- Home
- Security, Compliance, and Identity
- Microsoft Defender for IoT Blog
- Analyze IoT/OT device firmware with Microsoft Defender for IoT
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Consider an organization that has thousands of endpoints on their network that are running 10-year old, unpatched SSH servers. Or when a critical vulnerability like log4shell is discovered, having no easy way to know which of those endpoints are exploitable. This is the situation organizations find themselves in when it comes to IoT and OT devices. This problem is so important that the US National Cybersecurity Strategy released a report in March 2023 indicating the IoT security threat as a strategic objective.
With modern endpoint solutions, IT and security analysts get visibility into the software inventories and known vulnerabilities for IT devices. But for IoT and OT devices without an agent, organizations don’t get the same level of visibility into the growing number of devices on their network. The devices are basically black boxes – without insight into what software or patch level was used to build the device, known vulnerabilities, or other potential anomalies. To help address this challenge, we are excited to announce the firmware analysis capability in Microsoft Defender for IoT – now available in Public Preview.
How firmware analysis works
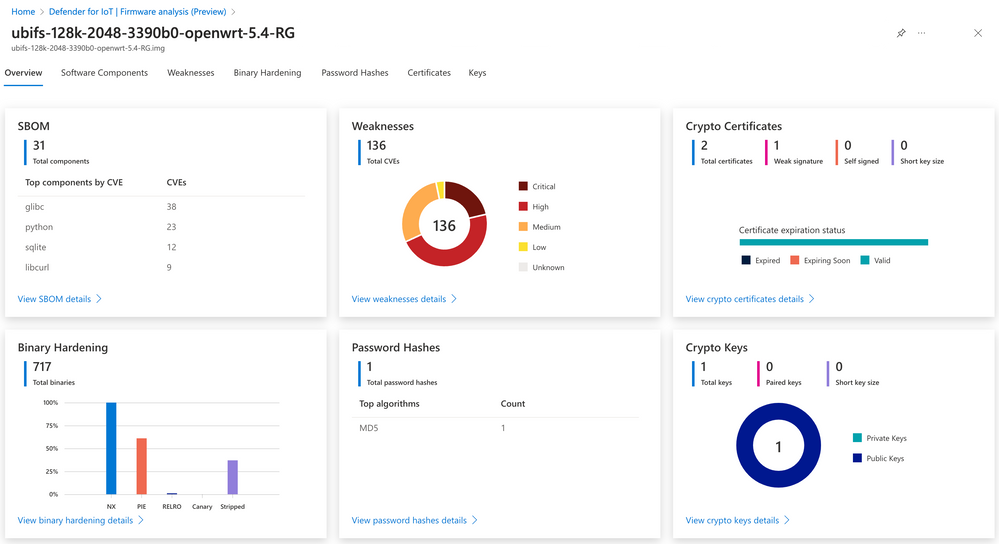
Firmware analysis takes a binary firmware image that runs on an IoT device and conducts an automated analysis to identify potential security vulnerabilities and weaknesses. This analysis provides insights into the software inventory, weaknesses, and certificates of IoT devices without requiring an endpoint agent to be deployed.
To use the firmware analysis capability, navigate to the “Firmware analysis (preview)” blade in Defender for IoT and upload an unencrypted Linux-based firmware image directly. The image needs to be acquired from the device vendor. Once the image is unpacked and the embedded file system is identified, a thorough security analysis of the firmware image identifies hidden threat vectors.
Identifying software packages and vulnerabilities
Firmware analysis begins by producing an inventory of the open-source packages found in the firmware image, like a Software Bill of Materials (SBOM). This information helps manufacturers track and manage the open-source components in their firmware. Relying on this software inventory, firmware analysis helps security teams identify existing vulnerabilities by scanning the firmware for published Common Vulnerabilities and Exposures (CVEs), bringing them to the attention of device builders and enterprises.
Analyzing binaries
After identifying vulnerabilities, firmware analysis goes a step further by assessing binary hardening. It looks at how the code that runs the device was built, and whether it conforms to security best practices such as Stack Canaries. Binary hardening analysis shows the difficulty or ease of possible binary exploitation and is also a good proxy for the overall security hygiene taken by the manufacturer.
Identifying weak accounts and crypto
Another important threat vector in IoT devices is the use of hardcoded accounts. For example, the Mirai botnet is malware that leverages over 60 default usernames and passwords to take over IoT devices and uses them to conduct mass Distributed Denial of Service (DDoS) attacks. Firmware analysis in Defender for IoT identifies built-in user accounts and the algorithms used to encrypt password hashes of those accounts. Device manufacturers can use this information to make improvements to their firmware, and enterprise operators will be able to identify devices on their network that may pose risk.
Firmware analysis also identifies cryptographic material embedded in the device. Adversaries commonly target these materials as entry points. For example, expired, revoked, or self-signed SSL certificates can compromise communication from a device to a cloud service, potentially leaking organizational data or opening the device up to exploitation. Another potential threat vector are public and private keys that were inadvertently left in the device by the developers and grant attackers access to the device or cloud service.
Let us know what you think
Navigating the increasingly complex IoT landscape requires the right set of tools to paint a clearer picture into your IoT environment. The firmware analysis capability in Defender for IoT is enabling security teams to get deeper visibility into these IoT/OT devices by providing better insights into the foundational software they are built on.
We are excited to share the firmware analysis capability with you. If you have any feedback, please feel free to let us know in the comments below.
To learn more about firmware analysis, click here.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.