- Home
- Windows Server
- Windows Server for IT Pro
- Group Policy: No BitLocker Drive Encryption Network Unlock Certificate Defined
Group Policy: No BitLocker Drive Encryption Network Unlock Certificate Defined
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 22 2022 03:12 PM - edited Nov 22 2022 03:15 PM
Current Domain Functional Level: Windows Server 2016
Test computer: Windows 10 20H2
I followed the guide here. I created a single GPO and linked it to the test OU. All of the following appear to be working as expected on the test computer:
- BitLocker was enabled on the OS drive
- Startup with TPM and PIN is working
- Recovery information is stored in AD
- RSOP shows all GPO policies applied as expected with one exception
The following observations appear to indicate one or more problems on the test computer
- User is prompted for a PIN at boot time even when the computer is connected to the local network
- HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\SystemCertificates\FVE_NKP\Certificates is empty
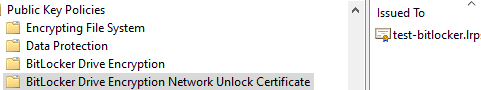
- RSOP shows "No BitLocker Drive Encryption Network Unlock Certificate has been defined in any group or local policy that was evaluated to produce this resultant set of policy." in Computer Settings\Windows Settings\Security Settings\Public Key Policies\BitLocker Drive Encryption Network Unlock Certificate.
Why is this setting missing while every other setting in the GPO appears to be applying correctly? I have confirmed multiple times that this setting points to a valid certificate on the WDS server (screen cap follows).
- Labels:
-
Active Directory
-
Networking
-
Windows Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 29 2022 11:09 AM