Happy New Year!!! One of my colleagues had shared with me some detailed information on how Active Directory (AD) integration works (in particular how the service connection points (SCP) are created) and I thought it would be a good blog post for this week. For those of you who have never heard about AD integration in OpsMgr it is the ability for an OpsMgr agent to query active directory and know which management server it needs to report to. AD integration is useful to those customers that have larger deployment of over a thousand agents and helps reduce manageability costs. By using AD integration you can specify the primary and secondary management server for agents something that cannot be done using push agent where users can only specify the primary management server.
The MOMADAdmin.exe command line tool does the following:
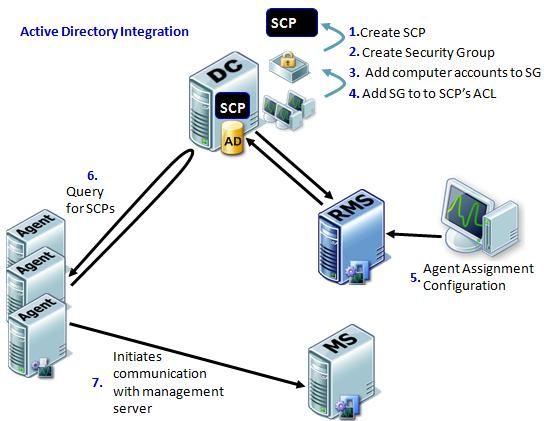
1. Creates a top level OperationsManager container in AD under the root of the specified Domain
Under that container, it creates a management group container - whose name consists of the management group name and the suffix “Root”
2. Adds Machine account of the root management server to the MOM Admin security group.
3. Adds the MOM Admin security group to the container's ACL with WriteChild access (only with rights to create Security Groups and SCP objects, but not other objects like user account) This allows members of the MOM administrator role and the root management server to manage the objects within the container. Only Domain Administrators have the right to remove or change the OperationsManager and
<ManagementGroup>
container.
Note:
The MOM Admin Security Group is the sole member of the MOM Administrator role. The MOM AD based agent assignment feature requires it to be a domain global group or universal group.
It can be modified in the MOM Console -> Administration space -> User Role node, right click the MOM Administrator role and select properties.
4. Creates 2 default SCPs and one security group within the container: One is HealthServiceSCP which represents the management group and the other one is SDKServiceSCP which represents the root management server. The security group is ACL’d to the HealthServiceSCP with Read permission – its membership will control which computers can “read” (hence discover) a particular management group, represented by the HealthServiceSCP. The Root MS and MOM Admins are given full rights over these objects.
Note: SCP (service connection point) is an AD object for publishing information that client applications can use to bind to a service. MOM AD based agent assignment feature uses SCP to represent a MOM server and contain connection info to that server. MOM Agents can automatically discover MOM servers by querying for SCPs.
Note: If the root management server or the MOM admin security group is changed, the domain administrator will have to either 1) modify the container ACL, HealthServiceSCP and SDKServiceSCP manually to reflect the change, or 2) delete the container, re-run MOMADAdmin.exe with updated parameter
After MOMADAdmin.exe is successfully ran by the Domain Administrator, a MOM Administrator can use the MOM Console to specify the set of agents he/she wanted to assign to particular management server, in the form of a LDAP query (the query should return a list of computer accounts).
The Ldap query and the other assignment settings are captured as configuration in a MOM rule.
When the rule runs the first time, it will create a SCP (if not already exist) in AD for the management server and domain specified in its configuration.
The SCP name is the management server netbios name with the suffix “_SCP”.
The rule also creates 2 security groups with the name of the management server netbios name, the first one with the suffix “_PrimarySG<random number>” and the second one “_SecondarySG<random number>”
The first security group is ACL’d to the management server SCP with Read and Read permission rights.
This SG contains the machine account of agents that report to the management server as the primary server.
It is also added as a member to the HealthServiceSCP’s security group.
The second security group is ACL’d to the management server SCP with Read right only.
This security group contains the machine account of agents that would failover to the management server (hence ‘secondary’) in the event that the Primary server is not responsive.
The rule would run every hour to update the members of the security groups (acl’d to the management server SCP) with results from the specified LDAP query (machine accounts of agents that the administrator intend to assign to the server)
When an agent starts up (& periodically thereafter) to check AD for connection info using its machine account, it would look in each Management Group container to find the management server (represented by the SCP) that it should connect to. It will only see SCPs where its machine account is a member of the associated security group.
Satya Vel