- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 09 2018 01:02 PM
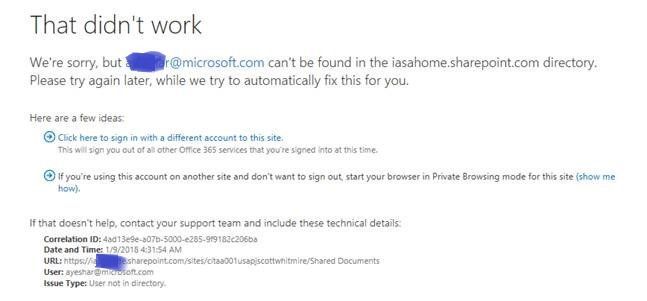
I get complaints all the time when users get this message - is there is fool proof way I can tell them to get this fixed? They follow the instructions but they tell me it doesn't help. And yes, my external guests are all @Pernille-Eskebo.com people!!
- Labels:
-
groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 09 2018 10:16 PM
The only way i could think of use Azure B2B and add there domain so there account works.
but if they have another account on your tenant then they will need to have a private window or signout first. or use Profiles in google chrome..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 09 2018 10:26 PM
Jan 10 2018 05:43 PM - edited Jan 10 2018 06:51 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 10 2018 05:43 PM - edited Jan 10 2018 06:51 PM
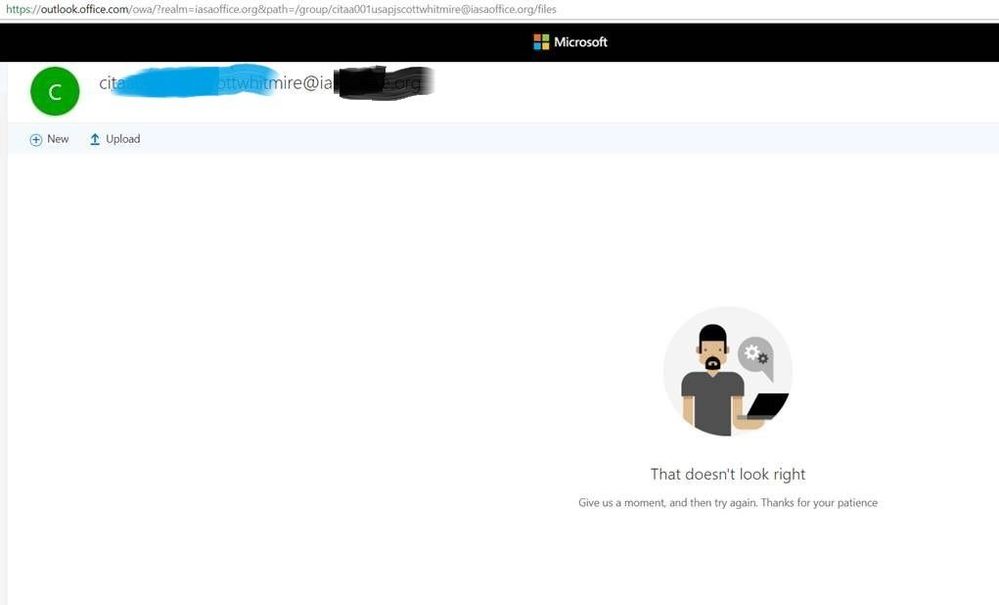
I am only sharing files that are simply part of the Group files. These are the URLs from the browser https://outlook.office.com/owa/?realm=XXXX.org&path=/group/citaa001usapjscottwhitmire@XXXX.org/files https://XXXX.sharepoint.com/sites/citaa001usapjscottwhitmire/Shared%20Documents/Forms/AllItems.aspx David
Here is the equivalent error … cute but just as useless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 10 2018 10:34 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 11 2018 02:10 PM
Yes with
Set-SPOSite -Identity https://iasahome.sharepoint.com/sites/citaa001usapjscottwhitmire -SharingCapability ExternalUserAndGuestSharing
I wonder if it has anything to do with the fact that the tenant and SharePoint have different names? SharePoint is
https://iasahome.sharepoint.com
while Outlook is
iasaoffice.org
PS: I know this is identifiable information but I am including the full names for clarity here.
Jan 11 2018 02:32 PM - edited Jan 12 2018 06:22 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 11 2018 02:32 PM - edited Jan 12 2018 06:22 PM
UPDATE 2: Reconfirming the AzureAD first approach has worked in every case. Manually checking in Azure AD that the SOURCE is External Azure Active Directory status (vs Invited User) is required.
The invitation can be resent from Azure AD but it is all a bit manual. Can we find out why the GroupSubscription.ashx script is not working reliably?
UPDATE: followed your suggestion and using AzureAD to add a GUEST does in fact add the runes needed. The issue however, is that when signing in to accept the account invitation from Azure AD, I have to sign in with a "Microsoft Account". Apart from the obvious confusion that every MS person understands (their @Pernille-Eskebo.com email is not a "Microsoft Account") that would seem to be a blocker unless they associate their Microsoft work email as a "Microsoft Account".
I can't remember if I ever resolved that issue. Any MS people reading care to give it a try?
Previously:
You suggested "add the users first as guests in Azure AD". Would I have to follow the EXTERNAL naming convention for the USERNAME?
satya_microsoft.com#EXT#@iasahome.onmicrosoft.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 13 2018 07:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 13 2018 04:52 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 14 2018 12:20 AM
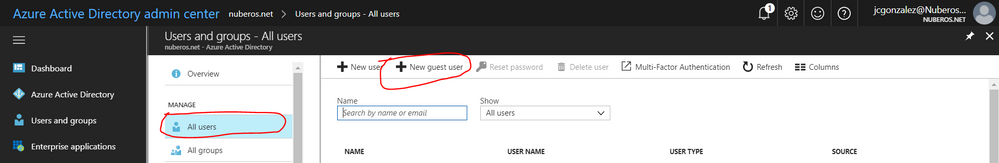
Mmmm...you don't see an ADD GUEST USER button? Strange...the experience should be like this:
1) Browse the Office 365 Admin Portal
2) Under Admin Center, clic on Azure AD so you will be redirected to https://aad.portal.azure.com/
3) Clic on Acture Active Directory and then on Users and groups
4) Clic on All users and you will see and Add guest user option there
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 14 2018 02:42 PM