Over the last couple of weeks, there has been an uptick in the number of different malware programs aimed at exploiting the vulnerability patched in MS08-067 . If you’ve been monitoring the various security websites and blogs, then you’ve probably already seen information on malware such as Worm:Win32/Conficker.A and Backdoor:Win32/IRCbot.BH . The major AV software packages are configured to detect this malware, so if you’ve already patched your systems with MS08-067 and your AV software is up to date, then the odds are that you are in decent shape. Nevertheless, here’s some of the common symptoms that you may see in relation to MS08-067 exploits:
- High CPU usage – especially by SVCHOST.EXE.
-
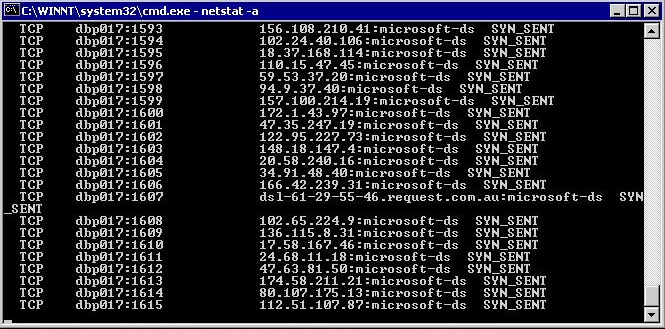
High connections to TCP port 445 (see the screenshot below)
- SVCHOST.EXE crashes – all of the services running in the same SVCHOST.EXE process will crash
A quick word of warning here – there are other reasons that SVCHOST.EXE might be experiencing high CPU usage, or may crash – remember that if your systems are already patched, then you’re probably experiencing something other than an MS08-067 exploit. To be on the safe side, here are some ways to identify if you are the victim of the exploit:
Steps taken to identify Worm: Win32/Conficker.A
- Run SERVICES.MSC: Check for a service that does not have a description with a name that is 4 to 8 bytes in length. This may be a Random Service Name (RANDOMSERVICENAME) that changes with each reboot
-
Check the Registry for RANDOMSERVICENAME:
Check this RANDOMSERVICENAME service in the registry
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RANDOMSERVICENAME]
"ImagePath"= “C:\Windows\system32\svchost.exe -k netsvcs”
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ RANDOMSERVICENAME \Parameters]
"ServiceDll"=”RANDOMDLL”
-
The DLL may be 62xxx bytes in size – depending on the variant of the malware
Steps taken to identify Backdoor:Win32/IRCbot.BH
- Run Registry Editor
-
Check two subkeys:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
-
Check for the presence of one o the following registry values / data. If the entries are there, the system is infected:
Value: "MS Gaurd Driver"
With data: "%ProgramFiles%\msgaurd.exe"
Value: "SoundMAX Driver"
With data: "%ProgramFiles%\soundmax.exe"
Value: "MediaAVI Driver"
With data: "%ProgramFiles%\mediaavi.exe"
If you discover that you have an infected system, here are the next steps:
- Use ACL’s to block port 445 on all network devices until all systems are patched
- Use IPSec to block inbound and outbound access to TCP port 445 on all Windows systems. By blocking inbound access, a system can be protected from the attack, and by blocking outbound access, affected systems can be prevented from attacking others. Windows Firewall is only able to block inbound access – which is why IPSec is required.
- All infected and uninfected systems should be patched with the latest security updates. The uninfected systems will be protected from the worms by the updates, however the infected systems will still try to attack systems
- On the infected systems, ensure that your AV software is up to date. The major AV packages such as Antigen, ESET, EZETrust, Kaspersky, McAfee, Microsoft Forefront, Symantec and Trend have AV definitions to detect these worms
As always, if you have any questions regarding this or any other exploit on a Windows system, or if you run into difficulties with cleaning infected Windows systems, please open a Support Incident with our Security team. Below are some additional resources regarding Security and Vulnerabilities.
With that, we’ve come to the end of this post. Until next time …
Additional Resources:
- Microsoft Malware Protection Center Blog
- Microsoft Security Vulnerability Research & Defense Blog
- The Microsoft Security Response Center Blog
- Microsoft Security Intelligence Report
- Forefront Client Security Team Blog
| Share this post : |
|
|
|

|

|

|

|

|
 Microsoft
Microsoft