- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Azure Information Protection: Ready, set, protect! – Part 2
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Part 2 - Adopt a data-centric protection strategy
This post is the second in a 4-part series focusing on how to implement information protection in your organization. In Part 1 of the series we showed you how to get going with classification and labeling, and FAST. In this next post in the series we are going to focus on how you can take the learnings and benefits from that and protect your information.What is data-centric protection?
Traditional information protection solutions focused a lot on control. Network security solutions such as firewalls and proxies made sure sensitive information never left corporate boundaries. Device security solutions ensured protection of sensitive data as long as the data was contained within the managed devices and apps. This works great if your data is being accessed by internal users on managed devices. But today data is travelling further and faster, and with rapidly increasing collaboration scenarios, these lines of defense fall short. Once your data is shared with external parties or stored in locations where you have absolutely no control or visibility, what then? This is where data-centric protection can help you.How does this help you?
If there is anything you should deeply internalize, it’s that data-centric protection is a journey not an event. Like any security approach, there is no magic wand to wave, you need to invest in the process and evolve along with threats, users work styles and technology advances. Doing nothing is not an option , so that leaves doing something! Right now, you may have nothing in place, getting started moves you from zero to something! For a broader data-centric security strategy, you should have a holistic approach and consider technologies such as data classification, watermarking, data loss prevention (DLP), conditional access and cloud access security broker (CASB). This will help you gain control over data in heterogeneous environments and also address most of your data loss challenges. Let’s see how we, as your enterprise security partner, can help you with this strategy by exploring a native, a DLP, and a CASB scenario.Scenario 1 – Identify sensitive data and apply protection automatically
You can create sensitivity labels and configure polices for actions to occur, whether that be after a user manually selects a label, or through content detection (conditions) that make recommendations or just apply automatically.- Choose default labels or customize per your needs. For guidance on labels, refer to Part 1 .
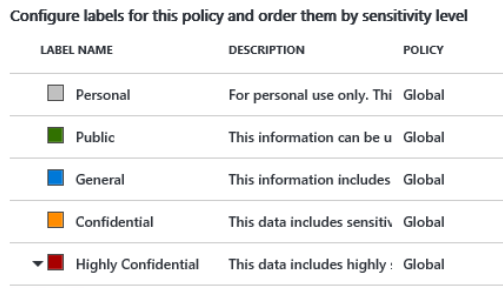
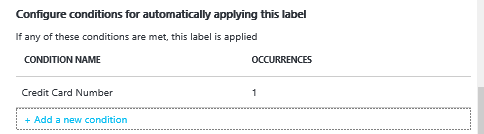
2. If you wish to do content detection, define conditions that look for patterns in data, such as words, phrases or expressions. You can select from preconfigured rules or customize to meet your requirements, as well as choose how many occurrences need to exist before the condition is met. In the example below, we want data to be automatically labeled as confidential if there is at least one occurrence of a credit card number.
3. Define the actions that will be executed when the label is applied. You can automatically apply protection (using Azure RMS or ADRMS with HYOK) as well as visual markings such as watermarks, headers and footers.
 You can follow our technical documentation on
configuring policies
which has the complete set of options, so you can test these options yourself.
You can follow our technical documentation on
configuring policies
which has the complete set of options, so you can test these options yourself.
Scenario 2 – Control information flows using a DLP engine
You can leverage your existing border gateway and information flow controls (such as mail gateways, content scanning and DLP engines) to create rules on how to manage information. As recommended in Part 1 if your data is classified and labeled appropriately, you can also set up your DLP engine to read the labels and take actions accordingly. In the example below, we have an Exchange Online rule that looks for email attachments that contain data labeled as Internal and blocks such emails when shared with external recipients.
Scenario 3 – Monitor the flow of sensitive data to cloud environments using CASB
As sensitive data travels to cloud environments, it becomes critical to monitor how the data is being used, shared or distributed. You can configure policies for a CASB solution to look for sensitive data in cloud environments and take actions or get alerted in case of abnormal behaviors. In the example below, we have configured an alert when a document with Confidential label is traveling to an external location.
 You can refer to
this blog
on how the integration of Azure Information Protection and Cloud App Security works along with
technical guidance
on how admins can gain visibility and control over sensitive data in cloud environments.
You can refer to
this blog
on how the integration of Azure Information Protection and Cloud App Security works along with
technical guidance
on how admins can gain visibility and control over sensitive data in cloud environments.
How to drive this change across your organization?
Information protection touches the day to day operations of the entire organization. How do you bring everybody along so they comply versus block? Here are some tips that can help you.- Start with our default labels! We put a lot of effort and research into these, and meet a large majority of customer needs.
- Start SMALL. Establish your first use case and scenario, pick something that allows you to learn and to gain confidence. Then your second, third … you get the idea
- Use protection templates to define permissions, and include groups for easy management.
- Work with your desktop and mobile management teams. They can help you package updates, clients and apps so that they are in place on devices prior to users needing them. This smooths the user experience.
- Download the new unified client from our Download Center
- Start a trial and kick the tires
- Learn more about Information Protection
- Get deep technical and scenario documentation
- Keep up to date by following our blogs
- Engage with us on Yammer , Twitter or send us an e-mail
- Watch the overview video
- Watch the recordings of our Ignite sessions ( BRK2127 , BRK2128 , and BRK3095 )
- Learn more about the Enterprise Mobility + Security offerings
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.