Part 3 of a 9-part
series
.
In today’s post, we tackle a common question I get from customers: “Why move to the cloud
right now
?
” Recently, however, this question has changed a bit to, “What should I move to the cloud
first
?
”
Part 3 of a 9-part
series
.
In today’s post, we tackle a common question I get from customers: “Why move to the cloud
right now
?
” Recently, however, this question has changed a bit to, “What should I move to the cloud
first
?
”
An important thing to keep in mind with either of these questions is that every organization has their own unique journey to the cloud. There are a lot of different workloads that run on Windows Server, and the reality is that these various workloads are moving to the cloud at very different rates. Web servers, e-mail and collaboration are examples of workloads moving to the cloud very quickly. I believe that management, and the management of smart devices, will be one of the next workloads to make that move to the cloud – and, when the time comes, that move will happen fast .
Using a SaaS solution is a move to the cloud, and taking this approach is a game changer because of its ability to deliver an incredible amount of value and agility without an IT pro needing to manage any of the required infrastructure.
Cloud-based device management is a particularly interesting development because it allows IT pros to manage this rapidly growing population of smart, cloud-connected devices, and manage them “ where they live .” Today’s smart phones and tablets were built to consume cloud services, and this is one of the reasons why I believe that a cloud-based management solution for them is so natural. As you contemplate your organization’s move to the cloud, I suggest that managing all of your smart devices from the cloud should be one of your top priorities.
I want to be clear, however, about the nature of this kind of management: We believe that there should be one consistent management experience across PC’s and devices.
Achieving this single management experience was a major focus of these 2012 R2 releases, and I am incredibly proud to say we have successfully engineered products which do exactly that. The R2 releases deliver this consistent end-user experience through something we call the “Company Portal.” The Company Portal is already deployed here at Microsoft, and it is what we are currently using to upgrade our entire workforce to Windows 8.1. I’ve personally used it to upgrade my desktop, laptop, and Surface – and the process could not have been easier.
In this week’s post, Paul Mayfield , the Partner Program Manager for System Center Configuration Manager/Windows Intune, and his team return to discuss in deep technical detail some of the specific scenarios our PCIT team has enabled (cloud-based management, Company Portal, etc.). Their work is a great example of the “ One Microsoft ” principle behind our company’s new reorganization . The PCIT team worked across teams and divisional boundaries to holistically address customer needs across Microsoft products.
I’m excited for all of our partners and customers to immerse themselves in this new technology and begin benefitting from R2’s new and improved features.
* * *
Last week, we discussed some of the new capabilities coming in the R2 wave of releases later this year. These new capabilities enable IT Pros to both embrace the Consumerization of IT and support the needs of their users to securely access their apps and data from any device anywhere. We have been referring to this new set of capabilities as “People Centric IT” (PCIT) because it puts the end user at the center of all that we do.
We don’t just think about these features differently, however – we’ve also engineered them differently. Engineering teams across major product lines and divisions collaborated to define these people-centric scenarios, and, together, we have executed against a common set of engineering milestones. Now, after working closely together for months, we are releasing together too.
In today’s post, we’ll examine a few examples of holistic end-to-end customer scenarios that are a result of our cross-company collaboration. Specifically, we’ll look at:
- Providing users with secure access to their files on their personal devices.
- Enabling users to provision their iOS devices for work while allowing IT Pros to restrict access to corporate resources.
- Enabling IT Pros to deliver VPN functionality to corporate and personal devices. This includes both Microsoft and 3rd party VPNs, clients, and gateways – and it also covers upcoming support for this on Windows RT.
Each of these three examples combine and maximize capabilities from across Windows, Windows Server, System Center and Windows Intune. These examples include features like Work Folders , the Web Application Proxy , Active Directory Federation Services , Unified Device Management in System Center Configuration Manager, the new Modern VPN Platform, and the Company Portal.
The diagram below articulates the major components at work in the People Centric IT pillar. It’s not necessary for each of these parts to be deployed in any given scenario. Instead IT teams can deploy just the parts needed to successfully implement the scenarios they care about. In the scenarios detailed below we’ll refer back to the technologies on this diagram.

View of major components that provide People Centric IT scenarios.
Scenario 1: Giving Users Secure Access to their Work Files on Personal Devices
This first example examines one way to enable users to access their work files on personal devices, as well as how to mitigate risks around compliance and information leakage. This example focuses on the new Work Folders feature in Windows Server 2012 R2.
Work Folders is a new file sync feature that compliments SkyDrive Pro . Where SkyDrive Pro gives users access to their SharePoint data, Work Folders provides access to files on traditional file servers. With Work Folders, users sync data to a corporate backend file server. This means you can use all of the tools for file servers with Work Folders to manage and secure this data. Windows 8.1 will include a built in Work Folders client. Also, soon after we release Windows 8.1, we will release Work Folder support for Windows 7 and iPad*.
The basic steps to enabling secure file access to personal devices are:
- Deploy a Work Folders server and configure it for your users.
- Publish Work Folders to Internet-connected devices using the Web Application Proxy, or through any reverse proxy solution.
- Provision devices to use Work Folders using System Center and Windows Intune.
Once this has been done, our services work together to secure your data:
-
Authentication
The Web Application Proxy integrates with Active Directory Federation Services (AD FS) so that you can restrict Work Folders to Workplace Joined or domain joined devices, and even require multi-factor authentication. -
Encryption
Work Folders files are stored in encrypted folders on devices. Additionally, you can use Dynamic Access Control to automatically classify and rights manage (RMS) protect sensitive documents to give extra protection against data leakage. -
Wipe
Work Folders files are rendered inaccessible from a user’s device when the user leaves the company or when the device is lost.
Combining all these capabilities allows you to provide data access to your users (who continue using their BYOD devices) while still protecting your corporate data.
With all of this in mind, here’s an example of what it looks like in action.
IT Configuration
As an IT Pro, your first step is to enable Work Folders on your file servers. This simple process is part of configuring the File Server role in Windows 2012 R2. Once complete, authorized users can manually set up Work Folders on their devices.
However, you don’t have to require users to configure themselves for Work Folders. You can use System Center Configuration Manager and Windows Intune to automatically provision devices with Work Folders settings to personal devices, and Group Policy for domain-joined machines. In the new R2 release of Config Manager, we’ve added native support for configuring Work Folder policy. You can target this policy based on a rich set of criteria. Once configured, any device that is domain joined, managed by Config Manager, or enrolled for Mobile Device Management (MDM) in Windows Intune receives Work Folder configuration as part of normal device provisioning.
Since Work Folders operates over an HTTPS-based protocol, you can now publish Work Folders to the Internet using the new Web Application Proxy (or any industry standard web publishing solution). This allows controlled access to files on Internet-connected devices, even if those devices never connect to the corporate network. The Web Application Proxy integrates with AD FS. This means you can use AD FS to restrict access devices that are Workplace Joined or domain joined. You can even require multi-factor authentication, leveraging the new plug-in model that AD FS provides in Windows Server 2012 R2.

Selecting the authentication provider for Work Folders to be AD FS. This integrates access control for Work Folders with our new Workplace Join features.
Finally, the IT pro can configure automatic classification of files using Dynamic Access Control. This can include keying in on sensitive words, phrases or regular expressions in a document (such as credit card numbers or the word “confidential”) and cause those files to be automatically classified as high impact and automatically encrypted and protected with RMS. These encryption rules help reduce information leakage of sensitive information. For example, when Joe (a hypothetical information worker) authors a sensitive customer information document on his desktop, this document synchronizes to the Work Folders share on the file server. The file server then automatically scans the document, tags it as sensitive, and applies RMS protection. The RMS protected version of the document then synchronizes back to Joe’s desktop and all other Work Folders enabled devices. This entire process is seamless to Joe so that he can continue working on the sensitive document without worrying about compliance or information leakage (e.g. if this device is lost or stolen, the sensitive data on it cannot be accessed).
Information Worker (user) Interaction
A major focus of the R2 development was to create a user experience that was simple and familiar. Part of this simplicity included making the protection and compliance automatic (i.e. not relying on users taking the necessary actions to protect corporate data).
To keep the user experience simple and familiar, we chose to present Work Folders as just another folder on the device. This allows users to access and store work data in a single place using a normal folder. The user doesn’t know that it happens to synchronize with other devices through a backend file server. In function, this is similar to how SkyDrive and SkyDrive Pro work.

Work Folders show up as a normal folder in the user’s profile on Windows.
In order to make compliance and protection automatic, we designed Work Folders so that the IT pro determines what policies are applied to what devices and what files. IT Pros manage the data using standard file server data management capabilities, thus backup, retention, classification and encryption are all handled for the end user automatically. In addition to this, Work Folder files are always synchronized to folders on the users’ devices that are separately encrypted just for this purpose. This allows the files to be wiped from the device in a secure manner if/when that is necessary.
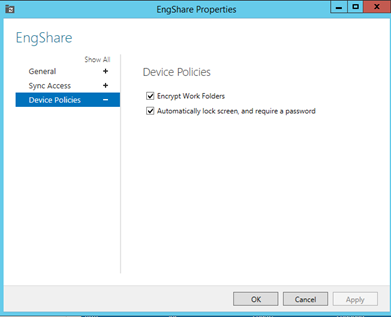
Configuring basic policy requirements for personal devices accessing Work Folders.
Back to Hypothetical Joe: Suppose Joe buys a new Surface RT and wants to access files from work. He simply has to Workplace Join his device and enroll for management. As part of enrollment, his Work Folder configuration will be automatically provisioned and his files will start to sync to an encrypted folder. Joe now has all his work files available to him. As he makes changes to these files on his Surface RT, the changes synchronize to his desktop at work and vice-versa. As he creates sensitive documents, they are automatically classified and RMS protected.
Later, when Joe leaves the company, the IT team removes his devices from management and Joe’s Surface RT automatically wipes (rendered inaccessible) his Work Folders data while leaving all his personal data intact.
Example 2: Enabling Users to Provision their iOS Devices for Work While Enabling IT Pros to Restrict Access to Corporate Resources Based on Device and Location in Addition to the User
This example provides an overview of one way to enable heterogeneous devices at work, and it demonstrates how to register an iOS device with your company’s Active Directory and then enroll it into System Center and Windows Intune.
Once a device is registered, IT pros can control access to company resources based on that user, the device and the location. Once the device is enrolled, IT pros can configure the device, monitor its compliance, publish line of business apps and perform other management tasks.
Although People-centric IT capabilities are great on Windows devices, these capabilities are not limited to Windows devices. We also put a lot of work into enabling first class support for heterogeneous devices in our People Centric IT capabilities. Putting users at the center of what we do includes enabling a broad set of devices.
Sometimes, MDM is talked about as a separate activity to manage mobile devices in addition to solutions deployed to manage PCs and other devices. We think about MDM more broadly. MDM is a part of managing all of your devices. We are building a single solution for managing all of your PCs and devices. We call this concept Unified Device Management.
To deliver UDM, we built the ability to attach Windows Intune to your System Center Configuration Manager deployment. This creates a single console (the Config Manager console) that can manage all types of devices –PCs, mobile devices, even embedded devices. The Config Manager console, when attached to Intune, includes MDM capabilities as a natural part of managing all devices. All device types need apps, data, settings, content and services, and Config Manager enables that in one place.
Here’s how you do it:
- Attach your Active Directory to Azure AD . If you are an Office 365 customer, you have already done this.
- Attach Windows Intune to Config Manager. This is a simple process that involves deploying a new “Intune Connector” Config Manager role. The role has some basic configuration such as the credentials for the Intune subscription. Your Config Manager deployment itself remains unchanged.
- In the configuration for the Windows Intune connector, you’ll be asked for some basic iOS configuration such as the APNs certificate from Apple (see the screen shot below). You can learn more about the options for iOS configuration at this post .
- Specify the users you want to enable to enroll their iOS devices

Setting up the iOS properties of the Windows Intune connector in the Config Manager console.

Uploading the APNs Certificate as part of enabling iOS management from Config Manager.
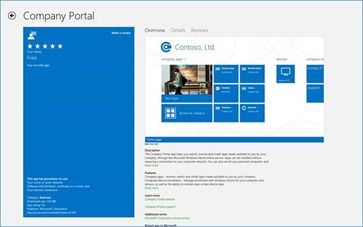
Once this is complete, your users are ready to begin working. They simply download the Company Portal app from Apple’s app marketplace. Seen below is the Company Portal app in the Windows marketplace. The iOS version will appear in the Apple Appstore as part of our R2 wave of releases later this year.
After this, the next time they launch the Company Portal app, they will be prompted for their credentials. From within the app, the user can then opt-in to the Windows Intune service. After this, your users can now access corporate apps and services.

The notification in the upcoming iOS Company Portal app that a device needs to be enrolled with Windows Intune service.

Enrolling the iOS device results in a new Management profile.
The enrollment process installs a certificate and MDM profile on the iOS device from the Intune cloud service. Once complete, that iOS device shows up in the Config Manager console alongside the other devices associated with that user. Any policies or apps targeted to users of that device that are appropriate for iOS will flow from Config Manager out to the Intune cloud and then down to the user’s device. In this way, the device gets provisioned with the settings, Wi-Fi profiles, VPN profiles, certificates, apps and other resources it needs. At the same time, IT is able monitor and manage the device on an ongoing basis.

All of the user’s devices (PCs and mobile) show up in one place together when Config Manager is attached to Windows Intune.
The next element to consider
is how to control access to corporate resources on that device? That’s where our integration with the Active Directory, the Web Application Proxy, and Active Directory Federation Services (AD FS) comes in.
With the R2 wave of releases it is now possible for applications and data to be published through a new Web Application Proxy service role as part of the Windows Server RRAS role. The Web Application Proxy then integrates with AD FS to control access to corporate resources based on a user’s identity, device, and location.
For example: Suppose an IT pro needs to publish an internal Sharepoint site to Internet-connected devices, but this access needs to be limited to known devices that belong to valid users. The IT pro can do this by configuring the AD FS role to restrict access to that Sharepoint site to devices that have been Workplace Joined . Attempts to access the published site will be denied when users connect from devices that are not Workplace Joined, but these same attempts will succeed from devices that are registered. Workplace Join is supported for both Windows and iOS devices.

Example experience of denying user access to a published web site from an iOS device because that device is not Workplace Joined.
To allow users to register iOS devices, you need to first enable the device registration service that is part of Active Directory Federation Services (AD FS). Once this is complete, users can simply be e-mailed a link to register their device. When the user clicks on that link they will be prompted for their credentials, and the registration service will record a user@device record in Active Directory and then issue a certificate profile to the iOS device. Once the user accepts this, they are good to go.
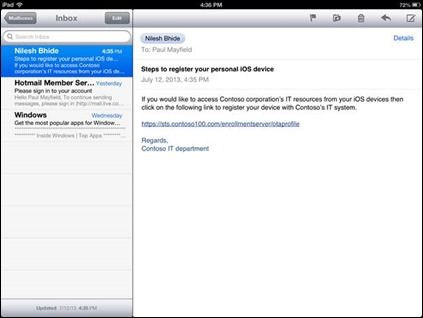
E-mail from IT pro with instructions to Workplace Join an iOS device.

Workplace Join, like any other Web Application Proxy -published IT service, includes the ability to require multi-factor authentication.

Installing the Workplace Join profile on an iOS device.

The profile is successfully installed and the iOS device is now Workplace Joined. Attempts to access the published website will now succeed, and IT can audit and control the access.
When the user attempts to access the published Sharepoint site, the Web Application Proxy will refer the device to AD FS for authentication and authorization. AD FS will challenge the user for their credentials and also challenge the device for the certificate that was installed as part of the Workplace Join. Once AD FS recognizes this as a known device belonging to a valid user, it allows the authentication to succeed and the user receives controlled access to the Sharepoint site.
Example 3: Enabling IT Pros to Deliver VPN Functionality to Corporate and Personal Devices. This Includes Both Microsoft and 3rd Party VPNs Clients and Gateways – and it Covers Upcoming Support for this on Windows RT.
In this example, we will examine a way to enable VPN connectivity on personal Windows 8.1 (including Windows 8.1 RT) devices. To do this, we will look at how to bring Windows 8.1, Windows Server 2012 R2, System Center and Windows Intune together.
Windows 8.1 includes both Microsoft and third party VPN client applications (plugins) already installed. These VPN plugins are included with Windows 8.1 OS (inbox) and do not require an application download. The overall experience blends with Windows, providing end users a consistent and integrated experience. The new VPN platform capabilities also include VPN profile management options and Automatic VPN capabilities. Automatic VPN connections dynamically come up or down as needed. You configure Automatic VPN for both Namespaces and Applications . The VPN connection is launched automatically whenever access to corporate resources are requested.
VPN profile management
In addition to including third party VPN plug-ins, Windows 8.1 also includes built-in manageability that allows multiple options for VPN profile management, including:
- IT Pros can use System Center and Windows Intune to provision VPN profiles and certificates to devices.
- IT Pros can use PowerShell scripts that provision VPN profiles.
- End users can create their own VPN profiles, including third party edges.
A cool new feature in the R2 wave of releases is the native ability to manage VPN profiles in System Center . We support both Microsoft and third party VPNs. You can provision all of your devices from the Config Manager console regardless of whether the device is a PC being managed by the Config Manager agent, or a mobile device enrolled in Windows Intune. When a user enrolls their device for MDM management, the system automatically provisions the appropriate VPN profiles. Additionally, the device enrolls for any certificates the VPN profile requires. Finally, the Automatic VPN policies are applied to the device. When provisioning is complete, the user is ready to start using the VPNs.

Creating a VPN Profile in Config Manager. The profile will be delivered to managed PCs and mobile devices.
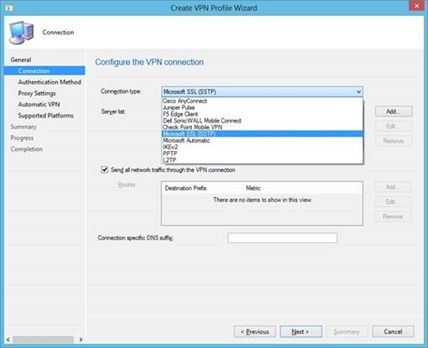
Selecting the VPN type in Config Manager. Our new platform supports both Microsoft and third party VPNs.
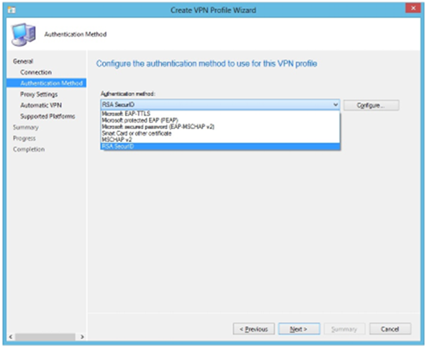
Selecting the authentication type in Config Manager. Again, we support both Microsoft and third party options.

Configuring the Automatic VPN settings. You can cause a connection to raise as needed based on a namespace or an application.
VPN Connect Experience
Whether you use Microsoft’s VPN gateways (the Remote Access role in Windows Server) or a third party VPN gateway, the experience remains the same to the end user. Our new VPN platform in Windows 8.1 integrates VPN into the Windows experience. This means it is no longer necessary to send special instructions to users. By simply enrolling for management, the profiles, certificates and Automatic VPN rules show up on the device. The user then attempts to access a corporate resource and the VPN automatically connects to enable it. If the VPN ever needs additional input from the user (e.g. a password or second factor of authentication), then a toast notification will take the user to a standard network experience to provide it. This experience is similar to joining a new Wi-Fi or mobile broadband network.

Example of providing additional user input as needed by the VPN – all integrated into the standard charms bar, even for third party VPNs.
VPN profile Using In-built PowerShell
In addition to supporting VPN management through System Center, we also support VPN scripting using built-in PowerShell commands. You can use these scripts in imaging or automation workflows – or you can publish them via an out-of-band mechanism such as an external website or a file share. The scripts create VPN profiles and configure remote access on the device.
Example: Creating the VPN Profile with Advanced Trigger Policies:
|
/* Adding name trigger rules */ PS C:> Add-VpnConnectionTriggerDnsConfiguration -ConnectionName "test" -DnsSuffix ".corp.contoso.com" -DnsIPAddress "1.1.1.10" PS C:> Add-VpnConnectionTriggerDnsConfiguration -ConnectionName "test" -DnsSuffix ".domain1.corp.contoso.com" |
|
/* Adding applications trigger rules – modern app*/ PS C:> Add-VpnConnectionTriggerApplication -ConnectionName "test" -ApplicationID "microsoft.windowscommunicationsapps_8wekyb3d8bbwe“ /* Adding applications trigger rules – classic app*/ PS C:> Add-VpnConnectionTriggerApplication -ConnectionName "test" -ApplicationID "C:ProgramDataMicrosoftWindowsStart MenuProgramsMicrosoft Product Studio“ |
|
/* Configuring suffix search list*/ PS C:> Set-VpnConnectionTriggerDnsConfiguration -ConnectionName "test" -DnsSuffixSearchList ("domain2.corp.contoso.com","domain3.corp.contoso.com") /* Adding More entries to Trusted Network List */ PS C:> Add-VpnConnectionTriggerTrustedNetwork -ConnectionName "test" -DnsSuffix "corp.contoso2.com" |
* * *
This overview represents some of the most dynamic features available from this new R2 wave, but there are dozens more. As IT teams deploy and operate the R2 products and services together, users will get to see even more examples of the power and functionality of these platforms.
This strength from interoperation is a result of our decision to approach the engineering of this R2 wave as a hyper-collaborative, highly structured, cross-Microsoft effort. The result of these thousands of hours spent working across teams and across the company is a new suite of products that work great together and enable our community of users to approach their jobs with better-than-ever tools.
In the coming weeks, the other pillar owners will further demonstrate these points as this series examines the Cloud OS, Hybrid IT, and Modern App capabilities built into these 2012 R2 products. You can keep track of each of these posts by bookmarking this link , or by following me on Twitter for regular updates.
- Brad
NEXT STEPS:
To learn even more about the technical topics discussed today, check out these posts from our engineering teams:
-
Supporting iOS Devices in the Workplace
Learn more about empowering your users using iOS devices for work. With System Center 2012 R2, iPhone, iPads, and iPod Touch devices can be productive and secure tools for business. -
PCIT demo from TechEd Europe 2013
To see another examples of these PCIT features at work, check out Adam Hall’s PCIT demo during my keynote at TechEd Europe 2013. -
Coming tomorrow:
Active Directory IT Controls to Manage Risk When Users Access Company Resources from a Wide Variety of Devices
A detailed overview of the new capabilities in Active Directory Federation Services (AD FS) that provide more IT controls to satisfy enterprise risk management needs. -
Compliance Settings and Company Resource Access in Configuration Manager
This post outlines how System Center Configuration Manager and Windows Intune allows an administrator to provide VPN, WiFi profiles, and Certificates to permit users to connect to company resources. -
Protecting Corporate Data on Mobile Devices by using Configuration Manager and Windows Intune
This is an overview of how System Center Configuration Manager and Windows Intune provide the ability for the administrator or user to protect corporate data on mobile devices by leveraging retire and wipe functionality. -
User experience with Unified Device Management using System Center 2012 R2 Configuration Manager and Windows Intune
This post examines how System Center Configuration Manager and Windows Intune provide the user with a consistent enrollment and resource access experience across devices. -
Simplified, User-centric Application Management across Devices with System Center 2012 R2 Configuration Manager and Windows Intune
In this post, the team looks at how System Center Configuration Manager and Windows Intune allow administrators to extend application delivery to all major device types while still centrally managing application delivery across devices from a single console. -
Extending device support in Active Directory
An analysis of Active Directory in Windows Server 2012 R2 and its capabilities to enable People Centric IT -
Enabling Modern Work Styles using Windows Server 2012 R2 Remote Desktop Services
An overview of the improvements made to Microsoft VDI (Remote Desktop Services) reducing storage related costs, improving the end user experience, and administration improvements to both session and VM based VDI. -
Introducing Work Folders on Windows Server 2012 R2
Work Folders enables IT administrators to provide Information Workers the ability to sync their work data on all their devices wherever they are while remaining in compliance with company policies. This is done by syncing user data from devices to on-premise file servers.
* iPad is a trademark of Apple Inc.