- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 20 2022 06:06 AM - edited Apr 27 2022 08:15 AM
Hello Community,
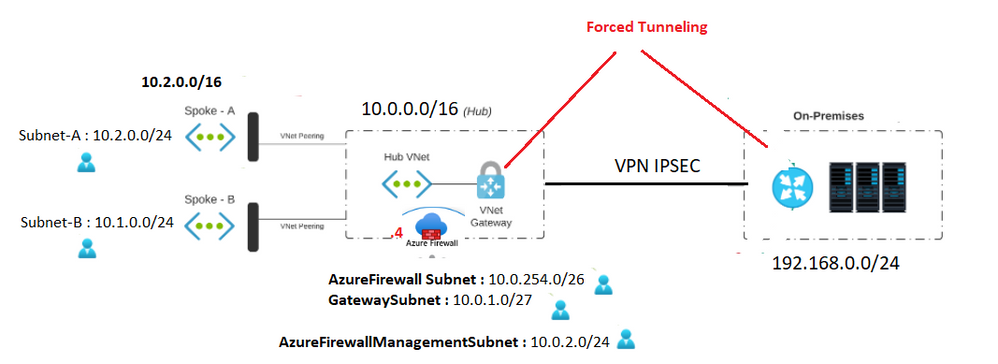
I have this architecture HUB and Spoke with Forced Tunneling applicated.
I need your propositon for the routes tables and the routes for every part.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2022 12:16 AM
Solution
Hi Ensure that you have the proper peering enabled
hub-to-spoke A with gateway transit
spoke A-tohub : Default + Use this virtual network's gateway or Route Server
hub-to-spoke B with gateway transit
spoke B-tohub : Default Use this virtual network's gateway or Route Server
If you want the incoming traffic (from the gateway ) to be filtered by the firewall attach a route table to the gateway subnet with the routes
Adress Prefix 10.1.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 10.2.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Ensure also that proper routes are present in spoke route tables
Route Table associated to Subnet Spoke A
Adress Prefix 10.0.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 10.1.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 192.168.0.0/24
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 0.0.0.0/0
Next Hop Type : Virtual Network Gateway (forced tunelling)
Route Table associated to Subnet Spoke B
Adress Prefix 0.0.0.0/0
Next Hop Type : Virtual Network Gateway (forced tunneling)
Adress Prefix 10.2.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall privat
Adress Prefix 192.168.0.0/24
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Read the full doc for forced tunneling if needed : https://docs.microsoft.com/fr-fr/azure/vpn-gateway/vpn-gateway-forced-tunneling-rm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2022 06:21 AM - edited Apr 26 2022 06:27 AM
Hello Ibrahima,
Thank you for your reply and assistance.
1-Can you confirme that for the :
** Route table attached to gateway subnet ( disable_bgp_route_propagation = true)
** All Route tables for the spokes ( disable_bgp_route_propagation = false)
2- You use the address space /16 and not the subnet /24 for every spoke in the routes ? Just to confirm that.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2022 06:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2022 10:29 AM
1- For HUB TO SPOKE :
resource "azurerm_virtual_network_peering" "peering-Hub-SPOKE" {
name =xxxxx
resource_group_name = xxxx
virtual_network_name = xxxxx
remote_virtual_network_id = xxxx
allow_gateway_transit = true
allow_forwarded_traffic = true
allow_virtual_network_access = true
use_remote_gateways = false
}
2- For SPOKE to HUB :
resource "azurerm_virtual_network_peering" "peering-SPOKE-HUB" {
name = xxxxx
resource_group_name = xxxxx
virtual_network_name = xxxxxx
remote_virtual_network_id = xxxxx
allow_virtual_network_access = true
allow_forwarded_traffic = true
allow_gateway_transit = false
use_remote_gateways = true
}
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 04 2022 04:25 AM
Yes it seems correct !
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 26 2022 12:16 AM
Solution
Hi Ensure that you have the proper peering enabled
hub-to-spoke A with gateway transit
spoke A-tohub : Default + Use this virtual network's gateway or Route Server
hub-to-spoke B with gateway transit
spoke B-tohub : Default Use this virtual network's gateway or Route Server
If you want the incoming traffic (from the gateway ) to be filtered by the firewall attach a route table to the gateway subnet with the routes
Adress Prefix 10.1.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 10.2.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Ensure also that proper routes are present in spoke route tables
Route Table associated to Subnet Spoke A
Adress Prefix 10.0.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 10.1.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 192.168.0.0/24
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Adress Prefix 0.0.0.0/0
Next Hop Type : Virtual Network Gateway (forced tunelling)
Route Table associated to Subnet Spoke B
Adress Prefix 0.0.0.0/0
Next Hop Type : Virtual Network Gateway (forced tunneling)
Adress Prefix 10.2.0.0/16
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall privat
Adress Prefix 192.168.0.0/24
Next Hop Type : Virtual Appliance
Next Hop IP address : Firewall private IP
Read the full doc for forced tunneling if needed : https://docs.microsoft.com/fr-fr/azure/vpn-gateway/vpn-gateway-forced-tunneling-rm