~ Maha Ibrahim | Senior Software Engineer

Updated 12/1/2015 : A newer version of this article for Tech Preview 4 is available here .
=====
Host Guardian Service (HGS) is a main component for configuring guarded hosts and running shielded VMs in Windows Server and System Center Virtual Machine Manager Technical Preview 3.
In this post we will demonstrate how to automate the deployment of Host Guardian Service using VMM service templates. The resulting Host Guardian Service instance can be used for your test or demo environments.
First, we will cover the relevant VMM service template configuration details, then show the steps needed to import and deploy the Host Guardian service template that can get you a virtualized HGS instance just in few clicks.
This post assumes you have some background about using VMM service templates, however if you’re interested in more details about HGS outside of the scope of this article you can refer to Windows Server TechNet articles about Guarded Fabric and Shielded VMs, or https://aka.ms/shieldedvms
Requirements
- Microsoft System Center Virtual Machine Manager – Technical Preview 3 – Download link
- Windows Server Technical Preview 3 Virtual Hard Disk Image – Download link
Host Guardian Service VMM Service Template
Now let’s start with details about how we’re configuring the Host Guardian Service using VMM service template.
There are 2 key configurations for the template:
1. Enable the Windows Server role for “Host Guardian Service” in the operating system configuration of the service template.
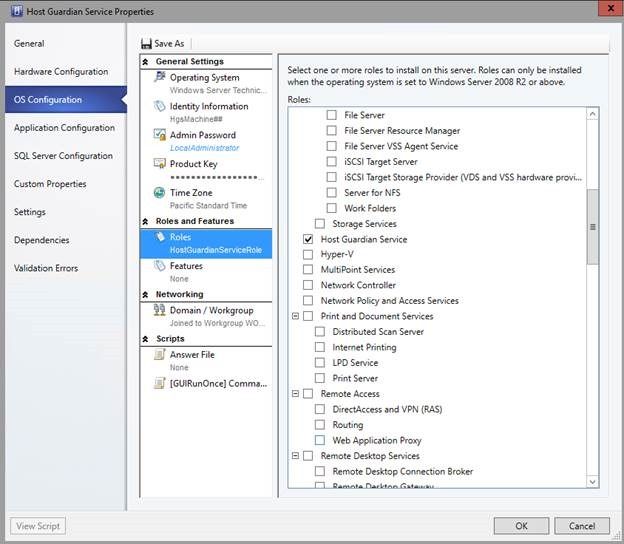
2. Run application configuration scripts to install and configure the Host Guardian service. For this purpose we are using two scripts: Install-HostGuardianService.ps1 and Configure-HostGuardianService.ps1 . To make it simple, both of the scripts are placed in a single custom resource folder named HostGuardianServiceScripts.cr .
Now let’s take a deeper look at the contents of the two scripts:
Install-HostGuardianService.ps1
[Environment]::Exit(“3011”)
In a nutshell, the script tests the pre-requisites of the machine, installs host guardian service, then exits with an exit code that allows VMM to orchestrate the machine reboot per the restart policy of the application script.

In the service template, the parameters will be passed to the script through VMM service settings:
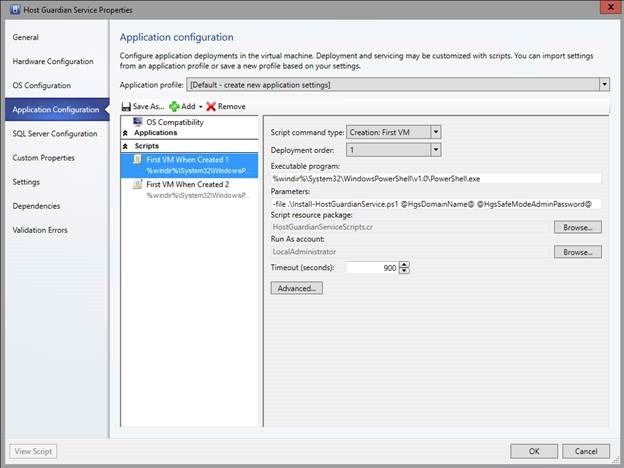
Configure-HostGuardianService.ps1
This script has a number of input parameters that enable customizations which in turn will result in the desired configuration for your HGS server, whether using AD or TPM based attestation.
For AD trust mode, the values for the parameters will control whether to configure the domain trust and DNS forwarder to the fabric domain, and whether to add the SID of the fabric AD group. Fabric hosts that are joined to this AD group are deemed guarded by HGS.
For Trusted Hardware TPM Mode, the content of HostGuardianServiceScripts.cr subfolders will determine whether and what TPM hosts and/or polices to add to the HGS server; if adding Code Integrity Policies, TPM Hosts and TPM policies is desired, then include the necessary files to your library in the respective subfolders prior to the deployment of the service configuration.
Below is the folder structure for the HostGuardianServiceScript.cr custom resource.

For details about how to create the files for TPM hosts, Code Integrity Policy or TPM policy, refer to the Windows Server TechNet articles about Guarded Fabric and Shielded VMs or https://aka.ms/shieldedvms
In the service template, the parameters will be passed to the script through VMM service settings:

The full parameters field is shown below for reference.
-file .\Configure-HostGuardianService.ps1 @HgsServiceName@ @HgsDomainName@ @AdMode@ @FabricAdGroupSid@ @FabricDnsIpAddress@ @FabricDomainName@ @FabricDomainUser@ @FabricDomainPassword@
Note that the order of the service settings must match the script parameters.
Now we should have a good understanding of the configuration required to orchestrate the deployment of the virtualized Host Guardian Service using VMM service template. The next section will cover how to download the service template, import it and deploy the Host Guardian Service.
Install Steps
1. Download compressed file from this download link .
2. Extract the custom resource folder HostGuardianServiceScripts.cr and copy it to your VMM library, then refresh the library share.
3. Create a Run As Account to be used for the Local Administrator of the HGS machine.
4. Verify that the Windows Server Technical Preview 3 VHD is imported in the VMM library.
5. Import the XML file as a VMM service template and map the resources according to resources included in the library.
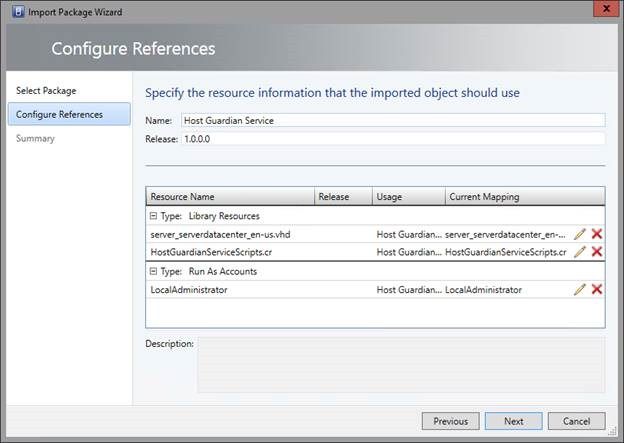
6. If needed, open the computer tier properties and update the product key in the operating system configuration.
7. Save and configure deployment.
8. Specify the VM Network to be used.

9. Specify the service settings per the configuration of the desired deployment. This is an example for settings needed to deploy a full-fledged AD mode HGS server:

And here’s an example for settings needed to deploy a TPM Mode HGS server. Host, code integrity and CI policies will be added to the HGS server only if the respective files are included in the subfolders as referred to earlier. If the files do not exist at the time of deployment then extra configuration steps will be needed before the HGS server can be used for host guarding.

Now that the service configuration is ready to be deployed, click Deploy Service and wait for the job to complete. Once complete, you’ll have a Host Guardian Service instance up and running!
Troubleshooting Tips
- When specifying the values for the service settings, choose different names for the HgsServiceName and the ComputerName of the VM.
- If for any reason the service deployment failed, retrying the failed service deployment job may not work since the virtual machine would have joined a different domain than what VMM expects. Investigate the cause of the failure and remediate in a new service deployment job.
- For failure analysis, the script output and error logs will be located inside the guest operating system under the C:\ drive (e.g. C:\hgs_install.* & C:\hgs_configure.*).
After the service deployment completes, before you can use the resulting instance for host guarding, extra configurations may be needed:
- For Both TPM and AD setup: Configure name resolution between the existing fabric domain and the new HGS domain.
- For AD Setup: Verify that the hosts where guarding is desired are added to the AD group whose SID is added to the HGS.
Here’s an example for the Attestation and Key Protection servers URLs per the service setting example values used in this article:
AttestationServerUrl: http://MyHgsService.ReleCloud.com/Attestation
KeyProtectionServerURl: http://MyHgsService.ReleCloud.com/KeyProtection
Happy host guarding and virtual machine shielding!
Maha Ibrahim | Senior Software Engineer | Microsoft
Get the latest System Center news on Facebook and Twitter :


System Center All Up: http://blogs.technet.com/b/systemcenter/
Configuration Manager Support Team blog:
http://blogs.technet.com/configurationmgr/
Data Protection Manager Team blog:
http://blogs.technet.com/dpm/
Orchestrator Support Team blog:
http://blogs.technet.com/b/orchestrator/
Operations Manager Team blog:
http://blogs.technet.com/momteam/
Service Manager Team blog:
http://blogs.technet.com/b/servicemanager
Virtual Machine Manager Team blog:
http://blogs.technet.com/scvmm
WSUS Support Team blog: http://blogs.technet.com/sus/
The RMS blog: http://blogs.technet.com/b/rms/
App-V Team blog: http://blogs.technet.com/appv/
MED-V Team blog: http://blogs.technet.com/medv/
Server App-V Team blog: http://blogs.technet.com/b/serverappv
The Surface Team blog: http://blogs.technet.com/b/surface/
The Application Proxy blog: http://blogs.technet.com/b/applicationproxyblog/
The Forefront Endpoint Protection blog :
http://blogs.technet.com/b/clientsecurity/
The Forefront Identity Manager blog :
http://blogs.msdn.com/b/ms-identity-support/
The Forefront TMG blog:
http://blogs.technet.com/b/isablog/
The Forefront UAG blog:
http://blogs.technet.com/b/edgeaccessblog/