First published on CloudBlogs on Aug 15, 2017
Role Based Access Control (RBAC) has been a favorite feature of the System Center Configuration Manager community since its introduction, and now it’s available in Intune. RBAC in Intune enables you to easily define who can perform various Intune tasks within your organization, and who those tasks apply to. RBAC gives you greater flexibility and control while ensuring your IT administrators have the necessary permissions to perform their job.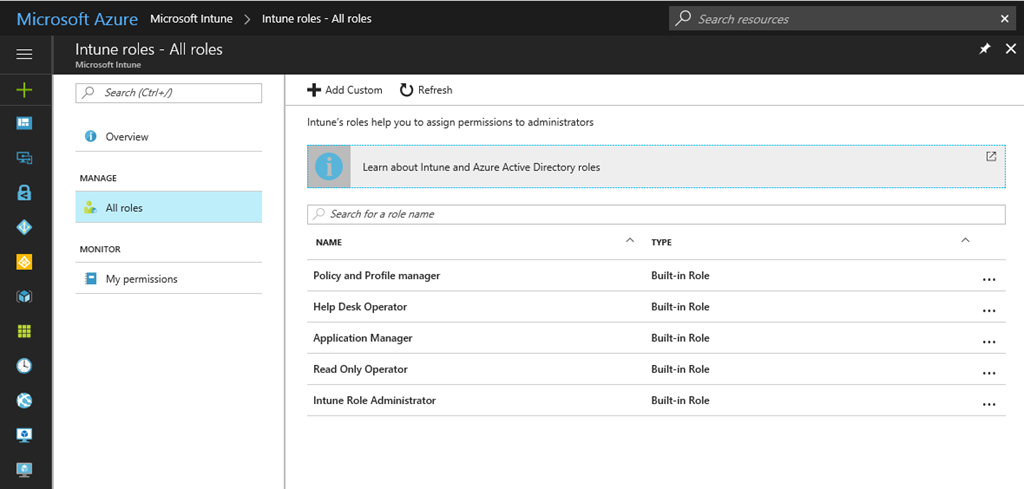 You can also create custom roles
with any permissions required for a specific function. For example, if an IT department group manages applications, policies and configuration profiles, you can add all of those permissions together in one custom role.
And if you’re into automation
– you can automate any RBAC task such as creating custom roles, or adding/modifying role assignments using the
Microsoft Graph API
. We also have a set of
PowerShell scripts
that can help you get started.
You can also create custom roles
with any permissions required for a specific function. For example, if an IT department group manages applications, policies and configuration profiles, you can add all of those permissions together in one custom role.
And if you’re into automation
– you can automate any RBAC task such as creating custom roles, or adding/modifying role assignments using the
Microsoft Graph API
. We also have a set of
PowerShell scripts
that can help you get started.
Role Based Access Control (RBAC) has been a favorite feature of the System Center Configuration Manager community since its introduction, and now it’s available in Intune. RBAC in Intune enables you to easily define who can perform various Intune tasks within your organization, and who those tasks apply to. RBAC gives you greater flexibility and control while ensuring your IT administrators have the necessary permissions to perform their job.
Integration with Azure AD Directory Roles for high level access control
The new Intune admin experience on Azure delivers deeper levels of integration with Azure Active Directory, which includes Azure AD Groups as well as integration with Azure AD Directory Roles. This integration provides the underpinnings of Intune’s RBAC capabilities and our overall permissions management story. RBAC for Intune starts by leveraging four Azure AD Directory Roles that define high level administrative access to Intune workstreams and tasks:- Global Administrator / Company Administrator : users in this role have access to all administrative features in Azure AD, including conditional access. They can also manage all of Intune.
- User Administrator : users in this role can manage users and groups but cannot manage all of Intune.
- Intune Service Administrator : users in this role can manage all of Intune, including management of users and devices, as well group creation and management. This role does not allow for management of Azure AD’s Conditional Access settings.
- Conditional Access Administrator : users in this role can manage Azure AD’s Conditional Access policies, but not all of Intune.
Intune Roles for finer-grained control based on job function
From there you can define finer-grained controls by leveraging built-in Intune roles, which are designed to mirror your IT Departments’ job functions. There are five pre-defined roles built into Intune:- Policy and Profile Manager : users in this role have rights to manage configuration and compliance policies.
- Application Manager : users in this role have rights to manage mobile and Intune managed app protection policies.
- Helpdesk Operator : users in this role have rights to manage tasks appropriate for end-user service desk support personnel.
- Read Only Operator : users in this role have rights to view Intune information without the ability to change configurations and policies.
- Intune Role Administrator : uses in this role have rights to manage of Intune Roles.
 You can also create custom roles
with any permissions required for a specific function. For example, if an IT department group manages applications, policies and configuration profiles, you can add all of those permissions together in one custom role.
And if you’re into automation
– you can automate any RBAC task such as creating custom roles, or adding/modifying role assignments using the
Microsoft Graph API
. We also have a set of
PowerShell scripts
that can help you get started.
You can also create custom roles
with any permissions required for a specific function. For example, if an IT department group manages applications, policies and configuration profiles, you can add all of those permissions together in one custom role.
And if you’re into automation
– you can automate any RBAC task such as creating custom roles, or adding/modifying role assignments using the
Microsoft Graph API
. We also have a set of
PowerShell scripts
that can help you get started.
Get started using RBAC in Intune today
For more detail on our RBAC story and how to get started using it in your Intune admin experience on Azure, check out this blog post from Dave Randall , the Program Manager responsible for RBAC in Intune. Dave’s post includes step by step screenshots that walk you through the capabilities, and shows you how granular you can get with defining access for roles. RBAC gives IT administrators a simple way to enable powerful control over who can perform various administrative tasks within their organization and they are available to use today in our new admin experience on Azure .Published Sep 08, 2018
Version 1.0Intune Team
Brass Contributor
Joined September 05, 2018
Microsoft Security Community Blog
Follow this blog board to get notified when there's new activity