- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Multiple Instances of the same app in Conditional Access App Control?
Multiple Instances of the same app in Conditional Access App Control?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 29 2022 12:07 PM
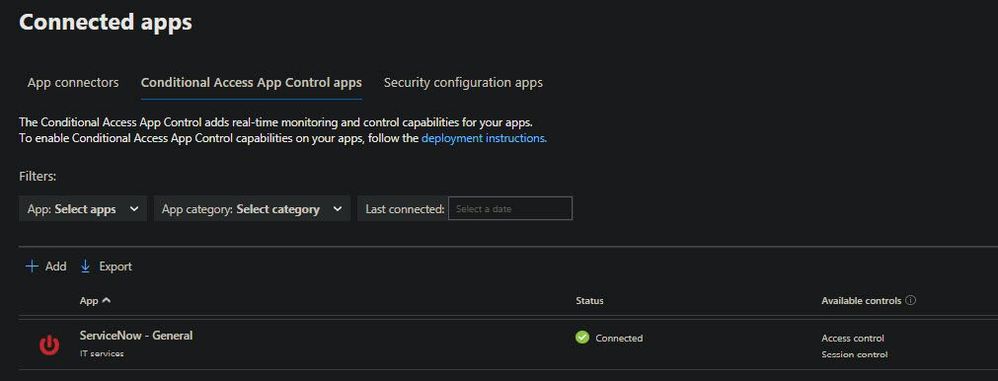
We have 4 ServiceNow instances (dev,test,stage,prod). We have all 4 instances added to App connectors. However, after adding one of the instances in Conditional Access App Control I've found I can't add the other 3. When I go to Add and search for ServiceNow, it is there but I can't click on it. Is there no way to add multiple instances of the same app to CAAC or am I missing something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 30 2022 09:28 AM
Hi @JoeDLP,
As a first step you'll need to complete a login to the app for it to appear. There can be some limitations though with apps where there are overlapping domains. If all 4 instances share namespaces, you should be able to configure your CA policy to send the session to Defender for Cloud Apps proxy which should allow you to control the session. The caveat is that all the data would be attributed to the same app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 30 2022 10:05 AM
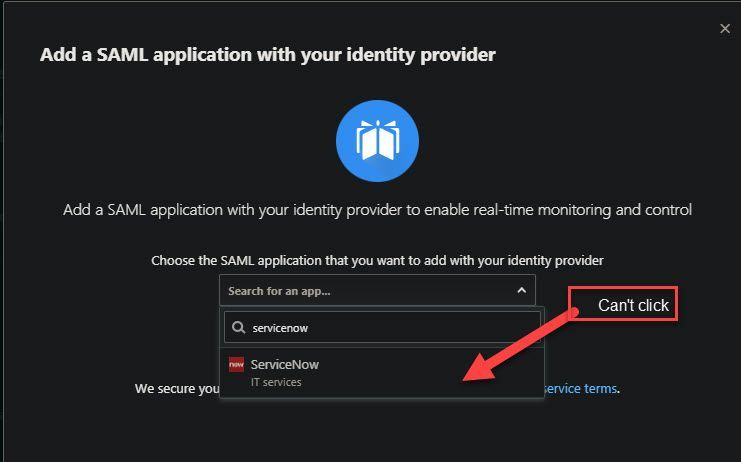
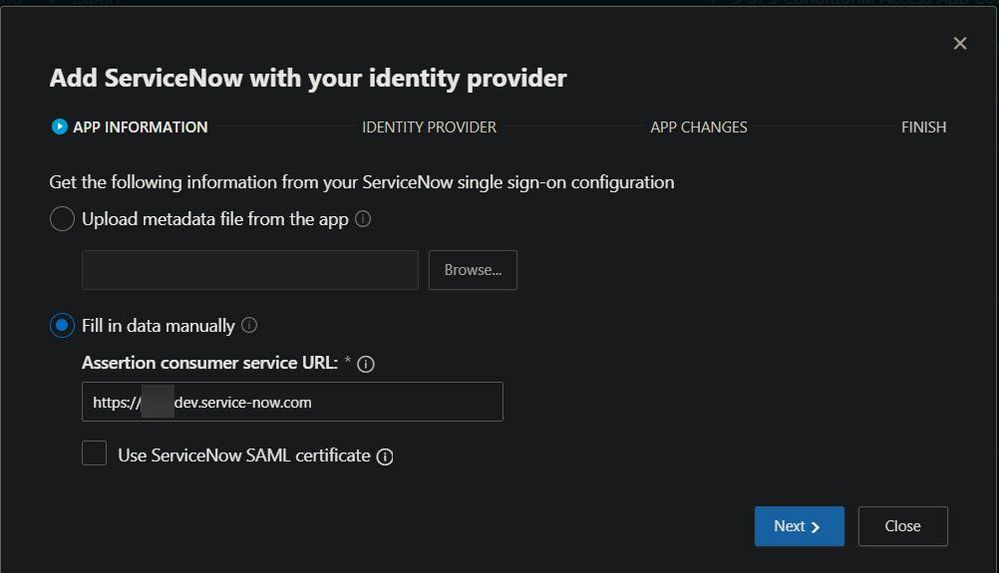
Hello. Yes we have the one instance of Servicenow configured and are able to apply Access and Session controls. Each of the 4 instances (acme-prod.service-now.com, acme-test.service-now.com, etc) each have their own SAML signin page and configuration. So now I'm trying to figure out how to add the the other 3 instances. You can see below if I try to add ServiceNow again it is greyed out and wont let me. Also, the configuration for the instance I've already configured (see below) requires the ACS url of the instance, but each of our 4 instances has a different ACS URL. And I don't see any way to add the other 3 ACS URLs of the other instances here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 03 2022 01:27 PM
Solution@JoeDLP can you try manually adding the app from the cloud app catalog? This should allow you to select it so you can enter a different ACS address. It's possible this might work but I don't believe it's actually been tested.
With 3rd party IDP (Ping, Okta, etc..) this can be a bit more challenging because the ACS endpoint is required but it's not for AAD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 05 2022 06:50 AM
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 03 2022 01:27 PM
Solution@JoeDLP can you try manually adding the app from the cloud app catalog? This should allow you to select it so you can enter a different ACS address. It's possible this might work but I don't believe it's actually been tested.
With 3rd party IDP (Ping, Okta, etc..) this can be a bit more challenging because the ACS endpoint is required but it's not for AAD.