Ned here again. Today I’m going to talk about a new feature of Windows Server 2008 and Windows Vista called Special Groups auditing . While we’re in here, I’ll run through how we can use the new Group Policy Preferences (GPP) client-side extensions to make deploying this fast and easy. We’ll also see some of the new information available about auditing in general. Let’s get started.
What are Special Groups?
Special Groups (SG) are a way for administrators to know when certain security groups are added to a user’s token at logon. This way if you need to keep track of highly privileged accounts that are accessing resources, you have an easy event to correlate in your Security event logs. Why would we want to do this? Well, let’s say we have a file server dedicated to the Human Resources department. You also have a set of users that do server-related maintenance work, called “Datacenter Operators”. Your HR department wants to have an audit trail of any ‘super’ users that log on to their server. You have all your audit events being collected automagically to a central SQL server using something like Audit Collection Services in System Center Operations Manager 2007 . If we create a new registry value and populate it with the list of Security Identifiers (SID’s) that match our important groups, we now get a special kind of security audit event that’s very easy to track.
To make this work, we need two things in place:
- The Special Logon subcategory of the main audit category Logon/Logoff must be enabled.
- The registry must be populated with
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Audit
SpecialGroups =<REG_SZ semicolon-separated SID value list>
Step 1 is done for you out of the box – by default, Special Logon is enabled for success in Windows Server 2008 and Windows Vista. If you need to enable it for some reason, you can use AUDITPOL /SET or follow KB921469 to deploy it through group policy. Here’s what it looks like in AUDITPOL :
Step 2 is a bit trickier though. We will need to get the SID’s for groups that we want to track, then somehow apply them to computers; maybe thousands of computers. In the past we’d probably go the custom ADM route – but Group Policy Preferences make this soooo much easier – let’s segue for a moment.
Group Policy Preferences
Group Policy Preferences are a new piece in Windows Server 2008 to customize machine settings in ways not covered by the canned group policies. You can modify the registry, copy files, create mapped drives, add printers, change local user passwords, and much more. If you still need a logon script or a custom ADM after you start using GPP, you’re probably doing it wrong. :-)
Mike Stephens has already posted some useful info on GPP earlier. He also called out the GPP whitepaper that you will definitely want to read if you want to understand the power of this new product. What you may not already know is that you can now download the GPP client-side extensions for Windows XP, Windows Server 2003, and Windows Vista. You currently need a Windows Server 2008 computer in order to have the right Group Policy Management Console (GPMC) snap-in to create preferences, but never fear – we should be releasing the Remote Server Administration Tools pack for Vista SP1 by the end of March.
Doing the needful
So enough theory – let’s make some electrons move. Here is a step-by-step scenario where we configure Special Groups using Group Policy Preferences for the HR department servers:
1. We already know the groups we want to consider ‘special’. We can download the PSGETSID tool and use it to get the SID’s we will be setting, like so:
2. Now we have our four SID’s for these important high privilege groups:
S-1-5-32-544
S-1-5-21-1843020702-2878055099-494904912-519
S-1-5-21-1843020702-2878055099-494904912-512
S-1-5-21-1843020702-2878055099-494904912-1104
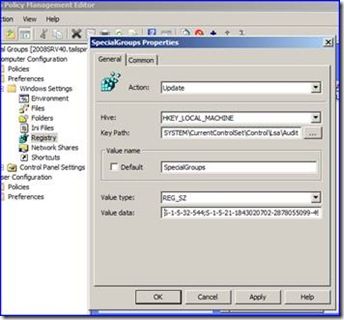
3. We open GPMC.MSC on our Windows Server 2008 machine, and create (or reuse) a new policy that we link at the Human Resources OU. We open the policy for edit, and navigate into ‘Computer Configuration’, then the new ‘Preferences’ section. We expand ‘Windows Settings’, then ‘Registry’. Now we can add our new registry values that we need. Right-click on ‘Registry’ like so and select ‘New’ and ‘Registry Item’.
4. We set our action to ‘Update’ so that it creates the value if not there or updates the value if it already exists. We select our exact key path and the value name. Then we take our list of SID’s that PSGETSID gave us and plug it in, using semicolons to separate them, like below:
5. We could stop here. Let’s get fancier. What if we keep all computers related to the HR department in that OU, including workstations? Nobody told us that they wanted this auditing in place on the client machines, and we want this setting to just apply to the right machines. Click the ‘Common’ tab and select ‘Targeting’.
6. Now we’re talking – check out all this filtering we can do!
7. In this case we’re going to select ‘Operating System’ must be Windows Server 2008 and we only want this to apply to the two HR file servers they asked us about (yes, technically I don't need the OS check if I assume that these two servers are 2008 - but I'm not an assumer). From looking at the above you can probably think of a zillion other things you might set as criteria. Don’t go crazy here, the more criteria you set, the more processing you add to the GPP calculations being done on the machine getting policy. Keep it simple.
8. Now we refresh group policy on one of our target HR servers. Our registry now has:
9. We logon to this server as a user that’s a member of at least one of these special groups and open our Security Event Log:
Heck yeah – worked like a champ. Anytime a user logs on to this server and is a member of one our special groups, we’ll have this easy and unique Event 4964 to follow. We don’t have to parse through the event logs looking at all the regular LOGON events that occurred, correlating them to individuals, and that makes life easier for everyone.
One last neat feature – let’s say you want to take this new registry setting and give it to a colleague that manages a different environment in your company. In the preference policy editor, Select your registry setting and drag it onto your desktop – an XML file will be created with those settings. Open it in Internet Explorer:
Slick. Lost your setting? Drag that XML back into the editor – your settings are back. Double slick.
Want to learn more about all the new security audit events? Read “Description of security events in Windows Vista and in Windows Server 2008 ”. Want even more? Head over to the “Windows Server 2008 Security Guide” and “Windows Server 2008 Security Resource Kit” (which contains a chapter by audit guru Eric Fitzgerald ).
- Ned Pyle