Hi folks, Mark Ghazai here once again with a quick tidbit on tweaking the WMI Provider Service (WMIPRVSE.EXE). We’ve been getting some calls recently about the performance of this service and some failures that customers have been experiencing – in particular “Out of Memory” errors when certain WMI-related tasks are running. We’ve talked about various memory management issues in previous posts, but the WMI Provider Service has some interesting quotas that administrators should be aware of. So, as the saying goes … tally ho!
Within the WMI System Classes there is a configuration class for host provider processes. The name of this class is _ProviderHostQuotaConfiguration. This class allows limits to be set on host process usage of system resources. The different properties available are:
- ThreadsPerHost: Defines the number of threads owned by any one host
- HandlesPerHost: Defines the number of kernel object handles each host may have
- ProcessLimitAllHosts: Defines the total number of host processes that can be executing concurrently
- MemoryPerHost: Defines the amount of private memory that can be held by each host
- MemoryAllHosts: Defines the combined amount of private memory (in bytes) that can be held by all hosts
When the WMI Provider service reaches its quota limit, WMI queries that are being handled by that instance of WMIPRVSE.EXE will most likely fail. However, there are applications like System Center that may require more memory or handles for the process. These quotas are configurable, however – do not modify these quotas for the sake of modifying them ! If the WMIPRVSE.EXE process is actually leaking handles or memory, modifying the quota will only delay the issue from occurring, not eliminate it. In instances such as these, normal leak troubleshooting must be performed to identify the root cause.
That having been said, if you are in a situation where there is a need to modify these values, you can do so using the steps below:
- Go to Start--> run and type wbemtest.exe
- Click Connect on the Windows Management Instrumentation Tester
- In the namespace text box just enter "root" (without quotes)
-
Click Connect
Note: you aren’t connecting to CimV2 or any other namespaces. It’s ROOT
-
Click "Enum Instances…"
-
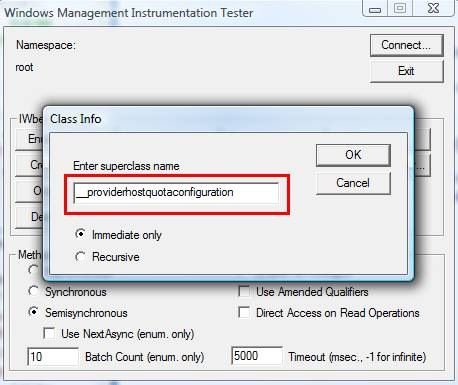
In the Class Info dialog box enter Superclass Name as "__ProviderHostQuotaConfiguration" (without quotes) and press OK.
-
A query Result window will come up. In this windows now double click "__ProviderHostQuotaConfiguration=@"
- An Object Editor windows will come up now
-
Under properties find the property "MemoryPerHost" or any other ones you need to modify and double click it
<In the case of modifying the memory quota;>
- Change the value to 512 MB which is 536870912
- Click Save Property
- Click Save Object in the Object Editor window
- Close the other windows now and exit WMI Tester
- Restart the machine.
A quick note here - on Windows XP and Windows Server 2003 systems, the memory quota per host is 128MB. For Windows Vista and Windows Server 2008 systems the memory quota per host is 512MB. The rest of quotas are all the same. And, with that, it’s time to bring this post to a close. Take care!
Additional Resources:
- Mark Ghazai
| Share this post : |

|

|

|

|

|
 Microsoft
Microsoft