azure ad b2b
221 TopicsWelcome to the Azure Active Directory B2B Collaboration Community!
The Azure Active Directory B2B Collaboration Community is a place we've built for all of you. You can learn more about the capabilities, discuss your work with Azure AD B2B collaboration, and connect with experts that build and use Azure Active Directory B2B Collaboration. Our community is a great place for engagements with us and connecting with other customers like you. Get your questions answered, give us feedback, make your favorite feature requests. Help us shape the future of the product. We are listening! Azure AD B2B collaboration capabilities enable IT Pros and Information Workers to work closely with users in any other organization on the planet. They can provide access to documents, resources and applications, while maintaining complete control over their internal data. Developers can use the Azure AD business-to-business APIs to write applications that bring two organizations together in a secure way that appears seamless to Information Workers and is intuitive for them to navigate. So, jump in! We look forward to getting to know you! Sarat Subramaniam and Mary Lynch Thanks, Sarat5.1KViews10likes6CommentsDetailed video overview of Azure Active Directory B2B collaboration
Lead engineer for Microsoft Identity Services Sarat Subramaniam, goes over Azure Active Directory B2B collaboration, which as of 4/12/ 17 is now generally available. If you are unfamiliar with Azure AD B2B: It is service that simplifies the secure sharing of your Apps and services with your external business partners and colleagues. It allows users to easily share common Apps and services to collaborate with their peers and IT to add and manage these external users without having to add them to the corporate directory or requiring partners to have Azure Active Directory in place. Further, conditional access authorization policies - including Multi-factor authentication enabled by Azure Active Directory keep data safe. More information can be found here: aka.ms/AddB2Busers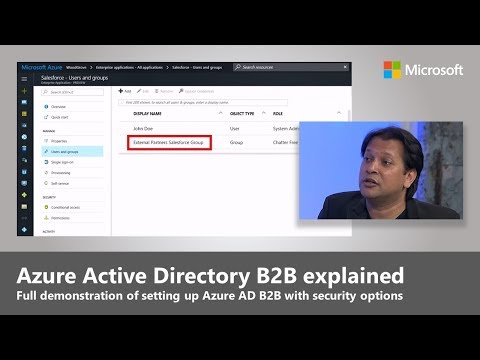 5.7KViews6likes0Comments
5.7KViews6likes0CommentsAccess across multiple companies without sending invitations
Hello, my name is Daniel and I'm the service owner for O365 at VMware. I have a use case that I need help with, you may have already seen a email from your colleague on this question. I would like to create a SharePoint site (hosted on vmware domain) that is accessable to everyone at Dell and EMC. What would be the best way to achieve this leveraging Azure B2B? Thanks2.5KViews5likes5CommentsJoin us for the #AzureAD B2B Collaboration AMA on July 6th!
We are excited to announce an Azure Active Directory B2B Collaboration AMA! Please join us on Thursday, July 6 th , 2017 from 9:00am to 10:00am PST in the Azure Active Directory B2B Collaboration Group. Add the AMA to your calendar. An AMA is a live online event similar to a “YamJam” on Yammer or an “Ask Me Anything” on Reddit. This AMA gives you the opportunity to connect with the Azure Active Directory B2B Collaboration team who will be on hand to answer your questions and listen to feedback. It this is your first AMA, please read the AMA Guide before posting. We look forward to seeing you there!3KViews5likes0CommentsAzure AD B2B: New updates make cross-business collab easy
Great updates and improvements in Azure B2B announced today: https://blogs.technet.microsoft.com/enterprisemobility/2017/02/01/azure-ad-b2b-new-updates-make-cross-business-collab-easy/ cc Salvatore Biscari VasilMichev8.7KViews5likes27CommentsMembership management by B2B guests
Hello, do you plan to add support for self user managed guest B2B memberships? So that user could also leave the organization they were invited into? Right now, I am in quite a lot of AADs from different projects and it is cluttering my Azure Portal and My Apps page... It would be great if there was a possibility to leave an organization I have been invited to on my own.1.6KViews4likes2CommentsAzure AD B2B Collaboration is Generally Available Worldwide!
I’m excited to let you know that Azure AD business-to-business (B2B) collaboration is generally available worldwide! Azure AD B2B collaboration capabilities enable any organization using Azure AD to work safely and securely with users from any other organization, small or large, with or without Azure AD, & with or without an IT organization. Organizations using Azure AD can provide their B2B partners access to documents, resources, and applications while maintaining control over corporate data. Developers can use the Azure AD B2B APIs to write applications that bring two organizations together in a secure way that is also seamless and intuitive for end users to navigate. Read more about it on the Enterprise Mobility and Security Blog.2.6KViews4likes2CommentsAttestation/account verification for Viral/Just in time users
For viral/JIT client users, we need to have validation set at regular intervals to ensure the user is still a part of their organisation. Currently, there is no validation in place for these JIT users. Are there any plans to address this and timings?2.8KViews3likes6CommentsLicensing Reports for guests in Azure B2B
Great to see Azure B2B reach GA! After reading about the licensing restrictions discussed here (https://docs.microsoft.com/en-us/azure/active-directory/active-directory-b2b-licensing), I was curious about the bullet point under "Additional licensing details" that states "There will be automatic calculation and reporting." Is there any further information about how this will work? Is there any estimate when this will be available? We are planning to utilize Azure B2B pretty heavily but need to have pretty clear visibility into how many licenes we need. We generally don't know if our partners are using Azure AD and certainly don't know what tier of functiality (Free, Basic, etc.) they use. What if a large partner organization suddenly reduces their AAD tier and we don't have enough licences to cover the level of access we are granting guests (such as MFA)?2.3KViews3likes2Comments


