We deal with application and service issues on a daily basis. Normally the problems relate to applications not performing as expected, hanging or crashing. However, every so often someone will ask us what network port a service is using. Unless we are talking about one of the well known services such as SMTP, FTP, HTTP, RDP, LDAP, basic RPC etc, the ports being used are potentially subject to change. That does make life a little more challenging – but it’s nothing that we can’t figure out using some simple tools.
When considering network port numbers, the numbers are divided into three ranges: the Well Known ports, the Registered ports and the Dynamic (Private) ports. The Internet Assigned Numbers Authority (IANA) is responsible for the global coordination of the port assignments. The Well Known port range is from 0 – 1023, Registered ports run from 1024 – 49151, and the Dynamic ports run from 49152 – 65535.
So how do we determine the port that a service is using? Without using Network Monitor, Wireshark or a similar utility, there are a couple of very handy utilities provided with the operating system that we can use – NETSTAT.EXE and TASKLIST.EXE. Most administrators are familiar with NETSTAT.EXE already, but for those who are not, you can use NETSTAT.EXE to identify what ports are being used by a particular process. The syntax that we will be using for NETSTAT.EXE is as follows: netstat.exe –a –n –o . The switches we are using provide the following:
- -a: listing of all connections and listening ports
- -n: display address and port numbers in numerical form
- -o: display the owning PID associated with each connection
When the command is run, you will see output similar to what is below. Something to keep in mind is that in the Proto column, the protocol may be TCP or UDP.
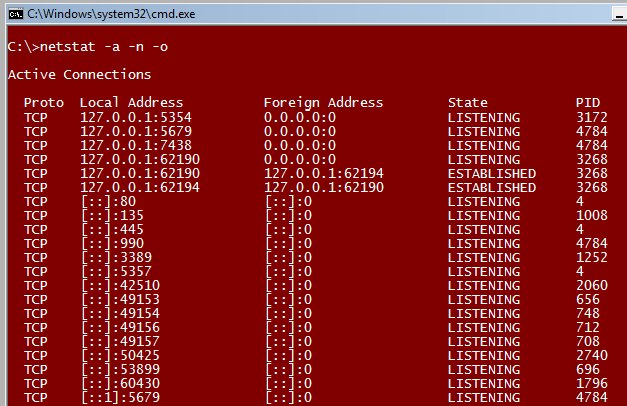
If there is a specific port in use that we want to examine, we need the PID of the owning process, and TASKLIST.EXE. Turning our attention to TASKLIST.EXE, we covered some of the functionality in our post, Getting Started with SVCHOST.EXE Troubleshooting . The command that we use to dump out all of the processes and their PID’s is simply tasklist.exe . When I run this command, this is what the output looks like:

So, looking at the output from these two utilities, I can take the port number, and then map the PID to a specific process. If the process that you are looking at is an instance of SVCHOST.EXE – let’s use PID 4784 as our example, then you will need to use slightly different switches for TASKLIST.EXE as shown below:

And thus I can tell exactly what services are running in that instance of SVCHOST.EXE.
And with that, we’ve reached the end of our post. Until next time …
Additional Resources:
- IANA Port Assignments
- Microsoft KB Article 832017: Service Overview and Network Port Requirements for the Windows Server system
- Microsoft KB Article 319553: How to restrict FRS (File Replication Service) replication traffic to a specific static port
- Microsoft KB Article 224196: Restricting Active Directory replication traffic and client RPC traffic to a specific port
| Share this post : |

|

|

|

|

|
 Microsoft
Microsoft