- Home
- Security, Compliance, and Identity
- Microsoft Entra
- Device filter in the conditional access policies
Device filter in the conditional access policies
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 29 2023 10:09 PM
Dear Microsoft Entra Friends,
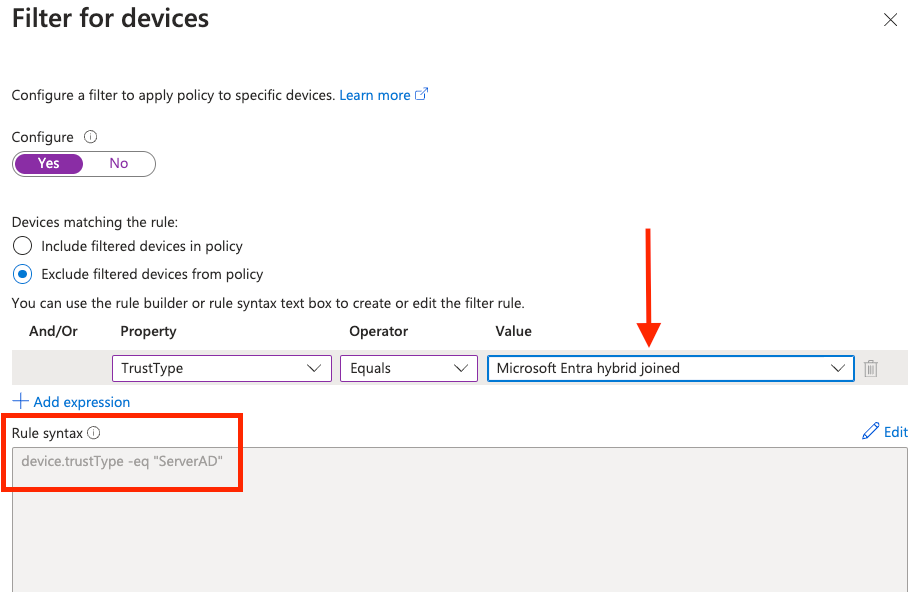
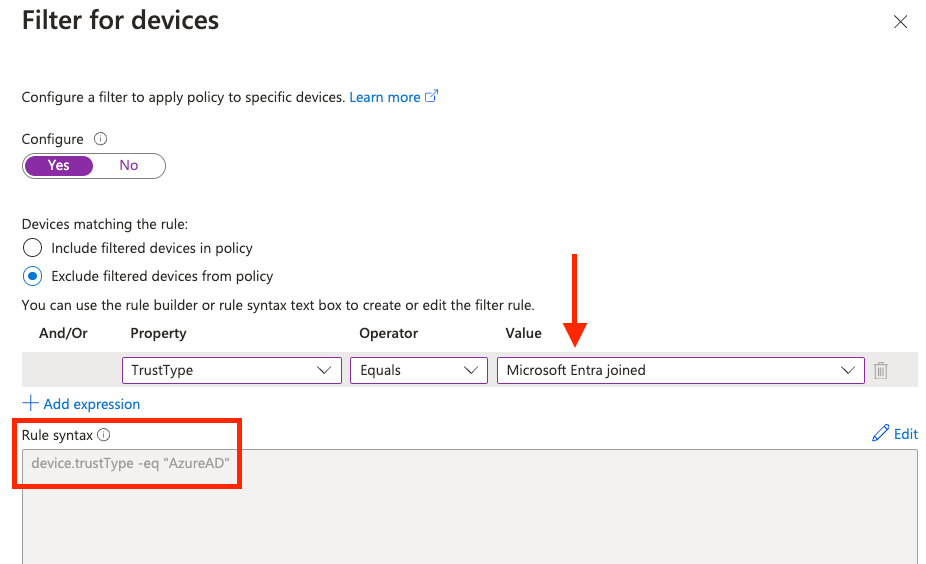
What is your experience with the device filter in the conditional access policies (Microsoft Entra ID)? The values of the attributes are not correct and therefore the policy is not processed correctly. This is confirmed in a "What If" test.
Kind Regards,
Tom Wechsler
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 01 2023 01:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 01 2023 04:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 16 2024 08:29 AM
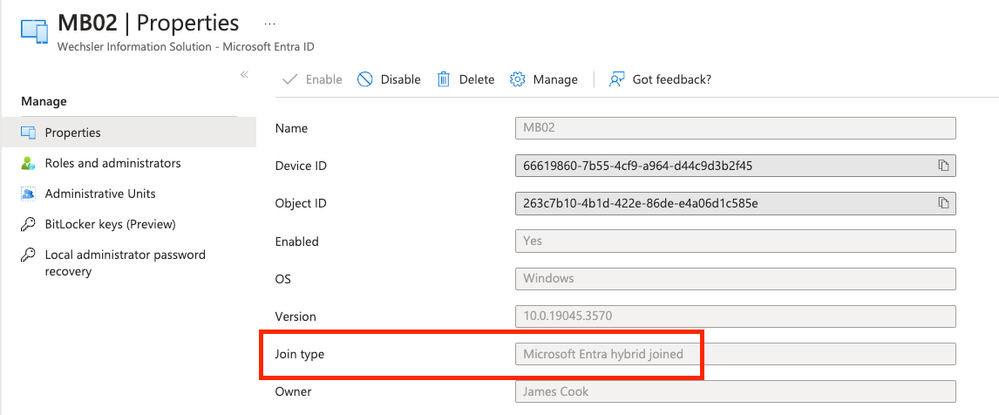
@TomWechsler the actual
value stored in the directory for the trustType property on Entra ID deviceID is SetverAD for Microsoft Entra hybrid joined and AzureAD for Microsoft Entra join. So whereever we show these values in the UI we show user friendly names except in the actual deviceFilter rule where we have to translate to the what’s stored in the directory. You can also see this when creating dynamic device groups using deviceTrrustType property. As this doc https://learn.microsoft.com/en-us/entra/identity/users/groups-dynamic-membership#rules-for-devices suggests the three values we support are ServerAD, AzureAD and Workplace. This should not cause any issues with how the policy is bending applied. I am curious on your statement that the policy is not processed due to this discrepancy. Can you elaborate more.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 16 2024 09:47 PM