- Home
- Public Sector
- Public Sector Blog
- Have you seen the “My” URLs of Azure Active Directory?
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft has long talked about how identity is the new security perimeter and using modern identity management tools like Azure Active Directory (Azure AD) can help, but have you ever visited the “My” URLs of Azure AD?
What are “My” URLs?
There are 4 user driven URLs for Azure Active Directory that many people have never seen and can empowers end users, reduce load on helpdesk employees, optimize organizations access to applications, and improve end user experience.
- MyAccess.Microsoft.com
- MyApplications.Microsoft.com
- MyWorkAccount.Microsoft.com
- MySignins.Microsoft.com
How does it help?
Have you ever logged onto https://myworkaccount.microsoft.com/ with your corporate ID?
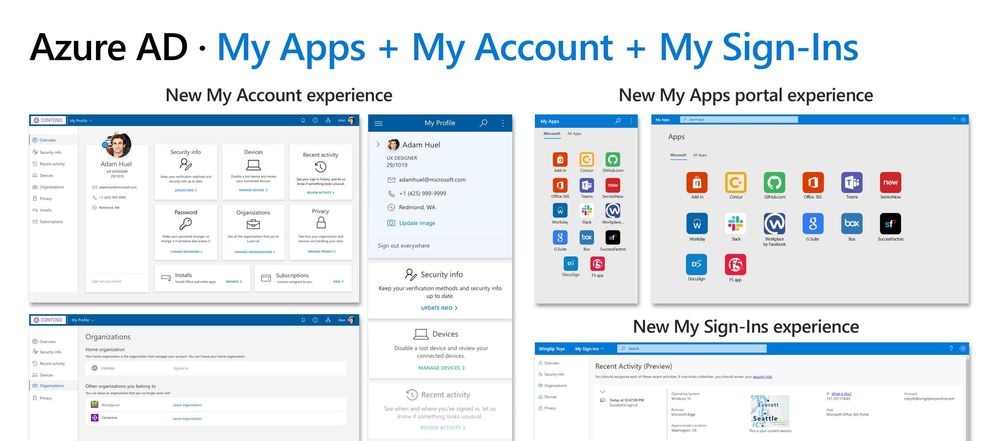
Last fall Microsoft updated features in Azure AD to empower end users to gain more insights and control over their own identity management.
Myworkaccount allows individuals to manage the following:
- Security info related to Multi-Factor Authentication (MFA)
- Managed lost devices
- Reset password
- Manage Azure AD org membership
- Access Office Apps
- View subscriptions
- View their recent sign-in information
How do I provide Access to Application?
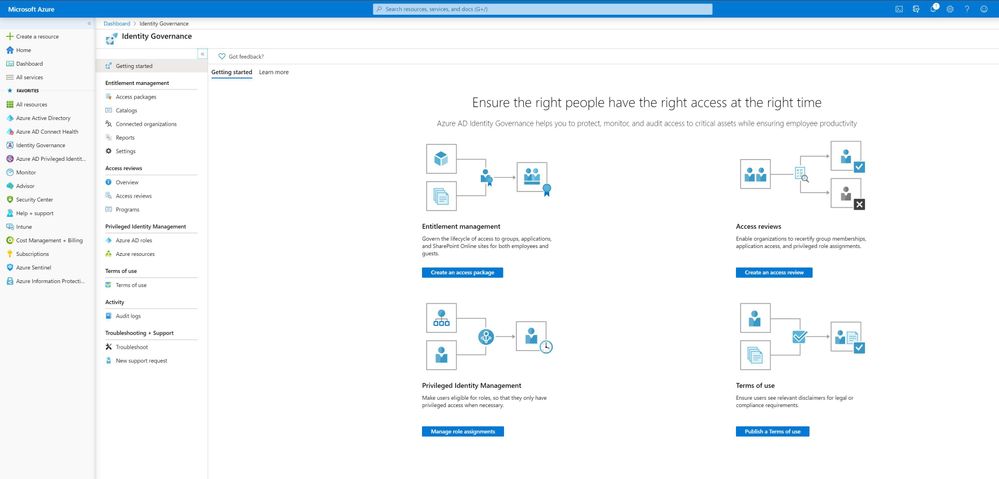
Microsoft released a feature of Azure AD called Identity Governance; Identity Governance allows organizations to create workflows that allow users to request access to applications through an automation process. A part of this process is a feature called Access Reviews, Access Reviews wraps a review process around each application request that provides controls to keep access limited to the correct user(s) and can limit how long users have access to applications.
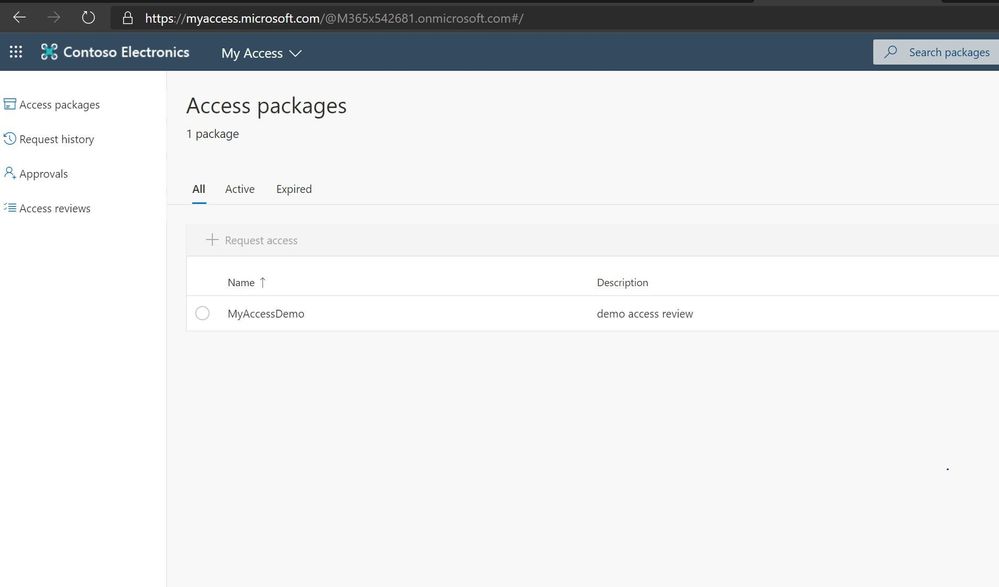
Users connect to https://myaccess.microsoft.com and once a user has logged in, they are presented with a list of access packages, request history, approvals, and access reviews.
How do I access my applications that I requested?
For years we have talked about how organizations can use Azure AD App proxy to publish applications for your organization. Recently, Microsoft updated the MyApps portal to a new look and feel providing a place where users can connect ( https://MyApplications.Microsoft.com) and are presented with a list of applications they are authorized to use. The MyApps portal now allows organizations to create categories of applications to simplify the users experience.
The new “My” URLs are another way an organization can allow users to manage their account settings, add additional security controls to web based applications, create governance around user’s access, and off load some help desk tasks.
**Please note URLs for Azure Gov and GCC-H will have .US extensions vs .COM and not all URLs have been updated yet for the new experience. For Azure Gov customers you can use MyAccess.Microsoft.US and account.activedirectory.windows.us until all URLs have been updated.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.