First published on CloudBlogs on Jul, 25 2018
Howdy folks, We know many of you use conditional access in Azure AD—it’s the most popular feature in Azure AD premium! And to manage conditional access at scale, we also know you need detailed visibility into how it’s actually working in your organization. So, today I’m excited to announce the public preview for conditional access information in the Azure AD Sign-ins report. This new information will help you troubleshoot conditional access policies and understand the usage of conditional access in your organization. As we designed this new capability, there were four key scenarios we focused on enabling:
 Additionally, you can access all this rich information through Microsoft Graph API! Learn more about the
Azure AD reporting API
.
Additionally, you can access all this rich information through Microsoft Graph API! Learn more about the
Azure AD reporting API
.
Howdy folks, We know many of you use conditional access in Azure AD—it’s the most popular feature in Azure AD premium! And to manage conditional access at scale, we also know you need detailed visibility into how it’s actually working in your organization. So, today I’m excited to announce the public preview for conditional access information in the Azure AD Sign-ins report. This new information will help you troubleshoot conditional access policies and understand the usage of conditional access in your organization. As we designed this new capability, there were four key scenarios we focused on enabling:
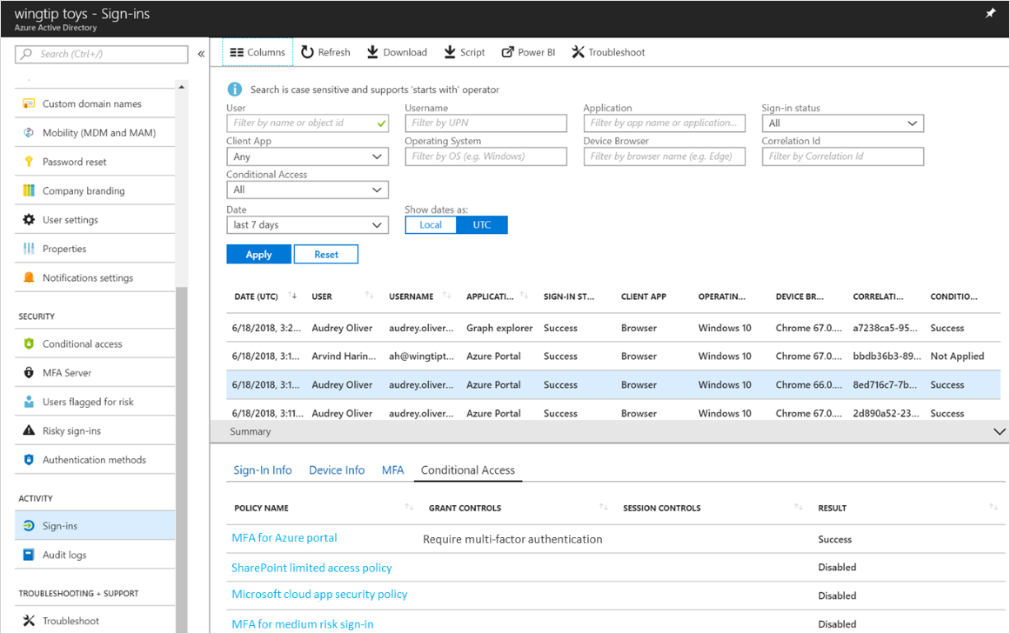
- Quickly troubleshoot conditional access policies —You can now view all the conditional access policies that impacted a user’s sign-in and the result of each policy. The correlation ID column in the Sign-ins report lets you to easily identify the sign-in reported by the user.
- Understand usage of conditional access policies —Using the conditional access column and the policy information, you’ll be able to understand how conditional access policies are working in your organization. Using the Azure AD reporting API, you can pull the usage data into your SIEM systems and business intelligence tools.
- Understand legacy authentication usage in your organization —Using the client app column in the Sign-ins report, you can see the users/apps using legacy authentication in the organization. This reporting will help you smoothly roll out a blocking legacy authentication policy. (To learn more about how to block legacy authentication, check out this recent blog post .)
- Identify gaps in your conditional access policies —Using the conditional access column in the Sign-ins report, you can easily identify sign-ins/apps/users that are not protected by conditional access.
Get started!
Ready to dive deeper? To get started, follow the steps below:- In Azure AD, go to the Sign-ins report.

- Select the sign-in you want to troubleshoot. If you have the correlation ID from the user, simply search for the sign-in using the correlation ID.
- Navigate to the Conditional Access tab. You can now view all the policies that impacted the sign-in and the result for each policy.
 Additionally, you can access all this rich information through Microsoft Graph API! Learn more about the
Azure AD reporting API
.
Additionally, you can access all this rich information through Microsoft Graph API! Learn more about the
Azure AD reporting API
.
Tell us what you think
As always, we want to hear any feedback or suggestions you have. Please let us know what you think in the comments below! Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity DivisionUpdated Jul 24, 2020
Version 7.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.