First published on CloudBlogs on Jan 20, 2016
People often ask us where to begin an enterprise mobility management (EMM) project. EMM is such a broad space, with so many ways to build an advanced solution, including apps, policies, and device configurations. What we’ve found is that it’s best to start with the basics—a good foundation—and build on that. Think of creating an EMM deployment like brewing beer. Breweries use malted grain to make amazing beers. Hundreds of malts are available to them, and each malt adds a unique quality to their beers. Breweries don’t throw every malt possible into their recipes, however. Most great beers have only a few malts in them that the master brewer choses for the unique qualities and balance they add. When it comes to beer, a simple foundation is invariably better. Likewise, a simple EMM deployment with a few select “malts” is the best way to start your mobile management project, particularly in the beginning, when you want to ease your users into mobility management by providing a great user experience. This approach will help build confidence and trust in your users. You can evaluate and extend your deployment later, but you don’t need to throw in every “malt” that the Microsoft Enterprise Mobility suite offers from the beginning. The best deployments balance the company’s need for security against the complexity of the proposed solution. When we look at our most successful customers, we’ve noticed that they took an incremental approach, iteratively refining their solutions. Frequently, these customers find that they don’t need to deploy as many capabilities as they originally thought. In short, your needs might be simpler than you expect.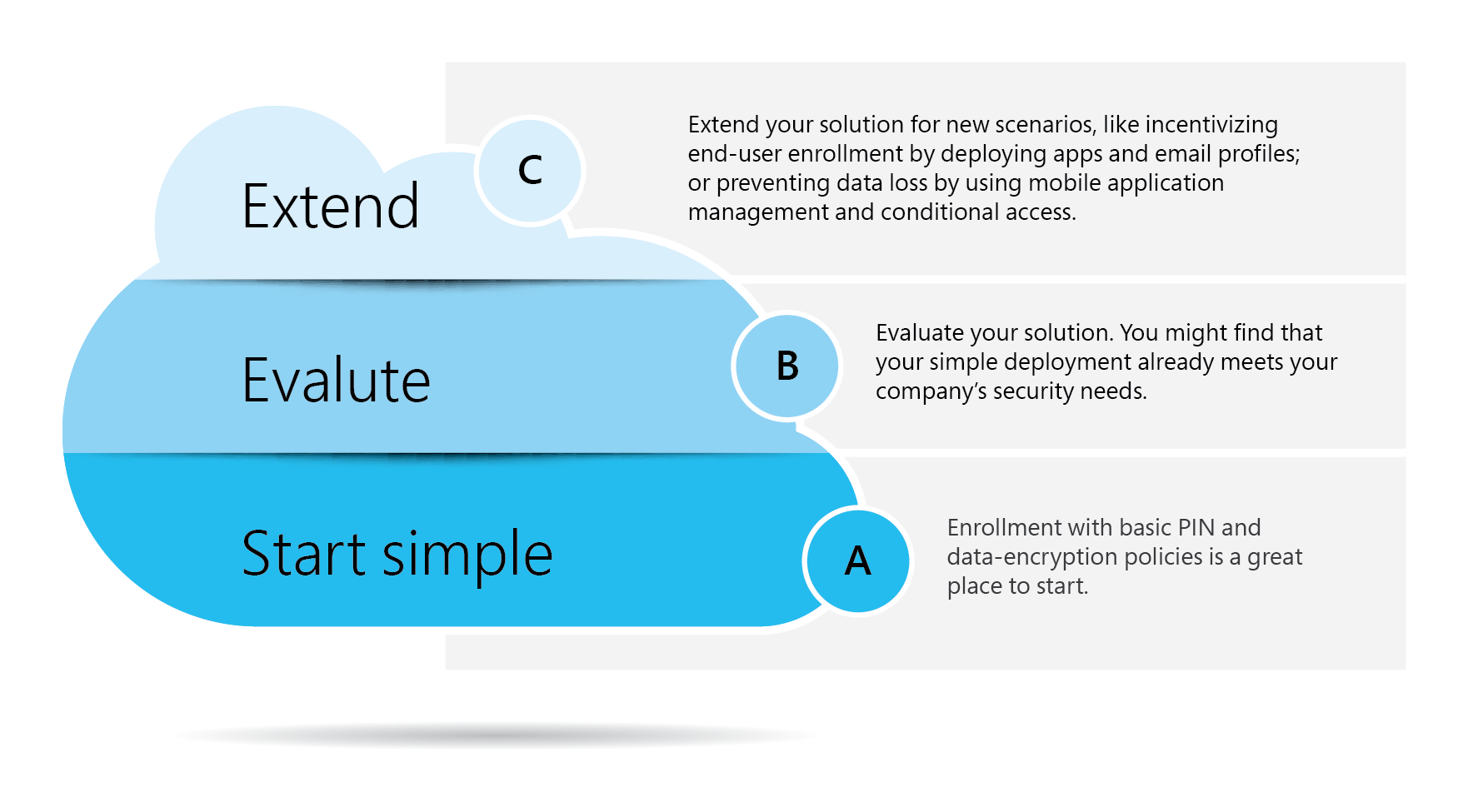
People often ask us where to begin an enterprise mobility management (EMM) project. EMM is such a broad space, with so many ways to build an advanced solution, including apps, policies, and device configurations. What we’ve found is that it’s best to start with the basics—a good foundation—and build on that. Think of creating an EMM deployment like brewing beer. Breweries use malted grain to make amazing beers. Hundreds of malts are available to them, and each malt adds a unique quality to their beers. Breweries don’t throw every malt possible into their recipes, however. Most great beers have only a few malts in them that the master brewer choses for the unique qualities and balance they add. When it comes to beer, a simple foundation is invariably better. Likewise, a simple EMM deployment with a few select “malts” is the best way to start your mobile management project, particularly in the beginning, when you want to ease your users into mobility management by providing a great user experience. This approach will help build confidence and trust in your users. You can evaluate and extend your deployment later, but you don’t need to throw in every “malt” that the Microsoft Enterprise Mobility suite offers from the beginning. The best deployments balance the company’s need for security against the complexity of the proposed solution. When we look at our most successful customers, we’ve noticed that they took an incremental approach, iteratively refining their solutions. Frequently, these customers find that they don’t need to deploy as many capabilities as they originally thought. In short, your needs might be simpler than you expect.

Set PIN and data-encryption policy
The follow-up question is, “Where do you start?” Our recommendation for most companies is to start with the basics, enabling device enrollment with device PIN and data-encryption policies. You apply all these device settings in a configuration policy (See Use policies to manage computers and mobile devices with Microsoft Intune for more information about configuration policies). That’s it! These policies will help give you instant risk mitigation, and you can configure them during your lunch break. Quick enrollment plus a basic policy might be all your company needs in the beginning. After reviewing the results, you might even realize that the deployment meets all your company’s security needs without too much complexity: a perfectly simple start.Deploy to a pilot group
The tendency for admins configuring policy in Intune is to set it and forget it. They deploy the policy to a large swath of users and assume the best. We encourage a different approach. Back to our beer analogy, think about deploying your EMM solution in a similar way. When breweries develop new recipes, they test them on small audiences and make adjustments as they get feedback. After they perfect the recipe, they lock it in and distribute it to a larger audience. Use a similar approach to deploy your EMM solution: start by deploying any new capability to a small pilot group. This group can consist of users within your IT department or a cross-section of the entire organization. Close the loop by collecting and addressing feedback from the pilot group. Then, deploy your solution to a larger group, possibly the entire organization.Proactively address any privacy concerns
Users’ privacy concerns will also lead you to think about EMM deployment differently. If your users fear that their privacy may be compromised, they won’t be eager to enroll. Make sure they understand what their organization can and cannot see or do on their mobile devices. To help you communicate these points, we provide the Microsoft Intune End User Enrollment Guide , which you can customize and give to your users. The following table summarizes what IT can and cannot see on users’ devices, as noted in the Enrollment Guide. Table 1. Information that IT can and cannot see on users’ mobile devices| IT can see this type of information: | IT cannot see this type of information: |
| · Company apps | · Call history |
| · Device manufacturer | · Camera roll |
| · Device model | · Location |
| · Device name | · Personal data |
| · Device owner | · Personal email, contacts, and calendar |
| · Device serial number | · Text messages |
| · Operating system | · Web history |
Build on your solution as your needs change
After you’ve deployed your EMM solution, you might identify additional scenarios that Intune can help you address. Extending your solution with new scenarios, however, doesn’t mean that you lose the simplicity. By using Intune, you can deploy simple solutions to those scenarios. Think of these scenarios as add-ons. Here are a few add-on scenarios for your consideration:- To incentivize your users to enroll, provide easy access to company resources and apps. This scenario is low-hanging fruit. You can encourage people to enroll simply by making their lives easier as a result of doing so. Use Intune to deploy Wi-Fi, virtual private network, certificate, and email profiles to users so that they don’t have to configure these connections manually (See Enable access to company resources with Microsoft Intune to learn how to configure these profiles in Intune). With basic connectivity in place, you can greatly simplify how users get the apps they need (See Deploy apps to mobile devices in Microsoft Intune ).
- Demonstrate devices’ compliance with company policies. By using compliance policies in Intune, you can establish compliance rules, and then determine which devices are or are not compliant with them. Rules can manage PINs or passwords, encryption, whether devices can be jail-broken, and whether Intune manages email on the devices (See Manage device compliance policies for Microsoft Intune for more information about Intune compliance policies).
- Protect access to email and Microsoft SharePoint sites. A logical extension of your simple deployment is to use conditional access policies to require device enrollment before users gain access to their company email. You can use conditional access policies to prevent backsliding on enrollment numbers. Combined with mobile application management (MAM) policies, you can also protect the data in your email system or SharePoint sites, preventing data leakage (See Configure data loss prevention app policies with Microsoft Intune to learn how to configure and deploy MAM policies in Intune).
Start simple, evaluate, and then extend
A good example of this philosophy comes from a customer of ours in Europe. The company has a successful EMM deployment focused on enrollment and basic policy (PIN and encryption), and then deployment of a single line-of-business app. This company is a great example of using EMM well because it protected against its biggest concern (lost devices) but didn’t control any more than necessary. The company uses Intune to manage 10,000 Android, iOS, and Windows Phone devices, with the goal of reaching 40,000 managed devices. Still, the company has a simple EMM deployment. It successfully hit the sweet spot between managing protection and enabling productivity. Our recommendation is that you start simple, evaluate your solution, and then consider whether you need to extend it. Start with a few basic enrollment policies and see how your users respond. Then, build on the deployment as you close the feedback loop and your needs grow. If you’d like to start a free 30-day trial and put these best practices to work, see Start using Microsoft Intune .Published Sep 08, 2018
Version 1.0Intune Team
Brass Contributor
Joined September 05, 2018
Microsoft Security Community Blog
Follow this blog board to get notified when there's new activity