- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint
- ASR - Behavior Changes - Blocking under User Context Now?
ASR - Behavior Changes - Blocking under User Context Now?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 02 2022 05:50 PM - edited Aug 02 2022 05:54 PM
Since July 7-27-2022
I have been seeing around 40 of 1800 machines in my work environment that are showing blocks under %userprofile% or usercontext for .dll blocks. This is new behavior and is recent. All of our machines have the same ASR rule applied, I checked on the machines via registry and their ASR rules are the same.
ASR Rule/Example Path - that is having this issue
Block executable content from email client and webmail
GUID: be9ba2d9-53ea-4cdc-84e5-9b1eeee46550
Path: %userprofile%\AppData\Local\Assembly\tmp*variousfilesandpaths.dll
Did this behavior change, is this a preview of a new feature or is this a bug? I am afraid this may spread to more machines.
We have E5 License and an MS Ticket Open as well. Hoping someone hear knows something as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 10 2022 06:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2022 12:37 AM
We are experiencing the same/similar issue too. Started about 2 weeks ago, is only effecting a small number of computers but number seems to be growing.
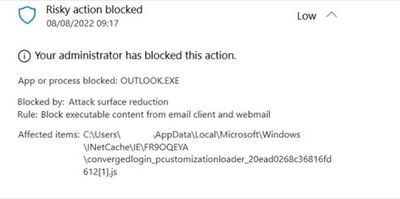
When Outlook requires authentication Defender blocks the log on screen from appearing as the ASR rule "Block executable content from email and client webmail" is blocking .JS files in C:\Users\local_\INetCache\IE<FOLDER>
Actual file can vary but so far I have seen: C:\Users\local_\INetCache\IE<FOLDER>\CommonDiagnostics[1].js
C:\Users\local_\INetCache\IE<FOLDER>\knockout-3.4.2[1].js
C:\Users\local_\INetCache\IE<FOLDER>\jsonstrings[1].js
C:\Users\local_\INetCache\IE<FOLDER>\jquery-1.12.4.1.min[1].js
C:\Users\local_\INetCache\IE<FOLDER>\hrd.min[1].js
C:\Users\local_\INetCache\IE<FOLDER>\convergedlogin_pccustomizationloader[1].js
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2022 12:56 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2022 12:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2022 02:40 AM - edited Aug 11 2022 03:29 AM
We are also facing the issue on several computers. The strange thing is, that all the version (Defender Engine, Signatures, Outlook and Windows) are reporting the same on affected and non-affected machines. Even the outlook internal help (press F1) is blocked.
We have also created a Microsoft case.
We provision the rules using Configuration Manager.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 11 2022 03:27 AM
we received the answer that it is indeed a known issue that has to be solved by the ms product team
we use intune to deliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 02:47 AM
If you get a response to say it has been fixed or if we are required to make any changes it would be great if you could post them here.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 02:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 03:07 AM
first we used hash from loaded plugin dll -> did not help
today we added all dll from the plugin (condeco) -> didnt help
currently we are waiting for additional microsoft support callback
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 03:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 03:09 AM
or problem plugin no1 is condeco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 03:14 AM
1 taking logs
2 idicator whitelisting
3 taking logs again to get to the prob.
we have another meeting with microsoft in 20 min and this time the agend knew about the possible product team fix. for this they want to pull logs again i believe. anyhow i keep sharing our experience :D
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 04:19 AM - edited Aug 12 2022 04:24 AM
What you could do temporarily is create exclusions for ASR Rules.
Blocked at Path
c:\users\jdoe\AppData\Local\Assembly\tmp\VXRVB.GHY\TheNameOfYourFile.dll
Example Exclusion
%userprofile%\AppData\Local\Assembly\tmp\*\TheNameOfYourFile.dll
Further Info
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 04:38 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 04:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 04:52 AM
You said that the ASR team have made some adjustments. Did they explain how those adjustments will be delivered to client and the time to see the results?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 05:03 AM
I also asked how we can check if a file hash rule has applied to a device but he categorically confirmed there are no local logs in Event Viewer or any associated reg keys for security purposes. So surely there's a log on the M365 Security portal? Again, no definitive answer other than check the "last device update" column for the device, which is a good indicator but not confirmation that the file hash rule has definitely applied successfully.
'Reports > Attack surface reduction rules' already showing a much lower number of detections (mostly false-positive) but that could just be because it's a Friday and super hot weather. Monday will be a better indicator of progress once all devices have received the file hash rule updates, cold booted etc...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 05:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 06:43 AM
Has anyone been given an explanation of why this is only affecting a small percentage of identically configured computers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2022 07:14 AM