- Home
- Security, Compliance, and Identity
- Azure Network Security
- New Blog Post | Text4Shell RCE vulnerability: Protecting against and detecting CVE-2022-42889
New Blog Post | Text4Shell RCE vulnerability: Protecting against and detecting CVE-2022-42889
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 04 2022 12:02 PM
Similar to the Spring4Shell and Log4Shell vulnerabilities, a new critical vulnerability CVE-2022-42889 aka Text4Shell was discovered on October 13, 2022.
Text4Shell is a vulnerability in the Java library Apache Commons Text. This vulnerability, in specific conditions, allows an attacker to execute arbitrary code on the victim's machine (Remote Code Execution or "RCE").
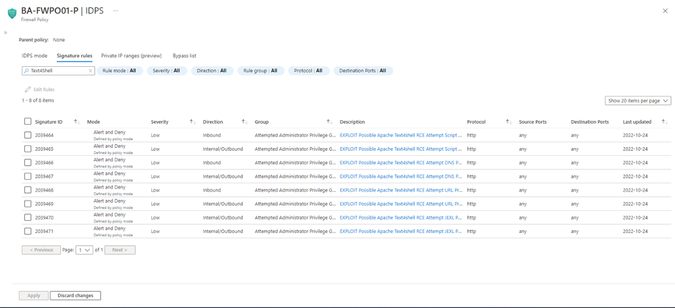
Customers can detect and protect their resources against Text4Shell vulnerability using Azure native network security services, Azure Firewall Premium and Azure Web Application Firewall (WAF). You can utilize one of these services or both for multi-layered defense.
Customers using Azure Firewall Premium, and Azure WAF have enhanced protection for this RCE vulnerability from the get-go. Customers can protect their assets by upgrading their Apache Commons Text version to the patched version 1.10. However, there are situations when upgrading software is not an option or may take a long period of time. In such case, they can use products like Azure Firewall Premium and Azure WAF for protection.
Original Post: New Blog Post | Text4Shell RCE vulnerability: Protecting against and detecting CVE-2022-42889 - Micr...
- Labels:
-
Azure Firewall
-
Azure WAF