First published on TECHNET on Apr 28, 2016
A few months ago, Azure Automation team released a new runbook authoring experience through Azure Automation ISE Add-on. https://azure.microsoft.com/en-in/blog/announcing-azure-automation-powershell-ise-add-on/ , Joe outlined the customer behaviors that inspired them to build the add-on.
This new tool is build based on the following observation:
1. Most of our customers use the PowerShell ISE when writing PowerShell.
2. They even use the PowerShell ISE writing runbooks, copy/pasting back and forth with the portal or importing/exporting with the PowerShell cmdlets.
We realized that these observations hold true for our System Center Service Management Automation (SMA) customers as well. We saw an opportunity to provide our customers with a seamless runbook authoring experience by providing a similar add-on for SMA. Today, we are happy to announce the release of Service Management Automation ISE Add-on to go with release of https://blogs.technet.microsoft.com/systemcenter/2016/04/27/whats-new-in-system-center-2016-technical-preview-5/ .
With this release, we provide our users with an authoring experience better suited to their needs and also consistent with our cloud automation offerings.
This blog will walk you through the installation and usage of Service Management Automation ISE Add-on.
If you would instead like to watch a video demonstrating the new ISE Add-on, here it is:
You can install the ISE Add-on module from https://www.powershellgallery.com/packages/SMAAuthoringToolkit/1.0 with:
> Install-Module SMAAuthoringToolkit -Scope CurrentUser
Then, if you want the PowerShell ISE to always automatically load the add-on, run:
> Install-SMAIseAddOn
Otherwise, whenever you want to load the add-on, just run the following in the PowerShell ISE:
> Import-Module SMAAuthoringToolkit
When you load the add-on, it will appear on the right-hand side of the PowerShell ISE.

You can use it to view, edit and test the runbooks in your SMA Account; also to manage your Automation assets.
The Configuration tab (pictured above) is where you sign in to SMA. Its runbooks and assets are downloaded to the workspace folder specified at the top of this tab. For security, secret asset values (like encrypted variables and credential passwords) are not downloaded, but can be manually entered and securely stored locally – more details on that later.
You will be able to connect to your SMA Web Server in the configuration, you can either use Windows/Basic authentication mechanism.
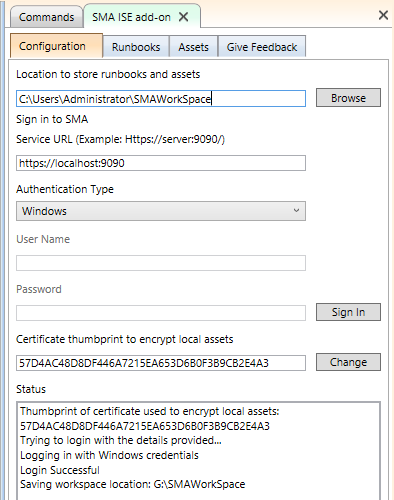
As soon as you are connected, you are able to manually download existing runbooks and assets or upload locally created runbooks and assets.

When you install the add-on, it also provides cmdlets that emulate the standard Automation activities like Get-AutomationVariable, Get-AutomationPSCredential, Set-AutomationVariable, etc. Because your assets get downloaded when you sign in, you can test your runbooks on your local machine before you test them in SMA!
Once you’ve done some local testing, you can also test your runbook in SMA without leaving the ISE experience. For example:

The new window shows information about a test job running in SMA for this runbook. It’s the PowerShell ISE’s equivalent to the Test Job pane in Windows Azure Pack (WAP) Automation.
As mentioned above, secrets will still need to be entered manually. You can enter these values from the Assets Tab. Assets missing values, such as an encrypted variable or a credential’s password field, will be highlighted in orange, as shown below.
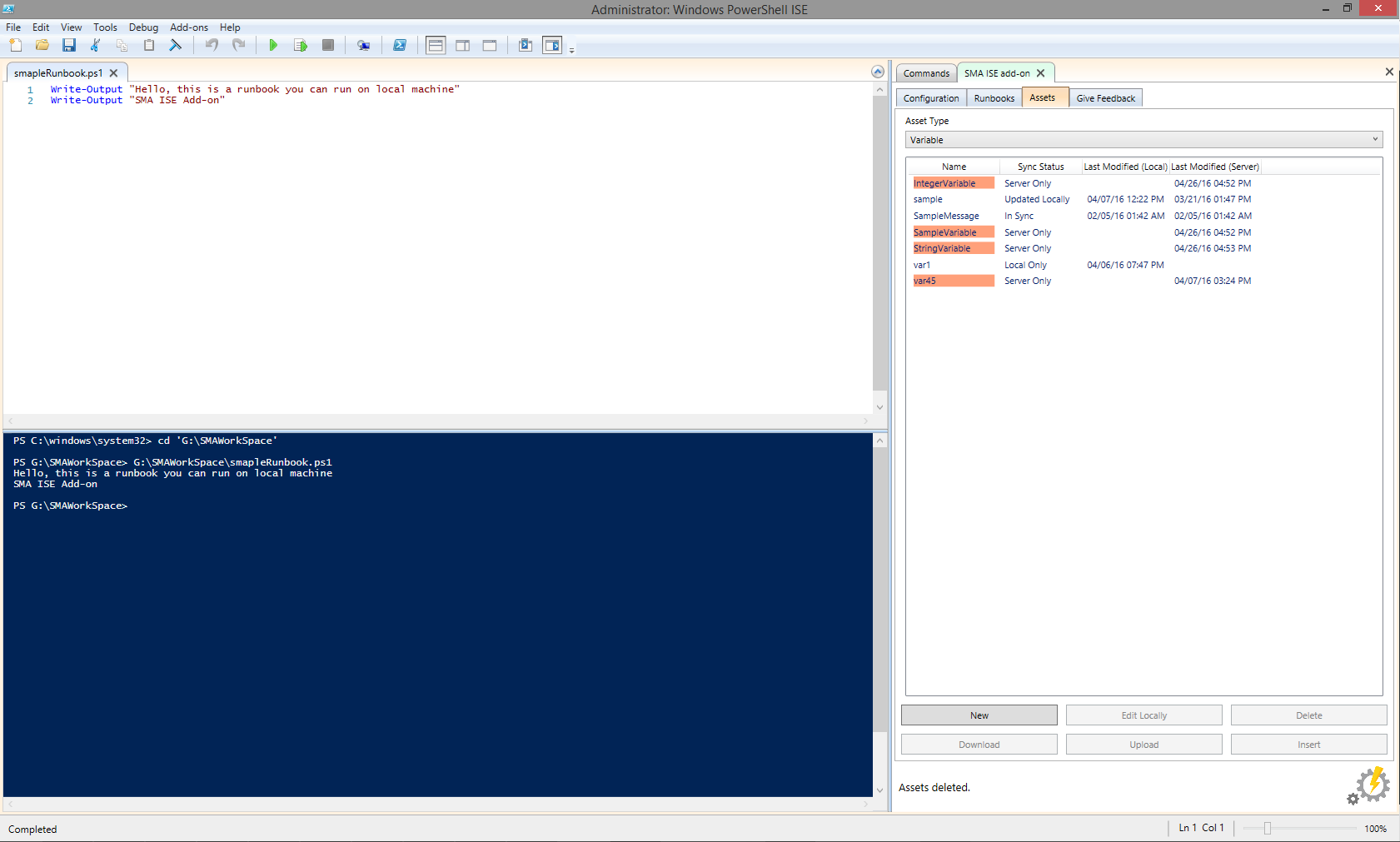
In this case, these variables are highlighted because their value fields have not been set. Double-clicking a variable asset allows you to enter the desired value.
Asset values are stored on disk in your workspace in two files – one for non-encrypted assets and the other for encrypted assets. Encrypted asset values use a certificate, whose thumbprint is shown on the Configuration tab for encryption and decryption at runtime. You can also select your own certificate to use for encryption.
Let us know what you think! If you discover any issues or have any feature requests you can submit feedback using the Feedback tab in the ISE add-on itself.
Note: The SMAAuthoringToolkit cmdlets are currently incompatible with AzureAutomationAuthoringToolKit due to name conflicts.
A few months ago, Azure Automation team released a new runbook authoring experience through Azure Automation ISE Add-on. https://azure.microsoft.com/en-in/blog/announcing-azure-automation-powershell-ise-add-on/ , Joe outlined the customer behaviors that inspired them to build the add-on.
This new tool is build based on the following observation:
1. Most of our customers use the PowerShell ISE when writing PowerShell.
2. They even use the PowerShell ISE writing runbooks, copy/pasting back and forth with the portal or importing/exporting with the PowerShell cmdlets.
We realized that these observations hold true for our System Center Service Management Automation (SMA) customers as well. We saw an opportunity to provide our customers with a seamless runbook authoring experience by providing a similar add-on for SMA. Today, we are happy to announce the release of Service Management Automation ISE Add-on to go with release of https://blogs.technet.microsoft.com/systemcenter/2016/04/27/whats-new-in-system-center-2016-technical-preview-5/ .
With this release, we provide our users with an authoring experience better suited to their needs and also consistent with our cloud automation offerings.
This blog will walk you through the installation and usage of Service Management Automation ISE Add-on.
If you would instead like to watch a video demonstrating the new ISE Add-on, here it is:
Installation
You can install the ISE Add-on module from https://www.powershellgallery.com/packages/SMAAuthoringToolkit/1.0 with:
> Install-Module SMAAuthoringToolkit -Scope CurrentUser
Then, if you want the PowerShell ISE to always automatically load the add-on, run:
> Install-SMAIseAddOn
Otherwise, whenever you want to load the add-on, just run the following in the PowerShell ISE:
> Import-Module SMAAuthoringToolkit
Overview
When you load the add-on, it will appear on the right-hand side of the PowerShell ISE.

You can use it to view, edit and test the runbooks in your SMA Account; also to manage your Automation assets.
The Configuration tab (pictured above) is where you sign in to SMA. Its runbooks and assets are downloaded to the workspace folder specified at the top of this tab. For security, secret asset values (like encrypted variables and credential passwords) are not downloaded, but can be manually entered and securely stored locally – more details on that later.
How does it work?
You will be able to connect to your SMA Web Server in the configuration, you can either use Windows/Basic authentication mechanism.

As soon as you are connected, you are able to manually download existing runbooks and assets or upload locally created runbooks and assets.

Test runbooks on your local machine
When you install the add-on, it also provides cmdlets that emulate the standard Automation activities like Get-AutomationVariable, Get-AutomationPSCredential, Set-AutomationVariable, etc. Because your assets get downloaded when you sign in, you can test your runbooks on your local machine before you test them in SMA!
Once you’ve done some local testing, you can also test your runbook in SMA without leaving the ISE experience. For example:

The new window shows information about a test job running in SMA for this runbook. It’s the PowerShell ISE’s equivalent to the Test Job pane in Windows Azure Pack (WAP) Automation.
Using encrypted assets
As mentioned above, secrets will still need to be entered manually. You can enter these values from the Assets Tab. Assets missing values, such as an encrypted variable or a credential’s password field, will be highlighted in orange, as shown below.

In this case, these variables are highlighted because their value fields have not been set. Double-clicking a variable asset allows you to enter the desired value.
Asset values are stored on disk in your workspace in two files – one for non-encrypted assets and the other for encrypted assets. Encrypted asset values use a certificate, whose thumbprint is shown on the Configuration tab for encryption and decryption at runtime. You can also select your own certificate to use for encryption.
Feedback
Let us know what you think! If you discover any issues or have any feature requests you can submit feedback using the Feedback tab in the ISE add-on itself.
Note: The SMAAuthoringToolkit cmdlets are currently incompatible with AzureAutomationAuthoringToolKit due to name conflicts.
Updated Mar 11, 2019
Version 4.0System-Center-Team
Former Employee
Joined February 15, 2019
System Center Blog
Follow this blog board to get notified when there's new activity