Good morning AskPerf! Nabarun here from the Windows Performance Team to discuss the method of allowing RDP access to multiple servers in a flash. System administrators often want to know how to enable RDP access throughout the domain. The uninspired answer is to go around to every machine in the domain and add users and groups to the local “Remote Desktop Users” group.
This is the most restrictive and conservative approach to achieve the solution, reinforcing the idea that administrators should enable RDP access only to servers where it is necessary.
There are still situations where administrators need to allow domain users and groups RDP access to a large number of systems.
For RDP access, the following Security Setting must be configured:
Computer Configuration | Windows Settings | Security Settings | Local Policies | User Rights Assignment |Allow log on through Remote Desktop Services
The user or group must also have the “Allow User Access” permission on the “RDP-Tcp” connection. By default, the local group “Remote Desktop Users” has access to both items above; so adding any user to “Remote Desktop Users” group ensures RDP access. Click
here
for another blog on the topic.
Myth - Adding a user to the “AD Users and Computers\Builtin\Remote Desktop Users” group does NOT allow RDP access to all servers throughout the domain! This is just a local group for the DC.
There are several different methods to add users and groups to the local Remote Desktop Users group for client systems or member servers.
Method 1 (Startup script)
Add the following command to a startup script for all servers where RDP access is required:
NET LocalGroup "Remote Desktop Users" /ADD " domain\user or group name "
Method 2 (“Restrictive groups” GPO)
Scripts are generally the least preferred method of achieving configuration if there is an easier, scalable way to enable RDP access for groupings of systems throughout the domain. This can be achieved with the “Restrictive Groups” group policy.
This policy allows us to configure group memberships on client computers or member servers. We can add domain accounts or groups to local groups on systems within the domain.
In this example, we will add the domain group DomainRDPGroup to the local Remote Desktop Users group on all client computers in the domain in one shot:
1. Create a new group named DomainRDPGroup (configure it as a Global Security group) and then add the users who need RDP access to the systems.
2. Open Group Policy Management Console, and right click on the Default domain policy, then select Edit - this should open the Group policy management editor
NOTE: Keep in mind this is only an example and by editing the default domain policy you will be adding the DomainRDPGroup to the Remote Desktop Users group on every machine in your domain – including your domain controllers. It’s generally better to create a separate policy and link it to a specific OU that contains the systems we need to enable RDP access to.)
3. Right-click “ Restricted Groups ” from Computer Configuration | Policies | Windows Settings | Security Settings , and select “Add Group”
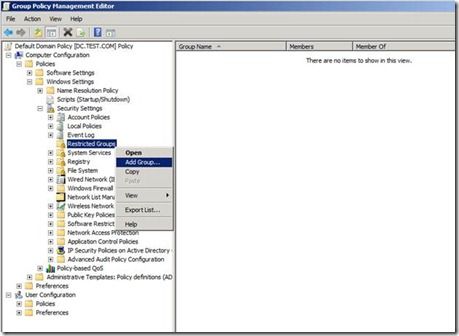
4. Type in or browse to the group we created in step 1 named “DomainRDPGroup”, then click OK.

After this, the “DomainRDPGroup Properties” will appear with an upper and a lower section. The top section allows you to modify the group membership of the group. Since we already added users to the DomainRDPGroup group, we can ignore this section in the policy.
NOTE: Entering any usernames as part of the policy setting will replace any existing group membership for this DomainRDPGroup. If we were to click Add and type user3 here, it would remove all of the users from DomainRDPGroup, and only leave user3. Leaving this section blank means it will use the existing group membership of DomainRDPGroup in Active Directory.
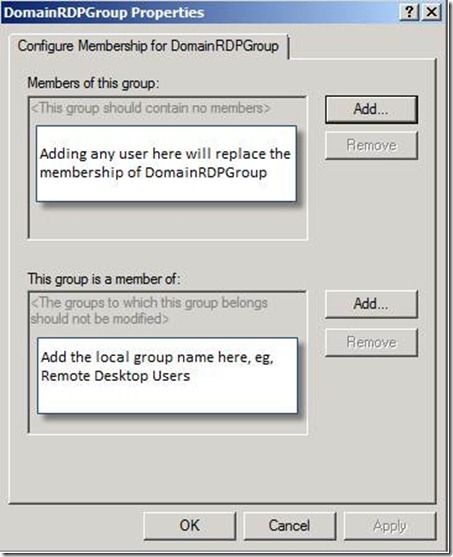
5. In the bottom section, click “Add” and type in the name of the local group; in this case, it is “Remote Desktop Users.”
This adds the entries entered in the section “This group is member of” into the local “Remote Desktop Users” group on each computer where the policy is applied.
Where the policy is applied depends on where the group policy is linked in the Domain. (Site, Domain, or Organizational Unit).This feature is non-intrusive and will not replace or remove the existing group membership of the Remote Desktop Users group on the target system. It simply adds additional members to the group.
More information about Restrictive Groups is available on TechNet .

7. Run “
gpupdate/force”
on the client computer. This will force the policy to apply immediately instead of waiting for the group policy processing interval to complete.
The following screenshot shows the local group “Remote Desktop Users”, which now includes our domain level group DomainRDPGroup. It also retains existing group members LocalUser1 and LocalUser2 which were added manually on the client computer.

This is a dynamic and seamless procedure of managing remote desktop group memberships at the Admin level without having to access the client computer/member server directly. Good luck!
-Nabarun Chakraborty
 Microsoft
Microsoft