- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- High severity curl vulnerability: prepare with Microsoft Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
On October 3rd, high severity vulnerabilities in curl were preannounced. The curl project has announced that curl8.4.0 has now been released, earlier than expected. Two vulnerabilities have now been disclosed: high-severity CVE-2023-38545 and low-severity CVE-2023-38546.
curl is a popular command-line tool and library (libcurl) used to transfer data across network protocols using URL syntax. The library is one of the most widely used open-source projects across most operating systems, including Windows and Linux, and is one of the most popular OSS packages present in clients, embedded systems, and cloud-native applications/containers.
CVE-2023-38545 refers to a heap overflow vulnerability associated with the SOCKS5 proxy handshake in both libcurl and curl. When curl receives a hostname exceeding 255 bytes to relay to a SOCKS5 proxy, it defaults to local name resolution to determine the address before transferring it to the SOCKS5 proxy. A 2020 bug makes this local resolution potentially fail if the SOCKS5 handshake is delayed. As a result, curl might forward the oversized hostname to the intended buffer, triggering a heap overflow.
CVE-2023-38546 pertains to a cookie injection vulnerability in curl_easy_duphandle(), a libcurl function responsible for duplicating easy handles. If cookies are active when an easy handle is duplicated, the resulting duplicate doesn't copy the actual cookies. Instead, it sets the filename to 'none.' As a consequence, when this duplicated easy handle is later utilized and no source is defined for the cookies, libcurl tries to load them from a file titled 'none' located on the storage.
What is the impact and how do I identify risk?
As a widely used OSS component in cloud-native applications, curl is very likely present in many resources, including Virtual Machines and Container Images. We strongly recommend that you collect an inventory of affected resources to ease the remediation process once the update is released.
Microsoft Defender for Cloud has multiple ways to quickly determine where in your environment you are vulnerable that are covered in this blog.
Method 1: Hunt for all impacted resources using the cloud security explorer
Note: To hunt for impacted resources, first enable Defender CSPM in Microsoft Defender for Cloud and ensure that the agentless scanning, container registry scanning, and agentless discovery for Kubernetes are enabled. For more details on enabling these services, click here for Defender CSPM.
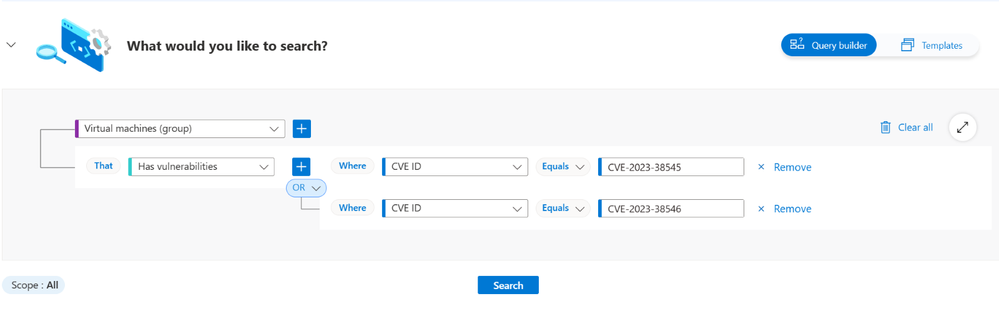
To query the cloud security graph for affected servers:
- Sign in to the Azure portal.
- Use the following links to pre-populate Cloud Security Explorer queries:
To query the cloud security graph for affected container images:
- Sign in to the Azure portal.
- Use the following links to pre-populate Cloud Security Explorer queries:
Learn more about cloud security explorer and other Defender CSPM capabilities.
Method 2: Identify VMs where the application installed contains curl using Inventory
Note: To hunt for impacted resources, first enable Defender CSPM or Defender for Servers P1 or P2 in Microsoft Defender for Cloud and ensure that agentless scanning is enabled or that vulnerability scanning with Microsoft Defender Vulnerability Management is enabled. For more details on enabling these services, click here for Defender CSPM and here for Defender for Servers.
- Sign in to the Azure portal.
- Filter for Installed applications contains curl.
- Sort based on the number of unhealthy recommendations.
- Remediate the unhealthy recommendations to ensure that your attack surface is reduced.

Method 3: Identify resources containing curl using Azure Resource Graph
- Follow the above steps. Within the Inventory blade select Open Query.
- Run the sample queries below.

Sample query for retrieving virtual machines running curl:
securityresources
| where type == "microsoft.security/softwareinventories"
| where name has "curl"
| extend deviceId = tostring(properties.deviceId),
subscriptionId = tostring(properties.azureSubscriptionId),
osPlatform = tostring(properties.osPlatform),
version = tostring(properties.version),
softwareName = tostring(properties.softwareName),
azureVMId = tostring(properties.azureVmId)
| where not(version has ("8.4"))
| extend vmId = iff(azureVMId has "securityconnectors", split(azureVMId, '/')[10], split(azureVMId, '/')[8])
| extend environment = iff(id has "Microsoft.HybridCompute", "arc", iff(id has "microsoft.security/securityconnectors", "multicloud", "azure"))
| project id, subscriptionId, vmId, softwareName, version, osPlatform, environment
Sample query for retrieving container images with a curl vulnerability:
securityresources
| where type =~ "microsoft.security/assessments/subassessments"
| extend assessmentKey=extract(@"(?i)providers/Microsoft.Security/assessments/([^/]*)", 1, id), subAssessmentId=tostring(properties.id), parentResourceId= extract("(.+)/providers/Microsoft.Security", 1, id)
| extend resourceId = tostring(properties.resourceDetails.id)
| extend subAssessmentName=tostring(properties.displayName),
subAssessmentDescription=tostring(properties.description),
subAssessmentRemediation=tostring(properties.remediation),
severity=tostring(properties.status.severity),
status=tostring(properties.status.code),
cause=tostring(properties.status.cause),
statusDescription=tostring(properties.status.description),
additionalData=tostring(properties.additionalData)
| where assessmentKey == "c0b7cfc6-3172-465a-b378-53c7ff2cc0d5"
| where status == "Unhealthy"
| where subAssessmentId in ("CVE-2023-38545","CVE-2023-38546")
| extend repositoryName = tostring(properties.additionalData.artifactDetails.repositoryName),
registry = tostring(properties.additionalData.artifactDetails.registryHost)
| distinct repositoryName, registry
Identify other curl usage patterns
Depending on your use case, it might be worth monitoring certain curl usage patterns. For example, you might have inadvertently hardcoded a curl release for download in a Dockerfile or a CI workflow definition.
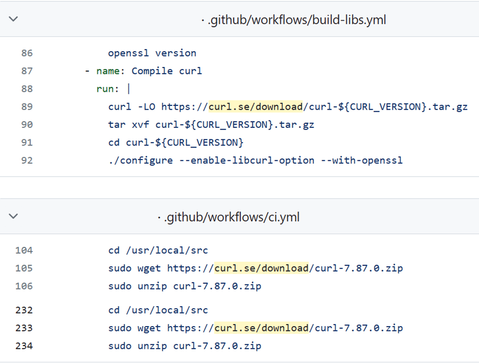
For GitHub Repos, you can leverage GitHub Code Search with a query like: (path:.github AND path:.yml) OR (path:Dockerfile) AND (curl.se/download OR github.com/curl/curl/releases) AND (org:<your org>).
You might encounter a hardcoded release number in this URL, or a parameter pointing to a hardcoded value. The screenshot below shows both patterns:
Authors
- Lara Goldstein, Product Manager 2
- Charles Oxyer, Product Manager
- Jose Miguel Parrella, Principal Architect
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.