- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Announcing mobile device tagging for iOS and Android
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update - 10/31/2023 - Tagging iOS and Android mobile devices in Microsoft Defender for Endpoint is now generally available.
Today, large enterprises are operating in multiple locations with decentralized SOC teams tasked with ensuring that company endpoints and data are not only safeguarded from threats but adhere to compliance and privacy policies. Without access control for admins, analysts would have access to all device information found across these locations – even those classified as sensitive devices, which could lead to privacy and security concerns. To alleviate these concerns, admins should implement controls that only allow designated analysts to have access to specific device groups they are responsible for protecting.
To ensure that admins can group all endpoint devices across their environment with ease, we are pleased to announce that Microsoft Defender for Endpoint enables admins to tag iOS and Android mobile devices, is now generally available.
What is device tagging?
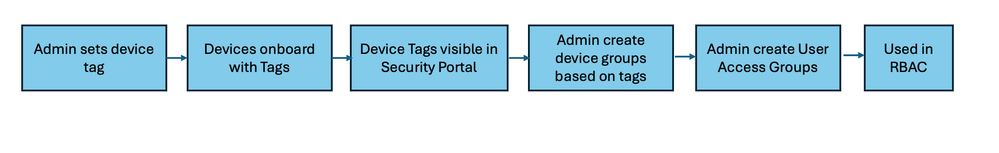
Tags are used primarily to label and classify devices in an environment. This help make searching easy, promotes better organization, and streamlines designating rules to specific groups or categories. In today’s reality where SOC analysts are decentralized across multiple geographical locations, this capability helps admins designate and group devices by location while ensuring that the correct role-based access control permissions are assigned to the SOC analysts responsible for that location. Tags are unique keywords set by admins to be assigned to particular devices. Admins then creates device groups based on these tags.
How to tag devices
Adding tags to devices that are already onboarded is simple. Admins can set a tag against a device in the Microsoft 365 Defender portal.
During onboarding and bulk tagging, the process becomes a little bit more involved. Device tagging during onboarding begins with admins setting a device tag. This is possible on Windows, macOS and Linux through registry keys and onboarding scripts, however this is not applicable for mobile devices. Once the devices onboard to Defender for Endpoint, these devices receive a tag visible in the Defender portal. The admin then creates the device group(s) based on these tags. Next, user access groups are created and assigned to these device groups. The user access groups are then used to setup role-based access controls.
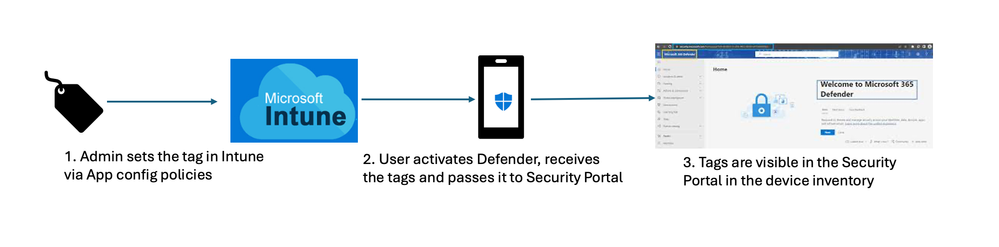
Now you might be wondering, what about mobile devices? We have made it possible to bulk-tag mobile devices during onboarding by allowing the admins to setup tags using Microsoft Intune.
Assigning tags with Microsoft Intune
Admins can configure the device tags using Intune through configuration policies and push them to user’s devices. Once the user installs and activates the Microsoft Defender client application, the mobile device begins receiving policies. The Microsoft Defender client application then passes the device tags to the Defender portal. The device tags appear in the device inventory. For customers with mobile device management or mobile application management, admins can set the device tags through App Configuration policies.
Configuring tags
Install the latest version of the Microsoft Defender client application.
Follow the steps below to configure tags for managed devices
1) For mobile device management – In Microsoft Intune admin center,
- Go to Apps > App configuration policies > Add > Managed devices
- Give the policy a name,
- For iOS : select Platform > iOS/iPadOS,
- For Android: select Platform > Android Enterprise,
- Select Microsoft Defender for Endpoint as the target app.
- In Settings page, select Use configuration designer and add DefenderDeviceTag as the key and value type as String.
- Admin can assign a new tag by adding the key DefenderDeviceTag= <set a value for device tag>
- Admin can edit an existing tag by modifying the value of DefenderDeviceTag = <modify the value of previously set tag>
- Admin can delete an existing tag by removing the key DefenderDeviceTag
- Click Next and assign this policy to targeted devices/users.
2) For mobile application management (MAM) – In Microsoft Intune admin center,
- Go to Apps > App configuration policies > Add > Managed apps.
- Give the policy a name.
- Under Select Public Apps, choose Microsoft Defender for Endpoint as the target app.
- In the Settings page, add DefenderDeviceTag as the key, under the General Configuration Settings
- Admins can assign a new tag by adding the key DefenderDeviceTag= <set a value for device tag>
- Admins can edit an existing tag by modifying the value of DefenderDeviceTag = <modify the value of previously set tag>
- Admins can delete an existing tag by removing the key DefenderDeviceTag
- Click Next and assign this policy to targeted devices/users.
3) End-user onboarding
- User downloads, opens and installs the Microsoft Defender client application with the required permissions.
- Upon successful onboarding, the device tag received from Intune’s policy is passed to the Defender portal.
Testing device tags
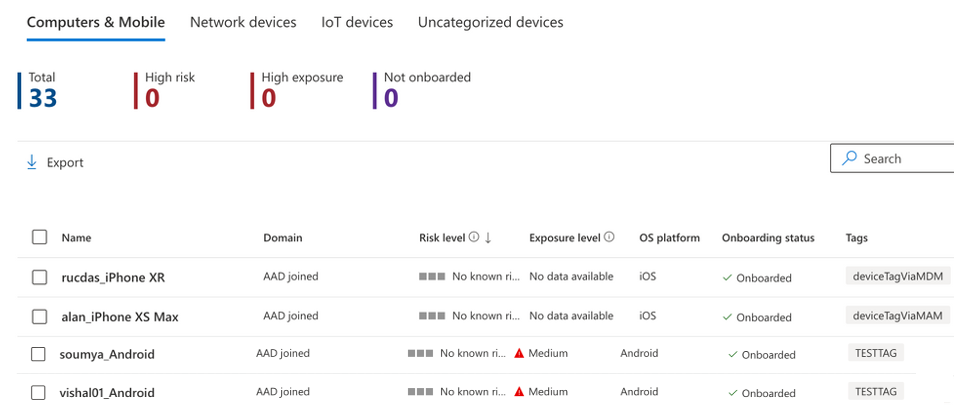
- Admins can validate the device tag in the Defender portal.
- Tags are visible in the device inventory against the device onboarded
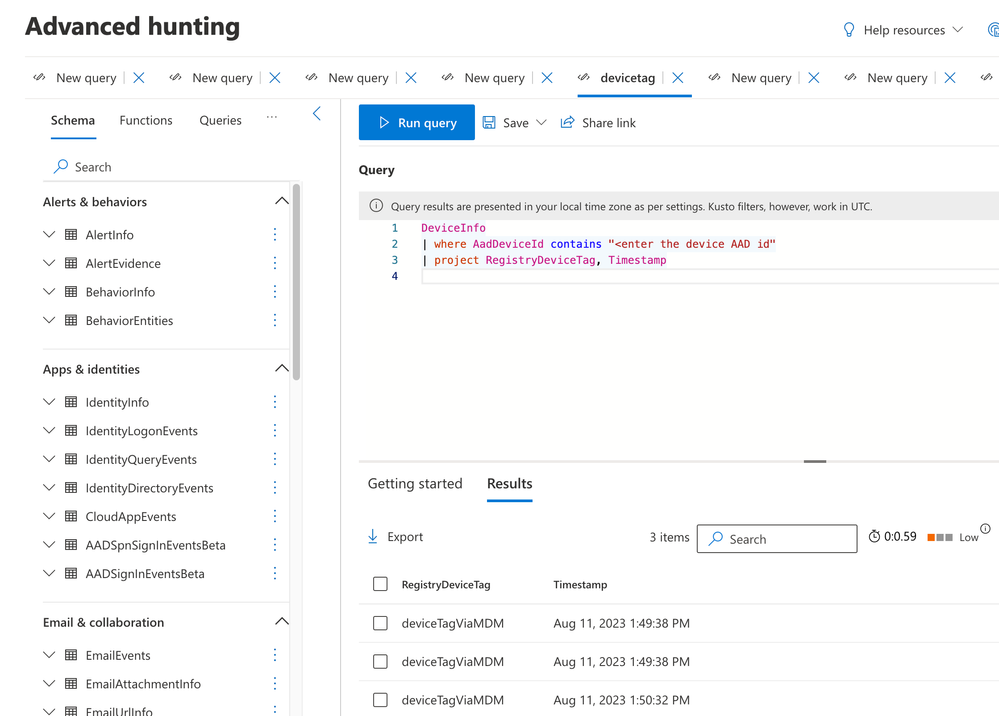
- Admins can also validate the device tags using Advanced Hunting queries.
Note:
- Please note that it may take up to 18 hours for tags to reflect in the Defender portal.
- The Microsoft Defender client application needs to be opened for tags to be synced with Intune and passed to the Defender Portal.
More Information:
Check out our documentation for more details on mobile device tagging. iOS | Android
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.