Following our last article, introducing the new Exchange Administration Center (EAC), we follow up on how the new EAC makes it really easy to manage multi-forest Exchange deployments.
As described in Deploy Exchange 2010 in a Cross-Forest Topology, Exchange Server 2010 can be deployed in a cross-forest or resource forest topology. For the purpose of this article, we will employ the same approach to deploy a resource forest topology with The New Exchange.
First, let’s setup a resource forest environment as shown below, with a one-way forest trust setup so that Forest B trusts Forest A.
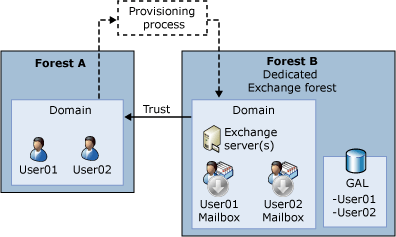
Figure 1: Layout of a resource-forest Exchange topology
Forest A is the account-forest, where all user accounts are provisioned. Forest A does not have any Exchange servers installed. Forest B is the resource forest – with Exchange Server 2013 installed and with linked mailboxes for each of Forest A’s user accounts. Forest B has no user accounts provisioned.
In a lab environment, we have a user, John Doe, setup in Forest A. We now want John Doe to be an Exchange administrator. To do this, we need to ensure that he has the appropriate Role-Based Access Control (RBAC) privileges in place in the Exchange resource forest. Since we are dealing with a multi-forest environment here, there are two ways of configuring RBAC, and we will try both:
- Using linked mailboxes
- Using linked role groups
You may already have users setup in an account forest. Configuring these users as linked mailboxes establishes their presence in the Exchange resource forest. By adding these linked mailboxes to existing RBAC role groups, the associated users thus effectively become Exchange administrators.
Using linked mailboxes
In the figure below, John Doe’s user account is setup in the accounts forest. Using EAC, an Exchange administrator can then create a linked mailbox for him, as shown below.
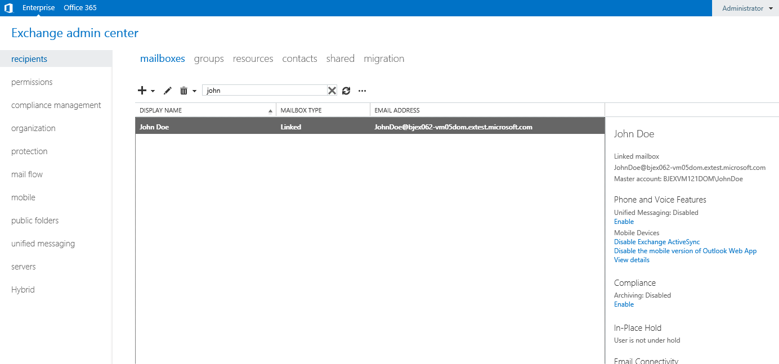
Figure 2: John Doe has been setup as a linked mailbox.
John’s mailbox can then be added to any of the built-in RBAC administrative role groups, thus making him an Exchange administrator. In the screenshot below, John has been made a member of the built-in Organization Management role group.

Figure 3: John Doe has been added as a member of the Organization Management role group.
Now, let’s try logging into EAC as John himself. John should now have Exchange administrative privileges, and that is what we see below.
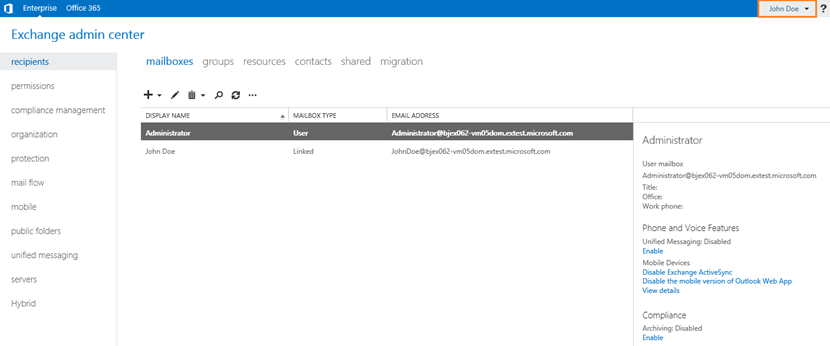
Figure 4: Logging into EAC as John Doe, configured as a linked mailbox, and as a member of the Organization Management role group.
Using linked role groups
Linked role groups are essentially role groups, but linked via a Universal Security Group (USG) across a forest boundary. Thus members of this USG effectively become members of the linked role groups. This means that if John Doe is a member of such a USG, he automatically gets all RBAC permissions in an Exchange resource forest via the linked role groups. Linked role groups thus make it possible for a small set of USGs in one account forest to manage complex, multiple Exchange forest topologies.
To demonstrate the above, we will do the following:
- In the account forest, using Active Directory Users and Computers (ADUC) management tool, we will create a USG called AdminSG. AdminSG will represent a group of Exchange administrators. We will then make John Doe a member of AdminSG
- In the resource forest, we will setup a single linked role group, based on the built-in role group “Organization Management”, mapped to AdminSG, using the following Exchange Management Shell calls:
$accountForestCredential = Get-Credential
$OrgMgmt = Get-RoleGroup "Organization Management"
New-RoleGroup "Organization Management - Linked" -LinkedForeignGroup "AdminSG" -LinkedDomainController bjex062.extest.microsoft.com -LinkedCredential $accountForestCredential -Roles $OrgMgmt.Roles
Get-ManagementRoleAssignment -RoleAssignee "Organization Management - Linked" -Role My* | Remove-ManagementRoleAssignment
Get-ManagementRole | New-ManagementRoleAssignment -SecurityGroup "Organization Management - Linked" -Delegating
With the above steps, John Doe now has all RBAC privileges in the Exchange resource forest even though his user account is in the account forest.
We will now attempt to login to EAC as John Doe. We launch EAC from any desktop, and point it to a CAS server in the resource forest, and we are logged in. John has standard RBAC privileges as defined in the Organization Management RBAC role group and is able to manage Exchange in the resource forest accordingly.

Figure 5: Logging into EAC as John Doe, via the linked Organization Management role group.
Try EAC!
As you can see, EAC makes it a snap to manage multi-forest Exchange deployments. You don’t need to remote into dedicated management machines to manage a specific Exchange forest, nor do you need to create special administrative accounts in every Exchange resource forest. You can do all this right from your own desktop with EAC, with your existing user credentials!
EAC is available in the latest Exchange 2013 Preview download bits as well as via the Office 365 Customer Preview offering. We will continue to write more about EAC in the upcoming weeks. In the meantime, do try the new EAC, and give us your feedback!
The Exchange Manageability Team