First published on TECHNET on Sep 18, 2017
Author: Zack Campbell , Service Engineer, Microsoft Skype for Business Online Services
I was recently engaged by the owner of multiple high-visibility and business-critical UCMA Trusted Applications, requesting my assistance to replace the Trusted App Computers associated to a large list of Endpoints. I didn't know the full backstory, but apparently their servers were VMs, hosted to Hyper-V hosts which they were under a hard deadline to vacate. Anyway, the initial request seemed simple enough, but as I dug in, I quickly realized that there was no direct relationship between their Trusted App Computers and their Endpoints.
I also realized (not so quickly) that there was not a one-to-one relationship between those objects. I knew I had the data I needed to figure out those relationships, but -- being the
smart
lazy SfB admin that I am -- I started by digging around the Internet for some background, only to come up empty.
Anyone who has worked much with UCMA Trusted Apps probably already understands this, but I was just then realizing that I had some quick scrambling to do to ensure I didn't cause an outage for their Trusted Apps… while implementing a change to prevent a different outage. That's never a good day.
Up to this point, I had been able to slide by on most UCMA change work, without having a super clear understanding of the relationships between UCMA Trusted Apps and their respective Pool, Endpoint, and Computer objects.
This time, however, while the app owner was somewhat confident of the App Pools and Apps associated with his various Computers and Endpoints, he wasn't totally certain, nor was he sure which ones corresponded with which. Unfortunately, that's not good enough, when doing change work… so it fell to me to really figure this whole model out, so I could give the App owner solid consulting advice, make the right changes at the right times, and help him avoid any impact.
Not having found any help on the Internet, I got to work, picking through my company SfB deployment's various existing Trusted Apps, Computers, App Pools and Endpoints, looking closely at the object properties that tied them together. I made several interesting observations, which I was later able to stitch together into a fairly simple model:
These observations were helpful, but not the kind of thing that's easy to remember or use. More to the point, I prefer pictures, so I made one. Nice, huh? This is a lot easier…
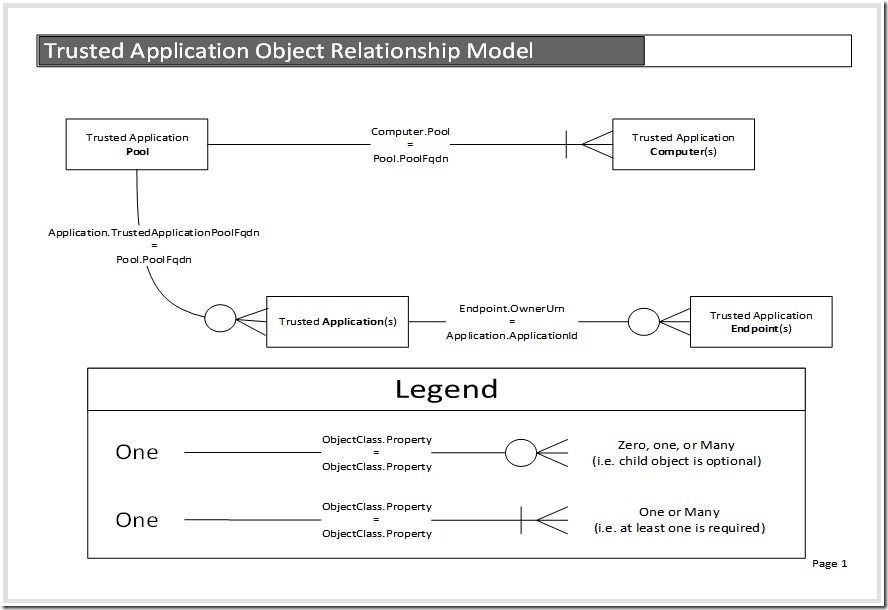
With this model in hand, it was a simple matter to build the list of all Trusted App Pools and respective Trusted App Computers associated with the Endpoints my customer provided, and it helped them as well, to see/understand how their objects related to each other.
My hope is that it'll be useful to other SfB admins, as well. Don't hesitate to provide comments and feedback. I'll be happy to update this, as needed.
Author: Zack Campbell , Service Engineer, Microsoft Skype for Business Online Services
I was recently engaged by the owner of multiple high-visibility and business-critical UCMA Trusted Applications, requesting my assistance to replace the Trusted App Computers associated to a large list of Endpoints. I didn't know the full backstory, but apparently their servers were VMs, hosted to Hyper-V hosts which they were under a hard deadline to vacate. Anyway, the initial request seemed simple enough, but as I dug in, I quickly realized that there was no direct relationship between their Trusted App Computers and their Endpoints.
I also realized (not so quickly) that there was not a one-to-one relationship between those objects. I knew I had the data I needed to figure out those relationships, but -- being the
Anyone who has worked much with UCMA Trusted Apps probably already understands this, but I was just then realizing that I had some quick scrambling to do to ensure I didn't cause an outage for their Trusted Apps… while implementing a change to prevent a different outage. That's never a good day.
You're really going to make me work at this, huh?
Up to this point, I had been able to slide by on most UCMA change work, without having a super clear understanding of the relationships between UCMA Trusted Apps and their respective Pool, Endpoint, and Computer objects.
This time, however, while the app owner was somewhat confident of the App Pools and Apps associated with his various Computers and Endpoints, he wasn't totally certain, nor was he sure which ones corresponded with which. Unfortunately, that's not good enough, when doing change work… so it fell to me to really figure this whole model out, so I could give the App owner solid consulting advice, make the right changes at the right times, and help him avoid any impact.
Getting all the pieces together
Not having found any help on the Internet, I got to work, picking through my company SfB deployment's various existing Trusted Apps, Computers, App Pools and Endpoints, looking closely at the object properties that tied them together. I made several interesting observations, which I was later able to stitch together into a fairly simple model:
-
Trusted App
Computers
are directly related to single Trusted App
Pool
.
- The property that ties them together is the App Pool 's PoolFqdn (corresponding to the Trusted App Computers ' Pool property).
- A Trusted App Pool requires at least one Trusted App Computer .
-
Trusted
Apps
are directly related to a single Trusted App
Pool
.
- The property that ties them together is the App Pool 's PoolFqdn (corresponding to the Trusted Apps ' TrustedApplicationPoolFqdn property).
- The App Pool has a corresponding Applications multivalued property, populated by all the Trusted Apps associated with it (via their ApplicationId properties).
- A Trusted App Pool doesn't have to have any Trusted Apps associated with it (it doesn't do much good without them, but there's nothing preventing this from happening).
-
Trusted App
Endpoints
are directly related to a single Trusted
App
.
- The property that ties them together is the Trusted App 's ApplicationId (corresponding to the Trusted Apps Endpoints ' OwnerUrn property).
- A Trusted App doesn't have to have any Trusted App Endpoints associated with it.
Ok, that's not so bad
These observations were helpful, but not the kind of thing that's easy to remember or use. More to the point, I prefer pictures, so I made one. Nice, huh? This is a lot easier…

Application
With this model in hand, it was a simple matter to build the list of all Trusted App Pools and respective Trusted App Computers associated with the Endpoints my customer provided, and it helped them as well, to see/understand how their objects related to each other.
My hope is that it'll be useful to other SfB admins, as well. Don't hesitate to provide comments and feedback. I'll be happy to update this, as needed.
Updated May 20, 2019
Version 2.0NextHop_Team
Brass Contributor
Joined May 16, 2019
Skype for Business Blog
Follow this blog board to get notified when there's new activity