First published on CloudBlogs on Jan, 29 2015
Howdy folks, Today I have the cool opportunity to tell you about two new features we've just put into preview:
Howdy folks, Today I have the cool opportunity to tell you about two new features we've just put into preview:
- Conditional Access for SaaS Apps
- Azure AD Connect Health
Azure AD Conditional Access Preview for SaaS Apps
Greetings, I'm Caleb Baker from the Cloud Authentication and Authorization Technologies team at Microsoft. If you've been following the news lately, you are painfully aware that from a security standpoint, passwords just aren't enough anymore. This is one reasons companies and SaaS App providers like Microsoft, Google and Twitter are increasing using Multi-Factor Authentication (MFA). So it's no surprise that the Azure MFA service has been one of our most popular services. Azure MFA, first launched in June of 2014, makes it easy to require MFA for all applications a user accesses which is a great option for increasing the security of your cloud applications. But many of you have asked for the ability to be able to decide whether to require Multi-Factor Authentication (MFA) on a per-application basis. We heard you, and today we're announcing that we have turned on the preview of our new Conditional Access service in Azure AD Premium which makes this (and soon many other scenarios) possible. Starting today, you can specify application specific MFA policies for all of the federated SaaS applications that work with Azure AD, including Workday, Salesforce, Concur and Google Apps for Work. Today's preview release gives you additional flexibility and granularity in configuring MFA.- You can limit the MFA requirement to specific security-sensitive applications.
- Policies can apply to all users, specific users or to specific security groups.
- You can allow users coming from a trusted network (e.g., your corporate network) to skip MFA based on a list of trusted IP ranges.
How to configure per-application MFA
Start by signing into the Azure management portal . Under the Active Directory section, select your directory and then select the Applications tab. Next, select a federated application such as Workday, Salesforce, Concur or Google Apps for Work. You can configure an application to be federated by choosing the Windows Azure AD Sign-On option when configuring SSO. The screen below shows you how to do this when configuring SSO for Salesforce.




- Require multi-factor authentication
- Require multi-factor authentication when not at work
Azure AD Connect Health Preview
Hi Everyone, Samuel Devasahayam here! As Alex mentioned in his intro, every day tens of thousands of Microsoft customers use ADFS to provide authentication and SSO to Azure AD/Office 365. They also use ADFS to secure internal LOB applications and collaborate with other organizations. However this can be challenging for IT organizations in that they must run ADFS as a reliable and highly available service. Afterall, for many businesses, if your employees can't login, it's pretty much impossible to get work done! This puts quite a bit of pressure on the IT team, especially because many times they aren't even of aware of issues until they results in loss of access to critical applications. To help address these challenges, today we are also releasing a preview of Azure Active Directory Connect Health in the Azure Preview Portal . This feature of Azure Active Directory Premium helps you monitor and gain insight into health, performance and login activity of your on-premises Active Directory infrastructure. While this release supports Active Directory Federation Services (ADFS), we are already working to add support for sync servers in the future. This release for ADFS has three key capabilities:- Alerts based on events, configuration information, synthetic transactions and perf data. So, when something goes wrong, or is about to go wrong, we let you know.
- Graphs of login activity that you can pivot multiple ways for easy viewing. These "usage insights," are accessible when you enable auditing on your ADFS servers. They are based on audits generated when user's login and tokens are generated for applications.
- Access to key performance indicators across multiple servers, including token request counters, processor, memory, latency, and so forth
Installing the agent
The first step is to install the agent on each of your ADFS and ADFS proxy/Web Application proxy servers.- Login into the Azure Preview Portal with your Azure AD global administrator account. This account must also be licensed for Azure AD premium.
-
Click on the Marketplace tile. Under Identity you will find the Azure AD Connect health extension.
Click on it to enable the service and gain access to Azure AD Connect Health within the portal.
- Click on the Quick Start tile and download the agent onto your ADFS and proxy servers.
-
Install the agent that you just downloaded.
-
Fire up a PowerShell window. Use the Register-ADHealthAgent commandlet to configure and register the health agent to securely connect to the Azure AD Connect Health service. You will need admin credentials.
Using the Portal to view the health and usage of ADFS
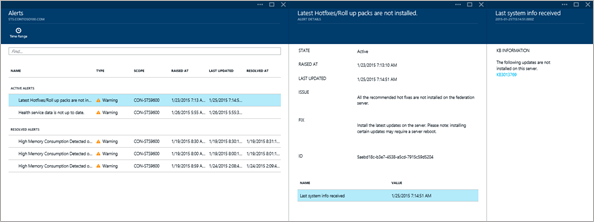
The portal is comprised of three key views. Let's dive into some of the details.Alerts
The Azure AD Connect Health Alerts section shows you the list of active alerts requiring administrator attention, which are based on ADFS service events, performance counters and configuration information. These could be issues with certificates, connectivity to domain controllers or as simple as detecting that the ADFS service is not running. They can also warn of potential issues. Selecting an alert reveals more detailed information, as well as resolution steps and links to relevant documentation. You can also view historical data on previously resolved alerts.

Usage Analytics
Usage analytics provide insight to login activity based on security audits that each of the ADFS servers generates and sends to the Azure AD Connect Health for analysis. Currently we support two views:- Successful logins can be viewed by application (relying party trust), network location, authentication method or server. The application pivot is tremendously useful for understanding usage patterns of applications.
- Unique user count shows the number of unique users accessing applications and can be viewed by application (relying party trust).


Performance Data
This is a simple, aggregated view of key performance counters collected from your ADFS and proxy servers, including token requests, CPU, memory and latency. It can also help you detect potential balancing issues within your environment.


What's coming next?
We are actively working on adding the following capabilities to the service:- Email notification of alerts
- Support for monitoring and reporting on sync servers
- Failure trending and reports for the ADFS service
- Health and reporting of Azure AD services such as SaaS applications, MFA and password reset
Published Sep 06, 2018
Version 1.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.



