- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- New Device Health Reporting for Microsoft Defender for Endpoint is now generally available
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Your security team now has a comprehensive view of the health and security of your endpoints. We are excited to announce new additions and improvements to the Device health dashboard (previously named Device health and compliance). We’ve redesigned the dashboard so that you can view sensor health and antivirus protection status across platforms and easily access detailed Microsoft Defender for Endpoint information.
Here’s what to expect:
- A new, tabbed reporting page with cards that display high-level information and security snapshots
- Detailed information about Microsoft Defender Antivirus, including engine version, security intelligence version, platform version, antivirus mode, and recent scan results
- Easier access to the actionable information and insights you need, with drill downs to Threat and vulnerability management recommendations, device pages and the all-new Microsoft Defender Antivirus details flyout that is a rich source of device security details
The following sections describe the new additions and improvements to the Device health dashboard and how to get to it.
New tabbed reporting page with cards
Previously, the Device health and compliance reporting dashboard displayed views in two columns: Device trends and Device summary. We have redesigned the experience! In the new and improved dashboard, you’ll see two tabs:
- Sensor health & OS
- Microsoft Defender Antivirus health
Let’s take a deeper look at these tabs.
Sensor health & OS
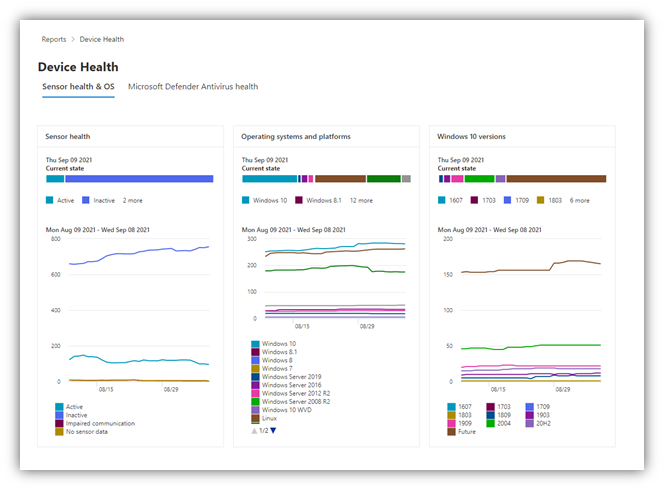
The Sensor health & OS tab contains cards that show details about sensor health across devices and operating systems in use at your organization, as shown in the following image:
Three, easy-to-use cards replace several of the views you previously saw in the former Device trends and Device summary columns. At a glance, you can see whether sensors are working correctly, what operating systems are in use at your organization, and which versions of Windows people are using.
Microsoft Defender Antivirus health
The Microsoft Defender Antivirus health tab contains detailed information about antivirus protection in your organization, as shown in the following image:
This tab features eight new cards (please note the version reports show the most recent 3 versions and collects the rest under ‘Other’; the ‘View full report’ flyout shows the most recent 9 versions and collects the rest under ‘Other’):
- Antivirus mode, which tells you at a glance how many devices are running Microsoft Defender Antivirus in active mode, in passive mode, with EDR in block mode turned on, and more
- Antivirus engine version with a full report flyout available
- Antivirus security intelligence version with a full report flyout available
- Antivirus platform version with a full report flyout available
- Recent antivirus scan results with a link to learn more about error codes (if you’re seeing any)
- Antivirus engine updates with a link to engine/platform updates documentation
- Antivirus security intelligence updates with a link to security intelligence updates documentation
- Antivirus platform updates with a link to engine/platform updates documentation
More detailed information about Microsoft Defender Antivirus
The tabs and cards provide at-a-glance information about Microsoft Defender Antivirus. In the new experience, full report flyouts provide more detailed information, as shown in the following examples.
Example #1: Antivirus engine version flyout
The following image shows the flyout that is opened when the user selects the View full report button on the Antivirus engine version card.
Example #2: Microsoft Defender Antivirus details
The following image shows the flyout presenting detailed information about Microsoft Defender Antivirus. On the flyout, you can navigate to your security recommendations to view any actions you should take, such as initiating a scan on an endpoint, or getting required updates installed.
Easier access to information
With these updates and improvements to the Device health reporting dashboard, you have easier access to information. You start with summary information in cards, and then move to more detailed views as needed. You also get a more interactive experience.
- Select a tab to view summary information displayed in cards.
- On each card, select a bar to view more details about that category. Or select a button or link to view more information, such as a full report.
- In a report view, use filters and choose columns to view the information you are most interested in.
How do I get to the Device health reporting dashboard?
The new and improved Device health reporting dashboard is currently in preview and will soon replace your existing dashboard automatically. Follow these steps to access your dashboard:
- Go to https://security.microsoft.com, and sign in.
- Choose Reports > Device health
Learn more
Want to learn more about the new device health reports? See Device health and compliance report in Microsoft Defender for Endpoint | Microsoft Docs for more details.
Let us know what you think!
We are excited to bring these reporting improvements to you and your security teams. Try out the new device health reports today and let us know what you think in the comments below! We take all feedback into account as we work to continue to improve your security experiences in Microsoft Defender for Endpoint.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.