declared BY LAW that the theaters HAD to be independant of the studios.
What we now need is a groundswell of public demand that the entertainment industry (movie and TV studios, music companies, makers of novels and whatnot) be REQUIRED BY LAW to sell off all news-related companies, that there be a law that FORBIDS ANY MASS ENTERTAINMENT COMPANY from having any financial ties to ANY news agency.
There must also be a law that forbids monolythic news companies. That is to say, publishing conglomerates must not be allowed to get larger than a certain size, and cannot own more than X number of major newspapers and/or own more than X number of television or radio stations that contain news shows, especially if a station IS PRIMARILY a news station. They could own as many Discover Channels and Fun And Games Channels and Mystery Movie channels and Pure Science channels as they wanted, they just couldn't have more than X news channels, or place news shows on more than X different of their channels.
No, on second thought, I take that back. The entertainment industry should be kept completely seperate from the news industry. By law. Period.
And there must be several, equal, large, independant news corperations, instead of effectively One Big, Monolithic News Industry... and one with a massive case of GroupThink, at that.
In any event, if we DID have the news industry split off from the entertainment industry, we WOULD SEE much more attention brought to this Sony DRM bruhaha by the news industry. Or, to be more acurate, if we succeeded in getting the news industry split off from the entertainment industry, AND if we caused the news industry to go BACK to the state of being several independant, competing agencies (like they were SUPPOSED to be!!!), then the NEXT TIME something LIKE this Sony DRM debacle came along, there WOULD be much attention brought to it by the news industry, as a matter of course, and without us having to drag them kicking and screaming to it!
11/8/2005 1:51:00 PM by NomadOfNorad
# re: Sony’s Rootkit: First 4 Internet Responds
xgwpc wrote:
"I think that the scariest part of this whole fiasco is that now Mr. Russinovich is liable under the DMCA (under the Circumvention provisions - a prohibition on the removal of copyright management information (CMI) [1202(b)])."
If Sony tries to charge Mark with that, it may backfire on them as they are even more liable as Sony has committed computer fraud, negligence, and trespass. There is a class action lawsuit being taken up by the Green Welling law firm in California. When all is said and done, Mark will be hailed as a whistleblower, and Sony will pay millions in damages to affected users. BTW, IANAL.
11/8/2005 2:07:00 PM by Rafterman2
# re: Sony’s Rootkit: First 4 Internet Responds
As a half-way decent barrack room lawyer, I have two observations:
1. The UK has a law, the Unfair Contract terms law. Its a very powerful and under-used weapon against exactly this.
What it says is, if you are obliged to accept an unfair contract term because of major disparity in negotiating power (eg Sony v. individual), any court - even a small claims cheap court - can rule it unlawful and strike it out. For not much money therefore (under $100) a UK user could get a court ruling most likely.
2. A key part of contract law is consent. if you are asked to install "software" then the assumption isthat you agreed to install a game, because that is what you bought. There is considerable law about things that are not what they seem... and you are NOT considered to have agreed to their installation if it was not made clear. The corporate answer "well you agreed" does not carry weight, a good lawyer would crucify them for that one. ACLU anybody?
My $0.02
11/8/2005 3:10:00 PM by Jeff
# re: Sony’s Rootkit: First 4 Internet Responds
CA has classified it as well.
http://www3.ca.com/securityadvisor/pest/pest.aspx?id=453096365
Speaking of which doesn't CA and Sony have distribution deals? Wouldn't this be a conflict of interest?
11/8/2005 3:19:00 PM by Blind
# re: Sony’s Rootkit: First 4 Internet Responds
You see, they aren't just "installing software". They aren't even just installing software to protect their rights. They are fundamentally reconfiguring the core of your machine, in a manner that they know you have not authorized, that the manufacturer (microsoft) has not approved, that voids the warranty, and renders your property (a windows based copmputer) more liable to serious flaws including instability, denial of operation, loss of resources, loss of personal data, increased vulnerability to malware, increased likelihood of software conflict.....
11/8/2005 3:20:00 PM by Jeff
# re: Sony’s Rootkit: First 4 Internet Responds
I wan't to qualify the following from the outset, by saying that none of what I am about to say in any way shape or form mitigates Sony and First 4 in their use of this stealthy rootkit. Sorry for sounding like a EULA but I just wanted to make that clear.
I'm glad there have been comments clearing up the administrative priveleges issue. Basically the way I operate when downloading and installing new software is this:
if the software wants an admin password to install, I take a long hard look at a) the software itself b) the supplier (i.e. the website), and c) whether or not I really have to install it in the first place.
I know this is a moot point in relation to our current issues surrounding Sony and First 4, since their cd rootkit definitely did not require any downloading on the part of the user.
That said, if admin priveleges were required (and enabled), surely a music cd that asks you to enter your admin password should trigger alarm bells.
In short, if you don't have admin passwords enabled on your OS, enable them now. The inconvenience of typing your password in from time to time is surely outweighed by the extra protection it gives you against software that requires low-level (ie device driver) access.
I know its obvious, but only system utilities, network software, and software that needs low level access should need admin priveleges. Be suspicious of anything else.
11/8/2005 3:33:00 PM by ruy_lopez
# re: Sony’s Rootkit: First 4 Internet Responds
I received the uninstall link email from Sony today. After following the link, it took me to an Active X page that had the Sony BMG logo on it and the words, "Welcome to the SonyBMG Customer Support Website. I wish to uninstall any software that has been installed after inserting a copy-protected Enhanced CD." There was a button labled "Uninstall" which did not allow you to download an executable file, but rather, ran the file remotely. After it completed, it displayed a button to "Restart". After doing this, I ran Hijack This and found two XCP associated items:
Service: XCP CD Proxy (CD_Proxy) - Unknown owner -C:\Windows\CDProxyServ.exe
DPF: {4EA7C4C5-C5C0-4F5C-A008-8293505F71CC} (CodeSupport Control) - http://www.xcp-aurora.com/clients/SoftwareUpdate.cab
Not only that, but after looking at F-Secure's site for the XCP DRM Software, I discovered that seven other files associated with it were still on my machine in the windows and system32 directory. When I checked my running processes, CDProxyServe.exe was still running.
So the question is, what did the uninstaller do? It certainly didn't uninstall everything.
11/8/2005 4:00:00 PM by Nearly
# re: Sony’s Rootkit: First 4 Internet Responds
Steve Gibson of www.grc.com and Leo Laporte of www.leoville.com have a Security Now! / TechTV podcast on this issue at http://www.grc.com/SecurityNow.htm
Nice to see this getting attention from other programming experts.
11/8/2005 4:18:00 PM by EdwardN
# re: Sony’s Rootkit: First 4 Internet Responds
I'm glad SANS picked up on this story in its latest NewsBites.
11/8/2005 4:39:00 PM by Dmitriy Blok
# re: Sony’s Rootkit: First 4 Internet Responds
I have been communicating with Brian Krebs of the Washington Post here is a new story:
Posted at 06:35 PM ET, 11/ 8/2005
Calif. Lawsuit Targets Sony
http://blogs.washingtonpost.com/securityfix/
It should be noted that the court filing is DEMANDING a Jury Trial and all detail of the filing and much more can be seen in Brian's article at the link above.
11/8/2005 6:15:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
Thanks Blind- this is great.
I wonder if Sony will go after CA. They list the player as spyware and the rest of it as a trojan. Sounds good to me. It doesn't specifically list the stealthing technology it uses in it's first 'variant'.
Extract from the CA Spyware Information Center:
XCP.Sony.Rootkit
Reasons For Retention
Installs without user permission, presenting only a vague and misleading EULA
Changes system configuration without user permission at time of change.
Defends against removal of, or changes to, its components
Silently modifies other programs' information or website content as displayed.
Includes mechanisms to thwart removal by security or anti-spyware products.
Cannot be uninstalled by Windows Add/Remove Programs and no uninstaller is provided with application.
http://www3.ca.com/securityadvisor/pest/collateral.aspx?cid=76345
We'll have to monitor their emerging threats page:
http://www3.ca.com/securityadvisor/pest/emerging.aspx
11/8/2005 6:17:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Nice work finding opening our eyes to the nastiness going on.
However, I hope you have a lawyer on retainer. I'm no lawyer, but there are things in your blog which raise red flags on my radar.
#1. Inflammatory statements against First-4-internet (Stating they are incompetant could make you liable for any business losses they can tie to statements made by you in your blog).
#2. Reverse engineering and/or releasing trade secrets. (Again, First-4-Internet would be the suitor)
#3. Inflammatory statements about Sony Music. Sony is in the top-10 most evil companies on earth, and it wouldn't suprise me if they targeted you as a convenient excuse for why their record sales continue to fall into the gutter.
Good luck, keep up the good work, please protect yourself as you expose the truth.
11/8/2005 8:45:00 PM by dohb0y
# re: Sony’s Rootkit: First 4 Internet Responds
http://blogs.washingtonpost.com/securityfix/
Washington Post
Brian Krebs on Computer Security
Posted at 06:35 PM ET, 11/ 8/2005
Calif. Lawsuit Targets Sony
A class-action lawsuit has been filed on behalf of California consumers who
may have been harmed by anti-piracy software installed by some Sony music
CDs. A second, nationwide class-action lawsuit is expected to be filed
against Sony in a New York court on Wednesday seeking relief for all U.S.
consumers who have purchased any of the 20 music CDs in question.
Experts say the Sony CDs use virus-like techniques to install digital rights
management software on computers. Windows users cannot listen to the
protected CDs on their computers without first installing the software,
which hides itself on the users' system and cannot be uninstalled by
conventional removal methods.
The California lawsuit, filed Nov. 1 in Superior Court for the County of Los
Angeles by Vernon, Calif., attorney Alan Himmelfarb, asks the court to
prevent Sony from selling additional CDs protected by the anti-piracy
software, and seeks monetary damages for California consumers who purchased
them.
The suit alleges that Sony's software violates at least three California
statutes, including the "Consumer Legal Remedies Act," which governs unfair
and/or deceptive trade acts; and the "Consumer Protection against Computer
Spyware Act," which prohibits -- among other things -- software that takes
control over the user's computer or misrepresents the user's ability or
right to uninstall the program. The suit also alleges that Sony's actions
violate the California Unfair Competition law, which allows public
prosecutors and private citizens to file lawsuits to protect businesses and
consumers from unfair business practices.
Himmelfarb was on a plane at the time of this writing and could not be
reached for comment. But a court-stamped copy of the lawsuit he filed is
online here (PDF).
Scott Kamber, an attorney in New York, said he plans on Wednesday to file
class-action suits targeting Sony under both New York consumer protection
statutes and a federal criminal statute that allows civil actions.
"This situation is particularly egregious and surprising from a company that
should be familiar with concerns people have with programs crashing their
Windows computers," Kamber said. "What Sony is saying with this software is
that 'Our intellectual property is more deserving of protection than your
intellectual property,' and Sony can't be allowed to get away with that."
Sony spokesman John McKay declined to comment on the suits.
I wouldn't be surprised if other lawyers and law firms around the country
are also preparing to file similar suits.
As I wrote in a story last week, "Sony's move is the latest effort by the
entertainment companies to rely on controversial 'digital rights management'
(DRM) technologies to reverse a steady drop in sales that the industry
attributes in large part to piracy facilitated by online music and movie
file-sharing networks like Kazaa and Limewire."
Experts who studied the Sony program said it has a built-in file-cloaking
feature that could also be used by attackers to hide viruses and other files
on a user's computer, and that conventional means of removing the
anti-piracy software renders the user's CD-Rom drive inoperable.
In response to public criticism over the invasiveness of the software, Sony
last week made available on its Web site a "patch" that would prevent its
software files from hiding on the user's system. But according to further
research by a variety of security experts, that patch can lead to a crashed
system and data loss.
By Brian Krebs | Permalink* | Comments (0) | TrackBack (0)
11/8/2005 9:08:00 PM by srynas
# re: Sony’s Rootkit: First 4 Internet Responds
It's a bit late but it had to happen over the following quote by a Sony exec:
""Most people, I think, don't even know what a rootkit is, so why should they care about it?""
http://www.theregister.com/2005/11/09/sony_drm_who_cares/
11/8/2005 9:11:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
"Most people, I think, don't even know what a rootkit is, so why should they care about it?"
^ That's like saying, "Most people don't know what a thermite grenade is so they won't care if an active one is underneath their pillow"
Anyways, thank you very much Mark for your hard work. I don't have any "infected" Sony CDs but what you have done is a service to computing-kind :)
11/8/2005 9:56:00 PM by Aaron
# re: Sony’s Rootkit: First 4 Internet Responds
If any hacker were to do this they would be prosecuted for cyber crime. Why are law makers and enforcement agencies not taking action against Sony. Personally I am passing this information around to as many people as I can and encouraging anyone I know to boycott Sony. I also wish there would be a good scanner and uninstaller available to identify this and other similar problems.
Mark, a job well done! Stay the course!
11/8/2005 10:26:00 PM by SchneiderIS
# re: Sony’s Rootkit: First 4 Internet Responds
The irony is that it's SAFER for your computer to download pirated MP3/OGG files of Sony artists than it is to buy and listen to a Sony CD.
11/9/2005 1:28:00 AM by VXDguy
# re: Sony’s Rootkit: First 4 Internet Responds
EULA's I hate em they lie they cheat and they think they have the law on their side.
Well add this little gem to your armoury. EULALYSER.
http://www.majorgeeks.com/EULAlyzer_d4759.html
Bright Light always make creepy crawlies run for cover. You hear that sony!!
11/9/2005 4:40:00 AM by Sharpy
# re: Sony’s Rootkit: First 4 Internet Responds
For long I have been observing Sony's negligence towards people friendly approach. Other than few products like walkman, psp et al., Sony has never tried to adapt any technology that has been widely accepted by the public.
They were still trying to push their own formats and in doing so forget what people expect out of them. This suggests what happened in case of BetaMax, ATRAC and now the long going war of BlueRay...
I thought though sony was trying to push its own format.. it was revolutionising the market and providing new options.. but when it comes with such flaws as happened in DRM as well.. I'm losing all my hopes against the electronics major that I admired once....
11/9/2005 7:17:00 AM by Srikanth
# re: Sony’s Rootkit: First 4 Internet Responds
Just like most big business and government, this story is starting to lose steam. The media outlets are losing intertest after devoting the standard nanosecond of coverage. It's up to us folks to keep this going. Even with the class action suits being filed, Sony knows this will bog down in litigation and ensure a nice holiday profit for this year and next Tell everyone you know. Hit Sony where it hurts, IN THE WALLET...keep yours closed!
11/9/2005 7:31:00 AM by Nads
# re: Sony’s Rootkit: First 4 Internet Responds
Made it in An Australian newspaper
http://theage.com.au/articles/2005/11/03/1130823323159.html
11/9/2005 7:46:00 AM by Mightyman
# re: Sony’s Rootkit: First 4 Internet Responds
Thanks for bringing this to everyone's attention Mark.
In case anyone missed it, you can sign the "Boycott Sony" petition at http://www.petitiononline.com/bcsony/petition.html
Sony are OFF my Christmas list - forever!
11/9/2005 8:37:00 AM by Elwood Herring
# re: Sony’s Rootkit: First 4 Internet Responds
@ Mark C, I read your letters found on http://www.mboxcommunity.com/SONY.html - Very nicely done! Not everyone would go through the trouble of writing Sony as you have. Your daughter has excellent taste regarding the CD you mention. I feel sad this has happened to her. Sony really should take notice to a well known business phrase " For every one complaint, there are at least 10 complaints that go unheard."
Did anyone else yet test this so-called "uninstall" from Sony yet? This is rediculous! You'd think they would make this immediately available to people in the wake of this madness that they've caused! After reading Mark C's and Nearly's thorough review on this gives some indication that perhaps this "uninstall" is NOT going to do what they say it will do afterall.
11/9/2005 8:42:00 AM by CindyRilla
# re: Sony’s Rootkit: First 4 Internet Responds
oh well.
I got a great idea to start my own business now.
I will start to write my own boot device driver.
Plan is to present this as THE ultimative game copy protection to the clueless game developers.
If you once installed the protected game it will alter your operating system at boot time in a way that it will only boot if you have inserted the original game cd in your drive.
it will disable everything and only give you the ability to play the game.
if you dont want to play anymore you need to write an email to me from another WORKING machine and I will call back in about 3 weeks and tell you the unique magic keyword to disable the boot protection.
yeah I will make BIG money with this because all the stupid people out their would by the cds.
But wait, if I sell such a sort of virus to a view million of people I would face about 50 years of jail and a few million $ of refunds to the stupid customers who blame me for their own stupidity to by the protected games.
this kind of protection IS possible though.
but @First4Internet:
who the *uck do you think you are?
did you think about what you are doing here?
did you think about what you install on my system without MY acknowledgement?
you are only some very clever virus authors (or very stupid, future will tell).
everyone talks bad thinks about holyfather (hackerdefender author) because he is selling edited and undetectable rootkits to people who pay for them.
the main difference between his and your business is:
people who buy from him know what they get, while you sold your rootkit to millions without their knowledge.
this is just too crazy to be true.
you dropped yourself into big problems.
11/9/2005 10:14:00 AM by stefan stephan
# re: Sony’s Rootkit: First 4 Internet Responds
Can you please clear up one point which has confused me (and several other posters by the look of it):
This "Service Pack" which Sony refers to: is it Microsoft's XP pack, or Sony's own?
Thanks - keep up the great work.
11/9/2005 3:15:00 PM by Elwood Herring
# re: Sony’s Rootkit: First 4 Internet Responds
Sony's (First 4 Internet's).
11/9/2005 3:17:00 PM by Mark Russinovich
# re: Sony’s Rootkit: First 4 Internet Responds
Are you a resident of California? Have you purchased one of the Sony/Columbia music CDs with the First 4 Internet DRM schemes?
If so please contact me ASAP at eleeAT1to1lawDOTcom.
Please SAVE your receipt and if possible, take a screenshot of the CD playing software installed on your computer.
I'm an attorney in Los Angeles, California and I'm investigating bringing a class action lawsuit against Sony.
The foregoing is an ADVERTISEMENT. I am licensed to practice law in the jurisdictions of California and New York only.
11/9/2005 3:20:00 PM by rocky
# re: Sony’s Rootkit: First 4 Internet Responds
If you did un-install this mess, can just the ACT of playing one of these CD's cause the original version to be re-installed?
If so, does Sony owe people a FULL list of which of these CD's can/could re-install this mess, posted SOMEWHERE on their site?
11/9/2005 3:42:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
Does First 4 Internet ALSO owe the public a list of what this software is currently being used with.
Example: Other CD's or DVD's from other companies, other software products and the like?
11/9/2005 3:49:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
i hope those lawyers roto-rooter sony in the arse
11/9/2005 10:16:00 PM by jimmy
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/9/2005 10:16:00 PM by jimmy
# re: Sony’s Rootkit: First 4 Internet Responds
The problem now is that Sony can't admit they have done anything wrong.
If they cave in to demands for a freely available uninstaller and a public apology it would become amunition against them in the various lawsuits that are being filed.
Oh well, untill I see the FORMAL & PUBLIC apology their lawyers surely won't allow them to make at this point, I won't be buying or reccomending ANY Sony products.
Kinda painted themselves into a corner here.
Damnd if they do and damed if they don't. I feel zero pity for them in a situation they created for themselves with this bit of hubris...
11/10/2005 4:40:00 AM by dc4bs
# re: Sony’s Rootkit: First 4 Internet Responds
I am more surprised with Sony’s reaction (or lack of) than with the technical issue itself.
Disguising this malware as a software player might have been the act of a desperate, clueless middle manager.
But it’s clear now that this is corporate policy of a desperate company that is no longer competitive in its main market (consumer electronics) and is trying to squeeze money everywhere, no matter what.
Long Live the iPod. Hurrah to Xbox 360.
11/10/2005 6:30:00 AM by MauroS
# re: Sony’s Rootkit: First 4 Internet Responds
When I think of REALLY effective antipiracy measures that actually help the lables' bottom line, I think of the Skinny Puppy double album Brap 3&4 a few years ago...
Along with all sorts of rare tracks, it included virtually every music video the group had ever made along with lots of other multimedia goodies..I almost never buy new CDs, but I couldn't find it used, couldn't get all the videos from napster, and couldn't figure out how to copy the CD tracks along with the multimedia onto one disc...
And you know what? Not only did I buy one $20 double disc, but when i lost it I bought ANOTHER one, something I've certainly never done with any other album before, and was very satifised with my purchase.
Imagine anyone doing that just so they can get the new Celine Dion single to spin a couple times?
Now if these people would only spend 1/2 as much money as they are giving to these crooks at F4I actually INNOVATING in a way that helps the consumer, ie putting relatively low resolution interviews with the bands, music videos, guitar tabs, concert recordings, etc. etc. they might actually make a dent in piracy.
Unfortunately, they do not understand basic psychology-most people, when given a challenge, will try to surmount it. Most people, when given something for free, will feel obligated to give something in return (ie buying a CD of a really great group you found on napster).
Sadly, the whole business of record labels has gone into a bunker mentality-not expansion, thinking of new ways to make the records more enticing, but contraction, paranoia, swinging their swords like Don Quixote.
Remember, record execs are typical middlemen, rightly paranoid because their traditional role, informing music buying consumers about music that interests them, is becoming obsolete, and they are going to have to get real jobs soon. Maybe the clever ones will find another group of financially naive people to exploit.
Major labels have already cost us listenable mainstream radio in this country, a crime in and of itself. They must not cost us free distribution and mashability of digital content.
If enough people stop buying from majors, they will go out of business and bands will be forced to indies or be forced to self-promote, a much better system for everybody.
Do your part to hasten the obsolescence of these parasitic organizations, and help your friends do the same. We will all be much better off. It is simply indefensible supporting business practices such as this any longer.
11/10/2005 11:57:00 PM by zyodei
# re: Sony’s Rootkit: First 4 Internet Responds
I would suggest that ALL people in the US who read this, take the opportunity to visit:
http://www.ala.org/al_onlineTemplate.cfm?Section=alonline&template=/ContentManagement/ContentDisplay...
This month, the public are able to post comments which will be considered in the review of DMCA next month. Everyone should take the opportunity to post protest about DRM techniques being used. Judging by the amount of noise this Sony rootkit issue has raised, I expect if enough people post to the comments section below:
http://www.copyright.gov/1201/comment_forms/index.html
They will be forced to listen and act on consumer concerns.
11/11/2005 10:23:00 AM by Alexander Hanff
# re: Sony’s Rootkit: First 4 Internet Responds
My law firm is investigating the situation surrounding “rootkits” on Sony-label CDs. In connection with our investigation, we are interested in learning more about the experiences consumers have had with those CDs. I can be contacted at (212) 239-4340 or, by e-mail, at tciarlone@lawssb.com.
11/11/2005 11:56:00 AM by Tom Ciarlone
# re: Sony’s Rootkit: First 4 Internet Responds
http://news.ninemsn.com.au/article.aspx?id=71751
READ THIS!!!!
Sony is suspending production of copy protected cds!
11/11/2005 6:24:00 PM by Jessica
# re: Sony’s Rootkit: First 4 Internet Responds
This is so bad... they built it to stay engaged even if you boot to Safe Mode! I hope they go to jail. I used System Restore since I just fell for this 2 days ago. Does that solve the problem??? Can it be that easy?
11/12/2005 12:19:00 AM by colorado dreamer
# re: Sony’s Rootkit: First 4 Internet Responds
Looks like Microsoft are getting involved now!
http://isc.sans.org/diary.php?storyid=845
11/13/2005 11:19:00 AM by Dan
# re: Sony’s Rootkit: First 4 Internet Responds
This is the new detection and disabling tool for the Sony-BMG XCP software:
http://tracker.zaerc.com/torrents-details.php?id=4106&hit=1
(it disables part of it at least, anyway -- and without addding more sh!t unlike the '''disabler''' from $ony-BM)
11/14/2005 6:54:00 PM by tnuocca342
# re: Sony’s Rootkit: First 4 Internet Responds
"This is the new detection and disabling tool for the Sony-BMG XCP software:
http://tracker.zaerc.com/torrents-details.php?id=4106&hit=1
(it disables part of it at least, anyway -- and without addding more sh!t unlike the '''disabler''' from $ony-BM)"
has anyone tested this out????
i think i downloaded this onto my computer because i now cannot rip files from cd's without a wretched squeal.
i already tried the "sc delete $sys$aries" method to no avail and i downloaded the symantec ryknos removal tool. after running the tool, a window appears saying 'ryknos has not been found on your computer'.
do i need to be patient and wait for an uninstaller to become available? please help!
11/14/2005 8:46:00 PM by kelly o
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/15/2005 11:51:00 AM by The-mad-professor
# re: Sony’s Rootkit: First 4 Internet Responds
Sony are showing their rampant disregard for consumers in Britain as well.
Apparently they are setting wholsesale prices higher to internet retailers than they set to high street retailers.
[URL]http://www.timesonline.co.uk/article/0,,2-1872549_1,00.html[/URL
I have never thought of globalisation as bad, however the recent actions by Sony might have to make me reappraise my viewpoint!!
Chris
11/15/2005 11:53:00 AM by The-mad-professor
# re: Sony’s Rootkit: First 4 Internet Responds
I think Mark is somewhat protected from a legal attack from Sony based on circumventing the copy protection because of one of the four exemptions to the DMCA ( Source ):
"Librarian of Congress James Billington issued four narrow exemptions to the Digital Millennium Copyright Act (DMCA) prohibition on circumventing digital copy-protection technologies. [...]
Billington’s October 28 announcement included two new exemptions: one allowing circumvention of access controls that block read-aloud or text-to-Braille devices, and another permitting circumvention in the use of computer programs and video games whose formats have become obsolete. He renewed exemptions issued in 2000 that allowed access to the lists of websites blocked by filtering software and the circumvention of access-control mechanisms that block because of malfunction, damage, or obsoleteness. The exemptions expire after three years, after which they must be renewed by LC’s Copyright Office.
Surely the sloppy code in Sony's DRM rootkit, as well as it's "removal tool" qualifies as "malfunction" or "damage". I suspect this will be the argument that Microsoft makes with the December addition of the Sony rootkit to it's malware removal tool.
11/15/2005 2:01:00 PM by rdcpro
# re: Sony’s Rootkit: First 4 Internet Responds
(Sharpy) " A CD is a type of FORMAT (Phillips wont allow the CD logo on these sony disks). So we need a new Acronym for them. Music Delivery System been used here already so MDS it is."
If the nominations are still open, I have a couple of candidates:
MERDE - Music Encrypted Rootkit Delivery Effort
SHIT - Sony Hijacks IT
11/16/2005 6:01:00 PM by Ken
# re: Sony’s Rootkit: First 4 Internet Responds
Surely the sloppy code in Sony's DRM rootkit, as well as it's "removal tool" qualifies as "malfunction" or "damage".
Unfortunately, the rule as written only refers to damaged or obsolete dongles that prevent access to the media in question.
Here, the problem is with horrible malware that interferes with machine operation totally unrelated to the content it's supposed to be protecting.
An exemption allowing the removal of such malware would seem like a no-brainer (and perhaps one might argue that it's the case implicitly) but the rules do not at present explicitly provide for it.
11/17/2005 12:50:00 AM by supercat
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Geez! Am I ever glad you're on our side. Thanks for all your hard work.
11/17/2005 11:11:00 AM by KLeonard
# re: Sony’s Rootkit: First 4 Internet Responds
I have found a hack for these xcp crap discs. Install zonealarm pro version 6.0.667.000. Also install Musicmatch 10.00.4015
When you insert the disc in your drive zonealarm pro firewall stops the software from running and somehow shields the pc and allows musicmatch to read the disc Then musicmacth rips tracks into MP3 at whatever bitrate you prefer.
Musicmatch is the only ripping software that I have found that will read these discs. But only after Zonealarm stops the xcp software from running.
TAKE THAT SONY/BMG
11/17/2005 7:25:00 PM by TXMP3
# re: Sony’s Rootkit: First 4 Internet Responds
Don't think Mark has anything to worry about with First 4 Internet.
Just read an article (sorry I do not have the url right now) and it is blasting F4I for using "tightly integrating" open source code from
LAME into their XCP software.
IF F4I did infact use open source in their software, then THEIR sofware MUST also be open.
:-)
11/18/2005 9:33:00 AM by b0rd3r g4l
# re: Sony’s Rootkit: First 4 Internet Responds
Symantec has posted a removal tool at http://securityresponse.symantec.com/avcenter/venc/data/securityrisk.aries.html
I don't know if it works, or how, but maybe someone here can evaluate it.
11/18/2005 2:12:00 PM by Kate Halleron
# re: Sony’s Rootkit: First 4 Internet Responds
The Department of Homeland Security labels XCP a serious threat. See
http://www.us-cert.gov/current
11/18/2005 2:54:00 PM by I am One of One
# re: Sony’s Rootkit: First 4 Internet Responds
In the immortal words of Howard Beale from Network : "I'm mad as hell and I'm not going to take it any more!"
I think that sums up my feelings very nicely.
11/19/2005 2:18:00 PM by dapanther
# re: Sony’s Rootkit: First 4 Internet Responds
In a nutshell...Sony needs to pay all of us administrators, and self employed business owners that have to remove their crap, for the time it takes to truly rid a system of their rootkit. PERIOD. AND WE ALL (Those of us that will be dealing with the removal NOW, a.k.a. before a proper removal system/procedure is produced,) SHOULD BE BILLING SONY FOR THE HOURS IT TAKES US, AND AT THE COMMONLY ACCEPTABLE RATE... SAY $95.00 Per hour, per system. The average person shouldn't have to pay these rates because SONY BLEW IT! I no longer own SONY anything, and WILL NEVER AGAIN, MY CHILDREN ALL THREW OUT THEIR CDS and CD PLAYERS OF THEIR OWN FREE WILL! I suspect they won't be buying SONY anything anytime soon either. Even the kids Playstations are in the trash right now, and THEY TOSSED IT!
Dear SONY, you had better get a proper removal tool out and in the public ASAP. No excuses. The Tsunami of this backlash is only getting bigger the longer you wait.
11/21/2005 6:40:00 PM by Tinker
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/22/2005 12:42:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/22/2005 12:42:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/22/2005 12:45:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
Sony and First 4 Internet don't care for intellectual property protection - they are just greedy companies after their own self-serving interests. How come? Because they insist on using the term CD to refer to items that are not. To quote the BBC website:
Philips, who defined the CD standard and then made it widely available, has been very clear that these music delivery systems do not count as Compact Discs and cannot use the CD logo.
As far back as 2002, Philips representative Klaus Petri told Financial Times Deutschland that "those are silver discs with music data that resemble CDs, but aren't".
So much for respecting intellectual property rights! This hypocricy is everywhere in the media industry. Look at how regional coding on DVDs was meant to protect the right ot release films at the cinema in a controlled way, yet is used on even re-issued DVDs. I think the industry couldn't do more to encourage people to pirate media.
11/22/2005 12:48:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
Help!
Ever since the xcp.rookit has been showing up on my spyware scanner, my cd and dvd drives aren't being detected on my computer. I did a system restore and that worked for a little while, but then the xcp.rookit popped up on my spyware notification again, and now my dvd & cd drives have stopped working again.
Also, even though my spyware says it's blocking it, when I go to my blocked items lists it's not listed there. My other spyware/virus programs (McAfee, Spybot, Adaware) don't detect it!
11/24/2005 4:56:00 AM by Liz
# re: Sony’s Rootkit: First 4 Internet Responds
Is there any way to see if you have this rootkit on your computer ? I have a Sony disc that has it , but I am not sure if I played the disc in here .
11/24/2005 11:02:00 PM by Keith
# re: Sony’s Rootkit: First 4 Internet Responds
Good on you Mark, I give you a round of applause. This whole issue is sheer idiocy. I bought one of the cds with the protection on it, and it did not work in my SONY discman or my car cd player, and because in australia it's illegal to backup music and movies, i couldn't legally p2p the cd. i was mad, because i couldn't even listen to the cd i PAID for! what the hell, sony?
12/4/2005 1:44:00 AM by Jordo1001
# re: Sony’s Rootkit: First 4 Internet Responds
First, Mark, thank you for all the great work.
Sorry for my poor English.
One small comment:
I have read message, posted by Jason : 11:50 AM, November 07, 2005
and followed the link in this message: http://www.sony.net/SonyInfo/IR/info/contact/index.html
I was surprised, when in the bottom of this Sony's page I have read the text:
>Notice of software trouble caused
>by Microsoft Windows' new
>security update program
>If you install Microsoft Windows
>Security Update program
>for "Windows XP," you might have
>trouble opening streaming video
>files in RealPlayer and other >programs.
> Please find instructions on how to set up Windows Firewall so that you may install Windows Update and Windows XP Service Pack 2.
And there was a link to http://www.sony.net/SonyInfo/IR/info/contact/realplayer.html web page.
On this page there was a recommendation, how to enable internet access for RealPlayer through WinXP SP2 Firewall.
I do not use RealPlayer. Is "RealPlayer" a Sony software? If so, it is will be funny, if it also content some undeclared malfunctions.
Anyway, after all, I can not trust Sony, and do not want to allow any Sony software to overhead Firewall security settings / limitations.
I hope, all planet web society will become a force that con stop Sony’s viruswriters!
Vadim.
12/22/2005 8:21:00 AM by Vadim
# re: Sony’s Rootkit: First 4 Internet Responds
I have always avoided "protected" media. Until now the main reason for this is the unreliability of most schemes that I have seen. Now, of course I have a new reason to avoid such products.
What they have done amounts to theft. It is much the same as criminal trespass on ones property.
Kudos to Mark for ferreting out the truth and pursuing it.
One comment on an earlier post: I do not see how Sony can be an example of "American corporate greed." Sony corporation is not an American company. Apparently there is no shortage of greed in the world.
12/26/2005 3:35:00 PM by Analogue
# re: Sony’s Rootkit: First 4 Internet Responds
Does it seem to anyone else that First 4 Internet is Sony's voice?
12/26/2005 8:47:00 PM by kochrep
# re: Sony’s Rootkit: First 4 Internet Responds
A friend of mine told me about DC++.
I saw that program working. It looks promising.
FROM NOW ON I WILL NOT BUY ANY MORE PROTECTED CD/DVDs. At least not from Sony.
I will use DC++.
1/7/2006 4:15:00 PM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
I picked up the new Kate Tunstall album and read on the back that the CD had copy protection and might not work on some CD players for example Car systems. This is eye-bulging stupidity from the Music industry and ensured that I did not part with my money
1/9/2006 6:47:00 AM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
i like sony cd/dvd's
but the d++ sucks
1/9/2006 10:10:00 AM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
I have discovered that I am a "victim" of Sony's "protected" content CDs.
I have had to go some considerable trouble to remove the blasted stuff from my computer only to be told recently by our IT Sytems bloke that all I ahve managed to do to my laptop is to alter the nature and form of the offending software.
I then used a packet sniffer and discovered he was right, there is still "phone home" software installed.
So now they want to steal my bandwidth too.
I feel that until Sony pays me damages in compensation I hold them and their immaterial property rights in contempt. Heck, why I don't just distribute copies of all their media free to everyone I know until I feel my loss sufficiently satisfied.
1/13/2006 6:17:00 AM by Customer Unknown
# re: Sony’s Rootkit: First 4 Internet Responds
My opinion is this, First 4 products must be destroyed and also they website must be hacked. By Sony is little different,we know they are good in building nice hardware but they are to stupid to write a program. Kill the system!!!!!
4/21/2006 4:12:00 AM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
All these has the effect on me that I will never again buy a Sony-CD
7/21/2006 6:20:00 AM by Jack
First 4 Internet , the company that implements Sony’s Digital Rights Management (DRM) software that includes a rootkit, has responded to my last post, More on Sony: Dangerous Decloaking Patch, EULAs and Phoning Home . They rebut four of the points I raise in the post. Their first statement relates to my assertion that Sony’s player contacts Sony’s web site each time it runs and sends the site an ID associated with the CD the user is playing:
The player has a standard rotating banner that connects the user to additional content (e.g. provides a link to the artist web site). The player simply looks online to see if another banner is available for rotation. The communication is one-way in that a banner is simply retrieved from the server if available. No information is ever fed back or collected about the consumer or their activities.
I speculated that the player sends Sony’s web site a CD identifier as part of a check to see if new song lyrics or artwork was available, which they essentially confirm. Their claim that the communication is “one way” from Sony’s web site is false, however, since Sony can make a record of each time their player is used to play a CD, which CD is played, and what computer is playing the CD. If they’ve configured standard Web server logging then they are doing that. As I stated earlier, I doubt Sony is using this information to track user behavior, but the information allows them to do so. In any case, First 4 Internet cannot claim what Sony is or is not doing with the information since they do not control those servers, and the First 4 Internet response fails to address the fact that the End User License Agreement (EULA) and Sony executives either make no mention of the “phone home” behavior or explicitly deny it .
Another point that I made in the post is that the decloaking patch that Sony has made available weighs in at a relatively large 3.5 MB because it not only removes the rootkit, it also replaces most of the DRM files with updated versions. First 4 Internet responded with this:
In addition to removing the cloaking, Service Pack 2 includes all fixes from the earlier Service Pack 1 update. In order to ensure a secure installation, Service Pack 2 includes the newest version of all DRM components, hence the large file size for the patch. We have updated the language on our web site to be clearer on this point.
It’s not clear to me what they mean by “a secure installation”, but like most of the disclosure in this story, they’ve acknowledged the updating nature of the patch only after someone else has disclosed it first. What’s also lost in their response is that Sony DRM users not following this story as it develops have no way of knowing that there’s a patch available or that they even have software installed that requires a patch.
Further, Sony’s patch is dangerous because the way that it removes the cloak could crash Windows. I discussed the flaw in the patch’s decloaking method in the first post and again in the last one (I also provide a simple way for users to remove the cloak safely), yet First 4 Internet refuses to recognize it. They contest my claim in their comment:
This is pure conjecture. F4I is using standard Windows commands (net stop) to stop their driver. Nothing more.
While the probability of a crash is relatively small, its not “pure conjecture”, but fundamental to multithreaded programming concepts. Anyone that writes Windows device driver code must have a firm grasp of these concepts or they can easily introduce bugs and security holes into Windows. Here’s one of many scenarios that will lead to a crash when the patch decloaks Sony’s rootkit:
- Thread A invokes one of the functions that Aries.sys, the Sony rootkit driver developed by First 4 Internet, has redirected
- Thread A reads the address of the redirected function from the system service table, which points at the rootkit function in Aries.sys
- Thread A executes the first few instructions of the Aries.sys function, which is enough to enter the driver, but not enough to execute the Aries.sys code that attempts to track threads running within it
- Thread A is context swapped off the CPU by the Windows scheduler
- The scheduler gives thread B the CPU, which executes the patch’s “unload driver” command, unloading the Aries.sys driver from memory
- The scheduler runs thread A again, which executes memory that previously held the contents of Aries.sys, but is now invalid or holds other code or data
- Windows detects thread A’s illegal execution and crashes the system with a blue screen
As further evidence of this, I’ve performed further testing of the Aries.sys driver using a program I wrote, NTCrash2 , and found that Aries.sys fails to perform basic checks on the data passed to it by applications. NTCrash2 passes randomly-generated invalid data to Windows APIs and on a stock Windows system simply receives error codes from the APIs. However, when NTCrash2 runs on a system that has the Sony rootkit installed Windows crashes. Here’s an example Windows blue screen that identifies Aries.sys as the cause of a crash that occurred while NTCrash2 ran:

Besides demonstrating the ineptitude of the First 4 Internet programmers, this flaw highlights my message that rootkits create reliability risks in addition to security risks. Because the software package that installed the rootkit is hidden when Windows is running (in this case Sony’s DRM software), and even if exposed not clearly identified, if an application triggers one of Aries.sys’s bugs a user would have no way of associating the driver responsible for the resulting crash with any software package they have installed on their system. The user would therefore be unable to conclusively diagnose the cause of the crash, check to see if they have the most recent version of the driver or of uninstalling the driver.
First 4 Internet and Sony also continue to argue that the rootkit poses no security vulnerability, repeating it in the description of the patch download. Any software that hides files, processes, and registry keys based on a prefix of letters can clearly be used by malicious software.
First 4 Internet’s final rebuttal relates to my complaint that as part of a request to uninstall their DRM software Sony requires you to submit your email address to their marketing lists. First 4 Internet says:
An email address is required in order to send the consumer the uninstall utility. The wording on the web site is the standard Sony BMG corporate privacy policy that is put on all Sony web sites. Sony BMG does nothing with the customer service data (email addresses) other than use them to respond to the consumer.
The Sony privacy policy the comment refers to clearly states that Sony may add a user’s email address to their marketing lists:
Except on sites devoted to particular recording artists, we may share the information we collect from you with our affiliates or send you e-mail promotions and special offers from reputable third parties in whose products and services we think you may have an interest. We may also share your information with reputable third-parties who may contact you directly.
Again, the fact is that most users of Sony’s DRM won’t realize that they even have software that can be uninstalled. Also, the comment does not explain why Sony won’t simply make the uninstaller available as a freely accessible download like they do the patch, nor why users have to submit two requests for the uninstaller and then wait for further instructions to be emailed (I still have not received the uninstaller). The only motivation I can see for this is that Sony hopes you’ll give up somewhere in the process and leave their DRM software on your system. I’ve seen similar strategies used by adware programs that make it difficult, but not impossible, for you to remove them.
Instead of admitting fault for installing a rootkit and installing it without proper disclosure, both Sony and First 4 Internet claim innocence. By not coming clean they are making clear to any potential customers that they are a not only technically incompetent, but also dishonest.
More on the story in Sony: You don't reeeeaaaally want to uninstall, do you?
Originally by Mark Russinovich on 11/6/2005 7:29:00 PM
Migrated from original Sysinternals.com/Blog
# re: Sony’s Rootkit: First 4 Internet Responds
damn, if they knew that their rootkit can crash they could just disable the driver and ask the user to reboot (not nice, but safe)
11/7/2005 6:44:00 AM by Diego Calleja
# re: Sony’s Rootkit: First 4 Internet Responds
The responses of both First 4 and Sony only confirm what many of us have suspected ever since Mark broke the news of this rootkit, that:
a) Sony and First 4 must think that this blog and its readers comprise a negligible portion of the market,
b) that by offering de-cloaking and the above rebuttals they can minimise any potential damage the story will have on those who aren't necessarily versed in the technical theory underlying much of our concerns, and
c) further 'rootkit' anti-piracy countermeasures are obviously something they are determined to push ahead with (as a valid practice), despite our concerns about their abilities to tinker with our systems.
It really does not bode well for the future of consumer computing when supposedly reputable companies are blurring the lines between virus propagation and product license protection. Okay, so the kit doesn't self propagate. I'll bet if it hadn't been for this blog we would be seeing instances of $sys$ prefixed trojans in pretty sharp fashion. And though he doesn't explicitly say in the article, the blue screen of death is synonimous with buffer overruns. So in this instance there may not exactly be an exploitable buffer, but how are we supposed to know whether there will be one in the future if we are in the dark about what processes are being introduced into our machines, at what level of privelege, and competence of design.
Nice hacking Mark. Ironically, this Sony/First4 blog has evidenced some rather Linux-style open source solidarity. Surely you pay the cost of end-user agreements so that your proprietary vendor ensures that this kind of thing shouldn't need to happen at the grass roots level? And further, for such a low level of device driver access (that this rootkit needs to install) you would expect some kind of OS warning or administrative password prompt? What do Microsoft have to say on the issue? They've been terribly quiet!
11/7/2005 7:25:00 AM by ruy_lopez
# re: Sony’s Rootkit: First 4 Internet Responds
I'm just some network admin. Just a couple hundred users, a few servers, nohting special. I've encouraged users to bring CD's in to work if they want to listen to music 'cause I don't really have the bandwidth to support a lot of streaming content. Silly me.
I don't have 1/4 of Russinovich's brains. If I find rootkits and spyware and ADS junk on my network, I go after it with a chainsaw, not a scalpel. It's the best I can do. I wish I had the time and IQ to research everything, set up test beds, etc. I don't. If I see it, I have to assume it's malicious and whack it.
Looks like if I try this with the Sony rootkit I'm pretty likely to wreck the CD drives. Which I'll have to spend half a day trying to fix to keep "Those-Who-Must-Not-Be-Annoyed"
happy.
Sony's uninstall routine ain't gonna work for me. Maybe or maybe not it'll work for an individual, but what am I supposed to do about a network with a bunch of infected (there, I've said it) machines? I need Sony to at least post the uninstaller at a website so I can go from station to station, detect it, and get rid of it at a single pass. I don't even have time for that, but what else am I gonna do?
11/7/2005 7:40:00 AM by jimnoble
# re: Sony’s Rootkit: First 4 Internet Responds
Hi,
I am a belgian lawyer specialised in ICT law and I would like to analyse more in depth this story.
Could you post the Sony's licence which appears when you install the proprietary program of Sony ?
Thanks.
11/7/2005 8:09:00 AM by Hydre
# re: Sony’s Rootkit: First 4 Internet Responds
Hydre - the EULA provided when Mark first installed the DRM "application" is linked to from within the first in this series of articles ( http://www.sysinternals.com/blog/2005/10/sony-rootkits-and-digital-rights.html ).
11/7/2005 8:13:00 AM by Wes
# re: Sony’s Rootkit: First 4 Internet Responds
I have been following this story since it hit betanews a few days ago. I must say first off that Mark you have done a tremendous job disecting this whole issue.
First I have to comment on the whole crash issue brought up by Mark which First4 has refuted. I am not going to sit here and say that I have written or fooled around with drivers before because I havent, however the FIRST rule that I learned in Multithreading in just a single app is that any and all threads that are accessing any piece of data in memory must be informed if said memory changes address. It is basic Multithreading programming. Heck it is basic pointers.
Anyhow, as far as the issue as a whole. I find it very disturbing to see this, and even more disturbing that the big news Corps are not covering this story heavily, since it is a clear case of invasion of privacy by a huge Corporation like Sony. However it doesnt surprise me since most of the news conglomerants are run by these companies.
Has anyone tried contacting Microsoft to see their response to this issue? Microsoft right now is advertising their focus on security for their current and future Operating Systems. It is basically their selling point right now.
The implications of "Legit" bussinesses distributing cloacking software unkowingly to consumers opens up a Pandoras box that could cause some serious trouble. How long before we see a virus or trojan out there that exploits this flaw?
11/7/2005 8:57:00 AM by Jedite
# re: Sony’s Rootkit: First 4 Internet Responds
Mark, again some stellar work. I'm wondering whether either Sony or F4I came back with anything about why they feel they need to "lie" to users by obfuscating the names of their files and software (for instance calling the aries driver "Network control manager" when it has nothing to do with networking)? I'd imagine that so far they have refrained from touching that, but I think long term we want to get them to address that too.
Thanks for all the great work on this.
11/7/2005 9:07:00 AM by Jerry Ham
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Thank you for all the great work on this very real issue. I hate to say it but it begs the questions "What else is out there?".
I recall working for a/the software company that sent out a beta to it's work force for testing. The beta had a giant bug due to a rootkit that reported back to the security department to see if anyone was making illegal copies. And that was from a company the should understand Windows drivers, hehe.
People think of their personal machines as their personal space without realizing how much the EULA's for the multitude of companies you are forced to accept opens your system and your life to their prying eyes.
Thank you again!
11/7/2005 9:17:00 AM by Adam Gates
# re: Sony’s Rootkit: First 4 Internet Responds
One underestimated way of preventing things to get installed on your computer, is to run without admin rights. The problem is that not all programs handle this well.
Does this mean you cannot play CDs with Sony's "rootkit" DRM if you are not an admin?
11/7/2005 9:26:00 AM by Thriol
# re: Sony’s Rootkit: First 4 Internet Responds
This may have already been addressed in the comments to the earlier stories
Am I right in thinking that if Autorun is disabled, this DRM never gets installed? (so long as you don't 'run' the CD)
These disks are intrinsically unprotected, and depend upon the DRM rootkit that infects your computer to protect them. So am I right thinking that non-windows systems are essentially immune?
11/7/2005 9:54:00 AM by Symphonic
# re: Sony’s Rootkit: First 4 Internet Responds
I was directed to a page to fill in my email address. However, the page required IE and you needed to let them install an Active-X control, which I refused after this fiasco. I am still arguing it with their support center.
11/7/2005 10:03:00 AM by Marcus
# re: Sony’s Rootkit: First 4 Internet Responds
I just sent an email to Sony telling them I'm putting on hold buying any Sony hardware or downloading and Sony software.
Can't take these risks until they get their act together.
11/7/2005 10:07:00 AM by worldcitizen
# re: Sony’s Rootkit: First 4 Internet Responds
Excellent work, Mark.
I've been following this discussion from the beginning. As a part of my job, I am sysadmin running less than 50 computers (with Windows XP and some Windows 2000) and several servers (Windows 2003). Although the number of computers is small, I need to spend some time in order to keep them all clean and safe; so I check this websiteas well as others to be as informed as possible (although this is the first time that I write a comment) .
This Sony's Rootkit just makes my work harder. And what's worse, it doesn't make any good to legal users that inadvertently install it. Having this program installed calling home is a security risk that no sysadmin can take, period. No matter how you call it: rootkit, DRM, etc. It opens a door in an already difficult to secure OS.
I am wondering if setting up users with limited accounts will prevent this rootkit from being installed. Not every user could be set this way, because some (poorly written) programs require you to have admin permissions to work; but at least would make the computer less vulnerable.
Thanks.
11/7/2005 10:19:00 AM by igalan
# re: Sony’s Rootkit: First 4 Internet Responds
Sony is just digging themselves a deeper hole by not admitting their guilt.
I'm sure that if asked politely most people would not mind installing some DRM software.
These covert ops however won't lead to anything good. Even being a fairly experienced sys-admin, up to just now, I would have never imagined that an audio CD could lead to blue screens.
11/7/2005 10:23:00 AM by Dmitriy
# re: Sony’s Rootkit: First 4 Internet Responds
"So am I right thinking that non-windows systems are essentially immune?"
# posted by Symphonic : 9:54 AM, November 07, 2005
This is easy to test: just
download a liveCD of knoppix and test your hipotese.
http://www.knopper.net/knoppix-mirrors/
11/7/2005 10:27:00 AM by zeh
# re: Sony’s Rootkit: First 4 Internet Responds
It is amazing that Sony can get away with doing things like this. Let's hope that these blogs and articles embarass them enough to stop this kind of behavior.
Didn't they used to have some nice products? I got burned on my minidisc player -- good idea, good construction, but the thing wasn't much more than a walkman -- by design. They could have done so much more, with just a bit of extra firmware.
11/7/2005 10:30:00 AM by Drew from Zhrodague
# re: Sony’s Rootkit: First 4 Internet Responds
If Sony was smart (insert joke here...) they would contact Dr. Russinovich and hire him to dig them out of this mess.
Personally I would feel MUCH more confident about the solution if I knew that it was written by Mark.
This would also be a nice 'mea culpa' for Sony. A little humility would be welcome in my opinion at this stage of the comedy of errors we've all witnessed.
11/7/2005 10:36:00 AM by ThisAJoke
# re: Sony’s Rootkit: First 4 Internet Responds
Hello, I found while searching on Microsoft.com for "first 4 internet" a link to a story posted at Cnet news :
http://news.com.com/New+CD+copy-lock+technology+nears+market/2100-1027_3-5492395.html
Sony and First 4 internet are both mentioned.
11/7/2005 10:37:00 AM by Bob-NL
# re: Sony’s Rootkit: First 4 Internet Responds
Isn't the CD still standard (redbook) CD Audio? If so, wouldn't you just put in the cd, cancel or block the autoinstall (shift) then just play with Media Player or other cd audio player? Perhaps with the older Media Player (start->run->mplay32->device->CD Audio)?
I don't have any F4I protected CDs to test this out.
11/7/2005 10:45:00 AM by halfdone
# re: Sony’s Rootkit: First 4 Internet Responds
Bob,
It is possible to circumvent most of those poorly written programs with a time and experimentation. Many of these programs 'need' admin access so they can modify data in their program folder and in specific registry keys. You can use detection software, such as regmon / filemon, to see what they access and give users modify permissions to only those things.
The upfront cost in time will save you much after your users are locked down.
11/7/2005 10:48:00 AM by McCitizen
# re: Sony’s Rootkit: First 4 Internet Responds
poor Sony programmers, they never thought a guy like Mark would find out (and disect in this way) about this stuff
now Sony is in deep trouble, messing up with the wrong guy
11/7/2005 10:53:00 AM by BlackTigerX
# re: Sony’s Rootkit: First 4 Internet Responds
Bob,
With a little time you could probably tame the poorly written programs as well. Often these programs 'require' admin rights so they can update specific files or registry keys. If you track what they access, say using regmon and filemon, you can give 'Domain Users' modify rights to the specific resources. Then they can run the programs and you can worry less about viruses and spyware.
11/7/2005 10:54:00 AM by McCitizen
# re: Sony’s Rootkit: First 4 Internet Responds
So it also forces you to install Windows SP2? I don't use that and don't intend to.
11/7/2005 11:07:00 AM by Per
# re: Sony’s Rootkit: First 4 Internet Responds
Thanks for keeping up the pressure, Mark. It strikes me as funny that it's more important to Sony and the rest of the RIAA crowd to stop the potential of piracy than it is to keep everyone who reads this as a customer. Which is going to cost them more in the long run, keeping me from stealing a CD, or guaranteeing that I'll never buy another Sony product?
11/7/2005 11:18:00 AM by Martin McKeay
# re: Sony’s Rootkit: First 4 Internet Responds
Answer to Limited User Account question: The Sony DRM player requires administrative rights to install. Tested on Windows 2000 on virtual machine. A regular limited user could not install the player and the DRM rootkit. The software presented a prompt saying that administrative rights were required. I did not test this as a "power user".
11/7/2005 11:48:00 AM by Hooper3.0
# re: Sony’s Rootkit: First 4 Internet Responds
I've been following this with great interest as my Granddaughter had asked me to look @ a Sony-BMG CD that she'd recently purchased (I got the CD just a day or two before this story broke).
I hadn't had a chance to look @ the CD before the story broke and read Mark's initial analysis closely. This remindes me of a copy protection scheme I discoverd after loading a new game.... The wonderful folk @ Starforce.com use a copy protection scheme that inserts 'daisy-chained' drivers in your IDE channel and the ATAPI code. This caused me no end of problems.... overall a 10% reduction in system operation, stuttering in games OTHER THAN the GTR racing game that installed the scheme, and loss of functionallity of legally purchased cd duplication software (Nero and CloneCD, and yes there ARE legal uses for both!). Starforce DOES supply a removal tool, but the version that I had (current version from the starforce.com site at the time I was looking) didn't remove the files from the "driver cache" so I STILL decided to go thru a complete re-install of the O/S after removing the software... I, at the time, decided to just NOT use the game (probably should have been more agressive, but a $40 game just isn't worth the hassles... I just wrote off the company(s) involved, 10tacle studios and SimBin...)... I've not yet gone over to their house to remove the root-kit, but will be doing so soon...
While I agree, companies have the legal right to protect their Intellectual Property, the metods used by Sony BMG and by 10tacle Studios and SimBin go too far... I'm a CISSP (Certified Information Systems Security Professional) and work with IP issues on a daily basis.. so I do understand the issues involved..
11/7/2005 11:48:00 AM by NtwkGestapo
# re: Sony’s Rootkit: First 4 Internet Responds
For those of you who are Sony stockholders, let them know how you feel about how they are representing your money and write Investor Relations:
http://www.sony.net/SonyInfo/IR/info/contact/index.html
11/7/2005 11:50:00 AM by Jason
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Great job! You have put the spotlight on Sony and their unethical Machiavellian business tactics. I really hope to see them get the book thrown at them. However, I think you are being too nice to them.
In your blog you write:
"I checked the EULA and saw no mention of the fact that I was agreeing to have software put on my system that I couldn't uninstall. Now I was mad."
"When I logged in again I discovered that the CD drive was missing from Explorer. Deleting the drivers had disabled the CD. Now I was really mad."
Ok, so you say you are "really mad".. then you write the following and here is where I think you are being WAY too nice to Sony:
"The media has done a great job of publicizing this story, which has implications that extend beyond DRM to software EULAs and disclosure, and I hope that the awareness they’re creating will result in Congressional action. Both the software industry and consumers need laws that will clearly draw lines around acceptable behaviors."
The problem is the mentality behind their actions. As consumers we want and need such laws as you mention. However, we shouldn't need these laws because businesses shouldn't have the desire to screw over their consumer base. This is just one example of corporate american greed that disgusts me. The problem is that they are by definition, being an american capitalist business, are purely in the "business" of making money... not just making money, but their goal is to make as much money as possible to increase the value of their stocks as highly as possible. This is the recipe for disaster. It's sad that we have to act retroactively on this. The business model allows for this behavior which is obviously unethical from the perspective of the consumer, however to the business they feel they are within their right to protect their income and revenue which they believe is under threat of piracy. Their entire mentality is backwards. The reality is that they are screwing everybody over so that they can make as much money as possible. I don't believe that "congressional action", essentially making new laws to limit what Sony can do, is enough. They will just come up with something else. What needs to happen is that they need to be sued and slammed with a HUGE punitive fine.. when I say huge, the only thing that Sony cares about is money, so with that in mind, they need the equivalent punishment as getting roundhouse kicked in the face repeatedly by Bruce Lee about 20 times, I don't know how many millions of dollars that needs to be, but that is what needs to happen.. the next question is, who gets that money? The sad thing is that attorneys will get 30 to 40% of the money. The money should be given to consumers of Sony products. What can consumers do in the mean time? Boycott Sony's products, this means don't buy Sony Televisions, DVD players, video cameras, digital cameras, etc. There are other brands that are better anyway. I was going to buy a Sony Digital Camera, but now I'm going to buy a Canon instead. I was going to buy a 65" Sony HDTV, but now I'll buy either the Mitsubishi 1080p or Toshiba instead. I have been a huge Sony fan all of my life and have recommended to dozens of people their products.. now I'm disgusted that I have contributed to a company that would resort to this sort of behavior. I think of all of the Sony VAIO laptops I have recommended in the past.. now I will be recommending Toshiba instead.
Also,Mark, could you please write a very simple step by step instruction list for removing this root kit. Or better yet, if you could please write an uninstaller or work with Adaware or Spybot or Microsoft Antispyware so that they can update their software to remove this infection. It would be great if I could have a simple .exe file that I could put in the login script that scans and removes this garbage and outputs a log file to a network drive.. Thanks again!
11/7/2005 11:59:00 AM by miamibeachman
# re: Sony’s Rootkit: First 4 Internet Responds
I hope this is true report: Sony to be sued in Italy:
http://theinquirer.net/?article=27508
11/7/2005 12:01:00 PM by Enough
# re: Sony’s Rootkit: First 4 Internet Responds
"An email address is required in order to send the consumer the uninstall utility."
You clearly already showed that the utility is available online, and does not need to be emailed. :|
11/7/2005 12:36:00 PM by nozzlehead
# re: Sony’s Rootkit: First 4 Internet Responds
I think that the scariest part of this whole fiasco is that now Mr. Russinovich is liable under the DMCA (under the Circumvention provisions - a prohibition on the removal of copyright management information (CMI) [1202(b)]). I would suggest that he consult with his attorneys forthwith before those A-Holes at Sony file charges.
11/7/2005 12:49:00 PM by xgwpc
# re: Sony’s Rootkit: First 4 Internet Responds
The worst and most stupid thing SONY can do is firing charges against Mark, that would bring this whole mess and bad publicity to a whole new level.
SONY should:
1. publish a uninstaller that can complete remove the rootkit;
2. dismiss F4I and then blame them for this;
3. buy this website and hire Mark.
11/7/2005 1:03:00 PM by dan
# re: Sony’s Rootkit: First 4 Internet Responds
This anti-consumer attitude is even more obvious in the upcoming HD-DVD/Blu-Ray war. Both formats allow the content creators to not only disable all copies of a "compromised" disc, but also brick all players that have been compromised as well.
Buy the latest video and lose the ability to play a portion of your movies or turn your top of the line video player into a brick even if you haven't done anything illegal/unethical/wrong.
http://www.dvdsite.org/faq.html#issue2
Even though I was an early adopter of DVD (Pioneer DVL-700 @ $1200 and over 300 movies), there is no way I'm going to give either format a dime until this attitude changes. The thought of having my equipment disabled because the inevitable happened is unacceptable.
Prime Mover for Blu-ray Disc:
Sir Howard Stringer, Chairman & CEO
Sony Corporation of America
550 Madison Avenue
New York, NY 10022
And/Or
Ryoji Chubachi, President & CEO
Sony Electronics, Inc.
16450 West Bernardo Drive
San Diego, CA 92127
- From the dvdsite.org FAQ
11/7/2005 1:37:00 PM by Altair
# re: Sony’s Rootkit: First 4 Internet Responds
Nozzlehead - you said "You clearly already showed that the utility is available online, and does not need to be emailed"
Not true - Sony only makes the DECLOAKING patch available, which Mark pointed out does this in a manner that can lead to a system crash.
The uninstall for their DRM stuff is NOT downloadable - read Mark's previous blog (and he's still waiting for the uninstall - he requested it last week).
11/7/2005 1:48:00 PM by David Solomon
# re: Sony’s Rootkit: First 4 Internet Responds
Also, the comment does not explain why Sony won’t simply make the uninstaller available as a freely accessible download like they do the patch, nor why users have to submit two requests for the uninstaller and then wait for further instructions to be emailed (I still have not received the uninstaller). The only motivation I can see for this is that Sony hopes you’ll give up somewhere in the process and leave their DRM software on your system.
Has anybody received this uninstaller by email as promised ? because otherwise, there is also an alternative explanation: they do not have such utility and they are frantically rushing to develop one. The email thing could be just a lame way to gather some extra time.
11/7/2005 2:00:00 PM by pennino
# re: Sony’s Rootkit: First 4 Internet Responds
I was looking forward to Blu-Ray, even though Sony championed it... After this story broke, I'm not sure I can trust the format.
It seems like a bone-headed thing for Sony to do. At the time when they are trying to make serious money on their new format, they are stabbing consumers in the back?
Sony didn't make money off of BetaMax, they largely failed (in the US) on MiniDisc, nobody I know ever got behind DTS... now this, just before Hollywood finally chooses sides on the movie format of the future.
Consumers can hit Sony where it hurts by voting with their wallets... don't buy thier "enhanced" music discs, and opt for HD-DVD. I sure won't.
11/7/2005 2:05:00 PM by Lee Jones
# re: Sony’s Rootkit: First 4 Internet Responds
I just took my recently purchased Sony DVD±RW back to Fry's. I didn't need it immediately, but figured it was a good enough deal to keep.
As I was filling in the rebate form, I realized I could make a small contribution to the world by not keeping it.
And the rest is now history...
11/7/2005 2:08:00 PM by RichHubbins
# re: Sony’s Rootkit: First 4 Internet Responds
Sony's insistance that you provide them with your email address (and other information, I gather) before they will grant you access to an uninstall tool is completely unacceptable behaviour. They are holding you and your system hostage until you give over personal information (and it makes not difference if they promise you they will never use it for any other purpose--it's still morally wrong).
11/7/2005 2:14:00 PM by Michael J. Walker
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Thank you for your insight, ability and clarity.
I sure hope this gets picked up more by the mainstream press.
11/7/2005 2:49:00 PM by Guy
# re: Sony’s Rootkit: First 4 Internet Responds
Some peon at First4 is actually trying to argue with Mark Russinovich about how to write a device driver and what is the correct behavior for such a drive? That is just hilarious. Do these guys have any idea who Mark is? Maybe I should get some popcorn.
Up next: A barely literate high school drop-out argues with Shakespeare about how to write sonnets.
11/7/2005 3:10:00 PM by Rhomboid
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/7/2005 3:25:00 PM by Ian
# re: Sony’s Rootkit: First 4 Internet Responds
Regarding coverage by major news agencies...
I noticed a lot of folks thinking it odd that the major news corporations aren't giving this issue a lot of air time. Well let's think about this for a moment:
CNN - AOL/Time/Warner
Foxnews - 20th Century Fox
ABC - Disney
NBC - Universal
CBS - oh, wasn't this Columbia? cant' remember
Now lets look at the members of the RIAA/MPAA...
MPAA:
Disney
Sony
MGM Studios Inc.
Paramount
20th Century Fox
Universal
Warner Bros
RIAA: - too many to list.
http://www.riaa.com/about/members/default.asp
Needless to say, all the major news outlets are well represented. Their not going to rat on their bretherin.
11/7/2005 3:29:00 PM by Ian
# re: Sony’s Rootkit: First 4 Internet Responds
Has anybody received this uninstaller by email as promised ? because otherwise, there is also an alternative explanation: they do not have such utility and they are frantically rushing to develop one. The email thing could be just a lame way to gather some extra time.
Or here's another thought... The development and web teams at Sony are rushing to wait for feedback from their lawyers because their masters that be have threatened certian death with the release of such code and they're all in a tivvy to see if their truely breaking any laws (or atleast any that will cause them significant damage). Ah... but that would be more conspiracy mode kicking in wouldn't it....
11/7/2005 3:34:00 PM by Ian
# re: Sony’s Rootkit: First 4 Internet Responds
In an earlier comment in this blog it was suggested that we, the readers, will do nothing about this problem. I already have taken action.
I've checked my own machines for the rootkit.
I've instructed my wife and children to NOT buy any CD that lacks the CompactDisc labeling. I plan on letting Sony and my local music distributors know of my decision.
I will not be purchasing any Sony audio, video, or computer equipment. I find it amazing that Sony sells digital recording devices. It appears they want to have it both ways...
I've written to the Boston Globe to inquire as to why they have not covered the story.
I've written to the technology writer for the Washington Post to them them for their coverage.
I'm looking for other ideas on how to act. Any ideas?
11/7/2005 3:47:00 PM by Dennis Murphy
# re: Sony’s Rootkit: First 4 Internet Responds
Can I suggest that all this anger with Sony is turned into corporate bruising?
Go to www.karmabanque.com and start a boycott, ecourage the hedge-funders in and go from there...
Enjoy
11/7/2005 3:59:00 PM by BlogOT
# re: Sony’s Rootkit: First 4 Internet Responds
Regarding Ian's comment: Fox News ran this story on their website, and was linked from the top of the front page for a while (not as the main headline, but as one of the several just to the right of that).
Another comment. Sony claims that most users are uninterested in whether their CDs install rootkit software to their computers. But the whole point of the rootkit is to foil people who would attempt to disable/bypass the DRM software, meaning it targets technically savvy people who are interested in preventing rootkit infection.
In other words, most of Sony's customers get punished with rootkit infection even though it has no additional effect on their ability to rip the CD beyond what the DRM provides. Considering them to be within the "audience" for the rootkit, and then claiming that their ignorance forms a sort of democratically-decided consent, is ridiculous.
11/7/2005 4:13:00 PM by Dachannien
# re: Sony’s Rootkit: First 4 Internet Responds
@ Ian
If you post "research", get your facts right, you are not credible with your post.
I just checked Foxnews, they had article on November 3rd.
http://www.foxnews.com/story/0,2933,174334,00.html
11/7/2005 4:15:00 PM by Enough
# re: Sony’s Rootkit: First 4 Internet Responds
The Beeb's(BBC) coverage of this very blog.
http://news.bbc.co.uk/2/hi/technology/4413856.stm
11/7/2005 4:15:00 PM by Sharpy
# re: Sony’s Rootkit: First 4 Internet Responds
ABC News has picke this up also
http://abcnews.go.com/Technology/ZDM/story?id=1289711
11/7/2005 4:27:00 PM by goober
# re: Sony’s Rootkit: First 4 Internet Responds
So if I pirate the music I am safe but if I pay for it I am risking my system? Leaves little choice doesn't it sony?
11/7/2005 5:20:00 PM by Shaedo
# re: Sony’s Rootkit: First 4 Internet Responds
A quick question from a non-MS Windows user following this mess: Does this mean that MS Windows based machines with the Sony rootkit installed cannot be cleaned up if they don't have internet access at this time?
11/7/2005 5:25:00 PM by Tomas
# re: Sony’s Rootkit: First 4 Internet Responds
Thank you for continuing to update your blog, Mark.
To quote the good guy:
"There's no way to ensure that you have up-to-date security patches for software you don't know you have and there's no way to remove, update or even identify hidden software that's crashing your computer"
An extract from the BBC's commentry on the bad guys:
"First 4 Internet, which made the copy protection system for Sony BMG, said that it would work with anti-virus companies to ensure that false alarms were not triggered by its software.
Sony says that users have been adequately warned about the copy protection software in the licence agreement and had been told that it used proprietary software to play the CD."
http://news.bbc.co.uk/2/hi/technology/4413856.stm
---
Is everyone waiting for someone else to make the first move in regards to which Antivirus/malware vendor will sig Sony's rootkit?
Mark has already demonstrated that this rootkit is a vulnerability in that it's been proven to be exploitable. There are no shortage of threats on the Internet today plus you could argue that the rootkit itself is a threat.
Mark: If Sony contacted you asking you to update RKR to ignore their "product", how would you respond?
Are you in contact with anyone on the (newly renamed) "Windows Defender" team? Are they considering blocking Sony's rootkit?
I just watched your Microsoft Technet presentation on Malware from a few months back. Great stuff. You're the man.
--
More links:
They're trying to /. this site again:
http://games.slashdot.org/games/05/11/07/1221209.shtml?tid=233&tid=207&tid=10
/. article also provided a Google translated link to the Italian lawsuit
http://translate.google.com/translate?u=http%3A%2F%2Fwww.lastknight.com%2F2005%2F11%2F07%2Fsony-bgm-...
11/7/2005 5:25:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
I don't think those idiots have a cleaning tool developed yet. If they're smart- they'll have Mark scrutinize it before setting off a new wave of BSoDs and disappearing CDROMs.
Or maybe they have they have their dodgy uninstall ready to go (or so they think) but they are waiting on the legal team to finish the soul stealing license agreement to go with it.
11/7/2005 5:33:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
Mark, I do believe you've started a major backlash against DRM.
11/7/2005 5:51:00 PM by anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/7/2005 6:02:00 PM by Spider Rice
# re: Sony’s Rootkit: First 4 Internet Responds
I was looking forward to buying a shinny new PS3 when they get release, but now Sony can go fornicate themselfs with a pole for all i care. They aint getting any more sales out of me!
Only problem being the alturnative is Micro$oft. Looks like the 'Revoltion' and it's wacky looking controler is the go!
11/7/2005 6:07:00 PM by Spider Rice
# re: Sony’s Rootkit: First 4 Internet Responds
I am willing to BET that Sony will never release a FULL un-installer for the PUBLIC here is why.
Sony is using these CD's as a LEGAL DRM Shield test, more below:
Just Wondered if others thought these same thoughts?
I am sure as some have already stated, that this Sony Mess, is not considered a "Big Deal" but are we forgetting the possible Fallout from this?
It could go 2 ways:
No Legal Action Or Change Of Laws Because Of This
1. Others can and will use similar techniques and claim they were protecting their software and not just for Media related software, but for everything!
2. Many folks in these forums, who already are kind enough to volunteer their time to help others will be swamped with very complicated removal instructions.
3. When more than one of these type protection mechanisms is installed on a system, it will be a house of cards to determine, which one to un-install first. There will be NO right way, it will be based on the order the malware was installed, as well as how many of these you are infected with.
4. More systems than ever before will become infected with malware because the mechanism used is now provided by companies providing commercial software which have much more access to the general public and in many different forms than the current malware producers, including hackers.
5. Most people might not even be able to pre-scan the software prior to being installed because it may be compressed or encrypted in such a way that you cannot see what it will look like until fully installed. This would mean you would need to take the chance to install it, and check later.
6. Exploits of holes in these protection methods will allow non-seasoned hackers to take advantage of such said holes with no liability as well. Since in some cases what they did might not have been possible without the commercial companies software.
7. As stated on Mark's Blog, if Sony's software stands as is, as legitimate DRM. Then any company that makes software that fixes the problems caused by this Root Kit exploit could be in violation of DRM laws and face serious consequences. For example, Microsoft could not legally create a patch that prevents this type of behavior as a security update.
If ANY software author creates software which contains media files, they could claim the cloaking portion was to protect their Media files under DRM, which would make it illegal to remove their cloaking as well.
This would include currently known spyware as well. Which for all practical purposes would now restrict automated removal, which is now allowed, simply by using DRM as a shield by including Media files of any type during their installation process.
Legal Action Or Change Of Laws Because Of This
1. Finally, some sanity comes to the rights of ownership of computer systems, and the ability of International Companies to Join the malware industry will be at least hindered, if not stopped.
2. Companies that could supply automated methods attempting to remove this type of software from systems will not need to fear litigation because the creators of the software use DRM as their shield.
Very Dangerous Precedent Exists NOW!
It matters very little if this was oversight, malice or accidental. Equally, it matters just as little that a ActiveX method of removal is offered because it does NOT determine that this method of DRM is wrong.
Therefore it is tying the hands of any entity which would attempt to offer any automated process to remove this or any future derivative of these types of methodologies because it has been used as an excepted method for DRM.
The proof itself that Sony was NOT compelled to remove this method of DRM as a mandate, would itself prove this.
We are setting a very dangerous precedent for other companies, and/or individuals who create software.
This actually could be the most important precedent set since the personal computer was created if we are going to allow ANY entity to continue to do this in the future.
We will have almost removed the purpose of EULA and in fact created the "Act Of Downloading" ANYTHING removes the liability of the creator(s) of the software downloaded itself.
I hope people don't think I am going over-board here, because I think after all is said and done, there are many companies that are waiting in the wings to see how this is resolved, and that this moment based on how it all goes down, could be the turning-point of what rights the computer owner has, once they have accepted ANY download.
There are many more possible BAD things that could come out of this, I just tried to think of some major ones.
Sony, will NEVER release a PUBLIC un-installer that removes ALL of this, without legal action requiring them to do so.
This is a Cheap DRM shield test testing their legal rights, and I would also BET they WILL threaten ANY company that attempts to create an automated method to remove this from systems using DRM as their shield ;-), watch..
They have already INFORMED virus scanning compaines on how to not FLAG this as a false-positive get it?
See where they are going, they will SUE anyone who tries to remove it on a mass scale!
Comments, Please?
11/7/2005 6:40:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
This is only one thing that the Sony Software Developers have rushed to delivery. Before this story broke I had purchased a Sony Network Walkman, an MP3 Player. They shipped a program called Sonic Stage with the unit.
Now I have a massive collection of MP3s that I have legally ripped from CDs I own. (I’ve always had certain apprehensions against buying MP3's online, and not actually owning a product.) The Sonic Stage software was some of the worst software I’ve dealt with, ever. It crashed every time I ever tried to use it and ended up searching the web for a month trying to find a program that would enable me to actually use this $200 dollar piece of equipment I had purchased. I eventually found a program; however that’s not the point. The point is that Sony’s Software division is obviously either lacking the necessary knowledge of how to write programs, or they’re rushed so much so that they cant even finish what they were sent to do.
I personally will never buy another Sony product ever again. I had been a huge fan of Sony, and had been thoroughly looking forward to the PS3. However no longer will I be buying one of these. Sony has seriously screwed up, and no matter what kind of bad publicity they get, they will still continue to screw up.
The only thing we can do is simply stop buying their products and hope they eventually get bought up buy a company that actually has some thoughts in their heads.
11/7/2005 9:40:00 PM by Dave B.
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
I received an email from Sony BMG with a link to uninstall the software. I'm hesitant to publish it here, because it may have a limited number of uses.
If you want to send me an email address, I'll forward it to you. *Mark only please!*
Thanks for all of your work on this.
Tom
user is thwalters
mail server is yahoodotcom
11/7/2005 9:53:00 PM by Tom
# re: Sony’s Rootkit: First 4 Internet Responds
NtwkGestapo mentioned this earlier- Starforce.
Apparently this is not entirely new ground. I'm just starting to look into this but there is copy protection for PC games called Starforce. It's been around for a while now and it loads in 'hidden' device drivers as part of it's protection mechanism.
Here's an extract from an interview last year by Firingsquad :
"FiringSquad: There's an uproar among segments of the game community that StarForce is installed without user approval. Is this a potential legal concern for your company?
Abbie Sommer: There is no legal concern because before a user loads a game, he or she has agreed to accept the conditions of the end-user licensing agreement, typically known as a EULA. These are also known as click and go, or click and accept agreements. When you accept, you are saying I will load this game or application at my own risk, and have read and understood the terms. Or there will be a disclaimer that protects the publisher from damages of any kind due to their products? use. Our product is licensed to our customers, and becomes part of their product, so the user by accepting the terms, is giving approval."
http://www.firingsquad.com/features/starforce_interview/
And a response to it:
http://www.tgdaily.com/2005/10/01/the_war_on_game_pirates/index.html
It does have a freely available removal tool because removing the game does not always remove the Starforce device drivers:
http://www.onlinesecurity-on.com/protect.phtml?c=55
So you buy music/game/whatever - the "product". You install the licenced "product" with your consent by accepting the EULA. Well the copy protection/rootkit/drm/malware is part of the "product" and you agreed to it- so you're screwed right there is the argument the bad guys will take.
11/7/2005 10:00:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
This BSoD issue with redirected code pointers in driver chains is a classic programming problem that goes back before Windows was even written. The earliest example I know of was with MS-DOS (there's that MS again) TSR utilities (Terminate and Stay resident). You could install multiple utilities, each of which put a hook into the keyboard interrupt, so that it could detect its hot-key combination and activate when requested. Anyone remember a little tool called Sidekick from Borland? If you uninstalled your TSRs out of order, your system would lock up because it couldn't read from the keyboard anymore. There are probably older examples out there.
So these clowns committed a programming error that was known and documented over 20 years ago.
11/7/2005 10:07:00 PM by Where_Wolf
# re: Sony’s Rootkit: First 4 Internet Responds
Three Programmers testing their design for their Sony DRM release:
MOE, come here, it's done, it hides our stuff!
Great Larry are you sure it hides just our stuff?
Well Curly says he tried to rename notepad.exe to C:\$sys$notepad.exe and he could see it!
OK, lets tell Sony were ready for the first CD!
Curly "Certainly...yuck...yuck...yuck"
11/7/2005 10:15:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
I have a Sony Ericsson GC79 wireless card installed on my laptop. This card and the associated software is the interface between my laptop and the local wireless communications tower.
Theoretically, the software for the GC79 could intercept certain packets from a known IP address. This software could rummage around my computer for certain personal information and send it back to that IP address. Theoretically, this could be done in a way that is undetectable by my firewall, spyware, and virus software. The traffic could be made undetectable by any monitoring software such as Ethereal.
Now I do not know whether the GC79 software does such things, but I would like to check the GC79 software just to be sure. Has this been done by anyone? And what about the software for the GC75/82/83/85/89?
11/7/2005 11:56:00 PM by Chris Billings
# re: Sony’s Rootkit: First 4 Internet Responds
Hey! I recognized the 'blue screen' in Marks NTCrash2 test.
A couple of weeks ago my daughter tried to play a CD that needed administrator rights. I am not against copy protection, so I installed the software for her. It came with some nice, fancy extra features, so she was happy.
The next day I wanted to make a backup to DVD of my digital photographs with Pinnacle instant CD/DVD and there it was: the blue screen!
After restart, I send Microsoft an error report and got back a message, stating that the problem was known, it had to do with CD copy protection and they directed me to a link on First 4 Internet for an update. After that I was able make a backup of my photographs.
I was glad with the service Microsoft provided and how quick I was up and running again, but I had an awkward feeling about that copy protection mechanism.
I do not use my CD burner that often, but a couple of days ago I had again some problems with my cd burner. The process could not be killed and Windows could not be shut down.
What bothers me, is that I do everything to keep my computer clean and by installing a copy protection mechanism on a legal CD I get this kind of trouble.
Feels like punishment for buying legal CD's.
Today, I got a link from Sony to deinstall the DRM software.
After returning from work (and find out what experience other people had with deinstalling) I will try this out.
11/8/2005 12:25:00 AM by hans
# re: Sony’s Rootkit: First 4 Internet Responds
I hope this is true report: Sony to be sued in Italy:
http://theinquirer.net/?article=27508
Actually Alcei (which is a private italian organization similar to EFF) didn't sue. It delivered what in Italy is called an "esposto" that is, you go to the Police and tell them that you have the notion that a crime is being or has been committed and you explain why. In this case, they used the information provided by F-Secure and a technical analysis made by an italian engineer from the Technical University of Milan.
Now it's up to the italian authorities to decide if the information provided is enough to warrant an inquiry. If a judge agrees that a penal crime has been committed, he/she is obliged to press charges, otherwise you have to start a civil action by yourself.
11/8/2005 2:49:00 AM by pennino
# re: Sony’s Rootkit: First 4 Internet Responds
The problem with legal action against Sony is the EULA. I am guessing that one reason that they picked New York for their choice of law is that they felt that their EULA would more likely be confirmed under that law. Since ProCD (one of the worst decisions I have ever read, by a fairly well respected judge), courts have more than not affirmed shrinkwrap licenses, and the Sony EULA fits right in there.
If you get through the boilerplate, what their EULA says is that you can't sue them for anything they did, if you do, you have to do it in NY, under NY law, and if you win, you are limited to $5.
I think that the EULA can be broken, but if it is, it will have major impacts on EULAs and shrinkwrap licenses across the music AND software industry. So, with the money at stake, expect an expensive, brutal, fight.
Remember, they have the money to fight this and a real economic incentive to do so - they stand to lose a lot of money if their EULA falls. And it does take a lot of money to fight this sort of case.
I see a couple of approaches that might have some success:
1. Small claims court. Informal, and they probably won't fight that hard (they can't) - but the damages are very limited. Pin pricks at best.
2. Class action suits. Would need them persued in more than CA though. A coordinated national effort in a lot of states, and you could probably break the EULA in one, opening up some of the rest of the country. But this takes finding enough attorneys willing to do this on consignment.
3. State Attorney Generals. I have sent a complaint in to the CO AG, and suggest that you do to yours too. Can't hurt, and they are more likely to break a EULA than anyone, except for the Feds. The problem is getting their attention. Need to convince them that this is a big consumer issue.
4. The FTC. A big long shot. But again, maybe a large concerted campaign might get their attention. They have the best chance of breaking the Sony EULA, but I think would be hesitant to do so, given how common they have become in the software industry.
Again, some links to legal issues on my blog:
Sony DRM rootkit code (#19) EULA
Sony DRM rootkit code (#11) Letter to CO AG
Sony DRM rootkit code (#6) Trespass to Chattels
Sony DRM rootkit code (#5) Msc Causes of Action
Sony DRM rootkit code (#4)
Sony DRM rootkit code (#3) Cyberia-l suggestions
Sony DRM rootkit code (#2) Class Action
11/8/2005 3:12:00 AM by Bruce Hayden
# re: Sony’s Rootkit: First 4 Internet Responds
Sorry, in my last post, I meant "contingency fee basis" instead of "consignment". Somewhat different for class action suits.
11/8/2005 3:15:00 AM by Bruce Hayden
# re: Sony’s Rootkit: First 4 Internet Responds
I do find the Italian system interesting here, as compared to our American system. Here, you have to get either the police, a DA, or a state or federal AG interested. But it is invariably discretionary, and almost all will pass on this sort of thing. And without that, you can't proceed criminally.
On the other hand, I would worry in the Continental system if you were to get a judge to say, yes, there is a case, but then the prosecutors wouldn't really get behind the suit. As noted in my previous entries, this is going to be expensive to prosecute.
That said, I do expect that Sony is going to run into more trouble legally in Europe than in the U.S., more from a different business climate than due to different judicial systems.
But if they do, I would expect that they would just not use the DRM code there, and fight the importation of such here - if it did make economic sense to do so, which it probably wouldn't.
11/8/2005 3:26:00 AM by Bruce Hayden
# re: Sony’s Rootkit: First 4 Internet Responds
First a big thanks to Mark for discovering all this.
Computer Associates are now descriping Sonys DRM as spyware and plan to enable detection and removal in their antispyware from November 12.
Source: http://www.pcworld.com/news/article/0,aid,123454,00.asp
Hopefully all the other security companies will do the same.
11/8/2005 3:57:00 AM by Fuzhi
# re: Sony’s Rootkit: First 4 Internet Responds
Hi,
Perhaps when Mark has some "free time" he could document NTCrash2 so we know what to expect amd how we might use this tool.
What results should we see on "working" systems against ones with XCP-Aurora installed?
What other software out there don't pass the tests from NTCrash2 ?
Kind Regards
Simon
11/8/2005 4:41:00 AM by Simon Zerafa
# re: Sony’s Rootkit: First 4 Internet Responds
I can confirm that, with autoplay disabled, the rootkit never installs. I have autoplay disabled on every machine I work with regularly, as a security precaution for just such things as this. I was even quite able to rip the CD to mp3 tracks. RootkitRevealer showed my system to be clean afterwards. I am currently showing all my housemates how to disable autoplay.
11/8/2005 4:56:00 AM by Synkronos
# re: Sony’s Rootkit: First 4 Internet Responds
A CD is a type of FORMAT (Phillips wont allow the CD logo on these sony disks)
So we need a new Acronym for them
M usic D elivery S ystem been used here already so MDS it is.
11/8/2005 6:38:00 AM by Sharpy
# re: Sony’s Rootkit: First 4 Internet Responds
Reading hans' comment above (that he had an aries BSOD, but MS support recognized it as First 4 Internet's problem) it sounded like MS had seen it cause crashes before, so I checked in MS support articles. Sho' nuff: aries.sys crashed Media Centre . Quoting the relevant portion:
Transcript: Windows Media Center Edition, August 18, 2005
...
Andrew_MSFT (Moderator):
Q: i have encountered the "blue screen" and the mini-dump files says the sytem is looking for aries.sys. An exhaustive search on my system and the web has turned up nada. What is aries.sys and where can it be found or how can i shut it off? Thanks
A: Which version of Windows XP Media Center Edition are you running on your PC?
11/8/2005 7:09:00 AM by bazzargh
# re: Sony’s Rootkit: First 4 Internet Responds
Hans,
Just share the uninstall utility!
11/8/2005 7:22:00 AM by Raj
# re: Sony’s Rootkit: First 4 Internet Responds
I have an idea! Instead of wasting your money on another SONY CD, why not waste your money buying shares in the company instead... If enough people did this... well I'm sure you can see where I'm going!
11/8/2005 7:50:00 AM by Chunky
# re: Sony’s Rootkit: First 4 Internet Responds
Look folks, a race condition isn't that big of a deal. They almost never happen! After all, race conditions have been directly linked to only five deaths and a handful of serious injuries (Therac-25).
11/8/2005 9:48:00 AM by Daniel Einspanjer
# re: Sony’s Rootkit: First 4 Internet Responds
I received this blue-screen-o-death in your blog starting on september 23rd, and continuing into the week. http://blogs.technet.com/photos/markrussinovich/images/482355/original.aspx
On the Following Tuesday, Microsoft recognized it and sent me to first4dangerous rootkits for information. They told me I had to go to Sony.
I harrassed Sony until they relented and emailed me a link to go to to get an unistaller. I downloaded it and it appears to have do the job. They DID NOT email it to me.
Here is a series of letters I have written to Sony starting on Sept 23rd, and includes their letters as response.
http://www.mboxcommunity.com/SONY.html
anybody wanting to contact me with my long experience ranging back to mid september and this rootkit can email me at sugar@coldprofessionals.com
11/8/2005 10:44:00 AM by Mark C
# re: Sony’s Rootkit: First 4 Internet Responds
Oh, and the uninstall utility had a time bomb in it that caused it to stop working after download and a period of time passed. I do not believe it can be passed around to all, which means that Sony id determined to leave this on most computers.
11/8/2005 10:48:00 AM by Mark C
# re: Sony’s Rootkit: First 4 Internet Responds
Concerning the fact that big content-companies (movie and music companies) own all or most of the news agencies... That is something has had a number of people concerned over the years, and I think it is time some action was taken about that, too.
Many moons ago, when the motion picture industry was new, the studios owned the theaters. Because of that, it was not possible for independant movie makers, and small studios to get their movies into the theaters. At some point, the government realised this was a Very Bad Thing and banned the ownership by the studios of theater chains. It was declared BY LAW that the studios had to sell off all the theaters that they owned, and declared BY LAW that the theaters HAD to be independant of the studios.
What we now need is a groundswell of public demand that the entertainment industry (movie and TV studios, music companies, makers of novels and whatnot) be REQUIRED BY LAW to sell off all news-related companies, that there be a law that FORBIDS ANY MASS ENTERTAINMENT COMPANY from having any financial ties to ANY news agency.
There must also be a law that forbids monolythic news companies. That is to say, publishing conglomerates must not be allowed to get larger than a certain size, and cannot own more than X number of major newspapers and/or own more than X number of television or radio stations that contain news shows, especially if a station IS PRIMARILY a news station. They could own as many Discover Channels and Fun And Games Channels and Mystery Movie channels and Pure Science channels as they wanted, they just couldn't have more than X news channels, or place news shows on more than X different of their channels.
No, on second thought, I take that back. The entertainment industry should be kept completely seperate from the news industry. By law. Period.
And there must be several, equal, large, independant news corperations, instead of effectively One Big, Monolithic News Industry... and one with a massive case of GroupThink, at that.
In any event, if we DID have the news industry split off from the entertainment industry, we WOULD SEE much more attention brought to this Sony DRM bruhaha by the news industry. Or, to be more acurate, if we succeeded in getting the news industry split off from the entertainment industry, AND if we caused the news industry to go BACK to the state of being several independant, competing agencies (like they were SUPPOSED to be!!!), then the NEXT TIME something LIKE this Sony DRM debacle came along, there WOULD be much attention brought to it by the news industry, as a matter of course, and without us having to drag them kicking and screaming to it!
11/8/2005 1:51:00 PM by NomadOfNorad
# re: Sony’s Rootkit: First 4 Internet Responds
xgwpc wrote:
"I think that the scariest part of this whole fiasco is that now Mr. Russinovich is liable under the DMCA (under the Circumvention provisions - a prohibition on the removal of copyright management information (CMI) [1202(b)])."
If Sony tries to charge Mark with that, it may backfire on them as they are even more liable as Sony has committed computer fraud, negligence, and trespass. There is a class action lawsuit being taken up by the Green Welling law firm in California. When all is said and done, Mark will be hailed as a whistleblower, and Sony will pay millions in damages to affected users. BTW, IANAL.
11/8/2005 2:07:00 PM by Rafterman2
# re: Sony’s Rootkit: First 4 Internet Responds
As a half-way decent barrack room lawyer, I have two observations:
1. The UK has a law, the Unfair Contract terms law. Its a very powerful and under-used weapon against exactly this.
What it says is, if you are obliged to accept an unfair contract term because of major disparity in negotiating power (eg Sony v. individual), any court - even a small claims cheap court - can rule it unlawful and strike it out. For not much money therefore (under $100) a UK user could get a court ruling most likely.
2. A key part of contract law is consent. if you are asked to install "software" then the assumption isthat you agreed to install a game, because that is what you bought. There is considerable law about things that are not what they seem... and you are NOT considered to have agreed to their installation if it was not made clear. The corporate answer "well you agreed" does not carry weight, a good lawyer would crucify them for that one. ACLU anybody?
My $0.02
11/8/2005 3:10:00 PM by Jeff
# re: Sony’s Rootkit: First 4 Internet Responds
CA has classified it as well.
http://www3.ca.com/securityadvisor/pest/pest.aspx?id=453096365
Speaking of which doesn't CA and Sony have distribution deals? Wouldn't this be a conflict of interest?
11/8/2005 3:19:00 PM by Blind
# re: Sony’s Rootkit: First 4 Internet Responds
You see, they aren't just "installing software". They aren't even just installing software to protect their rights. They are fundamentally reconfiguring the core of your machine, in a manner that they know you have not authorized, that the manufacturer (microsoft) has not approved, that voids the warranty, and renders your property (a windows based copmputer) more liable to serious flaws including instability, denial of operation, loss of resources, loss of personal data, increased vulnerability to malware, increased likelihood of software conflict.....
11/8/2005 3:20:00 PM by Jeff
# re: Sony’s Rootkit: First 4 Internet Responds
I wan't to qualify the following from the outset, by saying that none of what I am about to say in any way shape or form mitigates Sony and First 4 in their use of this stealthy rootkit. Sorry for sounding like a EULA but I just wanted to make that clear.
I'm glad there have been comments clearing up the administrative priveleges issue. Basically the way I operate when downloading and installing new software is this:
if the software wants an admin password to install, I take a long hard look at a) the software itself b) the supplier (i.e. the website), and c) whether or not I really have to install it in the first place.
I know this is a moot point in relation to our current issues surrounding Sony and First 4, since their cd rootkit definitely did not require any downloading on the part of the user.
That said, if admin priveleges were required (and enabled), surely a music cd that asks you to enter your admin password should trigger alarm bells.
In short, if you don't have admin passwords enabled on your OS, enable them now. The inconvenience of typing your password in from time to time is surely outweighed by the extra protection it gives you against software that requires low-level (ie device driver) access.
I know its obvious, but only system utilities, network software, and software that needs low level access should need admin priveleges. Be suspicious of anything else.
11/8/2005 3:33:00 PM by ruy_lopez
# re: Sony’s Rootkit: First 4 Internet Responds
I received the uninstall link email from Sony today. After following the link, it took me to an Active X page that had the Sony BMG logo on it and the words, "Welcome to the SonyBMG Customer Support Website. I wish to uninstall any software that has been installed after inserting a copy-protected Enhanced CD." There was a button labled "Uninstall" which did not allow you to download an executable file, but rather, ran the file remotely. After it completed, it displayed a button to "Restart". After doing this, I ran Hijack This and found two XCP associated items:
Service: XCP CD Proxy (CD_Proxy) - Unknown owner -C:\Windows\CDProxyServ.exe
DPF: {4EA7C4C5-C5C0-4F5C-A008-8293505F71CC} (CodeSupport Control) - http://www.xcp-aurora.com/clients/SoftwareUpdate.cab
Not only that, but after looking at F-Secure's site for the XCP DRM Software, I discovered that seven other files associated with it were still on my machine in the windows and system32 directory. When I checked my running processes, CDProxyServe.exe was still running.
So the question is, what did the uninstaller do? It certainly didn't uninstall everything.
11/8/2005 4:00:00 PM by Nearly
# re: Sony’s Rootkit: First 4 Internet Responds
Steve Gibson of www.grc.com and Leo Laporte of www.leoville.com have a Security Now! / TechTV podcast on this issue at http://www.grc.com/SecurityNow.htm
Nice to see this getting attention from other programming experts.
11/8/2005 4:18:00 PM by EdwardN
# re: Sony’s Rootkit: First 4 Internet Responds
I'm glad SANS picked up on this story in its latest NewsBites.
11/8/2005 4:39:00 PM by Dmitriy Blok
# re: Sony’s Rootkit: First 4 Internet Responds
I have been communicating with Brian Krebs of the Washington Post here is a new story:
Posted at 06:35 PM ET, 11/ 8/2005
Calif. Lawsuit Targets Sony
http://blogs.washingtonpost.com/securityfix/
It should be noted that the court filing is DEMANDING a Jury Trial and all detail of the filing and much more can be seen in Brian's article at the link above.
11/8/2005 6:15:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
Thanks Blind- this is great.
I wonder if Sony will go after CA. They list the player as spyware and the rest of it as a trojan. Sounds good to me. It doesn't specifically list the stealthing technology it uses in it's first 'variant'.
Extract from the CA Spyware Information Center:
XCP.Sony.Rootkit
Reasons For Retention
Installs without user permission, presenting only a vague and misleading EULA
Changes system configuration without user permission at time of change.
Defends against removal of, or changes to, its components
Silently modifies other programs' information or website content as displayed.
Includes mechanisms to thwart removal by security or anti-spyware products.
Cannot be uninstalled by Windows Add/Remove Programs and no uninstaller is provided with application.
http://www3.ca.com/securityadvisor/pest/collateral.aspx?cid=76345
We'll have to monitor their emerging threats page:
http://www3.ca.com/securityadvisor/pest/emerging.aspx
11/8/2005 6:17:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Nice work finding opening our eyes to the nastiness going on.
However, I hope you have a lawyer on retainer. I'm no lawyer, but there are things in your blog which raise red flags on my radar.
#1. Inflammatory statements against First-4-internet (Stating they are incompetant could make you liable for any business losses they can tie to statements made by you in your blog).
#2. Reverse engineering and/or releasing trade secrets. (Again, First-4-Internet would be the suitor)
#3. Inflammatory statements about Sony Music. Sony is in the top-10 most evil companies on earth, and it wouldn't suprise me if they targeted you as a convenient excuse for why their record sales continue to fall into the gutter.
Good luck, keep up the good work, please protect yourself as you expose the truth.
11/8/2005 8:45:00 PM by dohb0y
# re: Sony’s Rootkit: First 4 Internet Responds
http://blogs.washingtonpost.com/securityfix/
Washington Post
Brian Krebs on Computer Security
Posted at 06:35 PM ET, 11/ 8/2005
Calif. Lawsuit Targets Sony
A class-action lawsuit has been filed on behalf of California consumers who
may have been harmed by anti-piracy software installed by some Sony music
CDs. A second, nationwide class-action lawsuit is expected to be filed
against Sony in a New York court on Wednesday seeking relief for all U.S.
consumers who have purchased any of the 20 music CDs in question.
Experts say the Sony CDs use virus-like techniques to install digital rights
management software on computers. Windows users cannot listen to the
protected CDs on their computers without first installing the software,
which hides itself on the users' system and cannot be uninstalled by
conventional removal methods.
The California lawsuit, filed Nov. 1 in Superior Court for the County of Los
Angeles by Vernon, Calif., attorney Alan Himmelfarb, asks the court to
prevent Sony from selling additional CDs protected by the anti-piracy
software, and seeks monetary damages for California consumers who purchased
them.
The suit alleges that Sony's software violates at least three California
statutes, including the "Consumer Legal Remedies Act," which governs unfair
and/or deceptive trade acts; and the "Consumer Protection against Computer
Spyware Act," which prohibits -- among other things -- software that takes
control over the user's computer or misrepresents the user's ability or
right to uninstall the program. The suit also alleges that Sony's actions
violate the California Unfair Competition law, which allows public
prosecutors and private citizens to file lawsuits to protect businesses and
consumers from unfair business practices.
Himmelfarb was on a plane at the time of this writing and could not be
reached for comment. But a court-stamped copy of the lawsuit he filed is
online here (PDF).
Scott Kamber, an attorney in New York, said he plans on Wednesday to file
class-action suits targeting Sony under both New York consumer protection
statutes and a federal criminal statute that allows civil actions.
"This situation is particularly egregious and surprising from a company that
should be familiar with concerns people have with programs crashing their
Windows computers," Kamber said. "What Sony is saying with this software is
that 'Our intellectual property is more deserving of protection than your
intellectual property,' and Sony can't be allowed to get away with that."
Sony spokesman John McKay declined to comment on the suits.
I wouldn't be surprised if other lawyers and law firms around the country
are also preparing to file similar suits.
As I wrote in a story last week, "Sony's move is the latest effort by the
entertainment companies to rely on controversial 'digital rights management'
(DRM) technologies to reverse a steady drop in sales that the industry
attributes in large part to piracy facilitated by online music and movie
file-sharing networks like Kazaa and Limewire."
Experts who studied the Sony program said it has a built-in file-cloaking
feature that could also be used by attackers to hide viruses and other files
on a user's computer, and that conventional means of removing the
anti-piracy software renders the user's CD-Rom drive inoperable.
In response to public criticism over the invasiveness of the software, Sony
last week made available on its Web site a "patch" that would prevent its
software files from hiding on the user's system. But according to further
research by a variety of security experts, that patch can lead to a crashed
system and data loss.
By Brian Krebs | Permalink* | Comments (0) | TrackBack (0)
11/8/2005 9:08:00 PM by srynas
# re: Sony’s Rootkit: First 4 Internet Responds
It's a bit late but it had to happen over the following quote by a Sony exec:
""Most people, I think, don't even know what a rootkit is, so why should they care about it?""
http://www.theregister.com/2005/11/09/sony_drm_who_cares/
11/8/2005 9:11:00 PM by geek27
# re: Sony’s Rootkit: First 4 Internet Responds
"Most people, I think, don't even know what a rootkit is, so why should they care about it?"
^ That's like saying, "Most people don't know what a thermite grenade is so they won't care if an active one is underneath their pillow"
Anyways, thank you very much Mark for your hard work. I don't have any "infected" Sony CDs but what you have done is a service to computing-kind :)
11/8/2005 9:56:00 PM by Aaron
# re: Sony’s Rootkit: First 4 Internet Responds
If any hacker were to do this they would be prosecuted for cyber crime. Why are law makers and enforcement agencies not taking action against Sony. Personally I am passing this information around to as many people as I can and encouraging anyone I know to boycott Sony. I also wish there would be a good scanner and uninstaller available to identify this and other similar problems.
Mark, a job well done! Stay the course!
11/8/2005 10:26:00 PM by SchneiderIS
# re: Sony’s Rootkit: First 4 Internet Responds
The irony is that it's SAFER for your computer to download pirated MP3/OGG files of Sony artists than it is to buy and listen to a Sony CD.
11/9/2005 1:28:00 AM by VXDguy
# re: Sony’s Rootkit: First 4 Internet Responds
EULA's I hate em they lie they cheat and they think they have the law on their side.
Well add this little gem to your armoury. EULALYSER.
http://www.majorgeeks.com/EULAlyzer_d4759.html
Bright Light always make creepy crawlies run for cover. You hear that sony!!
11/9/2005 4:40:00 AM by Sharpy
# re: Sony’s Rootkit: First 4 Internet Responds
For long I have been observing Sony's negligence towards people friendly approach. Other than few products like walkman, psp et al., Sony has never tried to adapt any technology that has been widely accepted by the public.
They were still trying to push their own formats and in doing so forget what people expect out of them. This suggests what happened in case of BetaMax, ATRAC and now the long going war of BlueRay...
I thought though sony was trying to push its own format.. it was revolutionising the market and providing new options.. but when it comes with such flaws as happened in DRM as well.. I'm losing all my hopes against the electronics major that I admired once....
11/9/2005 7:17:00 AM by Srikanth
# re: Sony’s Rootkit: First 4 Internet Responds
Just like most big business and government, this story is starting to lose steam. The media outlets are losing intertest after devoting the standard nanosecond of coverage. It's up to us folks to keep this going. Even with the class action suits being filed, Sony knows this will bog down in litigation and ensure a nice holiday profit for this year and next Tell everyone you know. Hit Sony where it hurts, IN THE WALLET...keep yours closed!
11/9/2005 7:31:00 AM by Nads
# re: Sony’s Rootkit: First 4 Internet Responds
Made it in An Australian newspaper
http://theage.com.au/articles/2005/11/03/1130823323159.html
11/9/2005 7:46:00 AM by Mightyman
# re: Sony’s Rootkit: First 4 Internet Responds
Thanks for bringing this to everyone's attention Mark.
In case anyone missed it, you can sign the "Boycott Sony" petition at http://www.petitiononline.com/bcsony/petition.html
Sony are OFF my Christmas list - forever!
11/9/2005 8:37:00 AM by Elwood Herring
# re: Sony’s Rootkit: First 4 Internet Responds
@ Mark C, I read your letters found on http://www.mboxcommunity.com/SONY.html - Very nicely done! Not everyone would go through the trouble of writing Sony as you have. Your daughter has excellent taste regarding the CD you mention. I feel sad this has happened to her. Sony really should take notice to a well known business phrase " For every one complaint, there are at least 10 complaints that go unheard."
Did anyone else yet test this so-called "uninstall" from Sony yet? This is rediculous! You'd think they would make this immediately available to people in the wake of this madness that they've caused! After reading Mark C's and Nearly's thorough review on this gives some indication that perhaps this "uninstall" is NOT going to do what they say it will do afterall.
11/9/2005 8:42:00 AM by CindyRilla
# re: Sony’s Rootkit: First 4 Internet Responds
oh well.
I got a great idea to start my own business now.
I will start to write my own boot device driver.
Plan is to present this as THE ultimative game copy protection to the clueless game developers.
If you once installed the protected game it will alter your operating system at boot time in a way that it will only boot if you have inserted the original game cd in your drive.
it will disable everything and only give you the ability to play the game.
if you dont want to play anymore you need to write an email to me from another WORKING machine and I will call back in about 3 weeks and tell you the unique magic keyword to disable the boot protection.
yeah I will make BIG money with this because all the stupid people out their would by the cds.
But wait, if I sell such a sort of virus to a view million of people I would face about 50 years of jail and a few million $ of refunds to the stupid customers who blame me for their own stupidity to by the protected games.
this kind of protection IS possible though.
but @First4Internet:
who the *uck do you think you are?
did you think about what you are doing here?
did you think about what you install on my system without MY acknowledgement?
you are only some very clever virus authors (or very stupid, future will tell).
everyone talks bad thinks about holyfather (hackerdefender author) because he is selling edited and undetectable rootkits to people who pay for them.
the main difference between his and your business is:
people who buy from him know what they get, while you sold your rootkit to millions without their knowledge.
this is just too crazy to be true.
you dropped yourself into big problems.
11/9/2005 10:14:00 AM by stefan stephan
# re: Sony’s Rootkit: First 4 Internet Responds
Can you please clear up one point which has confused me (and several other posters by the look of it):
This "Service Pack" which Sony refers to: is it Microsoft's XP pack, or Sony's own?
Thanks - keep up the great work.
11/9/2005 3:15:00 PM by Elwood Herring
# re: Sony’s Rootkit: First 4 Internet Responds
Sony's (First 4 Internet's).
11/9/2005 3:17:00 PM by Mark Russinovich
# re: Sony’s Rootkit: First 4 Internet Responds
Are you a resident of California? Have you purchased one of the Sony/Columbia music CDs with the First 4 Internet DRM schemes?
If so please contact me ASAP at eleeAT1to1lawDOTcom.
Please SAVE your receipt and if possible, take a screenshot of the CD playing software installed on your computer.
I'm an attorney in Los Angeles, California and I'm investigating bringing a class action lawsuit against Sony.
The foregoing is an ADVERTISEMENT. I am licensed to practice law in the jurisdictions of California and New York only.
11/9/2005 3:20:00 PM by rocky
# re: Sony’s Rootkit: First 4 Internet Responds
If you did un-install this mess, can just the ACT of playing one of these CD's cause the original version to be re-installed?
If so, does Sony owe people a FULL list of which of these CD's can/could re-install this mess, posted SOMEWHERE on their site?
11/9/2005 3:42:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
Does First 4 Internet ALSO owe the public a list of what this software is currently being used with.
Example: Other CD's or DVD's from other companies, other software products and the like?
11/9/2005 3:49:00 PM by ZOverLord
# re: Sony’s Rootkit: First 4 Internet Responds
i hope those lawyers roto-rooter sony in the arse
11/9/2005 10:16:00 PM by jimmy
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/9/2005 10:16:00 PM by jimmy
# re: Sony’s Rootkit: First 4 Internet Responds
The problem now is that Sony can't admit they have done anything wrong.
If they cave in to demands for a freely available uninstaller and a public apology it would become amunition against them in the various lawsuits that are being filed.
Oh well, untill I see the FORMAL & PUBLIC apology their lawyers surely won't allow them to make at this point, I won't be buying or reccomending ANY Sony products.
Kinda painted themselves into a corner here.
Damnd if they do and damed if they don't. I feel zero pity for them in a situation they created for themselves with this bit of hubris...
11/10/2005 4:40:00 AM by dc4bs
# re: Sony’s Rootkit: First 4 Internet Responds
I am more surprised with Sony’s reaction (or lack of) than with the technical issue itself.
Disguising this malware as a software player might have been the act of a desperate, clueless middle manager.
But it’s clear now that this is corporate policy of a desperate company that is no longer competitive in its main market (consumer electronics) and is trying to squeeze money everywhere, no matter what.
Long Live the iPod. Hurrah to Xbox 360.
11/10/2005 6:30:00 AM by MauroS
# re: Sony’s Rootkit: First 4 Internet Responds
When I think of REALLY effective antipiracy measures that actually help the lables' bottom line, I think of the Skinny Puppy double album Brap 3&4 a few years ago...
Along with all sorts of rare tracks, it included virtually every music video the group had ever made along with lots of other multimedia goodies..I almost never buy new CDs, but I couldn't find it used, couldn't get all the videos from napster, and couldn't figure out how to copy the CD tracks along with the multimedia onto one disc...
And you know what? Not only did I buy one $20 double disc, but when i lost it I bought ANOTHER one, something I've certainly never done with any other album before, and was very satifised with my purchase.
Imagine anyone doing that just so they can get the new Celine Dion single to spin a couple times?
Now if these people would only spend 1/2 as much money as they are giving to these crooks at F4I actually INNOVATING in a way that helps the consumer, ie putting relatively low resolution interviews with the bands, music videos, guitar tabs, concert recordings, etc. etc. they might actually make a dent in piracy.
Unfortunately, they do not understand basic psychology-most people, when given a challenge, will try to surmount it. Most people, when given something for free, will feel obligated to give something in return (ie buying a CD of a really great group you found on napster).
Sadly, the whole business of record labels has gone into a bunker mentality-not expansion, thinking of new ways to make the records more enticing, but contraction, paranoia, swinging their swords like Don Quixote.
Remember, record execs are typical middlemen, rightly paranoid because their traditional role, informing music buying consumers about music that interests them, is becoming obsolete, and they are going to have to get real jobs soon. Maybe the clever ones will find another group of financially naive people to exploit.
Major labels have already cost us listenable mainstream radio in this country, a crime in and of itself. They must not cost us free distribution and mashability of digital content.
If enough people stop buying from majors, they will go out of business and bands will be forced to indies or be forced to self-promote, a much better system for everybody.
Do your part to hasten the obsolescence of these parasitic organizations, and help your friends do the same. We will all be much better off. It is simply indefensible supporting business practices such as this any longer.
11/10/2005 11:57:00 PM by zyodei
# re: Sony’s Rootkit: First 4 Internet Responds
I would suggest that ALL people in the US who read this, take the opportunity to visit:
http://www.ala.org/al_onlineTemplate.cfm?Section=alonline&template=/ContentManagement/ContentDisplay...
This month, the public are able to post comments which will be considered in the review of DMCA next month. Everyone should take the opportunity to post protest about DRM techniques being used. Judging by the amount of noise this Sony rootkit issue has raised, I expect if enough people post to the comments section below:
http://www.copyright.gov/1201/comment_forms/index.html
They will be forced to listen and act on consumer concerns.
11/11/2005 10:23:00 AM by Alexander Hanff
# re: Sony’s Rootkit: First 4 Internet Responds
My law firm is investigating the situation surrounding “rootkits” on Sony-label CDs. In connection with our investigation, we are interested in learning more about the experiences consumers have had with those CDs. I can be contacted at (212) 239-4340 or, by e-mail, at tciarlone@lawssb.com.
11/11/2005 11:56:00 AM by Tom Ciarlone
# re: Sony’s Rootkit: First 4 Internet Responds
http://news.ninemsn.com.au/article.aspx?id=71751
READ THIS!!!!
Sony is suspending production of copy protected cds!
11/11/2005 6:24:00 PM by Jessica
# re: Sony’s Rootkit: First 4 Internet Responds
This is so bad... they built it to stay engaged even if you boot to Safe Mode! I hope they go to jail. I used System Restore since I just fell for this 2 days ago. Does that solve the problem??? Can it be that easy?
11/12/2005 12:19:00 AM by colorado dreamer
# re: Sony’s Rootkit: First 4 Internet Responds
Looks like Microsoft are getting involved now!
http://isc.sans.org/diary.php?storyid=845
11/13/2005 11:19:00 AM by Dan
# re: Sony’s Rootkit: First 4 Internet Responds
This is the new detection and disabling tool for the Sony-BMG XCP software:
http://tracker.zaerc.com/torrents-details.php?id=4106&hit=1
(it disables part of it at least, anyway -- and without addding more sh!t unlike the '''disabler''' from $ony-BM)
11/14/2005 6:54:00 PM by tnuocca342
# re: Sony’s Rootkit: First 4 Internet Responds
"This is the new detection and disabling tool for the Sony-BMG XCP software:
http://tracker.zaerc.com/torrents-details.php?id=4106&hit=1
(it disables part of it at least, anyway -- and without addding more sh!t unlike the '''disabler''' from $ony-BM)"
has anyone tested this out????
i think i downloaded this onto my computer because i now cannot rip files from cd's without a wretched squeal.
i already tried the "sc delete $sys$aries" method to no avail and i downloaded the symantec ryknos removal tool. after running the tool, a window appears saying 'ryknos has not been found on your computer'.
do i need to be patient and wait for an uninstaller to become available? please help!
11/14/2005 8:46:00 PM by kelly o
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/15/2005 11:51:00 AM by The-mad-professor
# re: Sony’s Rootkit: First 4 Internet Responds
Sony are showing their rampant disregard for consumers in Britain as well.
Apparently they are setting wholsesale prices higher to internet retailers than they set to high street retailers.
[URL]http://www.timesonline.co.uk/article/0,,2-1872549_1,00.html[/URL
I have never thought of globalisation as bad, however the recent actions by Sony might have to make me reappraise my viewpoint!!
Chris
11/15/2005 11:53:00 AM by The-mad-professor
# re: Sony’s Rootkit: First 4 Internet Responds
I think Mark is somewhat protected from a legal attack from Sony based on circumventing the copy protection because of one of the four exemptions to the DMCA ( Source ):
"Librarian of Congress James Billington issued four narrow exemptions to the Digital Millennium Copyright Act (DMCA) prohibition on circumventing digital copy-protection technologies. [...]
Billington’s October 28 announcement included two new exemptions: one allowing circumvention of access controls that block read-aloud or text-to-Braille devices, and another permitting circumvention in the use of computer programs and video games whose formats have become obsolete. He renewed exemptions issued in 2000 that allowed access to the lists of websites blocked by filtering software and the circumvention of access-control mechanisms that block because of malfunction, damage, or obsoleteness. The exemptions expire after three years, after which they must be renewed by LC’s Copyright Office.
Surely the sloppy code in Sony's DRM rootkit, as well as it's "removal tool" qualifies as "malfunction" or "damage". I suspect this will be the argument that Microsoft makes with the December addition of the Sony rootkit to it's malware removal tool.
11/15/2005 2:01:00 PM by rdcpro
# re: Sony’s Rootkit: First 4 Internet Responds
(Sharpy) " A CD is a type of FORMAT (Phillips wont allow the CD logo on these sony disks). So we need a new Acronym for them. Music Delivery System been used here already so MDS it is."
If the nominations are still open, I have a couple of candidates:
MERDE - Music Encrypted Rootkit Delivery Effort
SHIT - Sony Hijacks IT
11/16/2005 6:01:00 PM by Ken
# re: Sony’s Rootkit: First 4 Internet Responds
Surely the sloppy code in Sony's DRM rootkit, as well as it's "removal tool" qualifies as "malfunction" or "damage".
Unfortunately, the rule as written only refers to damaged or obsolete dongles that prevent access to the media in question.
Here, the problem is with horrible malware that interferes with machine operation totally unrelated to the content it's supposed to be protecting.
An exemption allowing the removal of such malware would seem like a no-brainer (and perhaps one might argue that it's the case implicitly) but the rules do not at present explicitly provide for it.
11/17/2005 12:50:00 AM by supercat
# re: Sony’s Rootkit: First 4 Internet Responds
Mark,
Geez! Am I ever glad you're on our side. Thanks for all your hard work.
11/17/2005 11:11:00 AM by KLeonard
# re: Sony’s Rootkit: First 4 Internet Responds
I have found a hack for these xcp crap discs. Install zonealarm pro version 6.0.667.000. Also install Musicmatch 10.00.4015
When you insert the disc in your drive zonealarm pro firewall stops the software from running and somehow shields the pc and allows musicmatch to read the disc Then musicmacth rips tracks into MP3 at whatever bitrate you prefer.
Musicmatch is the only ripping software that I have found that will read these discs. But only after Zonealarm stops the xcp software from running.
TAKE THAT SONY/BMG
11/17/2005 7:25:00 PM by TXMP3
# re: Sony’s Rootkit: First 4 Internet Responds
Don't think Mark has anything to worry about with First 4 Internet.
Just read an article (sorry I do not have the url right now) and it is blasting F4I for using "tightly integrating" open source code from
LAME into their XCP software.
IF F4I did infact use open source in their software, then THEIR sofware MUST also be open.
:-)
11/18/2005 9:33:00 AM by b0rd3r g4l
# re: Sony’s Rootkit: First 4 Internet Responds
Symantec has posted a removal tool at http://securityresponse.symantec.com/avcenter/venc/data/securityrisk.aries.html
I don't know if it works, or how, but maybe someone here can evaluate it.
11/18/2005 2:12:00 PM by Kate Halleron
# re: Sony’s Rootkit: First 4 Internet Responds
The Department of Homeland Security labels XCP a serious threat. See
http://www.us-cert.gov/current
11/18/2005 2:54:00 PM by I am One of One
# re: Sony’s Rootkit: First 4 Internet Responds
In the immortal words of Howard Beale from Network : "I'm mad as hell and I'm not going to take it any more!"
I think that sums up my feelings very nicely.
11/19/2005 2:18:00 PM by dapanther
# re: Sony’s Rootkit: First 4 Internet Responds
In a nutshell...Sony needs to pay all of us administrators, and self employed business owners that have to remove their crap, for the time it takes to truly rid a system of their rootkit. PERIOD. AND WE ALL (Those of us that will be dealing with the removal NOW, a.k.a. before a proper removal system/procedure is produced,) SHOULD BE BILLING SONY FOR THE HOURS IT TAKES US, AND AT THE COMMONLY ACCEPTABLE RATE... SAY $95.00 Per hour, per system. The average person shouldn't have to pay these rates because SONY BLEW IT! I no longer own SONY anything, and WILL NEVER AGAIN, MY CHILDREN ALL THREW OUT THEIR CDS and CD PLAYERS OF THEIR OWN FREE WILL! I suspect they won't be buying SONY anything anytime soon either. Even the kids Playstations are in the trash right now, and THEY TOSSED IT!
Dear SONY, you had better get a proper removal tool out and in the public ASAP. No excuses. The Tsunami of this backlash is only getting bigger the longer you wait.
11/21/2005 6:40:00 PM by Tinker
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/22/2005 12:42:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/22/2005 12:42:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
This post has been removed by the author.
11/22/2005 12:45:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
Sony and First 4 Internet don't care for intellectual property protection - they are just greedy companies after their own self-serving interests. How come? Because they insist on using the term CD to refer to items that are not. To quote the BBC website:
Philips, who defined the CD standard and then made it widely available, has been very clear that these music delivery systems do not count as Compact Discs and cannot use the CD logo.
As far back as 2002, Philips representative Klaus Petri told Financial Times Deutschland that "those are silver discs with music data that resemble CDs, but aren't".
So much for respecting intellectual property rights! This hypocricy is everywhere in the media industry. Look at how regional coding on DVDs was meant to protect the right ot release films at the cinema in a controlled way, yet is used on even re-issued DVDs. I think the industry couldn't do more to encourage people to pirate media.
11/22/2005 12:48:00 PM by nico
# re: Sony’s Rootkit: First 4 Internet Responds
Help!
Ever since the xcp.rookit has been showing up on my spyware scanner, my cd and dvd drives aren't being detected on my computer. I did a system restore and that worked for a little while, but then the xcp.rookit popped up on my spyware notification again, and now my dvd & cd drives have stopped working again.
Also, even though my spyware says it's blocking it, when I go to my blocked items lists it's not listed there. My other spyware/virus programs (McAfee, Spybot, Adaware) don't detect it!
11/24/2005 4:56:00 AM by Liz
# re: Sony’s Rootkit: First 4 Internet Responds
Is there any way to see if you have this rootkit on your computer ? I have a Sony disc that has it , but I am not sure if I played the disc in here .
11/24/2005 11:02:00 PM by Keith
# re: Sony’s Rootkit: First 4 Internet Responds
Good on you Mark, I give you a round of applause. This whole issue is sheer idiocy. I bought one of the cds with the protection on it, and it did not work in my SONY discman or my car cd player, and because in australia it's illegal to backup music and movies, i couldn't legally p2p the cd. i was mad, because i couldn't even listen to the cd i PAID for! what the hell, sony?
12/4/2005 1:44:00 AM by Jordo1001
# re: Sony’s Rootkit: First 4 Internet Responds
First, Mark, thank you for all the great work.
Sorry for my poor English.
One small comment:
I have read message, posted by Jason : 11:50 AM, November 07, 2005
and followed the link in this message: http://www.sony.net/SonyInfo/IR/info/contact/index.html
I was surprised, when in the bottom of this Sony's page I have read the text:
>Notice of software trouble caused
>by Microsoft Windows' new
>security update program
>If you install Microsoft Windows
>Security Update program
>for "Windows XP," you might have
>trouble opening streaming video
>files in RealPlayer and other >programs.
> Please find instructions on how to set up Windows Firewall so that you may install Windows Update and Windows XP Service Pack 2.
And there was a link to http://www.sony.net/SonyInfo/IR/info/contact/realplayer.html web page.
On this page there was a recommendation, how to enable internet access for RealPlayer through WinXP SP2 Firewall.
I do not use RealPlayer. Is "RealPlayer" a Sony software? If so, it is will be funny, if it also content some undeclared malfunctions.
Anyway, after all, I can not trust Sony, and do not want to allow any Sony software to overhead Firewall security settings / limitations.
I hope, all planet web society will become a force that con stop Sony’s viruswriters!
Vadim.
12/22/2005 8:21:00 AM by Vadim
# re: Sony’s Rootkit: First 4 Internet Responds
I have always avoided "protected" media. Until now the main reason for this is the unreliability of most schemes that I have seen. Now, of course I have a new reason to avoid such products.
What they have done amounts to theft. It is much the same as criminal trespass on ones property.
Kudos to Mark for ferreting out the truth and pursuing it.
One comment on an earlier post: I do not see how Sony can be an example of "American corporate greed." Sony corporation is not an American company. Apparently there is no shortage of greed in the world.
12/26/2005 3:35:00 PM by Analogue
# re: Sony’s Rootkit: First 4 Internet Responds
Does it seem to anyone else that First 4 Internet is Sony's voice?
12/26/2005 8:47:00 PM by kochrep
# re: Sony’s Rootkit: First 4 Internet Responds
A friend of mine told me about DC++.
I saw that program working. It looks promising.
FROM NOW ON I WILL NOT BUY ANY MORE PROTECTED CD/DVDs. At least not from Sony.
I will use DC++.
1/7/2006 4:15:00 PM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
I picked up the new Kate Tunstall album and read on the back that the CD had copy protection and might not work on some CD players for example Car systems. This is eye-bulging stupidity from the Music industry and ensured that I did not part with my money
1/9/2006 6:47:00 AM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
i like sony cd/dvd's
but the d++ sucks
1/9/2006 10:10:00 AM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
I have discovered that I am a "victim" of Sony's "protected" content CDs.
I have had to go some considerable trouble to remove the blasted stuff from my computer only to be told recently by our IT Sytems bloke that all I ahve managed to do to my laptop is to alter the nature and form of the offending software.
I then used a packet sniffer and discovered he was right, there is still "phone home" software installed.
So now they want to steal my bandwidth too.
I feel that until Sony pays me damages in compensation I hold them and their immaterial property rights in contempt. Heck, why I don't just distribute copies of all their media free to everyone I know until I feel my loss sufficiently satisfied.
1/13/2006 6:17:00 AM by Customer Unknown
# re: Sony’s Rootkit: First 4 Internet Responds
My opinion is this, First 4 products must be destroyed and also they website must be hacked. By Sony is little different,we know they are good in building nice hardware but they are to stupid to write a program. Kill the system!!!!!
4/21/2006 4:12:00 AM by Anonymous
# re: Sony’s Rootkit: First 4 Internet Responds
All these has the effect on me that I will never again buy a Sony-CD
7/21/2006 6:20:00 AM by Jack
0
Likes
Version history
Last update:
Nov 09 2023
11:09 AM
Updated by:
Labels