- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Re: Learning Sentinel inc
Learning Sentinel inc
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 07 2022 03:25 AM
Hello
I am looking for advise, not sure what I am doing wrong :) I am learning how to create incidents in Sentinel.
so I created detection rule looking for Suspicious Encoded Powershell, then I back to my to VM and run encoded PowerShell command and i cant see any incident in sentinel... I also check defender i have a few indecent regarding this activity. Why i cant see any incident in sentinel?
I used this rule:
github.com/Bert-JanP/Hunting-Queries-Detection-Rules/blob/main/Threat%20Hunting%20Cases/Suspicious%20Encoded%20Powershell.md
Ps: is possible to add screenshots here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 07 2022 03:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 07 2022 04:50 AM
1. You can paste in a screenshot or attach a file here. When you create a message or REPLY - there is an "Open Full Text Editor" link to press
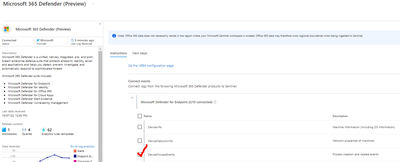
2. Do you have the DeviceProcessEvents Table connected from the "Microsoft 365 Defender (preview)" connector? Note, Raw events like this are billable (the Alerts are free), so keep that in mind if you start to ingest these.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 07 2022 06:13 AM
thanks for your answers. I have this connector enabled. I would like to add screenshots but I have this message : You do not have permission to upload images.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 09 2022 07:00 AM - edited Oct 09 2022 07:02 AM
@pingmetiwce
Did you configure the "Connect incidents & alerts", within the Microsoft 365 Defender data connector?
You mentioned that incidents appear in Microsoft 365 defender and not in Sentinel, so it sounds like the detection rule was created in Microsoft 365 defender (Custom detection rule) and not in Sentinel (Analytics rule).