Howdy folks,
Today we've got some pretty cool news! We've just released the preview of our new Windows Azure Active Authenticaton service. A few months ago we showed you how to enable multi-factor authentication for your Azure AD Global Admins . With this preview we're giving you the ability to give all your employees, customers and partners a rich set of smartphone based two factor authentication options.
Starting now, companies can use this preview to enable multi-factor authentication for all their Windows Azure Active Directory identities securing access to Office 365, Windows Azure, Windows Intune, Dynamics CRM Online and many of the other applications that are integrated with Windows Azure AD. Additionally Developers can also use the Active Authentication SDK to build multi-factor authentication into their custom applications and directories.
Getting Started
To start using multi-factor authentication with your Windows Azure Active Directory tenant, you’ll first need to add the Active Authentication service. To do that:
-
Sign in to the Windows Azure Portal as an Administrator.
-
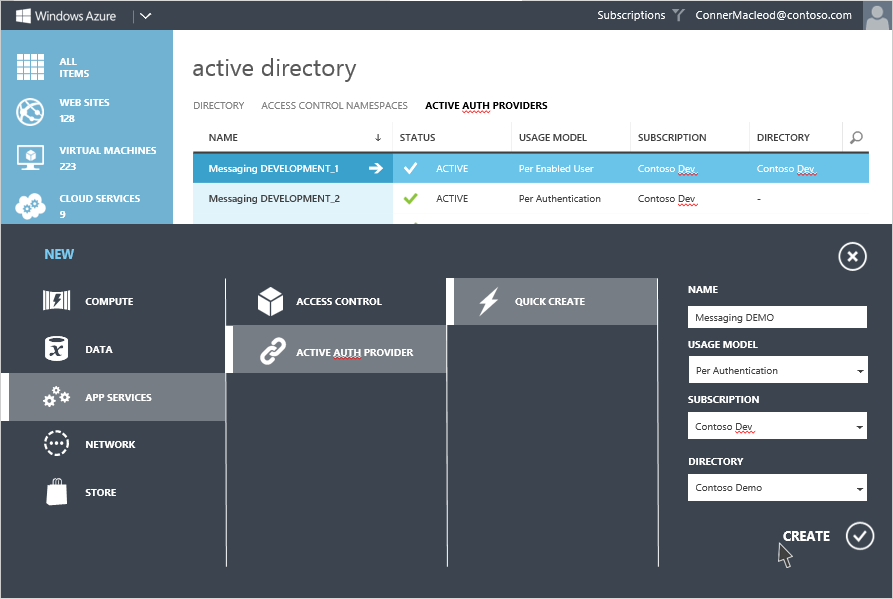
On the Active Directory page, at the top, select Active Auth Providers .
-
In the tray at the bottom of the page, click New .
Fig 1: Active Auth Provider Tab
-
Under App Services , select Active Auth Providers , and select Quick Create .
Fig 2: Adding a new provider
-
Fill in the following fields and when completed, select Create .
a. Name – The name of the Active Auth Provider, so you can associate for billing purposes for example, “Messaging DEMO”
b. Usage Model – Select the usage model you prefer - “ Per Enabled User ” or “Per Authentication”. This sets the billing model for this authentication provider as either per user or per authentication.
Note: You can learn more about these usage models and pricing here
c. Directory – Enter the Windows Azure Active Directory tenant that the Active Authentication Provider is going to be used with e.g. Contoso Demo
Fig 3: Completing the Authentication Provider Quick Create form
-
Once you click create, the Active Authentication Provider will be created and you should see a message stating: Successfully created Active Authentication Provider.
-
Click Ok
Now you've got Active Authentication provisioned and ready to use. Time to configure which users will have it enabled.
Turning on multi-factor authentication for specific users
-
Click on the Active Directory tab on the left
- Click the Directory tab underneath the Active Directory header
- Click on your Windows Azure AD tenant.
-
On the Users page, click the user you want to enable.
-
Select the Require Multi-factor Authentication check box
Fig 4: Activating 2 Factor Authentication for a user
Your admin tasks are all done. Pretty easy eh?
Signing in with Windows Azure Active Authentication Service
Once Active Authentication has been enabled for a user the next time that user signs into a service that uses Windows Azure AD, they will be asked to select and configure one of these multi-factor authentication methods:
- App Notification – Use the Active Authentication smart phone app.
- App One-time password (OTP) – Use a One-time Password with their Active Authentication smart phone app.
- Phone Call – A phone call to their mobile or landline phone.
- Text Message –A text message sent to their mobile phone.
This auto-enrollment feature , makes deploying multi-factor authentication easy and hassle free for ITPros while providing the end user the flexibility to configure the primary method that suits their needs. Users can add or change methods later.
While all four of these authentication methods work great, my favorite is our Active Authentication app (available for Windows Phone , iOS and Android smartphones and tablets). You can download the free app from the device store and activate it. If you are a gadget geek like me, this is the one you’ll want to use!
Configuring your account to use the Windows Azure Active Authentication smart phone app:
-
First, if you are logged into Windows Azure, Office 365, or another service integrated with Windows Azure AD, log-out.
-
Using your browser, sign in to Windows Azure or Office 365 .
-
You will be prompted to configure your multi-factor options. Click the "Set it up now" button.
Fig 5: Prompt to configure Multi-Factor Auth when signing in the first time.
-
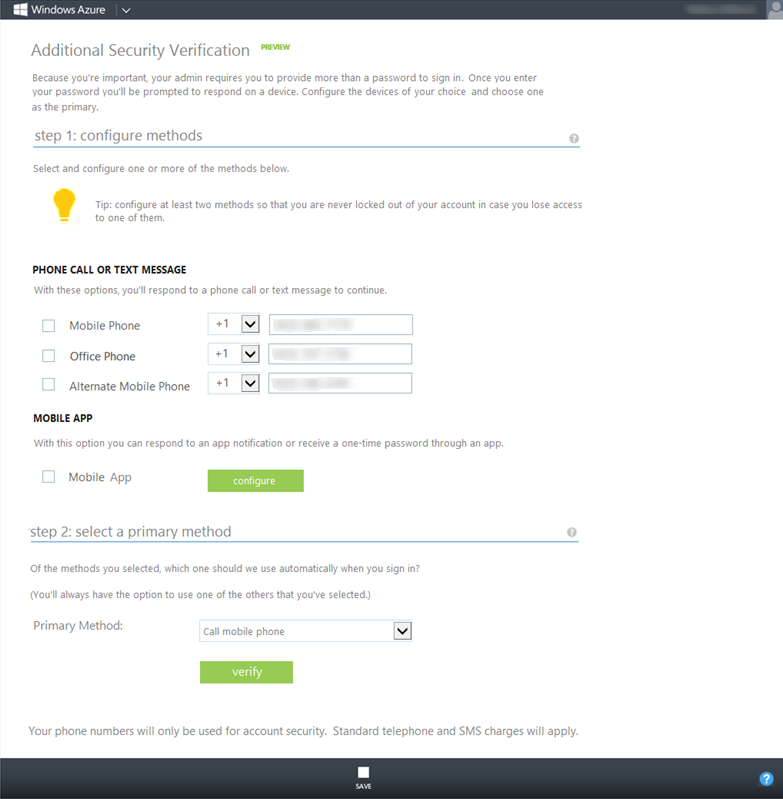
This will bring up the Additional Security Verification settings page. Once that page loads, under mobile app , select the check box and click Configure .
Fig 6: Additional Verification Page
-
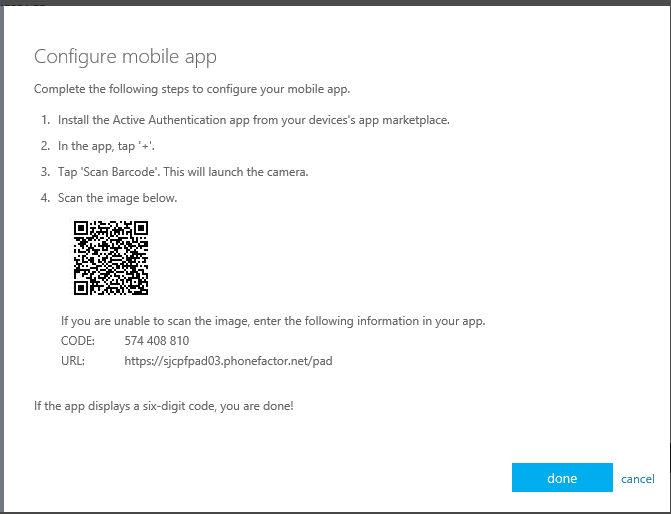
That will bring up the App Configuration screen:
Fig 7: Configure App Screen
-
On the phone that has the Active Authentication app installed, launch the app.
-
Now click the + sign in the app to add a new account.
-
Then click the barcode scanner button on the far right in the app. This will launch the camera.

Fig 8: Active Authentication App Configuration Screen
-
Scan the barcode picture that came up with the configure phone app screen.
-
After a few seconds you should see a 6 digit code on the app screen. Once you see this click the check mark button on the configure phone app screen.
-
Click Save .
You are all set!
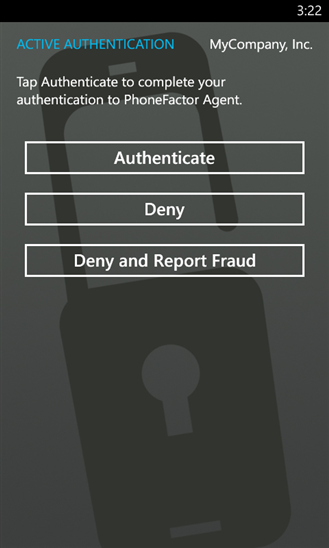
The next time you sign-in to a cloud application or service protected by Windows Azure AD, the app will activate on your phone and ask you to authenticate or deny the login. You also have the option to report the attempt as being fraudulent.
Of course, the app is my personal favorite but you might like receiving a phone call better and most of the folks on our team prefer the SMS messaging option. The great thing about the service is that your users can choose the method they like best and switch between methods without any additional configuration on your part.
We’ll have a lot more coming in this space in the very near future, so stay tuned. And as always, we would love to hear your feedback. Head over to the Windows Azure Active Authentication forum to let us know what you think.
Best Regards,
Alex Simons (Twitter: Alex_A_Simons)
Director of Program Management
Active Directory
 Microsoft
Microsoft