First published on CloudBlogs on Feb, 06 2017
Howdy folks, One of the top requests we hear from customers is to be able to secure their on-premises VPNs using Azure AD and our cloud-based MFA service. Today we're announcing the public preview of NPS Extension support in Azure MFA. This cool enhancement gives you the ability to protect your VPN using Azure MFA (which is included in Azure AD Premium) without having to install a new on-premises server. This is another step along the road to realizing our vision of making Azure AD a complete, cloud based "Identity Control Plane" service that makes it easy for enterprises to assure their employees, partners and customers have access to all the right cloud and on-premises resources while assuring the highest levels of compliance and security. To give you the details about this release, I've asked Yossi Banai to write a blog about this cool new capability. His blog is below. I hope you'll find this update useful for improving the security of your organization! And as always, we would love to receive any feedback or suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division ------------------ Hello, I'm Yossi Banai, a Program Manager on the Azure Active Directory team. As you know, multi-factor authentication is an important tool to help safeguard data and applications while meeting user demands for a simple sign-in process. With Azure Multi-factor authentication (MFA), customers currently can choose between MFA Server (an on-premises solution) and cloud-based MFA (a cloud-based solution supported and maintained by Microsoft). While MFA Server provides a rich set of features, more and more customers are choosing to use cloud-based MFA to secure their environment, to simplify it, reduce cost, and take advantage of powerful Azure AD features such as Conditional Access and Azure AD Identity Protection . However, since cloud-based MFA services like Azure AD have not traditionally supported RADIUS authentication , customers who wanted to secure on-premises clients such as VPN had no choice but to deploy MFA Servers on-premises. With today's release of the NPS Extension for Azure MFA, I'm excited to announce that we have closed this gap, and added the ability to secure RADIUS clients using cloud-based MFA! The NPS extension for Azure MFA provides a simple way to add cloud-based MFA capabilities to your authentication infrastructure using your existing NPS servers . With the NPS extension, you'll be able to add phone call, SMS, or phone app MFA to your existing authentication flow without having to install, configure, and maintain new servers. How does the NPS Extension for Azure MFA work? With the NPS Extension for Azure MFA, which is installed as an extension to existing NPS Servers, the authentication flow includes the following components:
Howdy folks, One of the top requests we hear from customers is to be able to secure their on-premises VPNs using Azure AD and our cloud-based MFA service. Today we're announcing the public preview of NPS Extension support in Azure MFA. This cool enhancement gives you the ability to protect your VPN using Azure MFA (which is included in Azure AD Premium) without having to install a new on-premises server. This is another step along the road to realizing our vision of making Azure AD a complete, cloud based "Identity Control Plane" service that makes it easy for enterprises to assure their employees, partners and customers have access to all the right cloud and on-premises resources while assuring the highest levels of compliance and security. To give you the details about this release, I've asked Yossi Banai to write a blog about this cool new capability. His blog is below. I hope you'll find this update useful for improving the security of your organization! And as always, we would love to receive any feedback or suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division ------------------ Hello, I'm Yossi Banai, a Program Manager on the Azure Active Directory team. As you know, multi-factor authentication is an important tool to help safeguard data and applications while meeting user demands for a simple sign-in process. With Azure Multi-factor authentication (MFA), customers currently can choose between MFA Server (an on-premises solution) and cloud-based MFA (a cloud-based solution supported and maintained by Microsoft). While MFA Server provides a rich set of features, more and more customers are choosing to use cloud-based MFA to secure their environment, to simplify it, reduce cost, and take advantage of powerful Azure AD features such as Conditional Access and Azure AD Identity Protection . However, since cloud-based MFA services like Azure AD have not traditionally supported RADIUS authentication , customers who wanted to secure on-premises clients such as VPN had no choice but to deploy MFA Servers on-premises. With today's release of the NPS Extension for Azure MFA, I'm excited to announce that we have closed this gap, and added the ability to secure RADIUS clients using cloud-based MFA! The NPS extension for Azure MFA provides a simple way to add cloud-based MFA capabilities to your authentication infrastructure using your existing NPS servers . With the NPS extension, you'll be able to add phone call, SMS, or phone app MFA to your existing authentication flow without having to install, configure, and maintain new servers. How does the NPS Extension for Azure MFA work? With the NPS Extension for Azure MFA, which is installed as an extension to existing NPS Servers, the authentication flow includes the following components:
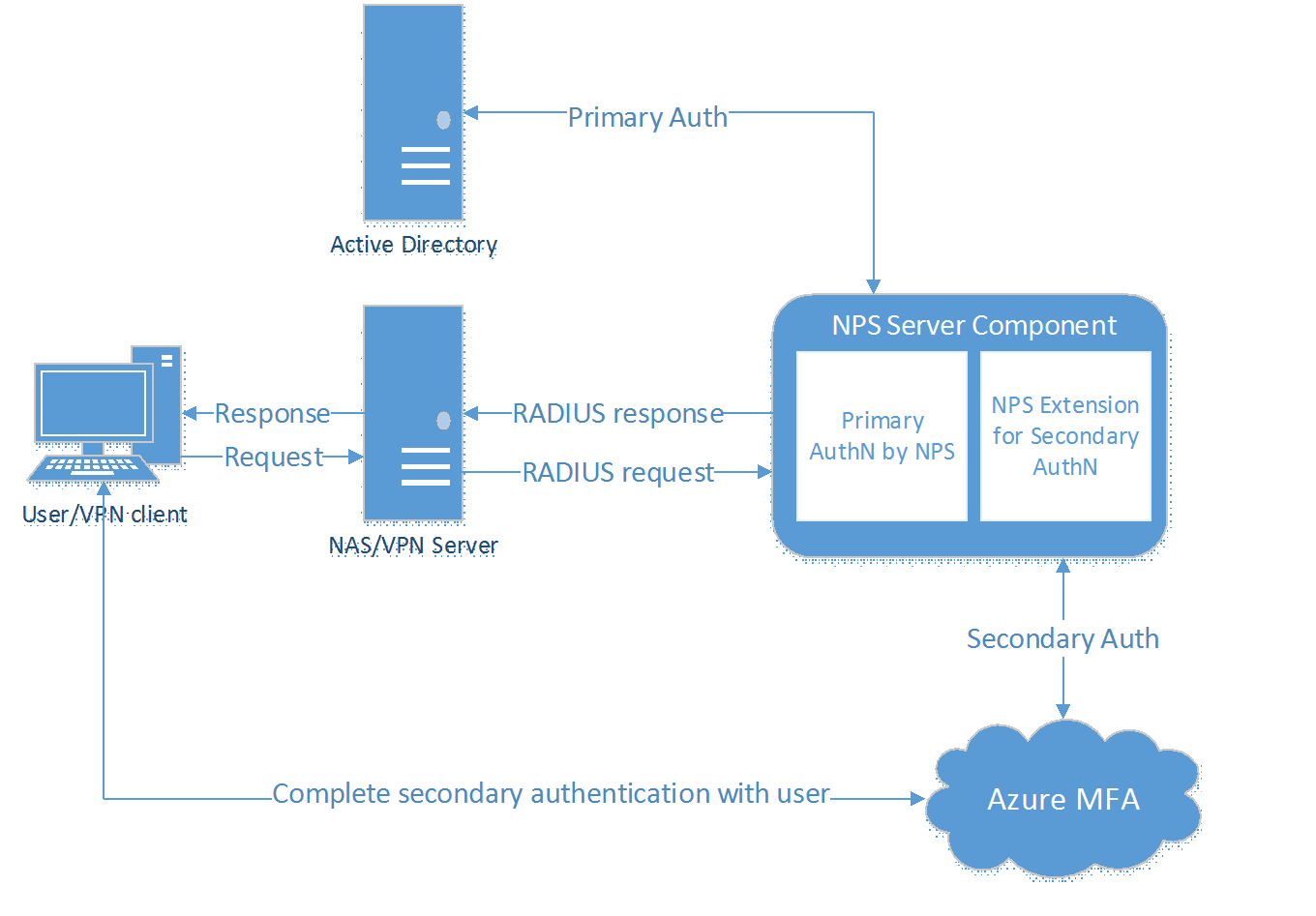
- User/VPN Client: Initiates the authentication request.
- NAS Server/VPN Server: Receives requests from VPN clients and converts them into RADIUS requests to NPS servers.
- NPS Server: Connects to Active Directory to perform the primary authentication for the RADIUS requests and, if successful, pass the request to any installed NPS extensions.
- NPS Extension : Triggers an MFA request to Azure cloud-based MFA to perform the secondary authentication. Once it receives the response, and if the MFA challenge succeeds, it completes the authentication request by providing the NPS server with security tokens that include an MFA claim issued by Azure STS.
- Azure MFA : Communicates with Azure Active Directory to retrieve the user's details and performs the secondary authentication using a verification method configured for the user.
Updated Jul 24, 2020
Version 8.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.