Howdy folks,
Many of you know that unfortunately, all it takes is one weak password for a hacker to get access to your corporate resources. Hackers can often guess passwords because regular users are pretty predictable. Regular users create easy to remember passwords, and they reuse the same passwords or closely related ones over and over again. Hackers use brute force techniques like password spray attacks to discover and compromise accounts with common passwords, an attack pattern we told you about back in March .
So today I'm really excited to announce the public preview of Azure AD Password Protection and Smart Lockout. Azure AD Password Protection helps you eliminate easily guessed passwords from your environment, which can dramatically lower the risk of being compromised by a password spray attack. Specifically, these features let you:
-
Protect accounts in Azure AD and Windows Server Active Directory by preventing users from using passwords from a list of more than 500 of the most commonly used passwords, plus over 1 million character substitution variations of those passwords.
-
Manage Azure AD Password Protection for Azure AD and on-premises Windows Server Active Directory from a unified admin experience in the Azure Active Directory portal.
-
Customize your Azure AD smart lockout settings and specify a list of additional company specific passwords to block.
Why you need Azure AD Password Protection
Banned passwords
Most users think if they have chosen a password that meets a complexity requirement, something like P@$$w0rd1!, they're safe, which is exactly wrong. Attackers know how users create passwords, and there are three general rules to be aware of.- They know to account for character substitutions like "$" for "s". "P@$$w0rd" isn't fooling anyone.
- They also that if there are complexity rules, most people will apply them in the same way: by starting a word with a capital letter and ending the password with a digit or punctuation. (Because of this we've been recommending doing away with complexity rules , and the latest NIST recommendations agree .)
- They know that requiring users to change their passwords periodically leads to other predictable patterns. For instance, if users have to change their password every quarter, they frequently pick passwords based on sports teams, months or seasons and combine them with the current year.
Smart Lockout
Smart lockout is our lockout system that uses cloud intelligence to lock out bad actors who are trying to guess your users' passwords. That intelligence can recognize sign-ins coming from valid users and treats those differently than ones that attackers and other unknown sources. This means smart lockout can lock out the attackers while letting your users continue to access their accounts and be productive. Smart lockout is always on for all Azure AD customers with default settings that offer the right mix of security and usability, but you can also customize those settings with the right values for your environment. With banned passwords and smart lockout together, Azure AD password protection ensures your users have hard to guess passwords and bad guys don't get enough guesses to break in. Please note: Azure AD Smart Lockout is included in all versions of Azure AD (including those versions in Office365).Get started in three simple steps
By default, all Azure AD password set and reset operations for Azure AD Premium users are configured to use Azure AD password protection. To configure a custom list of banned password strings for your organization and to configure Azure AD password protection for Windows Server Active Directory, follow the below simple steps:Configure the password protection for your tenant
Go to Azure AD Active Directory > Security > Authentication Methods.
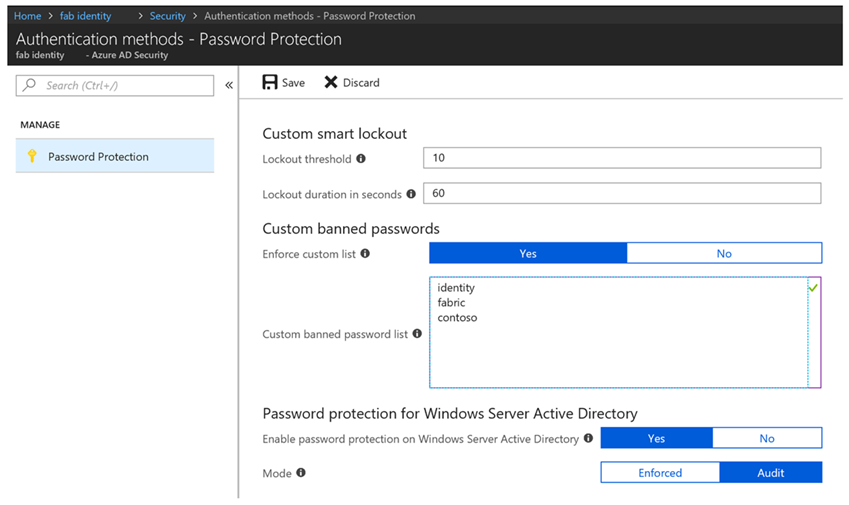
Customize your settings
- Set your custom smart lockout threshold (number of failures until the first lockout) and duration (how long the lockout period lasts)
- Enter the banned password strings for your organization in the textbox provided (one string per line) and turn on enforcement of your custom list
- Extend banned password protection to Windows Server Active Directory by enabling password protection in Active Directory. Start with the audit mode, which gives you the opportunity to evaluate the current state in your organization. Once an action plan is finalized, flip the mode to Enforced to start protecting users by preventing any weak passwords being used.
Install the Azure AD password protection proxy and domain controller agents in your on-premises environment.
Download the agents from the download center and use the instructions in the password protection deployment guide . Both the domain controller agent and the proxy agent support silent installation which can be leveraged using various deployment mechanisms like SCCM.
That's it! You're now configured to use Azure AD password protection across Azure AD and on-premises. Take a read through our detailed documentation to learn more about this functionality. As always, we're eager to hear from you! Still have more questions for us? Email aadppfeedback@microsoft.com or join us at the Ask Me Anything Session for Azure AD password protection. We look forward to hearing your feedback! Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division Microsoft
Microsoft