First published on CloudBlogs on Jan 14, 2015
Overview
This post provides guidance on how to properly configure a Wi-Fi profile to connect mobile devices to a secure WPA2-Enteprise network using certificate-based or PEAP-based authentication. For iOS, this process requires that SCEP-based certificate deployment already be configured and that a certificate profile for a valid client authentication certificate for accessing the network be configured ahead of time. When the Wi-Fi profile is deployed to iOS devices, a certificate enrollment request will also be initiated on behalf of the mobile device. For each Wi-Fi profile deployed to a device, then, a new certificate will be issued to that device. The steps provided in this post are for an Microsoft Intune subscription integrated with System Center Configuration Manager 2012 R2 via the Intune Connector. For standalone deployments of Microsoft Intune, the steps are different. For more information about how to configure Wi-Fi profiles with Microsoft Intune in a standalone deployment, check out the TechNet documentation here: http://technet.microsoft.com/en-us/library/dn818903.aspx .Creating a Wi-Fi Profile for an iOS device
- Launch the Create Wi-Fi Profile Wizard from the Configuration Manager 2012 R2 console.
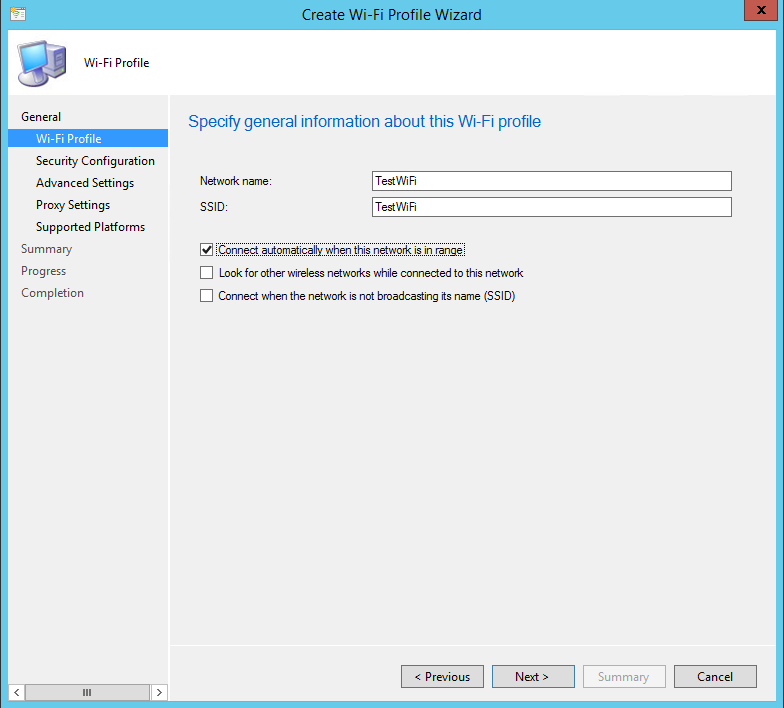
- On the Wi-Fi Profile screen, enter the Network Name (friendly name) and SSID of the Wi-Fi network. Select the option to connect automatically if desired and choose whether to connect when the network is not broadcasting if required. To ensure compatibility across platforms, the network name and SSID should match and be aware that they are both case-sensitive.

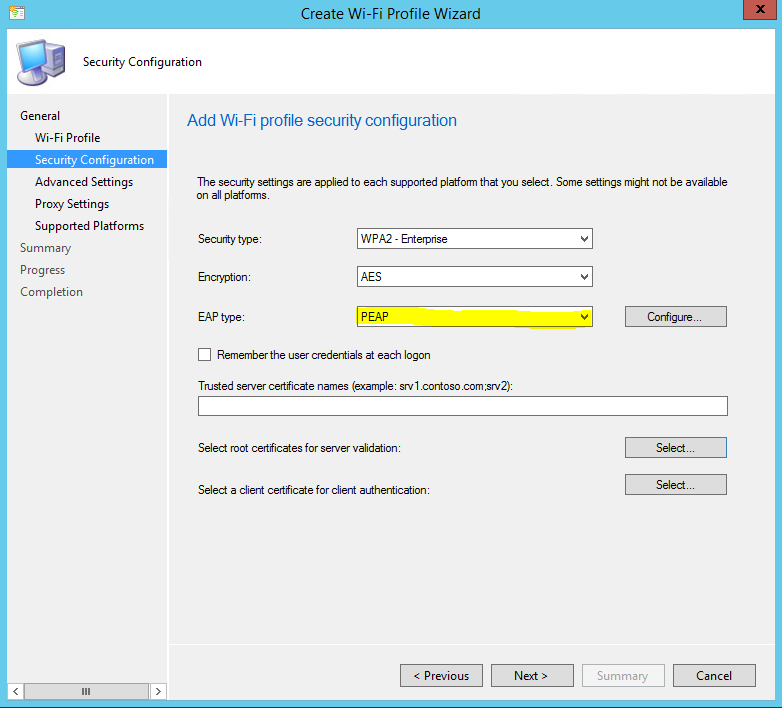
- Select the security type “WPA2-Enterprise” and the appropriate encryption. Some networks provide encryption for the initial authentication process using a trusted server name and a root certificate for server validation. If that is the case, enter those values on the Security Configuration screen. If a trust is not already configured the end user will be prompted to trust connection/server. Select “PEAP” or “Smart Card or other certificate” for EAP Type.
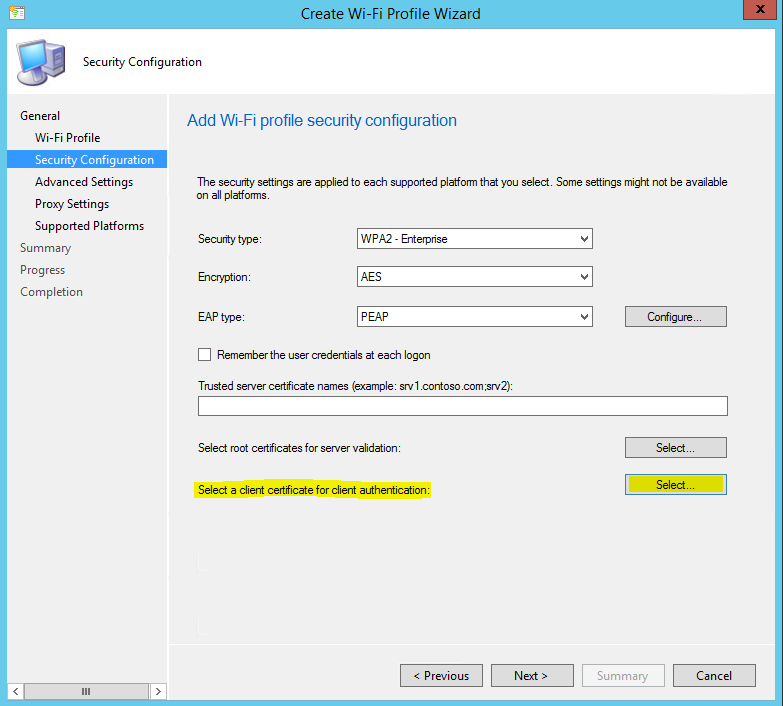
- Next, click “Select” to select a client certificate for client authentication to the network. From the list of configured SCEP profiles, select the appropriate client authentication certificate profile and click “OK”.
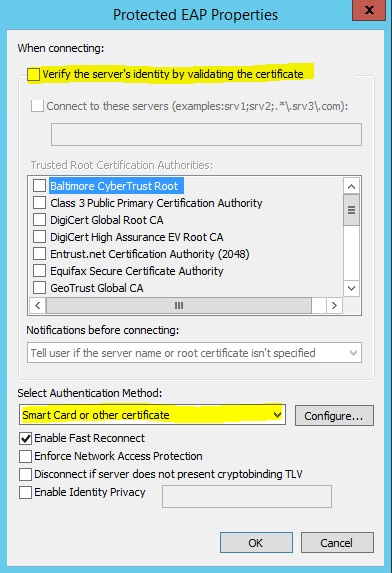
- ( For PEAP EAP Type Only ) PEAP and EAP-TTLS are special in that they allow “inner auth methods”. Click Configure to specify options for the selected authentication type. Uncheck the “Verify the server’s identity by validating the certificate” option. For password-based authentication, select “Secured password (EAP-MSCHAP v2)”. For certificate-based authentication, select “Smart Card or other certificate”.
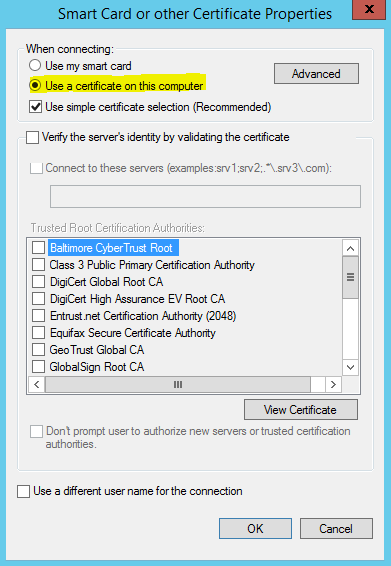
- ( For Cert-Based PEAP Authentication Method Only ) Click “Configure” to specify settings for certificate selection for authentication. Select the option to “Use a certificate on this computer”. Uncheck the “Verify the server’s identity by validating the certificate” option. Click “OK”. Click “OK” to close the Protected EAP Properties screen.
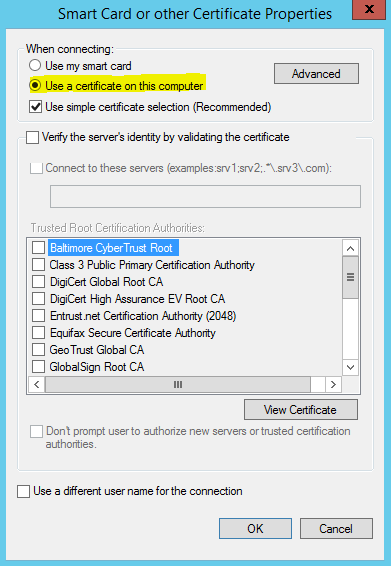
- ( For Smart Card or Certificate EAP Type Only ) Click “Configure” to specify settings for certificate selection for authentication. Select the option to “Use a certificate on this computer”. Uncheck the “Verify the server’s identity by validating the certificate” option. Click “OK”. Click “OK” to close the Smart Card or other Certificate Properties screen.
- Click “Next”.
- On the Advanced Settings screen, select “User authentication” as the authentication mode. Click “Next”.
- Configure connection-specific proxy settings if desired. Click “Next”.
- Select iPhone and/or iPad on the Supported Platforms screen. Click “Next”.
- Click "Next" on the Summary screen, then "Close" to close the Wi-Fi Profile Wizard.
Deploying a Wi-Fi Profile to User/Device Collections
- Right-click on the Wi-Fi profile in the Configuration Manager 2012 R2 console.
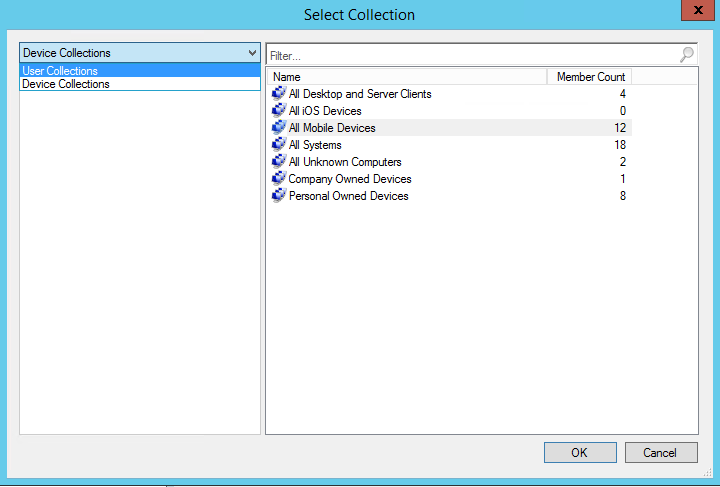
- Click “Browse” to select a user or device collection.
- Toggle the dropdown on the left to see the available user and device collections for deployment. Select the correct collection and click “OK”.
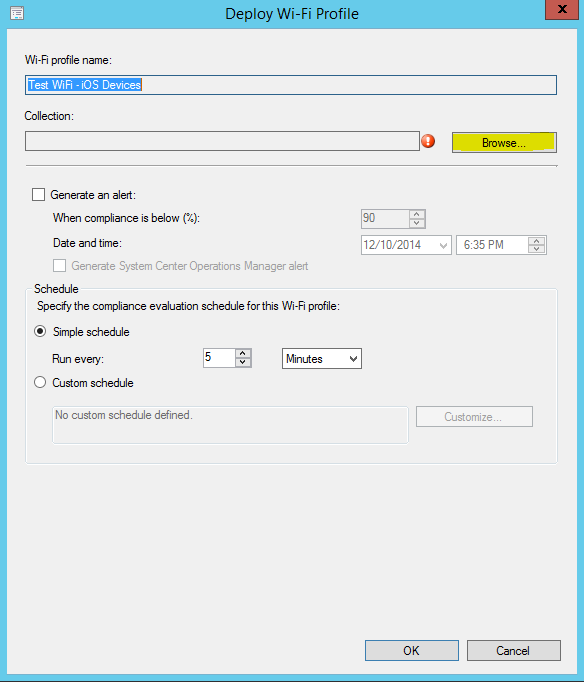
- Select “Generate an alert” to create console alerts based on deployment compliance and configure custom settings for updating compliance status for this profile if desired.
Troubleshooting
Try creating the same configuration profile on the device to check to see if the issue is reproduced. This can help narrow down the issue quickly and efficiently. Check the following configurations:- SSID must be the same as Network Name.
- Only User Authentication can be supported in the Authentication mode.
- Only User Cert is officially supported.
- FIPS is not supported on this release.
- If the certificate does not have a SAN then authentication will fail and it will not connect to the Wi-Fi network. The SAN on the certificate should be set to the UPN of the user.
- To setup TLS, you have to select smart card or certificates as a method of authentication for EAP type.
Additional Resources
For additional technical resources on Wi-Fi Profiles in Configuration Manager, visit TechNet here . I hope that you’ve found this blog post useful. Please bookmark this blog and check back frequently as we plan to post new content weekly! Also, if you’re not yet using Intune, sign up for a free 30-day trial today! - Bob Roudebush, Enterprise Mobility Technology SpecialistPublished Sep 08, 2018
Version 1.0Intune Team
Brass Contributor
Joined September 05, 2018
Microsoft Security Community Blog
Follow this blog board to get notified when there's new activity