- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity
- New Blog Post | Behind the scenes of business email compromise
New Blog Post | Behind the scenes of business email compromise
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 14 2021 11:11 AM - edited Jun 14 2021 11:11 AM
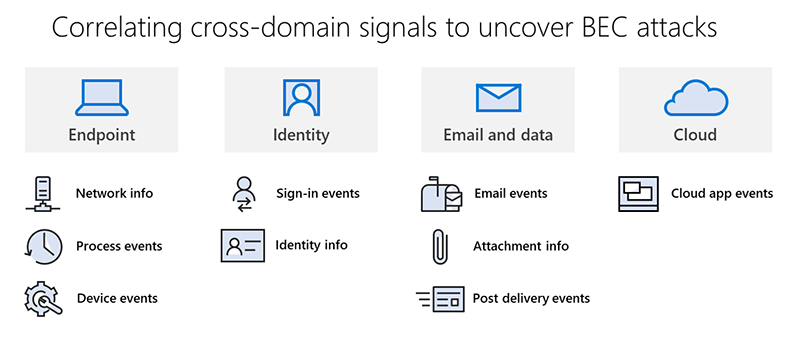
In this blog, we’ll share our technical analysis and journey of unraveling this BEC operation, from the phishing campaign and compromised mailboxes to the attacker infrastructure. This threat highlights the importance of building a comprehensive defense strategy, which should include strong pre-breach solutions that can prevent attackers from gaining access and creating persistence on systems in the first place, as well as advanced post-breach capabilities that detect malicious behavior, deliver rich threat data, and provide sophisticated hunting tools for investigating and resolving complex cyberattacks.
- Labels:
-
Azure
-
Cloud Security
-
Microsoft 365