- Home
- Microsoft Teams
- Microsoft Teams
- Teams Updater Vulnerability
Teams Updater Vulnerability
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 27 2019 01:07 AM
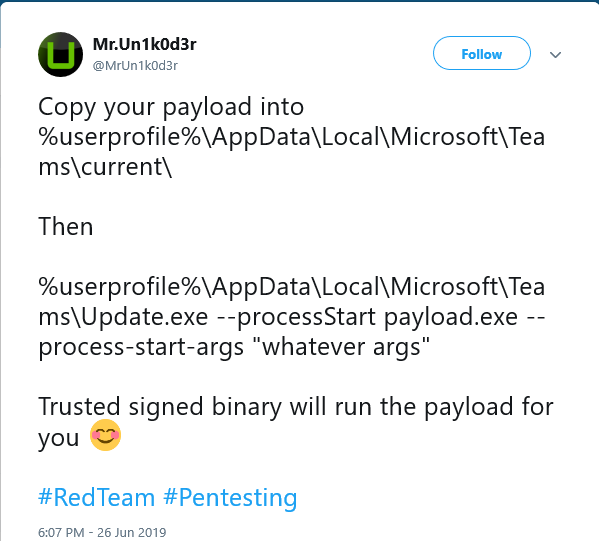
There are reports circulating that the Teams auto-update process suffers from the same unsigned code execution as other application built with Electron.
Running the Update.exe processStart with any unsigned application binary will run the unsigned application as signed code through a process chain. The Teams Update.exe is signed by Microsoft so the usual AppLocker and Application Guard defences will not block this exploit.
Has anyone got any advice on a work around or information on whether Microsoft are going to plug this exploit?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 27 2019 09:47 AM
The Microsoft folks are aware of this already, and with them "owning" Electron now it shouldn't take a lot of time to patch. The more interesting question here is why was this allowed to happen in the first place, considering security is on top of their SDL list. Guess we can always blame it on the open-source model, but whoever decided to use Electron should have put it through the SDL list to begin with...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 27 2019 12:20 PM
I have met some of the Teams Dev team at conference. They seem very well meaning and want to build a great product but I get the sense that there is a lack of appreciation for enterprise and security. That shows in the product.
Unfortunately the Electron / Squirrel updater issues are not confined to Teams. Slack and a few other widely used products have the same issues.
Also interesting to note that Electron have deprecated the use of Squirrel on Windows.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 01 2019 05:12 AM
Yep, the problem is with squirrel and affects a long list of apps.
but, you can hunt for them with defender ATP
this query only focuses on the update part but you can easily change this to include the procstart param
http://blog.sec-labs.com/2019/07/hunt-for-nuget-squirrel-update/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 01 2019 08:02 AM
@Mattias Borg Awesome. Great tip. I dig go looking for a Defender ATP hunt command but obviously did not look hard enough.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 01 2019 10:31 PM - edited Jul 01 2019 10:48 PM
@Andrew Matthews I've updated the query to catch all parameters used by squirrel and 2 URLs I know are legit. Other apps using squirrel which are also affected by this
Happy Hunting!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 02 2019 08:43 AM
I can confirm that MS has a fix for this already, should be rolling out shortly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 02 2019 08:49 AM
This is precisely why enterprise administrators want a standard MSI installer for Teams that puts things into a properly secured location like C:\Program Files location instead of the user's folder. Oh, sure, the vulnerability would still be there but a standard user wouldn't be able to readily leverage it without some other exploit or flaw.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 22 2019 05:22 PM
Any update now? Or is Teams still wide open to this vulnerability?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 04 2019 06:47 AM
Hi all,
Please, anyone knows if the vulnerabilty is still present in Teams v1.2.00.27559 (October 24, 2019)?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 04 2019 11:03 AM
Recommendation hardening your deployment of Windows 10: https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-security-configuration-f...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 12 2019 12:45 AM
CVE-2019-5922 is not related to this.
New update was pushed for this vulnerability on 1st week of Nov and fixed now, No CVE for this.
- Reegun J
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 14 2019 06:20 AM
SolutionThis particular squirrel vulnerability was fixed in Teams version 1.2.00.21068.
Thanks!
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 20 2020 01:18 PM
@John Rea Is there any official resource I can confirm this? My management is asking. Thank you!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 14 2019 06:20 AM
SolutionThis particular squirrel vulnerability was fixed in Teams version 1.2.00.21068.
Thanks!
John