Microsoft has released security updates (SUs) that resolve vulnerabilities found in:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
IMPORTANT: When manually installing SUs, you must install the .msp file from an elevated command prompt (see the Known Issues area in the KB).
These SUs are available for the following specific builds of Exchange Server:
The March 2022 SUs for Exchange Server address vulnerabilities responsibly reported by security partners and found through Microsoft’s internal processes. Although we are not aware of any active exploits in the wild, our recommendation is to install these updates immediately.
These vulnerabilities affect on-premises Exchange Server, including servers used by customers in Exchange Hybrid mode. Exchange Online customers are protected from the vulnerabilities addressed in these SUs and do not need to take any action other than updating any on-premises Exchange servers.
More details about specific CVEs can be found in Security Update Guide (filter on Exchange Server under Product Family).
Update installation
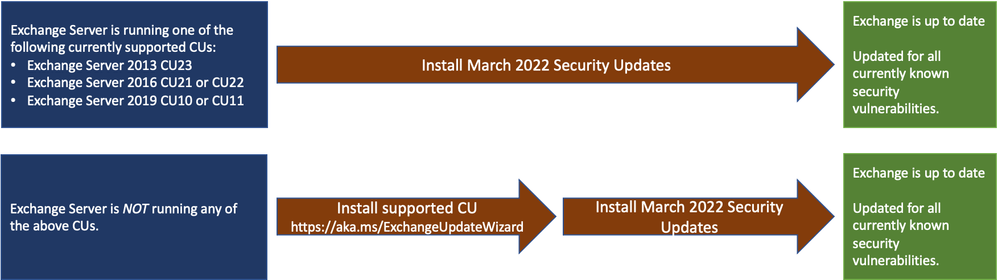
Two update paths are available:
Inventory your Exchange Servers / determine which updates are needed
Use the latest version of the Exchange Server Health Checker script to inventory your servers. Running this script will tell you if any of your Exchange Servers need CUs or SUs.
Update to the latest Cumulative Update
Go to https://aka.ms/ExchangeUpdateWizard and choose your currently running CU and your target CU to get update instructions.
If you encounter errors during or after installation of Exchange Server updates
If you encounter errors during installation, use the SetupAssist script. If something does not work properly after updating, see Repair failed installations of Exchange Cumulative and Security updates.
Known issues with this release
- Modifying DAG network settings failing with error 0xe0434352 after January SUs are installed - fixed in the March SU but Set-DatabaseAvailabilityGroupNetwork continues failing
- Customizing voicemail greetings might fail with error 0xe0434352 after January SUs are installed - not fixed in the March SU
- MSExchangeServiceHost service may crash repeatedly with Event ID 4999 logged in Windows Application event log. Please see Exchange Service Host service fails after installing March 2022 security update (KB5013118).
- Get-MailboxDatabaseCopyStatus command from Exchange 2013 server fails for databases hosted on Exchange 2016/2019 servers with following error:
A server-side administrative operation has failed. Operation failed with message: Error 0xe0434352 (Unknown error (0xe0434352)) from RpccGetCopyStatusEx4
Workaround: For Get-MailboxDatabaseCopyStatus error, run the Get-MailboxDatabaseCopyStatus command from Exchange 2016/2019 servers
- Checking Exchange 2016/2019 database status from Exchange Admin Center may fail with HTTP 500 error or with "Your request couldn't be completed. Please try again in a few minutes."
Workaround: Ensure the mailbox of admin is on Exchange 2016/2019 servers. If admin account has no mailbox, ensure all arbitration mailboxes, specially the “SystemMailbox{bb558c35-97f1-4cb9-8ff7-d53741dc928c}”, are on Exchange 2016/2019 servers.
FAQs
My organization is in Hybrid mode with Exchange Online. Do I need to do anything?
While Exchange Online customers are already protected, the March 2022 SUs do need to be applied to your on-premises Exchange Servers. You do not need to re-run the Hybrid Configuration Wizard (HCW) after applying updates.
Do I need to install the updates on ‘Exchange Management Tools only’ workstations?
Servers or workstations running only the Management Tools role (no Exchange services) do not need these updates.
NOTE: This post might receive future updates; they will be listed here (if available).
Updates to this blog post:
- 3/9: Added details about which previous issues are fixed.
- 3/10: Added details about the MSExchangeServiceHost service crash with this SU and the workarounds.
- 3/16: Added a reference to KB5013118
The Exchange Team