- Home
- Security, Compliance, and Identity
- Microsoft Defender Vulnerability Management Blog
- Vulnerable Components Inventory now in public preview
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In recent years, software supply chain vulnerabilities and related supply chain attacks have become a major concern for security teams across industries. As software systems become increasingly complex and software developers rely more on open-source software packages and commercial third-party software components, it has become difficult for security teams to keep track of and mitigate new vulnerabilities found within software being used in their organizations.
To address this challenge, Microsoft Defender Vulnerability Management is introducing a dedicated inventory that lists known vulnerable software components found in the organization. This inventory, along with a new security recommendation, improves visibility of vulnerabilities found within software components, such as open-source libraries. These components are widely used, but often not clearly visible, due to inner dependencies within software products.
By increasing awareness among security teams of vulnerabilities found in software components that are being used by multiple software products within an organization, security administrators can identify affected devices, prioritize, and mitigate risk proactively. Therefore, improving their security posture and reducing the risk of potential cyber-attacks.
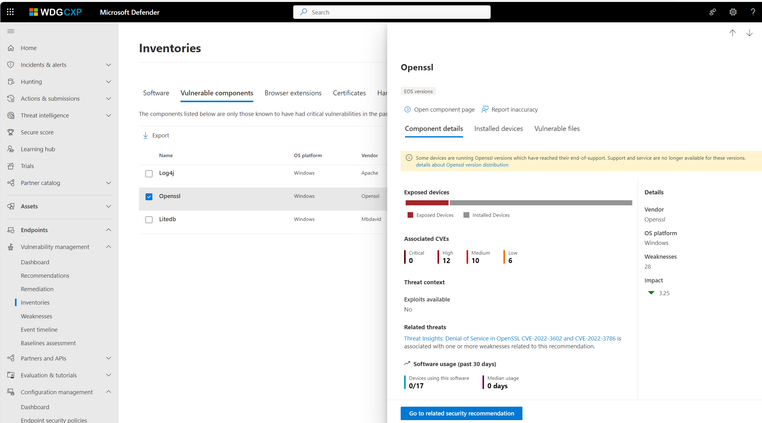
The new Vulnerable Components Inventory includes a list of software components that are known to have critical vulnerabilities in the past.
The following is a list of components that are currently supported. A few of these components were previously shown under the ‘Software inventory’ but are now available via the ‘Vulnerable components’ inventory.
- Apache Commons Text
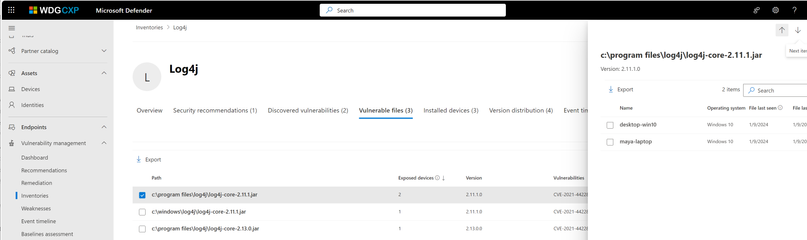
- Apache Log4j
- Apache Struts [newly supported]
- LiteDB
- OpenSSL
- Spring Framework
- WebP (libwebp) [newly supported]
Defender Vulnerability Management coverage of software components will continue to expand based on the ever-evolving threat landscape and customer demand. For example, in light of critical vulnerabilities recently found in WebP (CVE-2023-4863)
and Apache Struts 2 (CVE-2023-50164), Defender Vulnerability Management was updated to support both components.
For each vulnerable component you will see basic information including the component name and vendor, the number of weaknesses related to that component and the impact to the overall exposure score, whether an exploit is available, and if there are active threats or alerts associated with it.
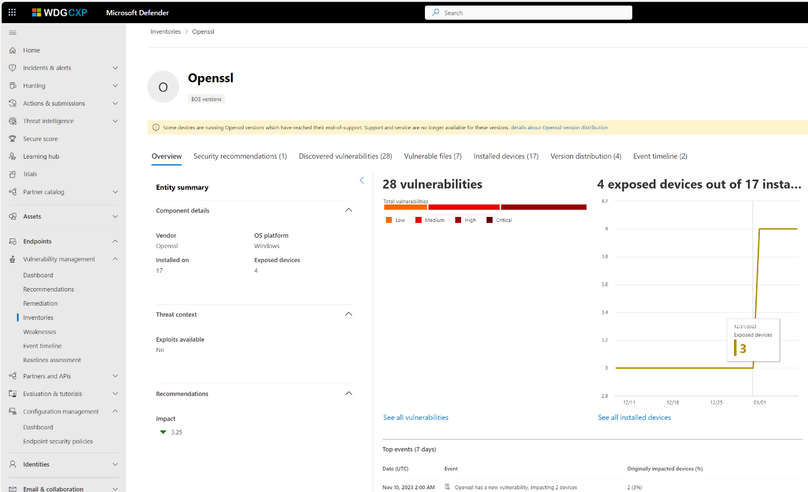
The Component page’s tabs provide detailed information and insights:
- Data visualizations show the number of, and severity of, vulnerabilities and graphs with the number of installed and exposed devices.
- Named CVEs of discovered vulnerabilities.
- Devices that have the component installed along with device name, domain, OS, and more).
- List of components’ versions, including number of devices the version is installed on, the number of discovered vulnerabilities, and the names of the installed devices.
In addition, a list of vulnerable files found is provided with file paths, version, and associated vulnerabilities, which can be exported for further investigation and handling.
Defender Vulnerability Management provides actionable Security Recommendations to assist security administrators reduce their organization’s exposure to vulnerabilities through the process of keeping their software up to date. Given the inherited complexity of updating a software component within an enterprise environment, the Attention required recommendation is designed to raise awareness of security teams to an emerging threat and explore their next steps, rather than a call for action to update a version, which may not be applicable for a specific software component.
Administrators can also drill down to a specific device and view a list of vulnerable components with the relevant file level evidence details.
Learn more.
If you’re interested in learning more about Microsoft Defender Vulnerability Management visit our website to take advantage of our free 90-day trial, check out our interactive guide, and read more information in our product documentation.
Providing feedback.
As always, we’d love to know what you think. Looking forward to your feedback. share your feedback directly at: mdvmfeedback@microsoft.com
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.