Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Windows
- Windows Blog Archive
- The Case of the Father-in-Law’s Scareware
The Case of the Father-in-Law’s Scareware
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Jun 27 2019 12:31 AM
10.2K
Views
Jun 27 2019
12:31 AM
Jun 27 2019
12:31 AM
First published on TechNet on Apr 18, 2015
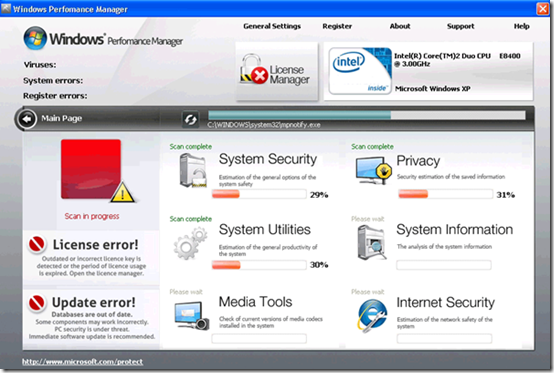
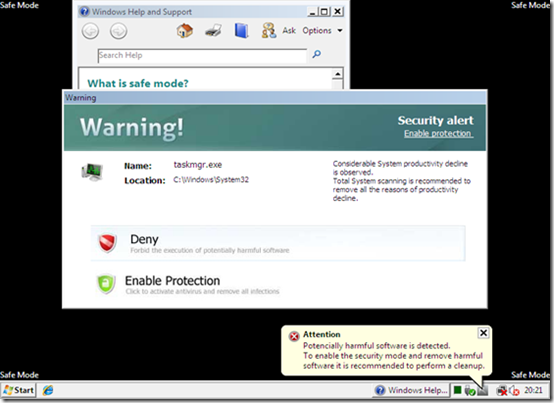
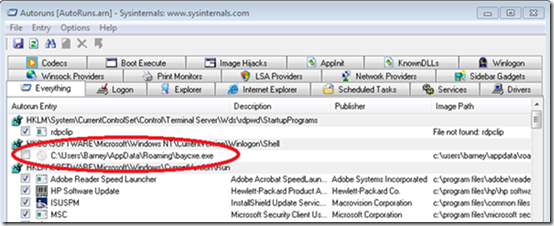
We all know people, friends and family, that have fallen for the “your system is infected, press here to get protected” scams that are becoming even more common since I first wrote about them in my The Antispyware Conspiracy blog post in 2005.
1 Comment