- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- 10 Reasons to Love Passwordless #2: NIST Compliance
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hello,
This is the second post in the “Ten Reasons to Love Passwordless” blog series. Last time, we talked about the flexibility and multi-platform benefits of FIDO2 open standards based technology. The second reason to love passwordless is it brings the highest levels of security to your organization. Passwordless multifactor authentication (MFA) eliminates the need to memorize passwords and as such makes it 99.9% harder to compromise an account. Using built-in crypto keys in your software or hardware from passwordless solutions, you get the security assurance that meets the highest standards. Helping our customers achieve these MFA goals is music to my ears!
Security assurance with NIST (800-63)
Let’s start with the National Institute of Standards and Technology (NIST) which develops the technical requirements for US federal agencies implementing identity solutions. NIST’s 800-63 Digital Identity Guidelines Authentication Assurance Levels (AAL) is a mature framework used by federal agencies, organizations working with federal agencies, healthcare, defense, finance, and other industry associations around the world as a baseline for a more secure identity and access management (IAM) approach. How does passwordless and multifactor authentication align with NIST’s requirement? And how can the required AALs be met?
Before diving into the details, let us align some terminology:
- Authentication - The process of verifying the identity of a subject.
- Authentication factor - Something you know, something you have, or something you are: Every authenticator has one or more authentication factors.
- Authenticator - Something the subject possesses and controls that is used to authenticate the subject’s identity.
Multifactor Authentication
Multifactor authentication can be achieved by either a multifactor authenticator or by a combination of multiple single factor authenticators. A multifactor authenticator requires two authentication factors to execute a single authentication transaction.
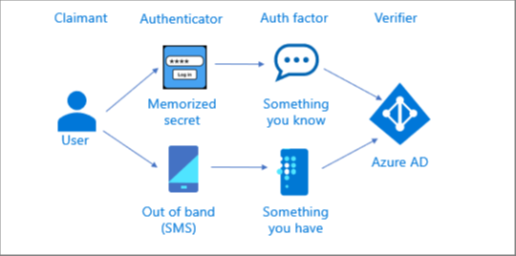
Multifactor authentication using two single factor authenticators
The illustration below shows how a multifactor authentication can be performed using a memorized secret (something you know) authenticator along with an out of band (something you have) authenticator. The user performs two independent authentication transactions with Azure AD.
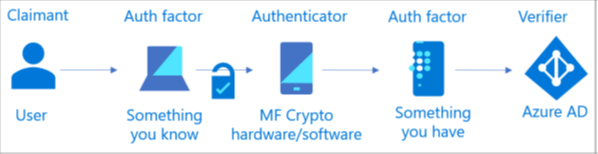
Multifactor authentication using a single multifactor authenticator
The illustration below shows how a multifactor authentication is performed using a single multifactor cryptographic authenticator requiring one authentication factor (something you know or something you are) to unlock a second authentication factor (something you have). The user uses a single authentication transaction with Azure AD.
Microsoft Passwordless Authenticators mapped to NIST 800-63 AALs
Microsoft passwordless authenticators allow multifactor authentication using a single authenticator and eliminate the dependency on memorized secret (password) authenticator and the associated password attacks (see Your Pa$$word doesn’t matter).
|
Authentication method |
NIST Authenticator type |
AAL |
|
Multi-factor cryptographic hardware (with TPM) Multi-factor cryptographic software (without TPM) |
AAL3 AAL2 |
|
|
Multi-factor cryptographic hardware (Android) Multi-factor cryptographic software (iOS) |
AAL2 AAL2 |
|
|
Multi-factor cryptographic hardware |
AAL3 |
*FIDO2 Security Key partners such as Feitian, Thales (formerly Gemalto), TrustKey (formerly eWBM), and Yubico, are in the process of certifying their FIDO2 security keys with FIPS 140.
Federal agencies, organizations working with federal agencies and organizations in regulated industries seeking Federal Information Processing Standards 140 (FIPS 140) verification are advised to reference Achieving National Institute of Standards and Technology Authenticator Assurance Levels with the Mic... and conduct risk assessment and evaluation before accepting these authenticators as AAL2/3.
Check out the other posts in this series:
- Temporary Access Pass is now in preview
- What's New in Passwordless Standards, 2021 edition!
- 10 Reasons to Love Passwordless #1: FIDO Rocks
- 10 Reasons to Love Passwordless #2: NIST Compliance
- 10 Reasons to Love Passwordless #3: Why biometrics and passwordless are a dream combination
- 10 Reasons to Love Passwordless #4: Secure your digital estate, while securing your bottom line
- 10 Reasons to Love Passwordless #5: The Ease of Use and Portability of Security Keys
- 10 Reasons to Love Passwordless #6: The Passwordless Funnel
- 10 Reasons to Love Passwordless #7: Authenticator app for easy phone sign in
- 10 Reasons to Love Passwordless #8: You won't get phished!
- 10 Reasons to Love Passwordless #9: Onboard without a password
- 10 Reasons to Love Passwordless #10: Never use a password
Learn more about Microsoft identity:
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.