First published on CloudBlogs on Oct, 04 2016
Howdy folks, Great news to share today! The Azure AD device-based Conditional Access policies for iOS, Android and Windows are generally available. Since we announced the public preview of this feature back in August, we’ve seen a ton of customer interest and usage. So we’re really pleased to be able to release these features for production usage. These policies in conjunction with MFA, network location and risk scores from Azure AD Identity Protection and the MDM capabilities of Microsoft Intune provide the industries most comprehensive set of security and compliance controls. (If you want to learn more about Azure AD conditional access go here .) Quite a few customers already have these policies in their production environments and are already requiring employees to use properly configured devices to access Office 365 and other applications. This includes controlling access from iOS, Android and Windows (10, 8.1 & 7). And just a quick reminder: Conditional Access works with EVERY application that authenticates using Azure AD! That means Office 365, Azure and Microsoft CRM as well as all the apps in our app gallery, including thousands of apps like ServiceNow, Salesforce.com & Concur, plus on-premises apps published through the Azure AD Application Proxy. Please note: Conditional Access is a feature of Azure AD Premium.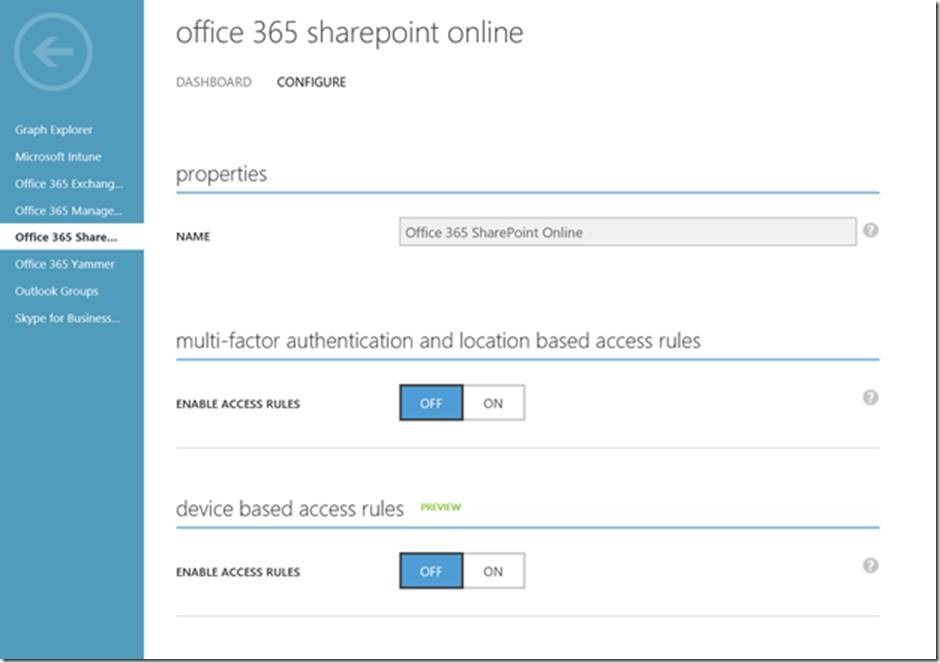 When you enable these rules, you can select which users or groups the policy applies to, which devices are covered and which type of client applications are covered (browser and native apps or native apps only).
When you enable these rules, you can select which users or groups the policy applies to, which devices are covered and which type of client applications are covered (browser and native apps or native apps only).
 After creating and saving the policy, all access attempts from a device that doesn’t meet the policy to an Azure AD protected resource will be denied.
To learn about each of the controls available we have prepared a guide where you can find the details on each of the conditions,
here
.
After creating and saving the policy, all access attempts from a device that doesn’t meet the policy to an Azure AD protected resource will be denied.
To learn about each of the controls available we have prepared a guide where you can find the details on each of the conditions,
here
.
Howdy folks, Great news to share today! The Azure AD device-based Conditional Access policies for iOS, Android and Windows are generally available. Since we announced the public preview of this feature back in August, we’ve seen a ton of customer interest and usage. So we’re really pleased to be able to release these features for production usage. These policies in conjunction with MFA, network location and risk scores from Azure AD Identity Protection and the MDM capabilities of Microsoft Intune provide the industries most comprehensive set of security and compliance controls. (If you want to learn more about Azure AD conditional access go here .) Quite a few customers already have these policies in their production environments and are already requiring employees to use properly configured devices to access Office 365 and other applications. This includes controlling access from iOS, Android and Windows (10, 8.1 & 7). And just a quick reminder: Conditional Access works with EVERY application that authenticates using Azure AD! That means Office 365, Azure and Microsoft CRM as well as all the apps in our app gallery, including thousands of apps like ServiceNow, Salesforce.com & Concur, plus on-premises apps published through the Azure AD Application Proxy. Please note: Conditional Access is a feature of Azure AD Premium.
Getting Started
To set these policies is easy. On the Azure Management Portal, select the application you want to protect. Under the ‘configure’ tab you will find the control to enable device base access rules. When you enable these rules, you can select which users or groups the policy applies to, which devices are covered and which type of client applications are covered (browser and native apps or native apps only).
When you enable these rules, you can select which users or groups the policy applies to, which devices are covered and which type of client applications are covered (browser and native apps or native apps only).
 After creating and saving the policy, all access attempts from a device that doesn’t meet the policy to an Azure AD protected resource will be denied.
To learn about each of the controls available we have prepared a guide where you can find the details on each of the conditions,
here
.
After creating and saving the policy, all access attempts from a device that doesn’t meet the policy to an Azure AD protected resource will be denied.
To learn about each of the controls available we have prepared a guide where you can find the details on each of the conditions,
here
.
Supported devices and applications
You may have a variety of devices in your organization. For devices to be able to participate in device-based conditional access, devices must be registered with Azure AD as follows:- Windows domain joined devices (in on-premises Active Directory) can be easily registered with Azure AD in an automatic manner. This includes both Windows 10 and down-level Windows devices.
- iOS and Android devices are registered with Azure AD when they get enrolled into Microsoft Intune, our MDM service.
- Windows 10 Azure AD joined devices are registered upon being joined to Azure AD.
- Windows 10 personal devices (BYOD) are registered when the work account is added to Windows.
- Microsoft Office 365 Exchange Online
- Microsoft Office 365 SharePoint Online
- Dynamics CRM
- Power BI
- All of the 2,700+ SaaS applications from the Azure AD application gallery
- On-premises apps registered with Azure AD Application Proxy
- LOB apps registered with Azure AD
Try it out
We’re excited to be making this functionality generally available. Please give it a spin and let us know what you think. You can learn more about conditional access capabilities here . This is a set of capabilities that I know a LOT of you have been asking for. I hope you’ll find it useful. And as always, we would love to receive any feedback of suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity DivisionUpdated Jul 24, 2020
Version 5.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.