- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Support Tip: Using AppLocker to create custom Intune policies for Windows 10 apps
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi everyone, today we have another article from Intune Support Engineer Mohammed Abudayyeh where he shows us how we can leverage AppLocker to create custom Intune Device Configuration policies to control Windows 10 modern apps. His example demonstrates just how easy it is to create a quick Intune policy that can be used in lots of different ways to control Windows apps in your environment.
=====
Windows AppLocker is a technology first introduced in Windows 7 that allow you to restrict which programs users can execute based on the program's attributes. In enterprise environments it is typically configured via Group Policy, however we can leverage the XML it creates to easily build our own custom policies that perform many of the same tasks with Microsoft Intune.
The process flow goes like this: We first model the policy we want to implement using AppLocker in Group Policy Editor. We then export the XML for that policy and use it to create a new, custom Windows 10 Device Configuration policy in Intune. Once the custom policy is deployed, the same policy behavior we modeled with AppLocker in Group Policy Editor is then applied to our targeted Windows 10 devices.
You can find all of our documentation on Windows AppLocker here, and in this post I’ll walk you through an example using this process to block the built-in Mail app on Windows 10 computers.
Generating the XML
The first step is to generate the XML we need for Intune by modelling the policy on a Windows 10 computer.
1. On a computer running Windows 10 Enterprise, start Group Policy Editor (GPEdit).
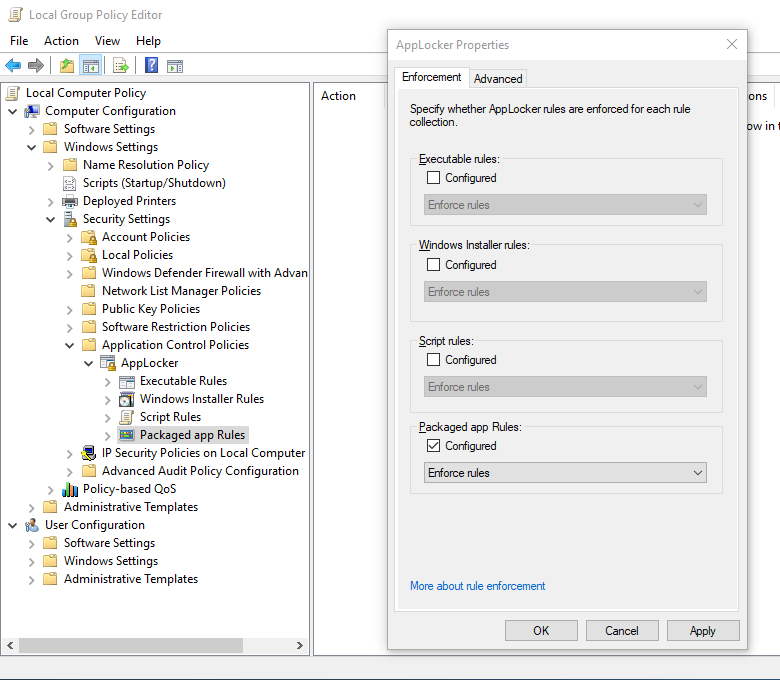
2. Under Computer Configuration\Windows Settings\Security Settings\Application Control Policies\AppLocker, right-click and select Properties, then enable Packaged app Rules and select Enforce rules. This turns on our AppLocker rules. Once done, click OK.
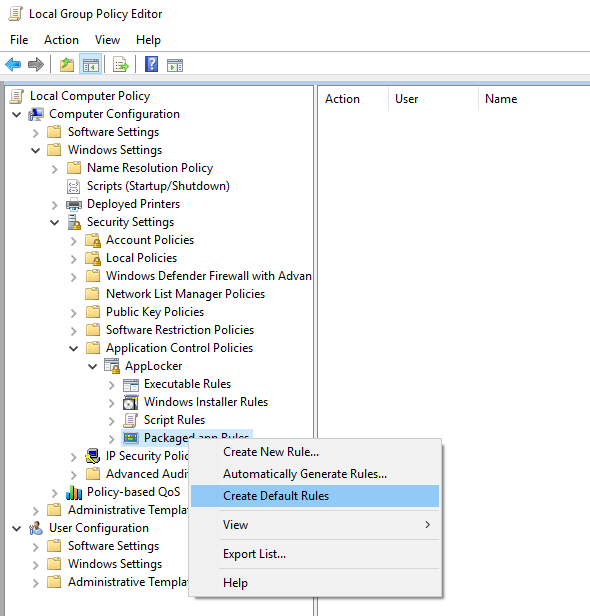
3. Next we need to create two Packaged app Rules: one default rule to allow all apps to run, and another rule to block our particular app. First, right-click Packaged app Rules and select Create default Rules. This will create a rule that allows all signed apps to be executed. Note that this setting only applies to Modern Apps and not Win32 applications.
4. Now create another new Package app Rule by right-clicking Packaged app Rules and selecting Create New Rule. This will start the Create Packaged app Rules wizard. Click Next to continue.
5. In this example we want to deny everyone access to the Mail app, so on the next screen select Deny and specify Everyone, then click Next.
6. Select Use an installed packaged app as a reference and click Select.
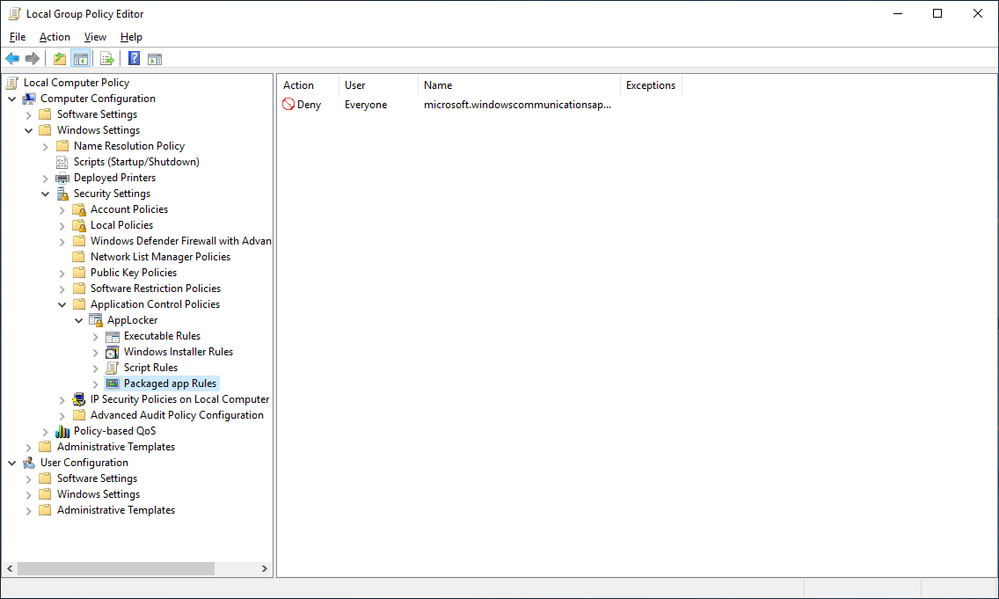
7. Here is where we select the app we want to block. In our example we’ll choose the one with Package Name = microsoft.windowscommunicationsapp which is the Windows Mail app. Once selected, click OK and Create.
8. Now we have a local policy created that blocks the built-in mail app. This will be our template.
9. Next we need to export that policy so we can use it in Intune. Right-click AppLocker and select Export policy. Save the file on a share so you can access it from the computer you will be using to create the policy in Intune.
10. When exporting the policy, an XML file will be generated that looks something like this:
<AppLockerPolicy Version="1">
<RuleCollection Type="Exe" EnforcementMode="Enabled">
<FilePathRule Id="921cc481-6e17-4653-8f75-050b80acca20" Name="(Default Rule) All files located in the Program Files folder" Description="Allows members of the Everyone group to run applications that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="a61c8b2c-a319-4cd0-9690-d2177cad7b51" Name="(Default Rule) All files located in the Windows folder" Description="Allows members of the Everyone group to run applications that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="fd686d83-a829-4351-8ff4-27c7de5755d2" Name="(Default Rule) All files" Description="Allows members of the local Administrators group to run all applications." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
</RuleCollection>
<RuleCollection Type="Msi" EnforcementMode="NotConfigured" />
<RuleCollection Type="Script" EnforcementMode="NotConfigured" />
<RuleCollection Type="Dll" EnforcementMode="NotConfigured" />
<RuleCollection Type="Appx" EnforcementMode="NotConfigured">
<FilePublisherRule Id="65bd6e53-0bf6-43dc-a85d-9668f66bf9dd" Name="microsoft.windowscommunicationsapps, version 16005.11029.0.0 and above, from Microsoft Corporation" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="CN=Microsoft Corporation, O=Microsoft Corporation, L=Redmond, S=Washington, C=US" ProductName="microsoft.windowscommunicationsapps" BinaryName="*">
<BinaryVersionRange LowSection="16005.11029.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
</AppLockerPolicy>
It’s important to note that if we use all of the XML in our Intune policy then the policy will fail because it includes other NotConfigured rules for things like MSI, Script, DLL and APPX. What we need to do is take only the configured RuleCollection element of our XML for use in our policy, like this:
<RuleCollection Type="Exe" EnforcementMode="Enabled">
<FilePathRule Id="921cc481-6e17-4653-8f75-050b80acca20" Name="(Default Rule) All files located in the Program Files folder" Description="Allows members of the Everyone group to run applications that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="a61c8b2c-a319-4cd0-9690-d2177cad7b51" Name="(Default Rule) All files located in the Windows folder" Description="Allows members of the Everyone group to run applications that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="fd686d83-a829-4351-8ff4-27c7de5755d2" Name="(Default Rule) All files" Description="Allows members of the local Administrators group to run all applications." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
</RuleCollection>
Creating the Policy
Once we have our XML, the next step is to create our policy in Intune and deploy it to users.
1. In the Intune admin portal, select Device configuration-> Profiles-> Create profile.
2. Enter the following settings:
- Name: Enter a name for the profile, such as Block Mail App.
- Description: Enter a description for the profile.
- Platform: Choose Windows 10 and Later.
- Profile type: Choose Custom.
3. On the Custom OMA-URI Settings screen, select Add then enter the following settings:
- Name: Give it a unique name so you can easily identify it.
- Description: Enter a brief description that describes the setting.
- OMA-URI: Enter the OMA-URI you want to use as a setting. In this case it is ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Native/StoreApps/Policy. This comes from the AppLocker CSP and you an find our documentation on that here.
- Data type: Choose String
- Value: Enter the XML from your exported policy. In our example this is the green text above.
4. Select OK to save your changes, then OK and Create to create the policy. Your profile will be shown in the Device configuration - Profiles list:
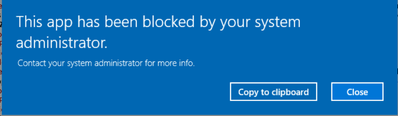
5. Lastly, assign your new profile to the groups of your choice. Once applied, when a targeted user attempts to launch the Mail app they will receive the following message:
IMPORTANT On the Windows 10 PCs that will be assigned the Intune policy, the Application Identity service must be running. This is the default, however if you’ve disabled this service for any reason, or if you have an issue where the policy is not being applied as expected, check the service and make sure it’s configured correctly. To do this, run services.msc and find the Application Identity service, then make sure Startup Type is set to Automatic and the Status is Running.
Summary
In this post I showed how you can easily leverage the XML generated by AppLocker to create custom Windows 10 Device Configuration policies in Intune. While the example I used demonstrated how to block the native Mail app on Windows 10, this same process can be used to control application execution for a variety of apps in many different ways. Be sure to check our complete documentation on AppLocker to learn more about the types of rules you can create for Windows 10 devices in your environment.
Mohammed Abudayyeh
Intune Support Engineer
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.