- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Apps
- Valid Client Certificate Setup
Valid Client Certificate Setup
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 12 2019 06:45 AM
How do you get valid client certificate to work?
What i have so far.
1. CA with Intermediate, User Certificate Template cloned for this purpose
2. Issued a cert to my domain desktop and IOS device
3. Enabled a conditional access policy for custom MCAS policy
4. Root and intermediate cert upload to MCAS
5. MCAS policy to block if there is no valid client certificate.
the block works, i get the "test block" message. but i can't get the client certificate prompt or figure out why it won't prompt for certificate.
My end goal is to test valid client certificate against a few 3rd party IOS apps where device certificate/standard device compliance checkbox doesn't work in conditional access.
- Labels:
-
Cloud App Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 14 2019 07:43 AM
tried to replace my individual root / intermediate certificates with a single file chained file. no luck so far.
anyone using valid client certificate option in MCAS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 12 2019 03:39 PM
I have the exact same issue. No combination of policy, certificates or settings seems to work.
We can successfully block access, but cannot get an MCAS Access policy to actually request a certificate from a client browser.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 16 2020 12:12 PM
@gd-29 Did you get any feedback on this? I have the exactly same issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 20 2020 12:10 PM
@rodrigobe i was only able to get this to work from one method. i think it was from a ios mobile device.
i could not get this to prompt on a windows machine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 20 2020 12:20 PM - edited Apr 20 2020 12:21 PM
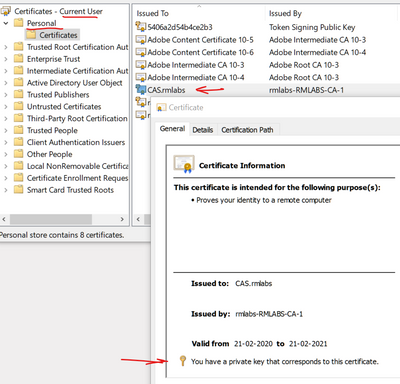
@rodrigobe are you importing the cert on the client in the current user's personal store? that's where the cert needs to be on the machine and it also needs to have a private key. Once you have configured a session/access policy to check for a valid client cert, you should be prompted to select one from this store when you browse to app you configured in the policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 11:59 AM
Hello,
Sorry to resurrect this thread.
I'm also trying to get a client-certificate based condtional access session policy to work in MCAS.
I can get the browser to prompt for the certificate I issued, but it never accepts it and access is always blocked. I'm sure the issuing CA chain is correct and configured in MCAS, but MCAS just doesn't like any certificate I issue from the CA.
Has anybody managed to get this to work?
Thanks,
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 12:04 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 12:04 PM
@ataviste did you try just the root CA or a combination of root and intermediate uploaded?
i forgot what was recommended by support when i was trying.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 12:10 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 12:15 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 12:17 PM - edited Apr 21 2020 12:18 PM
Hi,
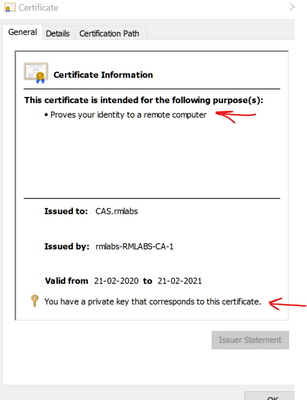
Yes I imported a PFX, and the "You have a private key that corresponds to this certifcate" message is present.
The cert usage is client authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 12:25 PM
also, just to understand the behavior, you are prompted for the cert and presented a list box, you select one and then does the page fail to load? or does it load but block activities configured in policy as if the cert is not valid?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 01:26 PM
Hi,
I'd already disabled the CRL checking.
Firefox prompts me for the client cert, it is the correct certifcate. I select it, and shortly afterwards the "access blocked" page is displayed.
I've also tried in IE on Windows, I'm not prompted for a cert (although I did add the PFX to IE) , but again the access blocked page is displated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 01:49 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 02:00 PM
Hi,
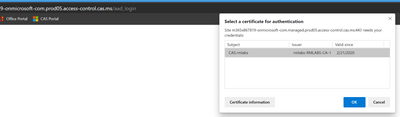
I got it to work!
I had added a session policy in MCAS (which is supposed to be for browser clients). I replaced that with an access policy (see screenshot), and now things work as expected on Firefox on Linux and in IE11 on Windows (I got prompted for the cert on IE11 though, even though I'd added the client cert to the user cert store).
Trying on another machine without the client cert blocks access (to MS Exchange) as expected.
Can you confirm your working setup is with an access policy in MCAS?
Thanks for your help.
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 02:09 PM
Hi @rajatm
I tried it with your certs/CA and they also work with my access policy. Looking at the certs they have the same key usage etc. (but you have no intermediate CA)
I created it initially as a session policy as they are supposed to be for browser clients. Very confusing!
Thanks very much for your help
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 02:11 PM
i have both session and access policies using the same certs and working as expected.
if you only need to block access to devices without certs, an access policy is the right way to go.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 02:15 PM
Hi@rajatm ,
Should my session policy have worked as well then? I guess something else was not quite right with it.
Thanks,
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 21 2020 02:20 PM
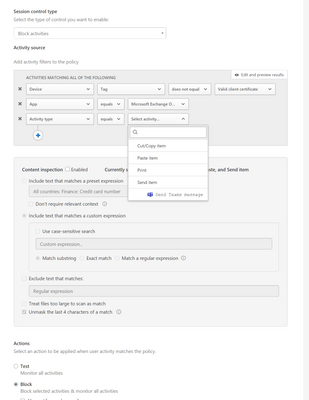
@ataviste depends on what you had configured in it. for example, this config for a session policy will block selected activities in the 3rd filter when a user logs on to EXO OWA and the device does not have a valid cert. it will not block overall access.