Update 1/19/2021: We have updated and expanded the information contained here in a new blog post. Please go here to read it: All you need to know about automatic email forwarding in Exchange Online
In support, I get this question quite frequently: “How do I block users from auto forwarding their mail outside my environment?” There are plenty of good reasons you may not want auto forwarding: you may have HIPAA laws to follow, regulatory compliance or data privacy concerns or simply because it makes you uncomfortable. A user can set up forwarding in a few different ways:
1. Create an inbox rule to forward using Outlook or Outlook on the web (also sometimes called by OWA, it’s old name). The types of forwarding via this method are: forward, forward as an attachment and redirect.
- In Outlook this is accessed through File > Manage Rules and Alerts
- In OWA this is accessed through Options > Mail > Inbox and sweep rules
2. Set forwarding on their mailbox using OWA options.
- In OWA this is accessed through Options > Mail > Forwarding. Users can select to Stop or Start forwarding and enter the address to forward to. This is set as a “ForwardingSMTPAddress” parameter on the mailbox.
Methods to stop auto forwarding
As an admin, you have a few different ways to prevent forwarding of emails outside of your environment. The main ways I have identified are listed below, along with a brief description of their pros and cons. Select the link to learn more:
- Pros: Applies to all the above-mentioned types of forwarding a user can set up. Quick and easy to configure.
- Cons: The user is not notified their forwarded message is dropped
- Use If: You have few exceptions to consider and just want an easy blanket option
- Pros: Allows you more granularity on conditions and actions, reporting is available
- Cons: Does not block the OWA “Start/Stop Forwarding” method
- Use If: You want to be able to notify the user their message was blocked, or if you have complex exceptions you need to allow for
Role Based Access Control (RBAC)
- Pros: In OWA, users simply do not see the option to set forwarding up
- Cons: Does not remove the options in Outlook and does nothing for forwarding that was already set up. It only removes the option to set it up from view; it does not remove any rules already in place and for that matter, it continues to allow those rules to function (though admittedly you could always run a script to null out the parameter).
- Use If: You are a company that primarily uses OWA and have already ensured users do not have forwarding set to begin with.
Remote Domain
You can set up the remote domain option through the Exchange Online Admin Center > Mail Flow > Remote Domains and select the default remote domain. Uncheck the “allow automatic forwarding” box and repeat for any additional remote domains you may have set up that you want to drop auto forwarded messages to. 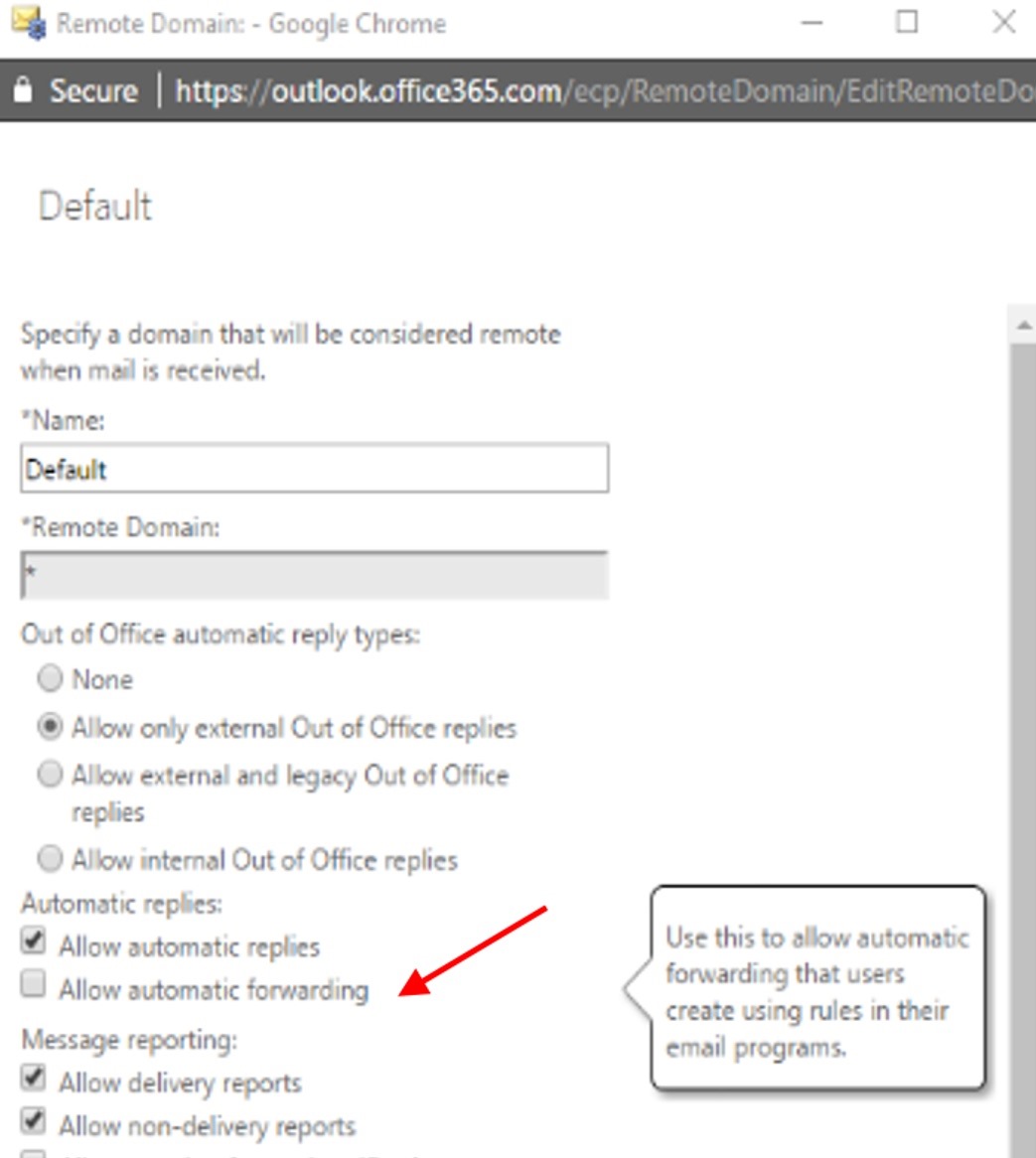 The downside to this method is that the user is not notified that their forwarded message is dropped. However, as an admin, you would see the drop in a message trace as a failed message with the following Drop reason: “[{LED=250 2.1.5 RESOLVER.MSGTYPE.AF; handled AutoForward addressed to external recipient};{MSG=};{FQDN=};{IP=};{LRT=}]” Say you have a partner company, and your users may have legitimate reasoning to forward their mail to the partner; you can configure an additional remote domain for the partner domain with different settings.
The downside to this method is that the user is not notified that their forwarded message is dropped. However, as an admin, you would see the drop in a message trace as a failed message with the following Drop reason: “[{LED=250 2.1.5 RESOLVER.MSGTYPE.AF; handled AutoForward addressed to external recipient};{MSG=};{FQDN=};{IP=};{LRT=}]” Say you have a partner company, and your users may have legitimate reasoning to forward their mail to the partner; you can configure an additional remote domain for the partner domain with different settings.
Transport Rule
To set up a transport rule in Exchange Online Admin Center, navigate to Mail Flow > Rules and select the plus sign to create a new rule. If you are not seeing all options, ensure you select “More options” towards the bottom of the screen. You can add multiple conditions, but the key is to include “the message type is… Auto-forward”. In PowerShell that would be the parameter ‘-MessageTypeMatches AutoForward’ In the image, I have chosen to apply the rule to messages forwarded to all recipients outside the organization and I am rejecting the message with an explanation so the user is informed of the policy. 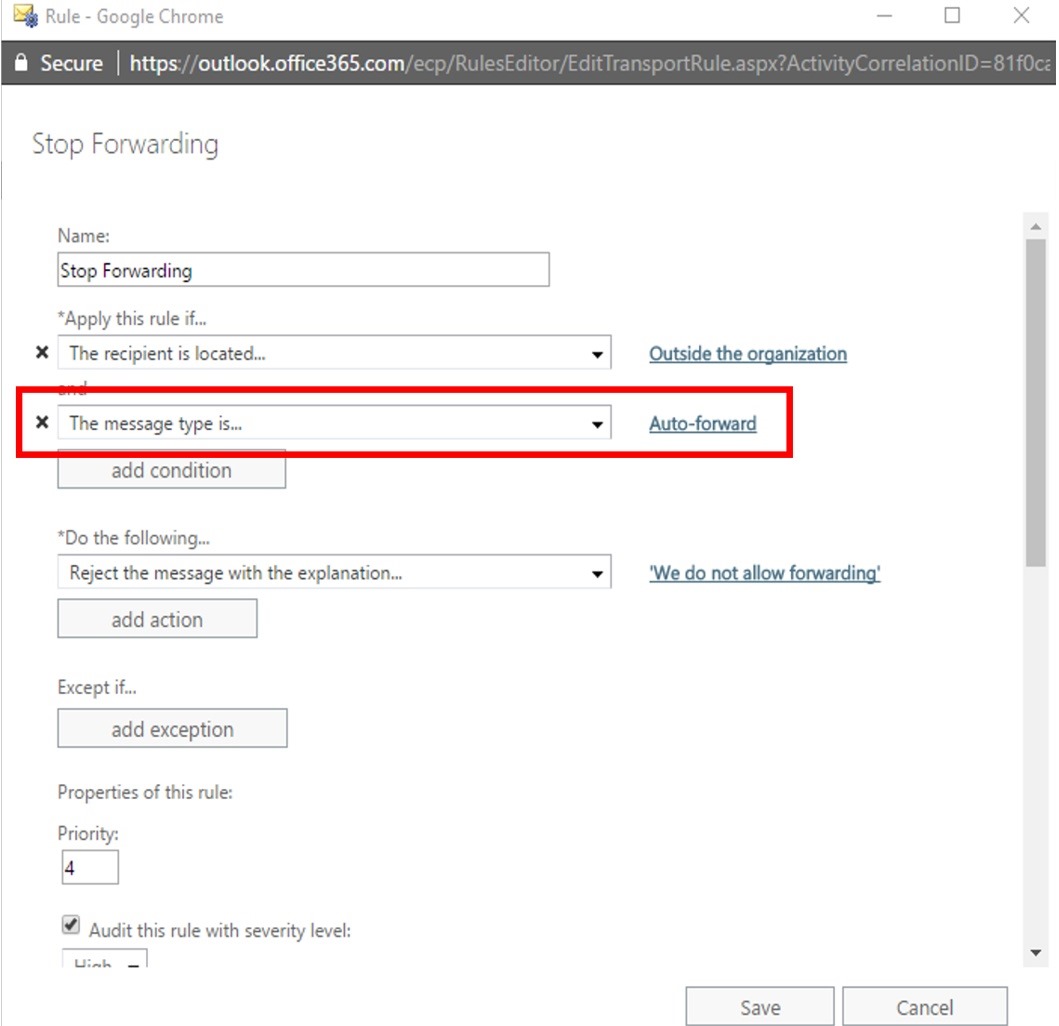 You can also easily add exceptions here via the “add exception” button if certain senders or recipient domains should be allowed to forward. In addition, you can easily identify the users hitting this rule as well through PowerShell reporting or by the generating an incident report action.
You can also easily add exceptions here via the “add exception” button if certain senders or recipient domains should be allowed to forward. In addition, you can easily identify the users hitting this rule as well through PowerShell reporting or by the generating an incident report action.
Role Based Access Control (RBAC)
RBAC is the method to remove the forwarding options from user’s view in Outlook on the web. You may want to note that RBAC is cumulative, so if an administrator has an admin role that includes New-Inbox rule with the forwarding parameters, removing it with the steps above will not make it disappear. If you are less familiar with manipulating RBAC, I would point you to this blog post which does a deeper dive into RBAC in general. This tips and tricks guide is also incredibly handy. I have already identified the main user role that includes the cmdlets and parameters that need to be removed, however if you would like to find which roles include other commands you could run the following: Get-ManagementRoleEntry “*\New-InboxRule” Here are the steps to create a new management role and remove the forwarding options.
1.) Create the new role with parent “MyBaseOptions”
- New-ManagementRole -Parent MyBaseOptions -Name DenyForwarding
2.) Depending on what you want to do, I have 3 sets of sample CMDlets for you:
- Removes ability to create a new inbox rule in Outlook on the web with 3 specified actions: Set-ManagementRoleEntry DenyForwarding\New-InboxRule -RemoveParameter -Parameters ForwardTo, RedirectTo, ForwardAsAttachmentTo
- Removes ability to edit an existing inbox rule to change it to one of specified 3 actions: Set-ManagementRoleEntry DenyForwarding\Set-InboxRule -RemoveParameter -Parameters ForwardTo, RedirectTo, ForwardAsAttachmentTo
- Removes the page in “Forwarding” page in Outlook on the web options: Set-ManagementRoleEntry DenyForwarding\Set-Mailbox -RemoveParameter -Parameters DeliverToMailboxAndForward,ForwardingAddress,ForwardingSmtpAddress
3.) Create a new policy and add all the management roles, including our new one. You may need to tweak this command some if you already have other custom entries
- New-RoleAssignmentPolicy -Name DenyForwardingRoleAssignmentPolicy -Roles DenyForwarding, MyContactInformation, MyRetentionPolicies,MyMailSubscriptions,MyTextMessaging, MyVoiceMail,MyDistributionGroupMembership, MyDistributionGroups, MyProfileInformation
4.) Lastly, assign your policy to your cloud mailboxes
- Set-Mailbox –Identity user@contoso.com -RoleAssignmentPolicy DenyForwardingRoleAssignmentPolicy
The result (if all of the CMDlets were used): 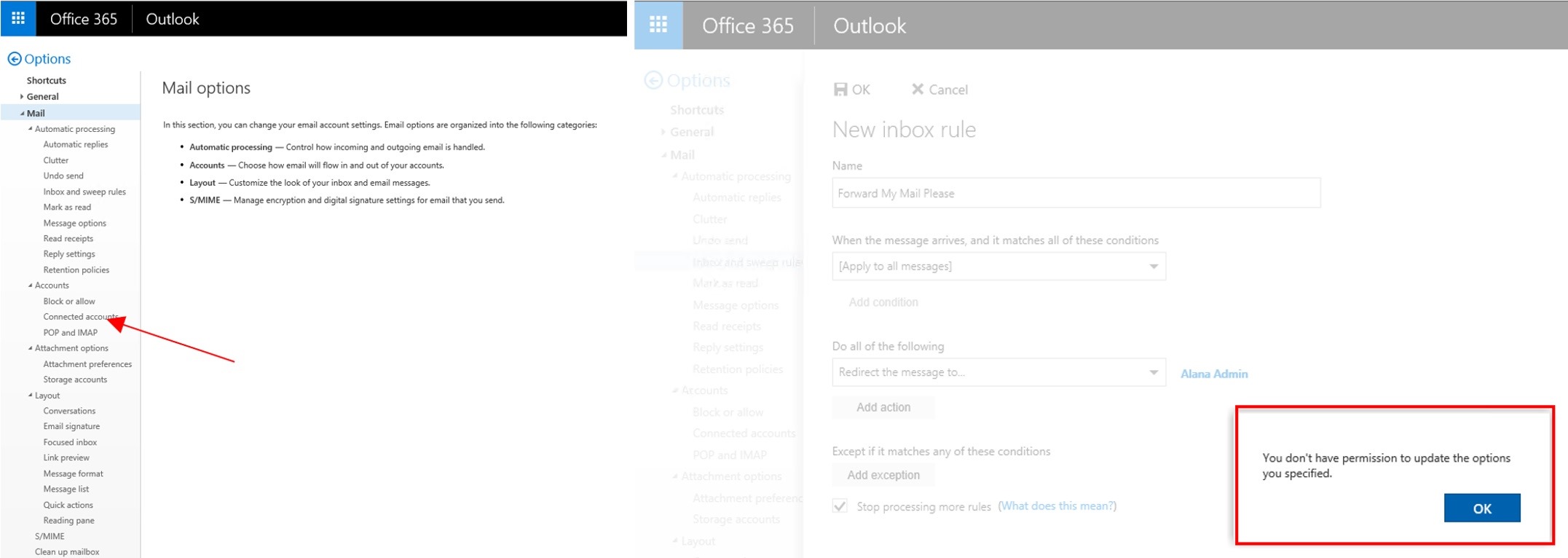
Note: since this article was written, we have heard a question on blocking emails forwarded by Power Automate (Flow). To learn about that, please see Email exfiltration controls for Office 365 connectors.
What do I suggest?
How restrictive do you want to be? What are you worried about in your environment? There’s no one size fits all option. You can implement all three options if you really want. Personally, I like the combination of transport rule + RBAC. This combination covers all bases, yet still allows for exceptions if necessary. In that setup, the forwarding options in Outlook on the Web are completely removed, and if a forwarding Inbox rule in Outlook is created, messages can be blocked with an informational Non-delivery report back to the user. Special thanks to Ben Winzenz and Tim Heeney for their assistance and review of this content.
Alana Wegfahrt