- Home
- Azure
- Apps on Azure
- Execute Azure Function using ADF activity and AAD Login
Execute Azure Function using ADF activity and AAD Login
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Oct 29 2020 09:26 AM - last edited on Feb 01 2021 04:21 PM by Eric Starker
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 09:26 AM - last edited on Feb 01 2021 04:21 PM by Eric Starker
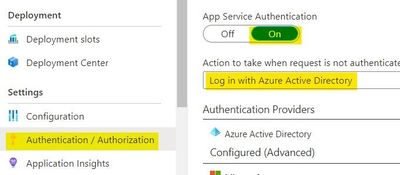
We are trying to execute an Azure Function (HTTP type) using Azure Data Factory (ADF). The Function App has the App Service Authentication set as "On" and the action to take when request is not authenticated is set as "Log in with Azure Active Directory".
If we have this configuration in the Function App, is it possible to execute the Azure Function from ADF?
We configured the Azure Function and Active Directory App by following this documentation:
Configure your App Service or Azure Functions app to use Azure AD login
We aren’t using a web app and maybe that’s the confusing part when trying to follow the steps from the documentation. ADF is the one that needs to authenticate when trying to access/execute the function. Do you know anything about this type of configuration?
- Labels:
-
AMA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 09:34 AM
@mariellecespedes I haven't done this myself before yet - but I believe it should work.
Have you enabled the managed identity on the Azure Data Factory?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 09:50 AM
Yes, we have Managed Identity in ADF.
The response when we get after the execution is a 401 Error type (unauthorized).
We used the Advanced settings configuration in the Function App and used the following information from the App Service app:
- Client ID
- Tenant ID
- Client secret
- Application ID URI
We retrieved the information from the Overview tab from the App Service app. Copy-pasted it into the Function App configuration and followed the steps from the documentation.
We aren’t using a web app (in this case it is ADF) and maybe that’s the confusing part when following the steps from the documentation, as ADF is the one who is calling the function.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 09:55 AM
@mariellecespedes When you access the function directly (not using ADF) - do you get the same 401, or does that authenticate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 10:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 10:05 AM
OK, so this seems to be functions related indeed and not ADF related.
Have you tried accessing the functions URL directly in a web browser to see if you get a redirect to AAD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 10:13 AM
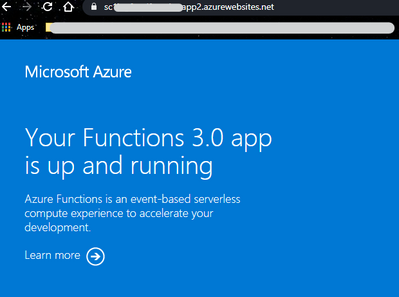
Yeah, it seems to be functions related, thanks.
Yes, I pasted the functions URL in a web browser and it prompted me for my login credentials. I entered them and this was the result:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 29 2020 10:37 AM
@mariellecespedes OK, that's a good sign, meaning the AAD sign-on actually works.
I seems like I was too optimistic about this scenario, it seems like AAD authentication FROM ADF is not supported. You will have to use a Functions key when connecting from ADF. I'm sorry about not confirming this earlier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 22 2020 08:41 AM
Any chance this is going to make it on the roadmap for ADF? AAD Auth from ADF I mean?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 19 2021 04:56 PM
Hi Nills, Would function key work from ADF to call function with AAD authentication enabled on the function app?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 10 2021 06:22 AM
Has anyone tried it by enabling Authentication on function app and accessing it from ADF through function key authentication. I don't think it works. If anyone made it work then please let me know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 08 2021 10:08 PM
Hello @venkatadorisala ,
I have tried this using function key for http trigger it worked. The only challenged is when i was working in vnet hosted SHIR for Azure data factory.
do you have privet network for your azure function and ADF ?
This is challenging that time otherwise it work like a charm for me.
Thanks,
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 15 2022 09:56 AM - edited Sep 15 2022 10:21 AM
Hi, Thanks for the response. So in this case when ADF is authenticated via function-key on azure function and ADF has managed identity enabled.
I have a similar situation where both ADF and Az-functions are in a VNET but I am still getting failure error message. I have two questions.
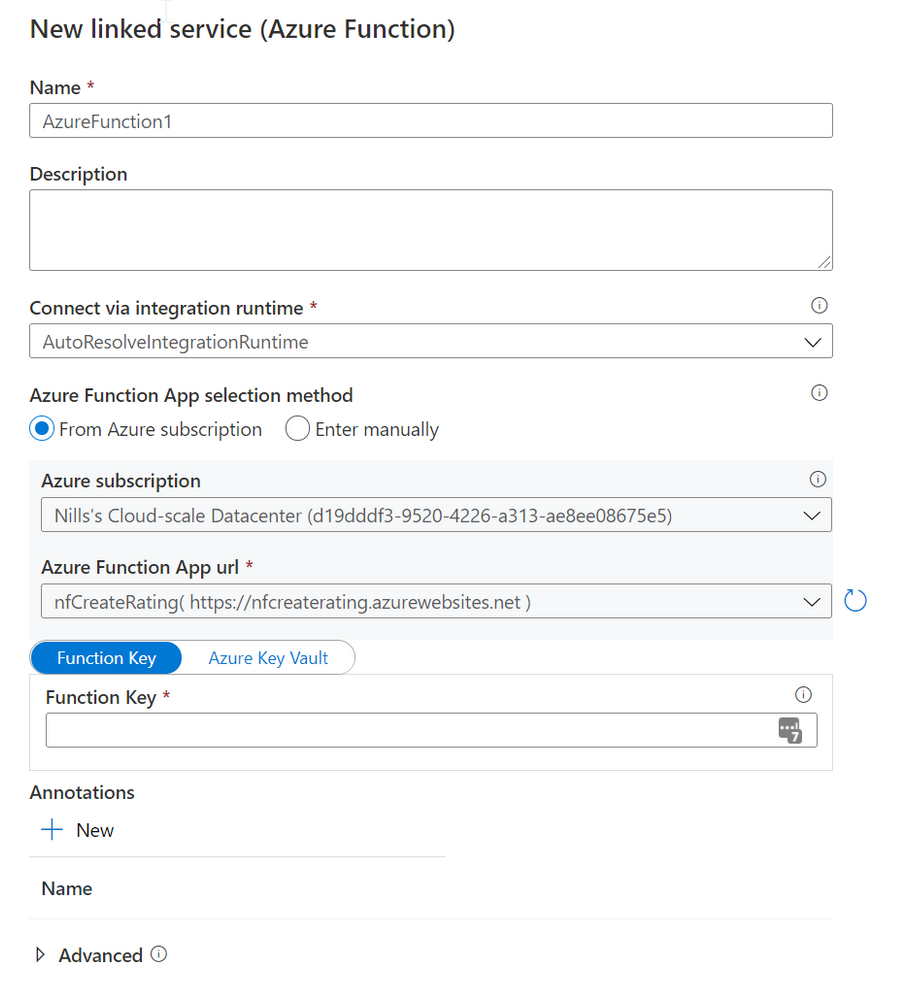
1/ while creating linked service for Az function, when it asks for key. is it key-name or value we have to provide
2/ what RBAC role I have to assign to ADF in Az-function' IAM blade ?
3/ Do I have to assign same role at App-plan blade also ?
4/ does function-app need to be registered in AAD
Error Message:
'Failed to get MI access token. The error message is: Acquire MI token from AAD failed. ErrorCode: invalid_resource, Message: AADSTS500011: The resource principal named https://xxx.azurewebsites.net was not found in the tenant xxx. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant.